Bogon flooding on my wan
-
ISP static ip to -> modem bridged to -> pfsense -> lan
Pfsense 2.5.0
I know that i can remove this from my log and i understand what "Block bogon networks" is but i'm just curious to understand why, i don't think it is normal to see so many times this ip on my log so i want to understand if it's my isp doing something wrong or what else..
Premise: 192.168.1.200 is part of a pool
on another location with a different ISP i have the same configuration but i never see bogon network on my wan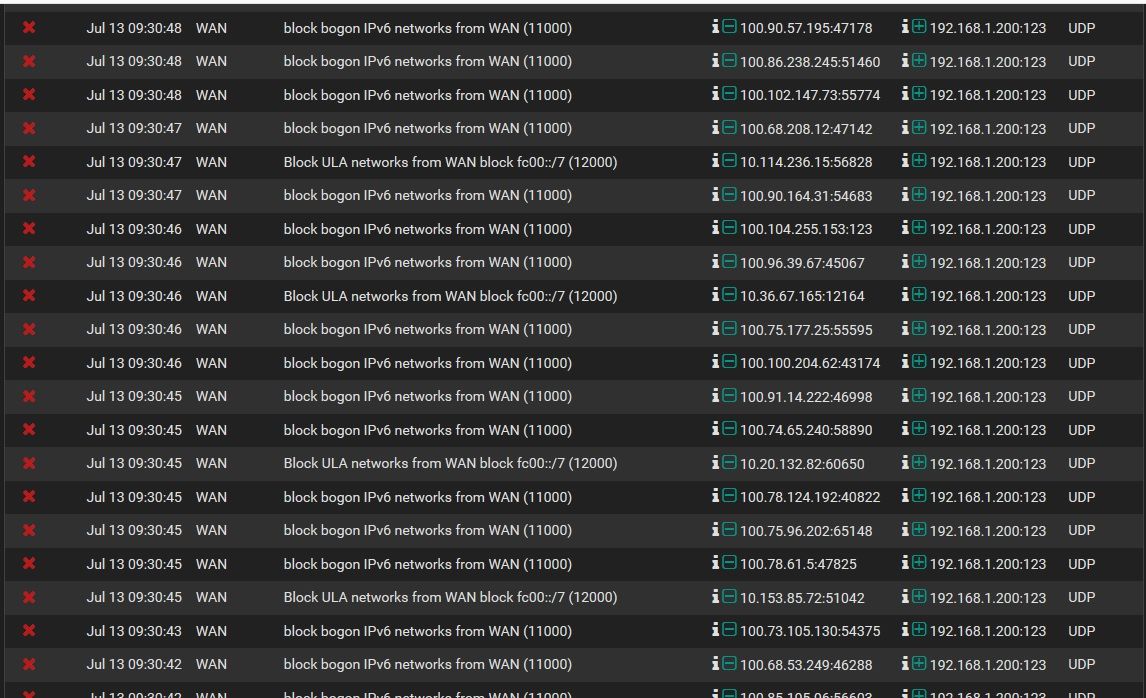
another thing, trivial, this is probably a little bug:
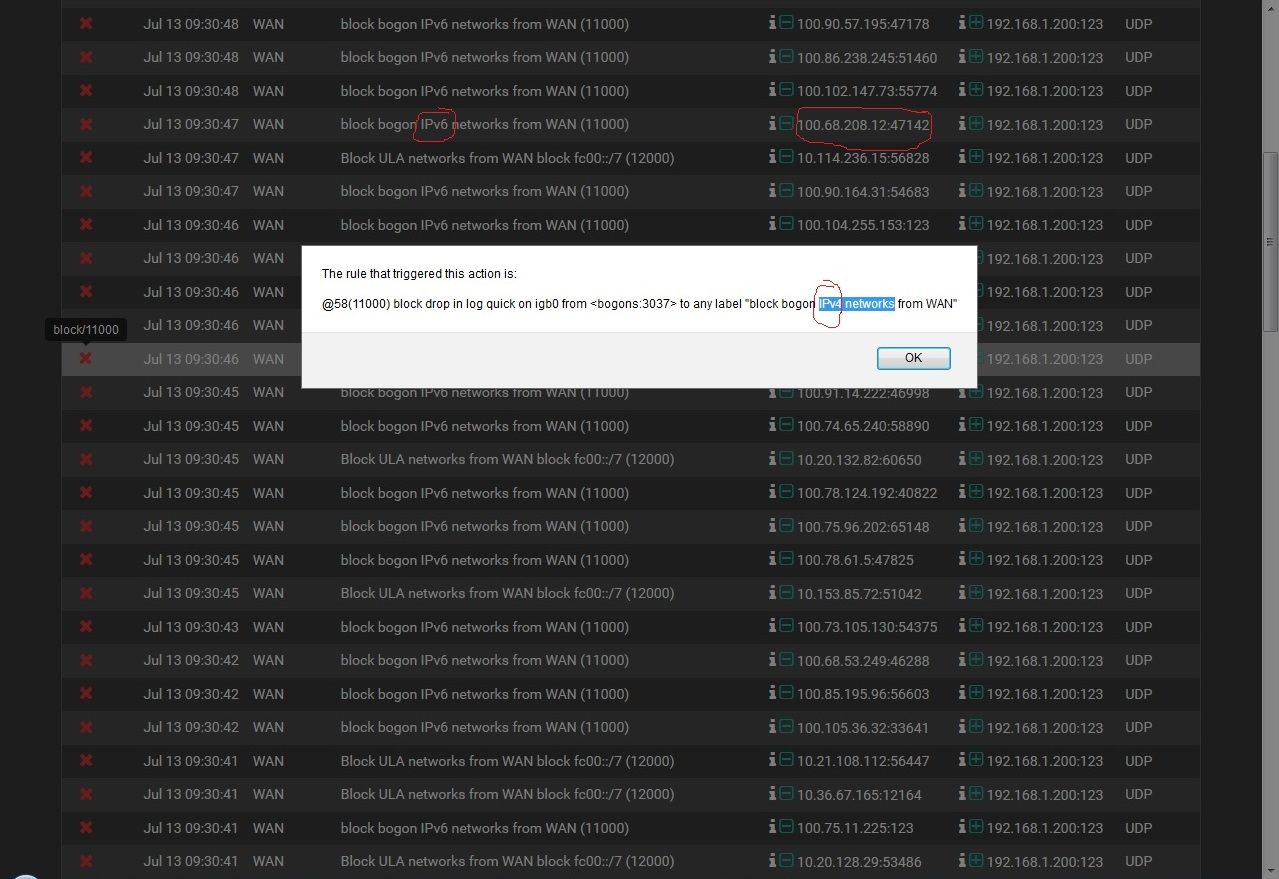
-
Hmm, well yeah odd that it's flagging those as IPv6! Probably better to open a thread in the developement section or just open a bug for that directly if it's easily replicable.
But those addresses all look legitimately blocked. Neither 10/8 private IPs or 100.64/10 CGN IPs should be arriving at your WAN.Steve
-
I moved this to 2.5 section... And you should mention exactly what snap your running, etc.
-
well, not a problem, the question was: why i have that many bogon ip on my wan, i don't think it's important which version of pfsense i have, the bug for 2.5 is irrilevant, i found it as a side effect of what is happening. i have already opened a bug on redmine for the 2.5
pfSense-CE-2.5.0-DEVELOPMENT-amd64-20190711-172 afaik previus version was doing the same as i have updated only some hours agoi think it's my ISP ..
C:\Users\Amministratore>tracert 100.75.96.202 Traccia instradamento verso 100.75.96.202 su un massimo di 30 punti di passaggio 1 11 ms 7 ms 11 ms 192.168.1.254 2 34 ms 32 ms 32 ms 10.5.3.98 3 31 ms 37 ms 31 ms 10.250.137.166 4 32 ms 32 ms 32 ms 10.251.155.186 5 52 ms 54 ms 52 ms 10.254.12.10 6 58 ms 52 ms 50 ms 10.250.132.9 7 83 ms 77 ms 79 ms 100.75.96.202 Traccia completata. -
i'm digging more stuff here,
on pfSense 2.4.4-p3
/etc/bogons contain only few lines,0.0.0.0/8 127.0.0.0/8 169.254.0.0/16 192.0.0.0/24 192.0.2.0/24 198.18.0.0/15 198.51.100.0/24 203.0.113.0/24 224.0.0.0/4 240.0.0.0/4/etc/bogonsv6 is empty
it seems like my pfsense 2.4.4 -RELEASE-p3 never downloaded bogons files from
https://files.pfsense.org/lists/fullbogons-ipv4.txt
and from
https://files.pfsense.org/lists/fullbogons-ipv6.txt
another bug?on pfSense 2.5.0-DEVELOPMENT
/etc/bogons is full of lines
/etc/bogonsv6 is full of linesi had to manually launch /etc/rc.update_bogons.sh to download the files
-
@kiokoman said in Bogon flooding on my wan:
i had to manually launch /etc/rc.update_bogons.sh to download the files
/etc/rc.update_bogons.sh is setup in a crontab so it runs every first of the month.
If, by any chance, at that moment, your uplink was on holiday/broke/disconnected/not feeling well/not set up correctly then a new try will be executed next month.Both files on my pfSense installs are dated : July 1, 2019.
-
@Gertjan
mmh it could be it, i have moved pfSense from an old machine to a VM in a server less tha one month ago
-
@Gertjan said in Bogon flooding on my wan:
If, by any chance, at that moment, your uplink was on holiday/broke/disconnected/not feeling well/not set up correctly then a new try will be executed next month.
That's why I recommend to customers to set this to daily instead of monthly. Monthly is too far apart. Especially in Germany the last RIPE IP4 blocks get shuffled or activated often (as there is not much remaining) and we already had two incidents of cable providers getting a new IP block formerly belonging to the bogon list. Had to debug multiple customer complaints to find out they were coming from a bogon-blocked IP -> after updating that was gone. So I'd recommend to reduce at least to weekly if not daily in general :)
-
I hope the guys that admin " files.pfsense.org " see this.
If all pfSense devices start grabbing these files one a day instead of ones a month, they better add some colong devices ;) -
I don't think there will be a problem - they state in the doc you can adjust
https://docs.netgate.com/pfsense/en/latest/firewall/show-bogons.html
The default update frequency is Monthly but it may also be set to Weekly or Daily.
So I take it they are prepared if "everyone" did it ;) Maybe not?
Quick glance at the update_bogons.sh looks like they check if the checkshum as changed before they actually download the full file. So its not like everyone is going to be downloading the full ipv6 bogon every day, etc. Unless it was actually updated. And even everyone changed their update to daily, it would be spread across the full 24 hours.. Not like every would be hitting the server at 0100 GMT or something ;)
Curious how often netgate updates their copies - looks like they were both just updated Tue Jul 16 08:50:01 2019 GMT
I personally don't even block them.. The default rule blocks all traffic anyway.. And only thing have forwarded is ntp as part of the pool.. And my plex, but that is behind cloudflare proxy now and limited to their source IPs. Bogon's are not routed by very nature.. So hits would have to come from your ISPs network, etc or forged source.. I don't see it real concern to be honest ;) Is it good practice to block sure - and if you had lots of services open to the public yeah you should prob block them.. But in the years I had the rule enabled - I never once saw a hit on them..