SSH Hardening question
-
Hi,
as we checked various hosts and the lab installations of firewalls against current recommendations, we had the 2.5 with following results:
# algorithm recommendations (for OpenSSH 7.9) | ssh2-enum-algos: | kex_algorithms: (2) | curve25519-sha256@libssh.org | diffie-hellman-group-exchange-sha256 -- [warn] using custom size modulus (possibly weak) -> remove | server_host_key_algorithms: (4) | rsa-sha2-512 | rsa-sha2-256 | ssh-rsa | ssh-ed25519 | encryption_algorithms: (6) | chacha20-poly1305@openssh.com | aes256-gcm@openssh.com | aes128-gcm@openssh.com | aes256-ctr | aes192-ctr | aes128-ctr | mac_algorithms: (6) | hmac-sha2-512-etm@openssh.com | hmac-sha2-256-etm@openssh.com | umac-128-etm@openssh.com -- [warn] using encrypt-and-MAC mode | hmac-sha2-512 -- [warn] using encrypt-and-MAC mode | hmac-sha2-256 -- [warn] using encrypt-and-MAC mode | umac-128@openssh.com -- [warn] using encrypt-and-MAC mode | compression_algorithms: (2) | none | zlib@openssh.comSo pretty good(!) per default but just wanting to question, if those MACs would hurt older clients much if they would be removed as per recommendation or if that would break things(TM) in a bad way. Also the KEX (DH GE with SHA256) is only possibly week, I'm assuming it has a strong modulus attached and I know that older clients often used it and behaved bad with only curve25519 left. Of course when dealing with a firewall, one could always say that things have to SOTA when dealing with your firewall and just up the ante ;)
Just wanting to get developer's take on that.
Greets
Jens -
We have refined that list before for security reasons, at the expense of some older clients. If you have some specific suggestions there, feel free to make a feature request or a PR.
-
You know what would be great feature - the ability to do check boxes on what ciphers and algo's you want to use.. Kind of like how the DSM on synology does it..
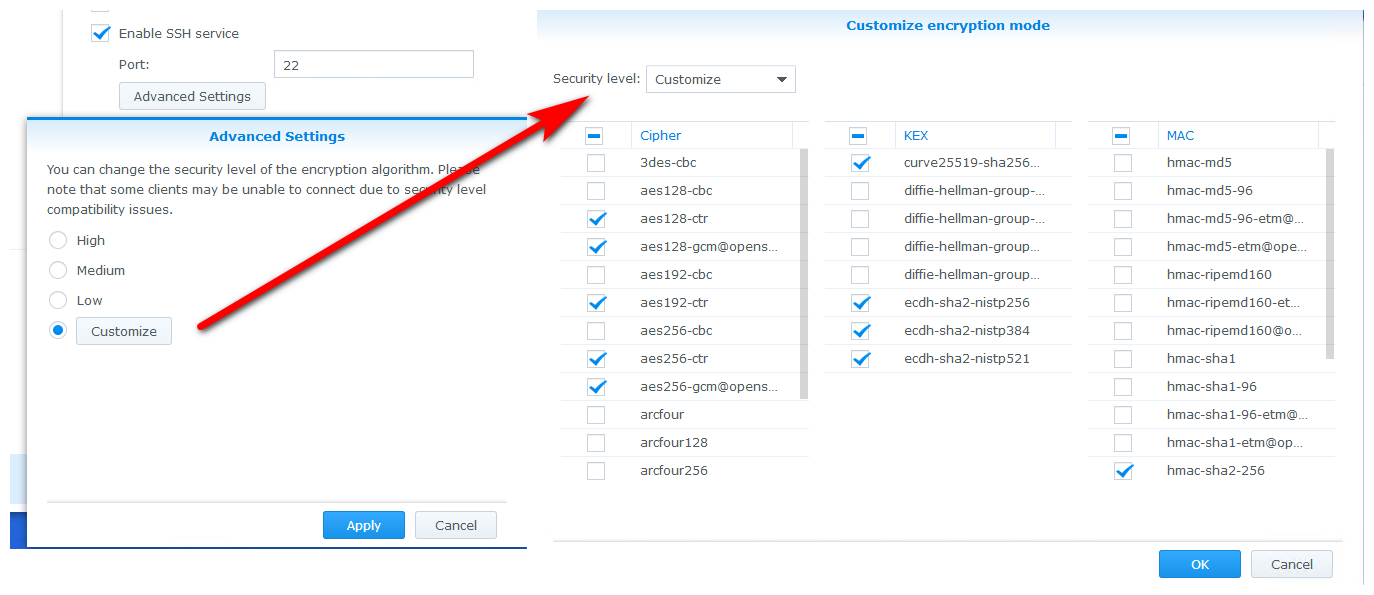
Something like this for the web interface https settings would be useful as well.