Setting up LAN Bridge and VLANs
-
No, no, no. You want 802.1q.
This is a solved problem. It all works. Just configure it correctly.
untagged is untagged. It doesn't matter what VLAN it is. You can connect two untagged devices, both untagged on different VLANs. They will both be in the same broadcast domain. The only way the switches would know there is a mismatch is if they participate in something like Cisco Discovery Protocol (CDP) which is completely outside the scope of this conversation.
Tagged
Untagged
That's all there is.
-
I have decided to simplify the setup that I am using in order to better understand things. I am using my desktop which is running VirtualBox to allow me to create a virtual lab of sorts as I don't have any spare hardware to test this out on.
I have created a new install of pfSense that has 4 interfaces assigned to it. the first I set up as the WAN interface and is bridged through to my production pfSense box and gets a DHCP address (which is 17.2.39.239).
I then assigned the second interface as the LAN which is connected to an internal VirtualBox network which I called OPT1 in VirtualBox.
I then assigned the LAN interface an IP address of 192.168.1.1 and using a 24 netmask. I created a DHCP server on the LAN interface with a range of 192.168.1.2 - 192.168.1.10.
Finally, I added the following firewall rules: 1 on the WAN interface to allow for remote administration so that I could use my desktop to access the GUI. I created a second rule to allow all traffic to any destination on the LAN interface.
When I then set up a second VirtualBox VM as an Ubuntu 18.04 desktop and assigned it an internal VirtualBox network interface on OPT1 I was then able to connect to the pfSense machine and receive an IP address of 192.168.1.2 and have access to the internet.
I now want to replicate how my Ubiquiti NanoHD will being connected eventually, so I created a second Ubuntu VM and assigned it to the OPT2 VirtualBox network for its network interface and then went into pfSense and selected the third interface which is on the same VirtualBox Network. But how do I then allow this machine to be on the LAN network? I tried adding it as an interface and creating an allow all rule but still was not able to connect. I then created a bridge which did give it an IP of 192.168.1.3 but I could not ping anything or access the internet.
Eventually I want to have my 3 NanoHD access-points connected to the same LAN network as all my other computers so that they can be controlled by an Unifi Controller on the 17.2.39.1 network but I want to then make different WiFi networks and have them either as part of the 17.2.39.1 network or on other isolated networks such as guest WiFi on 17.2.38.1 with only specific cross-traffic allowed such as allowing users on the guest WiFi to access my media server which is at 17.2.39.121 and I have a DNS override setup so that you can access it from media.local.network
I have been reading all day and watching videos about VLANs and how they work with pfSense, Unifi and D-link but I am clearly missing something, in the chain and so I have tried this setup to remove the switch from the equation to see if I can do it that way as I have enough interfaces on the pfSense box that I will use in production.
I also have an unmanaged D-Link switch if I that would help eliminate the need to VLAN tag things on the other managed switch and just have it pass things through between the Unifi and pfSense.
-
If you want it on LAN then you have to make a VM bridge to the LAN interface and put the VM interfaces on that network.
You should not be removing the switch from the equation you should be embracing the switch since it is the key to everything you want to do.
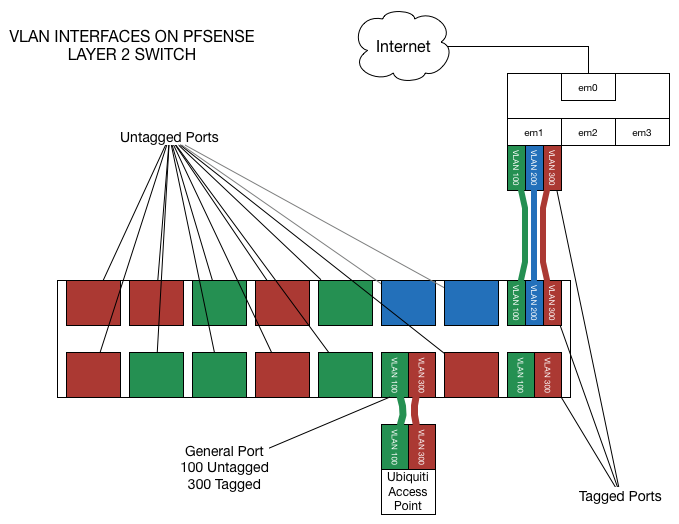
My advice is to slow down, stop trying to do everything at once, and make a simple pfSense VLAN interface on, say, VLAN 20, enable it, add the rules, enable DHCP.
Then put a tagged port on VLAN 20 on the switch and connect it to pfSense.
Then make an untagged port on vlan 20 on the switch and connect a laptop to it.
It will work.
Then worry about adding more VLAN interfaces, APs, etc. Do every step and test along the way.
-
I started this morning with a fresh mind and kept things simple. Here is what I did.
I added the spare interface on my main server into the pfSense VM so that pfSense could now see and use that interface. I then added it to pfSense under interface assignments and called it WIFI. I enabled it and did not assign an IP address to it. Next, I created a bridge between the WIFI interface and the LAN interface and called it BRIDGEDLAN. I then went over to the firewall and created 2 rules. One for the WIFI and one for the BRIDGEDLAN to allow all traffic through.
Once this was done my Unifi controller was able to see my wifi access point that I had plugged into the WIFI interface on the back of the server. I then modified my wifi networks so that my wifi that is plugged into the switch will only serve the normal wifi SSIDs which are PrivateWIFI and GuestWIFI. I then created 2 new SSIDs and assigned them only to the newly connected AP and called them TESTWIFIPrivate and TESTWIFIPublic. On the Public WIFI, I assigned a VLAN of 20.
Going back to pfSense I created a VLAN of 20 and assigned it as an interface (called GUESTWIFI) with an IP of 17.2.38.1 (my main network is on 17.2.39.1) and a 24 netmask. Next was to create the DHCP server of 17.2.38.2 - 17.2.38.10 and apply the changes.
Finally, I created 2 rules for the GUSTWIFI one blocking traffic to BRIDGELAN and the other allowing traffic to not BRIDGEDLAN.
When I connect my tablet to TESTWIFIPrivate everything works perfectly I an on the same network as the other devices and I can access internal resources. However, when I connect to the TETWIFIGuest I do get the right IP address from the DHCP of 17.2.38.2 but I cannot access the internet. I expectedly cannot access local resources which is correct as I will only be allowing one resource though after this first part is working.
The resrouse I will be passing through is a media server that has an entry on the pfSense as a DNS override to send the URL of media.local.domain to a nginx reverse proxy server so that I can hide the port numbers and used Lets Encrypt SSL certs. Any help on this next step is also appreciated.
By removing the switch and keeping it simple I have made a lot of progress, I will have to do more learning and research to make the switch part work after this setup is working so i can control the variables at play.
-
Why and the F would you create a bridge on pfsense for different interfaces as a VM? That is just utterly BORKED!!
There would be zero reason to ever do such a thing.. All the interfaces are virtual - if you want multiple vms to be on specific L2, you just connect them to the same vswitch port group.
And you sure and the F should not be using pfsense bridge on a vm to connect different physical ports... Just do that on your switch..
-
The reason I bridged the LAN and the WIFI interface is so that the Unifi AP which is a NanoHD can communicate to the Unifi Controller on the LAN network. I am in the process of learning and testing out using VLANs to segregate a Guest WiFi network and I had a spare NIC on the server that hosts my current pfSense setup.
I am running my pfSense in a VM so that I can leverage the power of the server for other things as pfSense takes very little resources to run, and because of the hypervisor (Proxmox) layer I decided that instead of passing the entire NIC to pfSense I would create virtual interfaces for pfSense to use that would be linked to a physical card, that way I did not have to have more cards and unused ports in the machine.
The only VMs that are running that are related to this thread is the pfSense VM and the Unifi Controller VM which each have their own ports because I wanted to separate pfSense from the rest of the LAN network. The Unifi Controller has a virtual NIC assigned to it what goes to a trunked (LACP) set of NICs that it shares with other VMs on the same server. I have been running this setup for the better part of 2 years without any negative impacts or issues. This is a home-based setup that is more my playground that a production business environment.
I believe the problem I am having with the internet on the GUESTWIFI is coming down to firewall rules and or configuration on how pfSense handles DNS lookups and also the configuration of my multiple gateways.
-
Again there is ZERO reason to creating any bridges in pfsense..
I ran pfsense for years on esxi, and run unifi AP...
All that is required here is tag correctly the vlans on your switch..
If you want tags to to be passed to pfsense then your vswitch in esxi vlan id needs to be set to 4095. If you don't want pfsense to handle the tags then do them on your port groups on your vswitches. And just connect new vnics on you pfsense to these different portgroups.
-
I tried removing the bridge between the WIFI interface and the LAN interface and it resulted in no internet to my tablet that is connected to the TESTWIFIPrivate.
Ideally, I want to plug in 3 NanoHD APs and have them use the addresses of 17.2.39.21 - 23. Their controller would be on 17.2.39.101. Then I want to create 4 types of networks in Unifi, 1 for my use that would be identical to a wired LAN connection but over WIFI. The second for my Roommate who would have access to things like printers and media server. Another for my significant other who would have the same access as the Roommate network plus things like shared storage and the NVR. The final network would be for guests that would only have access to the internet.
I have tried before to use VLANs in pfSense that is connected to a managed switch where I also configured (or thought I did) the appropriate VLANs and the APs are connected to that switch. I was not able to get things working so I simplified the setup.
I connected one AP to pfSense and setup the VLAN under Unifi for the Wireless SSID and then made the VLAN in pfSense and i was able to not only control the AP though Unifi though when connecting to the Guest WIFI I get an appropriate IP.
I am only aware of 2 ways with Unifi APs to control guest access and that is either through VLANs or the Captive Portal. but because I want to have multiple SSIDs applied to various networks VLANs seemed to be the best option.
-
I was able to get internet access on the guest wifi now, I needed to add the appropriate outbound routing information for the 17.2.37.1 network. I also had to change from 17.2.38.1 to 17.2.37.1 as the 38 network was in use by VPN service. I also have to create the needed rules under guest wifi in the correct order to allow only traffic on the internet and not anything else unless specified.
So I do have VLANs working and I did not create any additional networks in Unifi I simply told the Guest SSID to use a VLAN which keeps things a little simpler, now to figure out my D-Link switch issue. Though I may just plug in a dummy switch to see if that works and go that route, that would, however, limit me to only placing the APs in the office vs anywhere in the house.
-
@Astraea said in Setting up LAN Bridge and VLANs:
I was not able to get things working so I simplified the setup.
Not sure how you came up with that.. And have no idea what your doing in the controller for vlans... I run multiple vlans on my AP, and have zero setup in the controller about vlans.. Your not running a USG..
The onlything required for vlans on your AP is setting the vlan ID.
As to your outbound routing??? Do you mean policy routing out some gateway? That has ZERO to do with vlans - ZERO!!!
-
Under Firewall -> Outbound -> NAT I am using Manual Outbound NAT as I have a VPN client setup on pfSense to tunnel all my traffic other than a few server machines through the VPN tunnel. I also run 2 external IP addresses, 1 is static for said servers and the other is dynamic and is used by the VPN client to crated the tunnel.
So I needed to create an ANY map and a ISAKMP map for both the static and dynamic IP as well as the VPN tunnel. Once I did that I was able to browse the web from the guest WIFI.
I have noticed one final configuration issue and that is if I use a URL to access a local resource say mail.local.domain I can access that but if I type the IP of that same machine in that gets blocked. How do I filter DNS searches so that they can only access approved internal resources by name or IP?
As for the Unifi Controller, the only changes I have made are the added SSIDs and one of them contains settings for the VLAN. I am only running the Unifi Controller and the 3 APs, no other Unifi equipment.
-
I contacted D-Link customer support and they walked me through the configuration on the DGS-1100-24 switch, for others it is a B2 hardware revision. I now have the AP connected to the switch with the switch connected to the LAN interface of pfSense, no more bridge or additional outbound NAT settings required now. Here is how it is configured now.
pfSense LAN interface to switch and from the switch to AP. the AP SSID for the guest wireless has been set to use VLAN 20 and a VLAN was created on pfSense of 20 and assigned to the LAN interface. I made an allow all rule for the VLAN network and have DHCP configured and I am able to access the internet and local resources.
I will create a thread under firewall rules for the next part of this configuration.
Thanks to both Derelict and Johnpoz for your help, guidance and patience as I am new to VLANs.