Firewall Feedback
-
@johnpoz said in Firewall Feedback:
heheheheeh Ping it from a client on your lan.. Your rules do not allow it.
Okay Johnpoz, I am getting your points, and no...you're correct!
rnollisuzs$ ping 192.168.1.1
PING 192.168.1.1 (192.168.1.1): 56 data bytes
Request timeout for icmp_seq 0
Request timeout for icmp_seq 1
Request timeout for icmp_seq 2
Request timeout for icmp_seq 3
Request timeout for icmp_seq 4
Request timeout for icmp_seq 5
Request timeout for icmp_seq 6
Request timeout for icmp_seq 7
Request timeout for icmp_seq 8
Request timeout for icmp_seq 9
Request timeout for icmp_seq 10
Request timeout for icmp_seq 11
Request timeout for icmp_seq 12
Request timeout for icmp_seq 13
^C
--- 192.168.1.1 ping statistics ---
15 packets transmitted, 0 packets received, 100.0% packet loss@johnpoz said in Firewall Feedback:
I personally do not get why users want to put in rules that are more than likely only cause them grief and extra work when something doesn't work
Well, as I had said, I was following the thread "Taming the Beasts...aka Suricata Blueprint." The goal was to make things easy for Suricata. I had planned VPN and figured I would add that later. I also run Plex but not often or since my pfSense box. Also, I am not really a gamer but could have guests who do, and it would be cool to accommodate in the safest way.
@johnpoz said in Firewall Feedback:
Or are the devices behind the firewall all under your control?
Yes, I have a Mikrotik behind the pfSense. LAN boss for clients/devices...I was even thinking how I could have a double gate when I am ready to set up VPN later. So, could I setup aliases for those you said I would be locking out? pfSense is WAN boss and I understand things have surely changed since the author crafted "Taming the Beasts"...that's what I thought when I saw the any any default rule but incorporate it though.
-
@NollipfSense said in Firewall Feedback:
I could have a double gate when I am ready to set up VPN later
huh? You just policy route out of pfsense for stuff you want or don't want to use your vpn.. Not sure what this taming the beast guide is - my initial thought if they told you to do what you have setup is just a giant facepalm ;)
-
@NollipfSense :
The "Taming the Beast" thread for Suricata is an old thread that was all about how to structure Suricata rules and suppression lists for maximizing detection of bad things with as few false positives as possible. Not really sure how that relates to what you are doing here with all those firewall rules. I'm with @johnpoz here, you are way over complicating your setup - especially if this is for a home network. -
try this
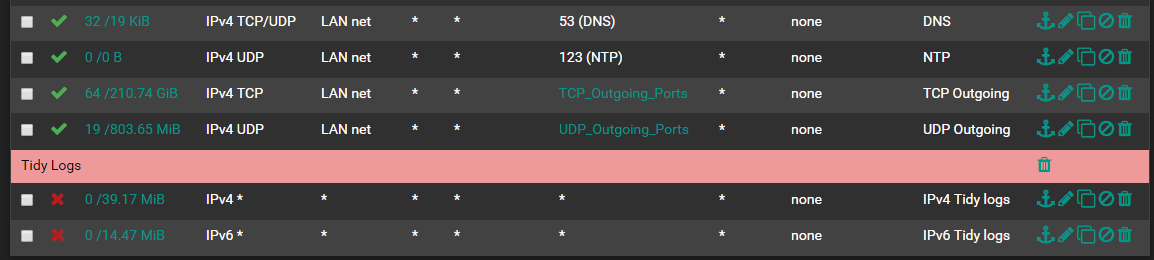
-
@jasonraymundo31 Thank you Jasonraymundo31 for responding...I had to laugh aloud...so clean...
-
@johnpoz Hey Johnpoz, this is how it is now...I understand what you were saying about the default any-any rule...I could not do without it as Internet radio breaks...I suspect it uses the lower UDP ports.
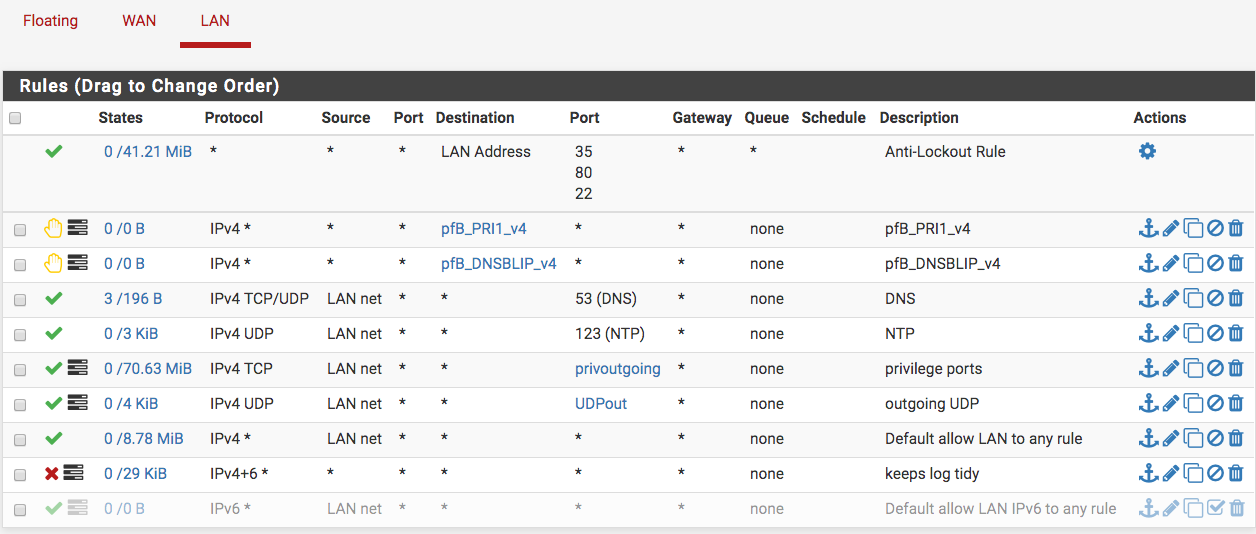
My double-gate idea I mentioned was about the obvious VPN gate at pfSense, then another gate at the Mikrotik...the fun part will be at the Mikrotik...seems doable though.
-
So a double nat? Yeah pointless ;) Or 2 firewalls inline with only your edge doing nat? Again pretty pointless and just added complexity and work and hassle for like zero benefit.
If your moving a shitton of traffic and you need a downstream/core router and possible firewall between your local networks.. Sure ok, then have a edge router/firewall... But in a home setup - its over complication and cost for no added value.
-
@bmeeks In the first part of that thread (Taming the Beasts), the author specified to create the firewall rules to make things easy...the second part was to structure Suricata rules and suppression lists for maximizing detection of bad things with as few false positives as possible. I'll be opening a thread with your section on the fourteen rules I had implemented. Lots of stuff had moved to pfBlockerNG too.
-
@johnpoz said in Firewall Feedback:
So a double nat? Yeah pointless ;) Or 2 firewalls inline with only your edge doing nat? Again pretty pointless and just added complexity and work and hassle for like zero benefit.
If your moving a shitton of traffic and you need a downstream/core router and possible firewall between your local networks.. Sure ok, then have a edge router/firewall... But in a home setup - its over complication and cost for no added value.
Well, right now it is double-natted...I'll turn off the Mikrotik nat rule though, and let the edge pfSense handle it. I have the pfBlockerNG and that by default added the nat. The thing is I was introduced to Mikrotik first and had for seven years before being introduced to pfSense late 2017. So, I just incorporated the two in my network...why throw away a good working kick-ass Mikrotik RB450G.
Yes, its way overkill...it is really recycling not too old equipment I had; so, cost already depreciated...the value to my home-office-lab network is tremendous and rival most small business, some medium-sized business network.
-
@NollipfSense said in Firewall Feedback:
why throw away a good working kick-ass Mikrotik RB450G.
Not saying you have to throw it away, but as a bump in your network is pointless, and just using electricity for no reason at all.. Be it 3w and only cost a $1 a month... Still just pointless..