Migrated from igb to bge Suricata Won't Run (solved)
-
Your firewall is a complete mess! Look at the log file you posted. Did you actually read what it says?
Look at these two lines:
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)... Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...You can't, and shouldn't, run both Snort and Suricata on the same interface. In fact, you should never run both packages on the same firewall- ever! They will conflict with each other, particularly over the use of the
snort2ctable..It also appears your migration of the
config.xmlfile to new hardware did not go well. The fact you still had references to the igb interfaces is evidence of that. My suggestion is that you just wipe this configuration out entirely and start over from scratch on this new hardware. Do not try to migrate the configuration from your old hardware over to this new box. -
@NollipfSense said in Migrated from igb to bge Suricata Won't Run:
Package installer said Suricata is installed however, there is no yaml...how could that be? Is there anything I can do at the command prompt?
Shell Output - /etc/suricata/suricata.yaml
sh: /etc/suricata/suricata.yaml: not foundYou are looking in the wrong directory. That is not where the configuration of local packages exists on FreeBSD installs such as pfSense. The correct directory is /usr/local/etc, but even then that is not the entire path for Suricata or Snort. The interface configurations live in sub-directories underneath /usr/local/etc/suricata or /usr/local/etc/snort.
-
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
Your firewall is a complete mess! Look at the log file you posted. Did you actually read what it says?
Look at these two lines:
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)... Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...You can't, and shouldn't, run both Snort and Suricata on the same interface. In fact, you should never run both packages on the same firewall- ever! They will conflict with each other, particularly over the use of the
snort2ctable..It also appears your migration of the
config.xmlfile to new hardware did not go well. The fact you still had references to the igb interfaces is evidence of that. My suggestion is that you just wipe this configuration out entirely and start over from scratch on this new hardware. Do not try to migrate the configuration from your old hardware over to this new box.Okay Bmeeks; however, only Suricata is in inline mode with blocking enabled...Snort is running in alert only with no blocking. Had that setup running for almost a year and a half with no problem on the HP box.
You are correct Bmeeks and I'll start over from scratch next weekend.

-
@NollipfSense said in Migrated from igb to bge Suricata Won't Run:
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
Your firewall is a complete mess! Look at the log file you posted. Did you actually read what it says?
Look at these two lines:
Jun 16 21:53:07 SuricataStartup 33537 Suricata START for WAN(32760_bge0)... Jun 16 21:53:07 SnortStartup 38614 Snort START for WAN(23083_bge0)...You can't, and shouldn't, run both Snort and Suricata on the same interface. In fact, you should never run both packages on the same firewall- ever! They will conflict with each other, particularly over the use of the
snort2ctable..It also appears your migration of the
config.xmlfile to new hardware did not go well. The fact you still had references to the igb interfaces is evidence of that. My suggestion is that you just wipe this configuration out entirely and start over from scratch on this new hardware. Do not try to migrate the configuration from your old hardware over to this new box.Okay Bmeeks; however, only Suricata is in inline mode with blocking enabled...Snort is running in alert only with no blocking. Had that setup running for almost a year and a half with no problem on the HP box.
You are correct Bmeeks and I'll start over from scratch next weekend.

Having both of those running on the same firewall makes absolutely no sense. They use essentially the same rule signatures. That's almost like running two copies of the same anti-virus program on a PC. What is one going to detect that the other doesn't? Pick one or the other IDS/IPS solution (Suricata or Snort) and use just that one. Don't try to use both on the same box, much less on the same interface.
-
@bmeeks Bill, I had to post this example although it's not related to pfSense...you might know of it and it's from Github: https://github.com/security-onion-solutions/security-onion
Security Onion"Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
For more information about Security Onion, please see our main website, blog, and docs".
They have both Suricata, and Snort on the same OS/box...I am not the only one with that crazy idea. For me, Suricata works WAN and Snort on LAN...I get your point though on potential conflict.
-
@NollipfSense said in Migrated from igb to bge Suricata Won't Run:
@bmeeks Bill, I had to post this example although it's not related to pfSense...you might know of it and it's from Github: https://github.com/security-onion-solutions/security-onion
Security Onion"Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
For more information about Security Onion, please see our main website, blog, and docs".
They have both Suricata, and Snort on the same OS/box...I am not the only one with that crazy idea. For me, Suricata works WAN and Snort on LAN...I get your point though on potential conflict.
I still see no point really in running both on the same box, but so long as they are on totally separate interfaces it will work (well, so long as one is using Inline IPS Mode and the other is using Legacy Mode or IDS mode only; otherwise they can conflict with the single snort2c table in
pf). In your case, I saw in the system log snippet you posted that both Suricata and Snort were attempting to start on the same interface (bge0, if I recall correctly). That won't work well at all! One is trying to configure the interface for netmap mode and other is trying to configure it for PCAP mode. Not going to work correctly. -
@bmeeks You did recalled correctly...may be it worked with the Intel card with no problem. However, the bge is a different animal and I should have anticipated problems...of course, my head was all about the cute and very small form factor...only the weekend will tell after taking your advice...will inform you then.
-
I never recommend running both on the same interface, but the only way it can work (well) is if only one application is running with blocking mode enabled. So you could run Suricata in just IDS mode (Block Offenders NOT checked) and Snort in blocking mode with Block Offenders checked; or the other way around. You should never run with both in blocking mode on the same interface.
And my other caution about both running on the same box in blocking mode, even on different interfaces, is valid because they will conflict with each other over use of the snort2c table. There is only a single snort2c table for the entire firewall.
-
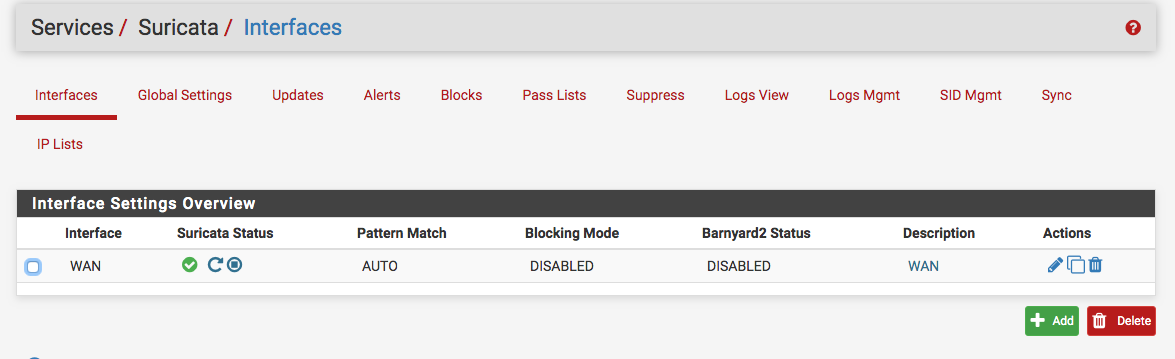
Okay Bill, I did the fresh install and Suricata will not run or not showing that its running on the interface tab. Suricata WAN log shows: 7/7/2019 -- 00:42:47 - <Error> -- [ERRCODE: SC_ERR_INITIALIZATION(45)] - pid file '/var/run/suricata_bge023163.pid' exists but appears stale. Make sure Suricata is not running and then remove /var/run/suricata_bge023163.pid. Aborting!
I went to edit file under Diagnostic and load /var/run

However, I cannot figure out how to delete it...can you help? Here's system log and noticed there is some time issue:
Jul 7 04:12:41 check_reload_status Syncing firewall
Jul 7 04:12:41 check_reload_status Syncing firewall
Jul 7 04:13:30 check_reload_status Syncing firewall
Jul 7 04:13:59 check_reload_status Syncing firewall
Jul 7 04:14:07 check_reload_status Syncing firewall
Jul 7 04:21:55 check_reload_status Syncing firewall
Jul 7 04:22:13 check_reload_status Syncing firewall
Jul 7 04:32:46 check_reload_status Syncing firewall
Jul 7 04:34:20 check_reload_status Syncing firewall
Jul 7 04:34:27 php-fpm 366 Starting Suricata on WAN(bge0) per user request...
Jul 6 23:34:27 php [Suricata] Updating rules configuration for: WAN ...
Jul 6 23:34:27 php [Suricata] Building new sid-msg.map file for WAN...
Jul 6 23:34:27 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 04:34:32 php-fpm 365 Starting Suricata on WAN(bge0) per user request...
Jul 6 23:34:32 php [Suricata] Updating rules configuration for: WAN ...
Jul 6 23:34:33 php [Suricata] Building new sid-msg.map file for WAN...
Jul 6 23:34:33 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 04:34:36 php-fpm 365 Starting Suricata on WAN(bge0) per user request...
Jul 6 23:34:36 php [Suricata] Updating rules configuration for: WAN ...
Jul 6 23:34:37 php [Suricata] Building new sid-msg.map file for WAN...
Jul 6 23:34:37 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 04:51:23 check_reload_status Syncing firewall
Jul 7 05:04:39 check_reload_status Syncing firewall
Jul 7 05:04:50 php-fpm 81239 Starting Suricata on WAN(bge0) per user request...
Jul 7 00:04:50 php [Suricata] Updating rules configuration for: WAN ...
Jul 7 00:04:51 php [Suricata] Building new sid-msg.map file for WAN...
Jul 7 00:04:51 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 05:05:49 check_reload_status Syncing firewall
Jul 7 05:05:54 php-fpm 366 Starting Suricata on WAN(bge0) per user request...
Jul 7 00:05:55 php [Suricata] Updating rules configuration for: WAN ...
Jul 7 00:05:55 php [Suricata] Building new sid-msg.map file for WAN...
Jul 7 00:05:55 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 05:07:01 check_reload_status Syncing firewall
Jul 7 05:42:24 check_reload_status Syncing firewall
Jul 7 05:42:46 php-fpm 56294 Starting Suricata on WAN(bge0) per user request...
Jul 7 00:42:46 php [Suricata] Updating rules configuration for: WAN ...
Jul 7 00:42:47 php [Suricata] Building new sid-msg.map file for WAN...
Jul 7 00:42:47 php [Suricata] Suricata START for WAN(bge0)...
Jul 7 05:46:46 check_reload_status Syncing firewall
Jul 7 05:46:46 syslogd exiting on signal 15
Jul 7 00:46:46 syslogd kernel boot file is /boot/kernel/kernel
Jul 7 00:46:46 nollipfsense.localdomain nginx: 2019/07/07 00:46:46 [error] 50081#100505: send() failed (54: Connection reset by peer)
Jul 7 01:00:00 php-cgi [Suricata] Checking for updated MaxMind GeoLite2 IP database file...
Jul 7 01:00:00 php-cgi [Suricata] GeoLite2-Country IP database is up-to-date.
Jul 7 01:00:00 php-cgi [Suricata] GeoLite2-Country database update check finished.
Jul 7 02:36:49 nollipfsense.localdomain nginx: 2019/07/07 02:36:49 [error] 50154#100632: send() failed (54: Connection reset by peer)
Jul 7 10:39:46 check_reload_status Syncing firewall
Jul 7 10:39:46 php-fpm 365 [Suricata] Updating rules configuration for: WAN ...
Jul 7 10:39:47 php-fpm 365 [Suricata] Enabling any flowbit-required rules for: WAN...
Jul 7 10:39:47 php-fpm 365 [Suricata] Building new sid-msg.map file for WAN...I have been reading your reply here: https://forum.netgate.com/topic/131716/still-seeing-suricata-stop-an-interface-due-to-pid-error/35
Also this and I wondered why permission denied:
Shell Output - /var/log/suricata
sh: /var/log/suricata: Permission deniedBTW, I had increased Stream memory Cap to 512MB for my 8 CPU/Core with no luck.
-
Do you actually have 2 instances of Suricata running on both your LAN and WAN interfaces?
You also seem to have the same UUID on both bge0 and bge1. That is not possible within the GUI. Did you manually edit something in the
config.xmlfile? If so, the configuration is not correct. You should never have the same UUID on any interface. You have 23163 on both bge0 and bge1. While that is not directly the cause of your PID file problem, it does clearly indicate to me that your Suricata configuration is totally hosed up on that box. Is this still that Mac server you were trying to use earlier? -
@bmeeks said in Migrated from igb to bge Suricata Won't Run:
Do you actually have 2 instances of Suricata running on both your LAN and WAN interfaces?
You also seem to have the same UUID on both bge0 and bge1. That is not possible within the GUI. Did you manually edit something in the
config.xmlfile? If so, the configuration is not correct. You should never have the same UUID on any interface. You have 23163 on both bge0 and bge1. While that is not directly the cause of your PID file problem, it does clearly indicate to me that your Suricata configuration is totally hosed up on that box. Is this still that Mac server you were trying to use earlier?Yes Bill, it is the same Mac server and no, I didn't edit config.xml. When I first configured Suricata on WAN to see whether it would run without enabling any blocking and it did not. So, I implement LAN to see whether it would run and that didn't either. May be I should have rebooted the machine.
-
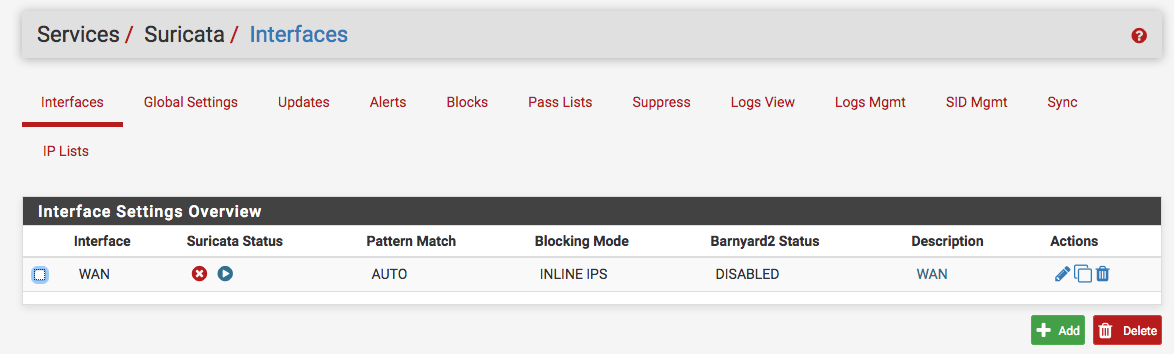
Bill, I just rebooted and Suricata is now running!