How to identify source ip through OpenVPN tun tunnel
-
I have configured a OpenVPN to connect the central oficce with pfSense and a remote site with a Wifi router as client in tun mode. The problem is that I would need identify the source ip of remote computer in local servers, but they are identified with the pfSense IP.
The scenario is as in the image shown bellow:

If the computer with remote ip 192.168.4.5 access to www 192.168.0.2, the ip of pfSense 192.168.0.1 appears as source ip in the apache acces log. And if the access by ssh or other service, the same thing happens.
Does anyone know if it is possible to get the source IP?
Regards.
Enrique. -
@enor said in How to identify source ip through OpenVPN tun tunnel:
The problem is that I would need identify the source ip of remote computer in local servers, but they are identified with the pfSense IP.
That's not the normal behaviour.
Normally pfSense only translate source IPs on interfaces with an associated upstream gateway.
So is there a gateway stated in the interface settings of 192.168.0.1?
What do your outbound NAT rules look like? -
@viragomann said in How to identify source ip through OpenVPN tun tunnel:
upstream gateway
Yes, I tried to simplify the image and omitted something that I thought was not important, but obviously I was wrong. Between pfSense and the server exists a layer 3 switch routing to a diferent network range.
I will try to show you in the next image:

pfSense have as gateway for LAN interface the ip 192.168.0.2, and a static route in the interface LAN for network 192.168.0.0/16 to GW 192.168.0.2.
I thought that while connections were routed, they would keep source ip.
Do you know what is the best way to fix it ?
Thanks. -
Again:
Is there a gateway stated in the LAN interface settings???
Show your outound NAT rules! -
Yes, the LAN interface has setting the switch IP 192.168.0.2 as gateway.
By other hand exist a route in the LAN interface from 192.168.0.0/16 to the GW IP 192.168.0.2.There is more ruler for other interfaces, but this is the nat rule for LAN:
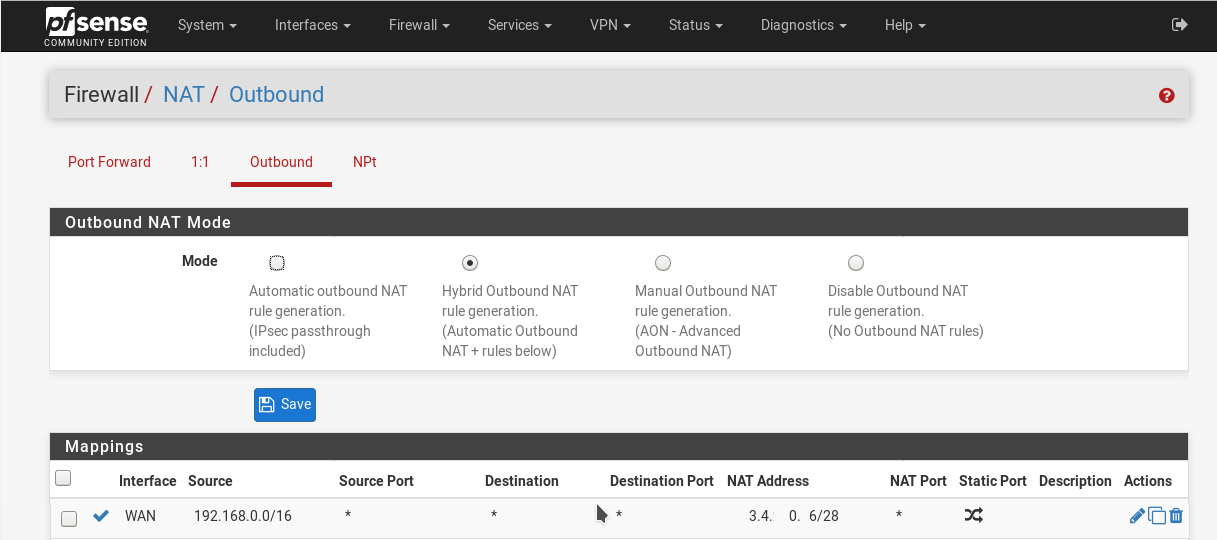
The pfSense WAN interface has a Public IP but in the image I only write the IP of the OpenVPN interface 10.0.0.1.
-
@enor said in How to identify source ip through OpenVPN tun tunnel:
Yes, the LAN interface has setting the switch IP 192.168.0.2 as gateway.
There shouldn't be set an upstream gateway for your goals!
The routing to the network behind the L3 switch is done by the static route you've already added.
Just set the LAN upstream GW to "none". This will delete the LAN outbound NAT rules. You don't need them in a routing environment.
-
@viragomann Great, this solve it in the pfSense network, but now the remote computers are identified with remote router IP 10.0.0.2. At least one part has been fixed.
-
@enor said in How to identify source ip through OpenVPN tun tunnel:
but now the remote computers are identified with remote router IP 10.0.0.2
Is that the virtual VPN IP?
In a site-to-site setup it shouldn't translate the source IP. -
@viragomann The virtual VPN IP of the pfSense in the site-to-site OpenVPN tunnel is 10.0.0.1 and the remote computers are identified with the IP of the OpenVPN client tunnel IP 10.0.0.2.
I think something is wrong in my OpenVPN client setting.
The file .ovpn that I used for the remote OpenVPN client setting is:dev tun persist-tun persist-key cipher AES-128-CBC auth SHA256 resolv-retry infinite proto udp remote vpn.mydomain.com 1194 nobind ifconfig 10.0.0.2 10.0.0.1 keepalive 10 60 ping-timer-rem comp-lzo adaptive route 192.168.1.0 255.255.255.0 <secret> ... -
That is not set by OpenVPN. That is set on the interface by the router. OpenVPN only provides the virtual interface which the router uses here.
Some non-professional routers do the translating by default. Maybe you can disable it. Look for settings named like "masquerading".