Captive Portal only shows authenticated users
-
I have not read in the online docs anywhere and this forum. I am not 100% sure if this is by design. I have one Mac setup to bypass the portal login page.
So what I am showing is that only authenticated users show up in the list, I would like to see all active users listed.
I thought I would be seeing two users, however I only see one even though both users are active and accessing the internet just fine!
So if a user mac bypasses the portal login that means that user will not show in the status list?
Am I missing something?

I did find something on the forum, kind of a workaround yet not 100% useful!
https://forum.netgate.com/topic/134048/captive-portal-status-users-not-showing/2https://www.netgate.com/docs/pfsense/captiveportal/captive-portal-troubleshooting.html
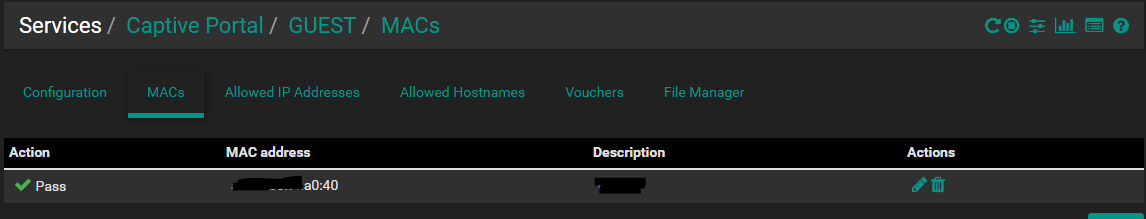
ipfw table all listIt does show a list of all mac's listed, however not all the associated IP's
--- table(cp_ifaces), set(0) --- em1.50 2100 445576 369047032 1562865062 --- table(guest_auth_up), set(0) --- 192.1.50.34/32 00:00:00:00:48:36 2002 2506 242108 1562865062 --- table(guest_host_ips), set(0) --- 192.1.50.1/32 0 8412 5118007 1562864776 --- table(guest_pipe_mac), set(0) --- 00:00:00:00:a0:40 any 2005 20776 19731461 1562865008 any 00:00:00:00:a0:40 2004 19874 3277981 1562864812 --- table(guest_auth_down), set(0) --- 192.1.50.34/32 2003 2506 2431949 1562864776 --- table(guest_allowed_up), set(0) --- -
BIOS Vendor: LENOVO Version: M05KT60A Release Date: Thu Jul 21 2016 Version 2.4.4-RELEASE-p3 (amd64) built on Wed May 15 18:53:44 EDT 2019 FreeBSD 11.2-RELEASE-p10 CPU Type Intel(R) Core(TM) i3-6100 CPU @ 3.70GHz Current: 740 MHz, Max: 3700 MHz 4 CPUs: 1 package(s) x 2 core(s) x 2 hardware threads AES-NI CPU Crypto: Yes (active) -
@tleadley said in Captive Portal only shows authenticated users:
I thought I would be seeing two users
A service who has its MAC address listed on the "MACs" page will no see the authentication process. Packets that match the MAC rule are just passed.
To be member of the connected user list you should connect using the Captive Login page.
The MACs page is more for automated devices like APs etc so they can access the Internet for their NTP (example) needs. These devices can't 'login" again a captive portal.
-
@Gertjan said in Captive Portal only shows authenticated users:
The MACs page is more for automated devices like APs etc so they can access the Internet for their NTP (example) needs. These devices can't 'login" again a captive portal.
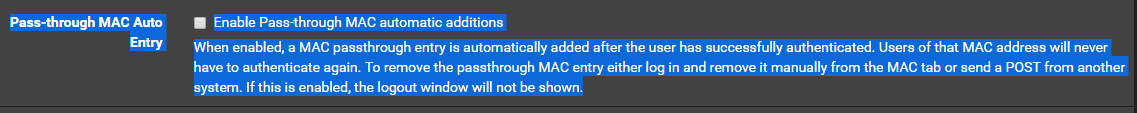
I get your argument and It makes absolute logical sense yet in the pfSense documentation and on the firewall itself states nothing of the sort for what the absolute purpose is, only what is does or the effect of it's use. this leaves this up to interpretation, so I am not sure I buy in to this completely. I am using Captive portal on an interface that is vlan aware and the captive portal is set for a vlan guest WiFi network.
So maybe this should be a feature request

-
That is completely different from adding a MAC address manually to the MAC address pass through.
When a user authenticates and that checkbox results in a MAC passthrough entry being automatically added, the captive portal process sees the authentication attempt and knows about the user.
When you just add a MAC passthrough to the table, the traffic is passed but there is no user login to be displayed.
-
@Derelict Like I said before it makes sense, I am thinking outside the box. I think it would be cool to see these devices show up, at the very least as an unauthenticated device or let the login show as the description you choose when you set up a mac manually.
Otherwsie you would have to be a bit of a slueth to find that device in a sea of possible hundreds of devices. There is no possible way to remember why for each mac address for every device I have done for every customer, on their networks.
I know it is a small thing, every small thing makes this product even better. I have already made a feature request.
-
@tleadley said in Captive Portal only shows authenticated users:
to find that device in a sea of possible hundreds of devices.
On a captive portal their might be devices (or actually users using these devices) that need to connect to the network that is set up as a captive portal, but don't want to be bothered by the 'manual, human based logging portal.
Hard to imagine that this could be 'many' devices. In that case, redo you network setup, and build (add) another network for these devices that need a semi permanent access using their MAC address.
Captive portals are "guest based", accepting unknown or non trusted devices that should have an Internet access. As said above, exceptions can be made so that your devices (trusted by you - not directly accessible to the network users), can bypass the html login portal page.
If you really need to accept a boatload of MAC's, then yes, you'll be handling this load manually.
-
This post is pointless if this argument points to rebuilding my network, how else are you going to get 2000 plus users on the same meshed Wifi guest network. I am not sure where your advice is coming from. This is a guest network setup so no mystery here, so if I have a conference center with an event your advice would lead me to believing I would require an astonishing 10 seperate network interfaces and SSID's...
Interesting

I would use the UniFi controller for this however it will not work the way I need it to without the USG device in addition to the controller appliance. I would have one interface to control and manage everything. Unifi FW and switches are glitchy and the cpative portal doesn't work as expected which is why I switched. pfSense can handle the throughput better. The captive portal on pfSense is rock solid when used with ubiquity AP's!
Except for one little asthetic that I could live without, it would be nice to see. That is the point
