Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...
-
This is VMware design question. I don't really see the challenges- ISPs uplink to a core, you set these on vlans, you create vlans for your networks. The ESXi hosts just have a trunk to the core, you create vmnets on the vlans. You restrict access with firewall rules.
-
1 and 6 are in direct contradiction to each other.
Unless your talking about putting some wireless devices on same L2 as wired they need to talk to this. This is just simple AP that understands vlans.
But then that contradicts 2..
What exactly is this problem of devices wired and wireless not being able to talk across subnets?
This really has zero to do with pfsense at all from your questions... You have not asked how to do something specific in pfsense..
I don't see any questions here related to pfsense at all.. pfsense supports vlans, pfsense supports lacp which isn't going to matter anyway if pfsense is a VM.. Your lacp connections would be handled by the hardware pfsense vm is running on.
3 - yeah ok.. Yes pfsense can handle multiple wan connections - what does that have to do with L2/Vlans or switching?
Happy to answer a question once you ask one... How you want to segment out your network is up to you. And not anything to do with pfsense - I can move this topic to the general section for you.. This seem more like where it belongs.
-
@dotdash the question about WANs and distributing those wasn't the pressing issue, but I did ask in case there was a better way. I do indeed ue vLANs for the distributing the WAN links.
-
@johnpoz said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
I don't see any questions here related to pfsense at all.. pfsense supports vlans, pfsense supports lacp which isn't going to matter anyway if pfsense is a VM.. Your lacp connections would be handled by the hardware pfsense vm is running on.
Happy to answer a question once you ask one... How you want to segment out your network is up to you. And not anything to do with pfsense - I can move this topic to the general section for you.. This seem more like where it belongs.
Well.
I felt my question was asked, but I suppose that it's not clear?
How do I ensure that the Wired and wireless devices can be segments safely, yet avoid the "cant talk across subnets" issues?
The reasons that these cant talk across subnets are varied and would require tactical solutions for each.
Some need "helpers" like Bonjour, etc.Placing them on the same subnet eliminates all these types of issues.
In other cases, some only have wireless connectivity and others only have wired interfaces.
Yet they must speak to each other - but wont outside of their subnet.Another reason to flatten them would be to remove the router as a dependency for connectivity.
In the case of a routing issue, devices on the same subnet would still be able to talk.Maybe it's possible to set up segments within the same L2 network and still manage the segments as if they were on separate interfaces? If I could, then I can continue to use features like "Captive Portal", firewall rules on interfaces, etc.
Many of these devices are biomedical and lab testing/sampling devices.
They are very dumb, and must be operational during a test or the data isn't captured. (they cant buffer data)So, if they cannot talk for whatever reason, then the results of some experiments are lost.
Vendors are uncooperative, so I must find a way to manage the risks these wireless devices present while at the same time ensuring low-latency, low dependency connectivity.
I hope that helps with clarifying the question, while at the same time gives more insight into the challenges i'm facing.
-
@lburns said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
How do I ensure that the Wired and wireless devices can be segments safely, yet avoid the "cant talk across subnets" issues?
What issues??? I have zero issues with this, every single company have worked at wireless is always on its own segment.. .Only the smallest of the small ma and pop shops have issues with this where they try and get their ABC home equipment to work..
Please give an example of what you feel is not going to work across segments? Only something that requires discovery on the same L2 would have issues.. Airprint can be an issue - but you can just use mdns to solve that issue. And or just put a printer on the segment so your guests or wifi users can print to that printer, etc.
You have devices then put them on the same L2... If you want to have different firewall rules for different devices on that L2 - then you would assign device X IP A, and device Y, IP B - and firewall that way - pfsense is a L3 firewall. If you want to isolate devices on the same L2... That would be done with your L2 infrastructure.. private vlans, multicast filtering, etc. etc.
How do you have it setup currently? Everything on 1 flat network?? What equipment are you wanting to replace with pfsense? Pfsense can pretty much go head to head with some very expensive gear ;)
-
@johnpoz said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
@lburns said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
How do I ensure that the Wired and wireless devices can be segments safely, yet avoid the "cant talk across subnets" issues?
What issues??? I have zero issues with this, every single company have worked at wireless is always on its own segment..
Of course - This is what we currently HAVE and for the SAME reason anyone would do it.
This is also how I know it's not working for some devices.Please give an example of what you feel is not going to work across segments? Only something that requires discovery on the same L2 would have issues.. Airprint can be an issue - but you can just use mdns to solve that issue.
This type of issue is exactly how I'm encountering issues.
These devices do require "discovery on the same L2 ".Some have network based control features while other send video streams and other un-routable data streams. Each vendor has their own take on how to make these devices "work".
You must understand that the challenge here is presented by vendors that still require Windows XP to run their "servers" or maybe they just hacked an older device to use IP instead of IPX (via some crappy bridge) and then hike the price and sell them in this hacked/modded state.
The medical testing and measurement industry is riddled with devices that use the CRAZIEST approaches to design. There is NOTHING we can do about it and I'm merely attempting to re-design our network network in a way that allows for the plethora of un-routable network communications while also providing the most stable, secure and manageable network for them.
This iosn't so much about our ability to design a safe network, it is how to accommodate devices that have a bad design on that network.
We have no choice. Most of these devices have only one manufacturer and they have a monopoly on the product. No competition exists.
How do you have it setup currently? Everything on 1 flat network??
Nope, as I mentioned previously, everything IS segmented as it should be, but this is causing issues with non-routable devices talking to each other.
What equipment are you wanting to replace with pfsense? Pfsense can pretty much go head to head with some very expensive gear ;)
I am aware. We own much of that "expensive gear" and know that Pfsense can do the job.
This is why i'm here asking about how to get Pfsesne to make a subnet or supernet or something to allow me to manage the wired and wireless devices as if they were segmented, but still are in the same network.My questions really comes down to...
"How would you make something like... airprint as you suggested (or bonjour, etc) to speak across more than one network segment but NOT pass through a router to do it?"
OR...
"How would you break a single /24 network into parts that can be managed as you would separate segments?"
If I can get these non-routable issues to go away (make them act like they are on the same L2 net), all while maintaining the ability to manage them as if they were segmented (like they should be), then that would be ideal.
-
@lburns said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
If I can get these non-routable issues to go away (make them act like they are on the same L2 net), all while maintaining the ability to manage them as if they were segmented (like they should be), then that would be ideal.
Sounds like you need a good L3 capable managed switch. pfSense is not the right tool for this.
-
You want Layer 2 port isolation, Private VLANs, etc. Your solution is at Layer 2, not in the firewall.
-
Yea as Derelict repeated what I stated - if you want to isolate devices on a specific L2 from talking to each other you do what with your L2 infrastructure.. private vlans would allow you to have control which devices could talk to which other devices that are on the same L2/L3 network..
So for example you fire up a private vlan... device on port A could talk to device on port C, but not on port B. All devices could talk to port H which is where the gateway is connected so they could get off that L3..
Your AP is connected to say port G.. You could allow those wireless device to talk to port B, but not C or A, etc. etc. etc..
All of this is outside of the scope of pfsense - since pfsense is L3 firewall. What switches do you have to work with? Do you have budget to get new ones?
-
We have many Dell PowerConnect 8024 10G and other PowerConnect 1gb switches.
All we need in abundance
-
then yeah you should be good - I would assume they could do port isolation, ie private vlans - not sure what dell calls it.
-
Ive had a similar issue
esxi6.5 server running vms with vlan id added to the vmware NICs
6 WAN loadbalanced pfsense then to another pfsense squidguard firewall for siteblocking as squid will NOT work via a loadbalanced connection at all
my solution was to use UniFi hardware switches and AP's combined with pfsense firewall for routing.
the Unifi Controller enables the use of vLAN tagging for switch ports and separate wifi SSID's so your wifi users are vlan tagged depending on the wifi SSID they join, as well as being able to tag any port on any unifi switch among other things.
then vlan networks in pfsense with obvious firewall rules for segragating networks and allowing different devices through to whatever network you need.
then bonjour accross vlans and networks was avahi enabled and needed networks selected and select repeat mdns packets across networks 'as i needed the bonjour traffic to pass for air print capabilities and other minor bonjour services to work
just pulling my hair out over the routing for my PBX server's in/out SIP trunk and forcing it to use a single WAN connection from behind the squid pfsense vm not though squid though mind you, around it,the other strange thing about this network is I have the 6 WAN connections vLAN tagged through a different network and am wirelessly routing through a separate network over about 800-900 meters all using these sweet little UniFi switches
adding in for now I am having issues with old netbios name resolution across vlan networks -
@sundarnet said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
now I am having issues with old netbios name resolution across vlan networks
Yah think? Now sure you think that is suppose to work across subnets - ever ;) its a broadcast, why should it or how could it cross L2s?
Windows solution to this was a wins server ;)
-
Pretty sure I got it to work without a WINS server
in the DNS Resolver I selected
Register DHCP leases in the DNS Resolver and
Register DHCP static mappings in the DNS Resolver
I also created host override for the host in question
now my normal windows drive mappings work without change -
that is not a netbios discovery, that is just dns working how it should.
Here I tried to connect to
\\testhostIt first tries dns query, with my search suffix (domain attached) to my dns. the testhost.local.lan, it gets back from dns NX.. So it then tries a NB broadcast for it..
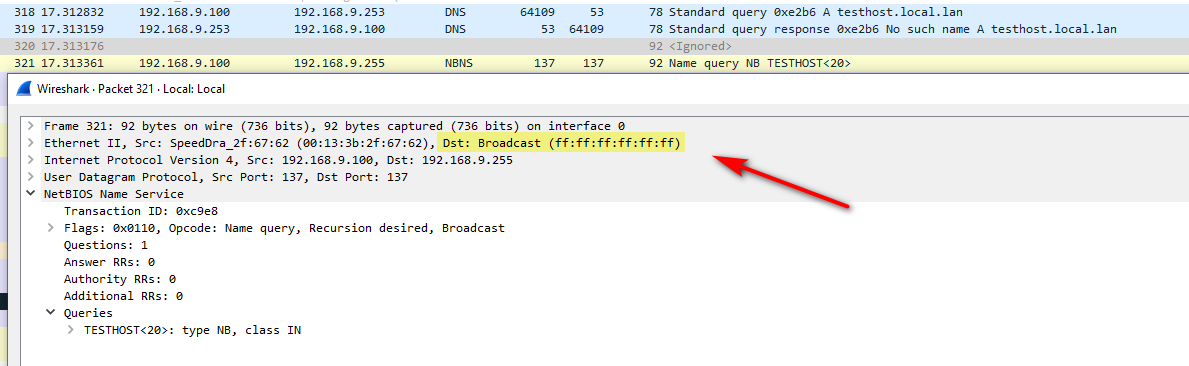
-
@johnpoz I like the explanation on that, I needed that earlier instead of this.
Yah think? Now sure you think that is suppose to work across subnets - ever ;) its a broadcast, why should it or how could it cross L2s?
Windows solution to this was a wins server ;)
;)
thanks for the help though
I still got it to work without a WINS server ;) -
As he demonstrated, it tries DNS first. After that fails it tries NETBIOS.
DNS works just fine across subnets.
-
it still works without a WINS server and the needed info would have been better than this comment! ;)
johnpoz LAYER 8 Global Moderator 7 days ago
@sundarnet said in Design frustrations with PFsense, VMWare, vLANs, Routing & LACP...:
now I am having issues with old netbios name resolution across vlan networksYah think? Now sure you think that is suppose to work across subnets - ever ;) its a broadcast, why should it or how could it cross L2s?
Windows solution to this was a wins server ;)
-
and Im also using Avahi to allow bonjour traffic across vLAN's for Airprint capabilities which works very nicely
-
Yeah dns works, that is not what you asked about - you asked about netbios resolution..
Which does NOT work across subnets, because it is a broadcast discovery. Was my response a bit snarky - maybe.. It was a stupid question to be honest, you used a term "netbios" which by its very nature tells you it wouldn't work across subnet without wins ;)
Where did you come up with the term to use, if you don't understand its meaning?
Have a read
https://www.techrepublic.com/article/how-netbios-name-resolution-really-works/