Suricata Not Blocking legacy mode
-
@wperes said in Suricata Not Blocking legacy mode:
@bmeeks said in Suricata Not Blocking legacy mode:
You are doing something wrong or else you have an actual configuration that is different from what you think you have.
The problem was that a custom rule was in drop in the legacy_mode, but have be reject, drop is only inline_mode.
Thanks Bill.
Actually, for Legacy Mode, the action verb should be ALERT. DROP will work when using the special Suricata option of "block on DROPS only" when Legacy Mode is enabled. However, you are correct that typically DROP and REJECT are associated with Inline IPS Mode.
-
@bmeeks said in Suricata Not Blocking legacy mode:
Here are some screenshots from my test virtual machine. Suricata is configured to run on the WAN interface and set to use Legacy Blocking Mode. I scanned the Suricata VM's WAN IP address from another Kali Linux virtual machine. The Emerging-Scan rules were enabled on the Suricata machine.
Here are the alerts recorded from an
nmapscan from the Kali Linux VM. The IP of the Kali machine is 192.168.10.21, and the Suricata firewall IP is 192.168.10.124: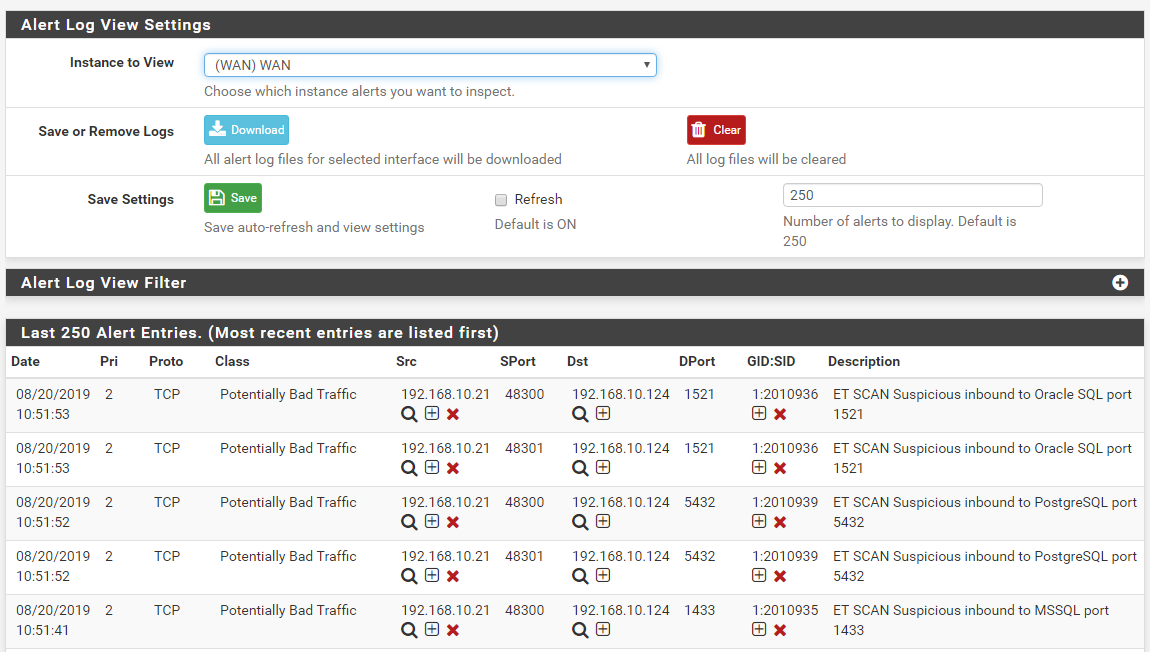
And here is the resulting block of the Kali Linux machine's IP address:
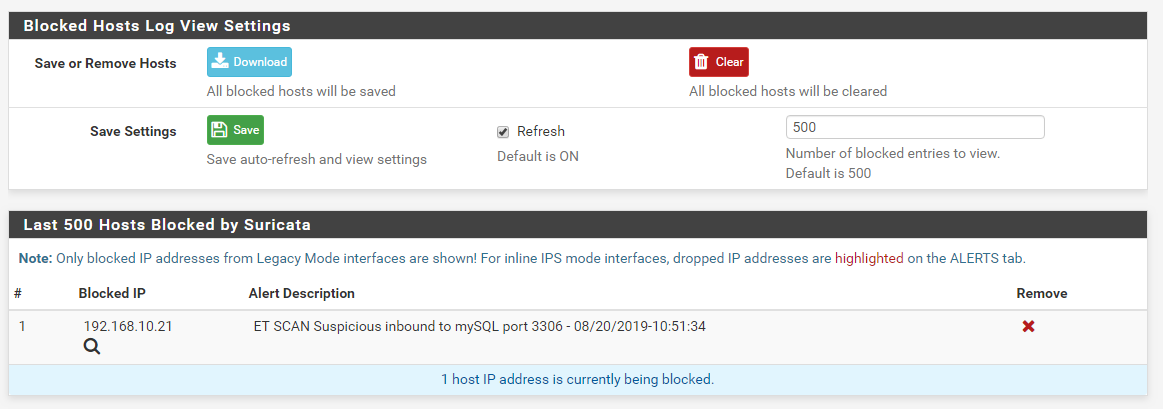
I installed the Suricata package fresh on the test virtual machine this morning immediately after reading your post. The times are for the U.S. Eastern Time Zone (where I live).
Hi Bill,
You use ET-SCAN rules to test, it works. But when you select ET-MALWARE or ET-TROJAN, it's not working.
no ip can be blocked. because src ip (in passlist) to dst ip (not in passlist) can not be blocked. -
@everfree :
There is no difference in the Suricata binary code that is triggered because you select different rules. If the code blocks for one set of rules, it will block for another set of rules if those rules also properly trigger. Do you think Suricata examines which rule set you have enabled and then randomly decides not to block for one of them?If you are not getting blocks from a given rule (or rule category) then that rule is either not triggering, or if you are using Inline IPS Mode or Legacy Mode with "block DROPs only" enabled, the action keyword is something other than DROP.
Also understand that when using Inline IPS Mode the ALERTS tab display is different and the BLOCKED tab has no function at all. For Inline IPS Mode, rule alerts that have resulted in dropped traffic will be shown highlighted in red. The BLOCKED tab will be empty because that subsystem is not used with Inline IPS Mode operation.
Suricata's operation with regards to blocking traffic is quite different depending on which of the three operating modes are selected: 1) Legacy Mode; 2) Legacy Mode using block DROPs only; or 3) Inline IPS Mode. Based on all of the questions you have submitted thus far, it appears to me you are confusing the various operating modes and what will be displayed in terms of blocks or drops for each mode.
-
@bmeeks said in Suricata Not Blocking legacy mode:
Legacy Mode with "block DROPs only" enabled,
I sure that Legacy Mode with "block DROPs only" disabled
src 163.22.0.0/16 (in my passlist),dst 158.85.63.185 (not in my passlist)
-
@everfree said in Suricata Not Blocking legacy mode:
@bmeeks said in Suricata Not Blocking legacy mode:
Legacy Mode with "block DROPs only" enabled,

I sure that Legacy Mode with "block DROPs only" disabled
So if you have Legacy Mode disabled, then you have to use Inline IPS Mode. If you use Inline IPS Mode you must manually change rule actions to DROP for any "blocks" to happen. You can do that either via the icons on the ALERTS or RULES tabs, or you can use the features on the SID MGMT tab to change a specific GID:SID to DROP or you can change an entire category to DROP using SID MGMT features.
There are several Sticky Posts at the top of this forum that describe how the various Suricata blocking mode work and how to configure them.
Here is one link: https://forum.netgate.com/topic/119237/about-the-new-block-on-drops-only-option-in-suricata-4-0-0/12.
Here is how to use SID MGMT: https://forum.netgate.com/topic/128480/how-automatic-sid-management-and-user-rule-overrides-work-in-snort-and-suricata.
Here is one that describes Pass List operation: https://forum.netgate.com/topic/119238/about-pass-lists-in-suricata.
-
I use Legacy Mode block for 2 years, it works, i can't sure what version let the problem occurred.
I only say the version have bug, I hope you check by check, I have bad English, I don't know give you more details. Dst is not have any block icon in block mode, it's strange. I have two suricata IPS, it have the same problem. one is 2 years before, others is the new machine.
thanks.
Ming-Chang Cheng.
-
@everfree said in Suricata Not Blocking legacy mode:
I use Legacy Mode block for 2 years, it works, i can't sure what version let the problem occurred.
I only say the version have bug, I hope you check by check, I have bad English, I don't know give you more details. Dst is not have any block icon in block mode, it's strange. I have two suricata IPS, it have the same problem. one is 2 years before, others is the new machine.
thanks.
Ming-Chang Cheng.
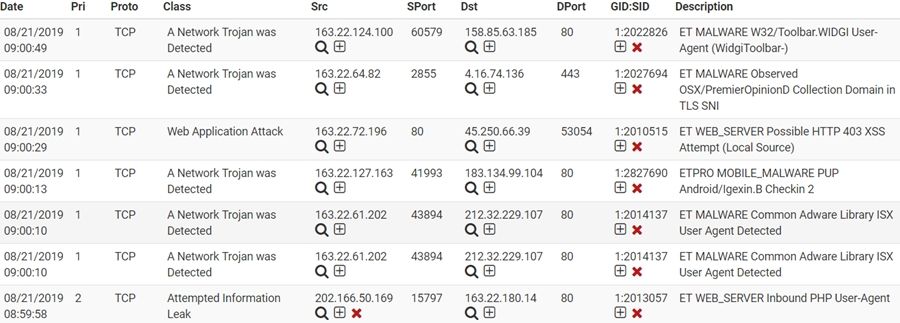
Looking at your last screen capture, it appears to me that you have blocking set to SRC IP only. I say that because you have the red X "unblock" icon showing for Source IP addresses that are not in your large Pass List network (I recall you said 163.22.0.0/16 was in your Pass List). For all of the ET MALWARE and ET MOBILE_MALWARE rules I see in your screen capture, the SRC IP is in your Pass List, so no block. However, for one of the ET WEB_SERVER rules (the last one shown), the SRC IP was 202.166.50.169 and that IP is showing as currently blocked (it has the red X icon).
I will fire up my test virtual machine again and double-check that blocking of DST IP addresses works.
-
yes, 202.166.50.169 is like ET-SCAN, it's inbound direction rules, ET-Trojan is outbound direction rules, I very sure block mode i select block both , so i don't know why 158.85.63.185 and others dst is not blocked.
-
@everfree said in Suricata Not Blocking legacy mode:
yes, 202.166.50.169 is like ET-SCAN, it's inbound direction rules, ET-Trojan is outbound direction rules, I very sure block mode i select block both , so id don't know why 158.85.63.185 and others dst is not blocked.
Go to the LOGS VIEW tab and select the interface where you posted the screen captures from. I assume it is maybe your WAN interface. If not, use whatever interface the earlier posted screen capture is from.
Open the
suricata.logfile and find this line:20/8/2019 -- 21:54:37 - <Info> -- alert-pf output initialized, pf-table=snort2c block-ip=both kill-state=on block-drops-only=offThis will display the startup cofiguration of the custom alert-pf blocking plugin. Post back here with what it says. The line above is from my test virtual machine with Suricata installed on it.
-
I just got these blocks in my test virtual machine. Notice that it blocked the DST IP on the WAN. The IP shown happens to be the Link-Local IP, but it was the destination address of the packet that triggered the rule. I am in the U.S. Eastern Time Zone, so my dates and times are obviously different than yours (by an entire day almost).
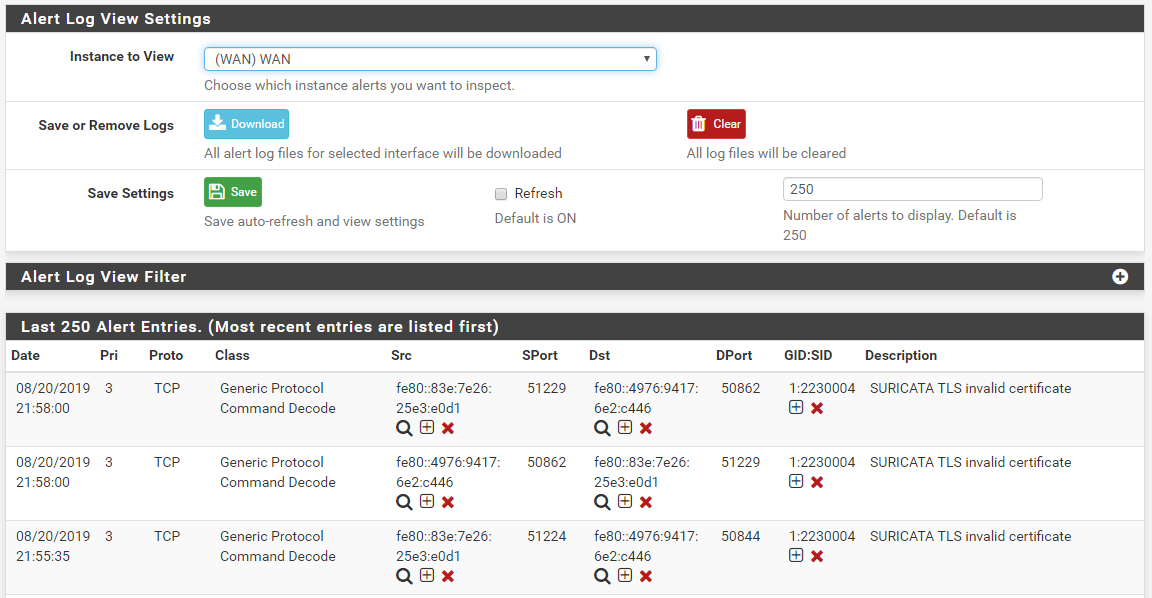
and here is the BLOCKS tab showing that blocked destination IP address along with the source IP.
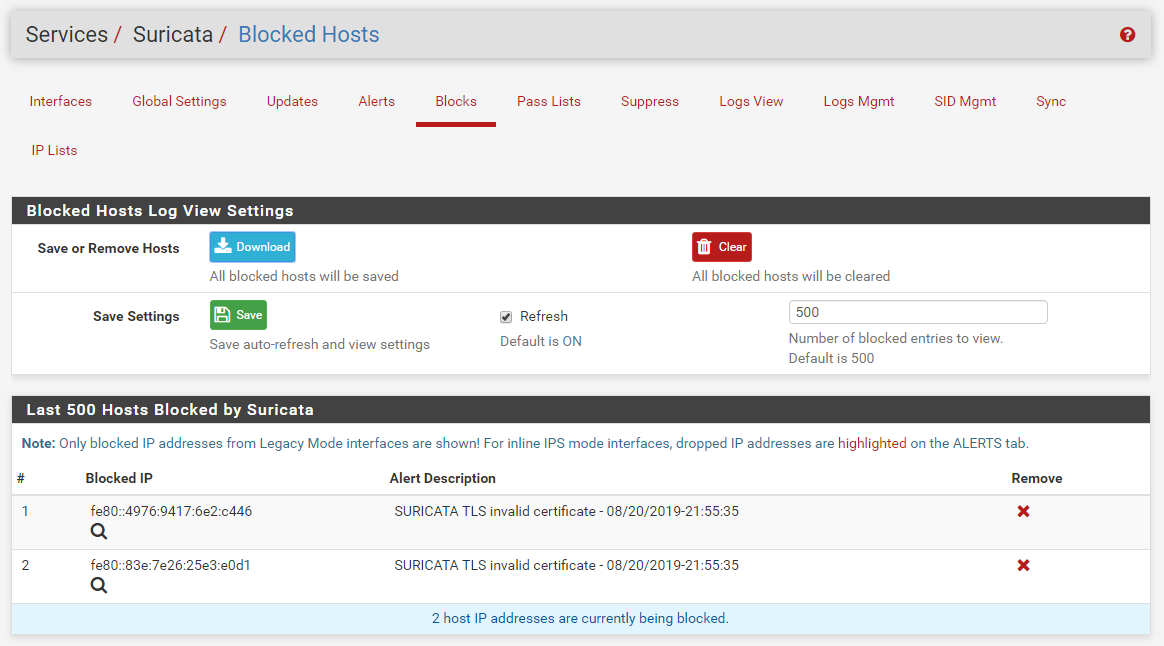
So from this I have to conclude the code is working as it should. There has to be something astray in your configuration that you are overlooking.
-
20/8/2019 -- 13:15:06 - <Info> -- alert-pf output initialized, pf-table=snort2c block-ip=both kill-state=on block-drops-only=off -
@everfree said in Suricata Not Blocking legacy mode:
20/8/2019 -- 13:15:06 - <Info> -- alert-pf output initialized, pf-table=snort2c block-ip=both kill-state=on block-drops-only=offHave you modified anything in your HOME_NET or EXTERNAL_NET variables? Have you checked for any duplicate Suricata processes? I would certainly first check for a duplicate process using this shell command:
ps -ax | grep suricataYou should see only a single running instance of Suricata for each configured interface. If you see any duplicate processes, you need to stop all Suricata processes in the GUI, open a command-line shell and repeat the above command to see if any Suricata process is still running. If you see one, kill it with this shell command:
kill -9 <pid>where <pid> is the process ID of the remaining Suricata process. At this point I don't know what else to suggest. The Suricata code is working for me, and I installed it fresh on this VMware virtual machine this morning (it is now 10:12 PM in the evening here). As you can see in my screen shots, the blocking is working for both directions (source and destination IPs). There is nothing in Suricata that would change simply based on the rules category.
-
@bmeeks If i don't select any passlist, My IPS show the same screen.
-
@everfree said in Suricata Not Blocking legacy mode:
@bmeeks If i don't select any passlist, My IPS show the same screen.
Just making sure you realize that anytime you change the Pass List or the blocking mode, you must restart Suricata on that interface in order for the change to become effective. Suricata only reads its configuration at startup. It does not "live update" any configuration setting. The only "live update" it can do is reload the rules.
-
And just to be complete, my virtual machine just recorded these IPv4 DST IP blocks:
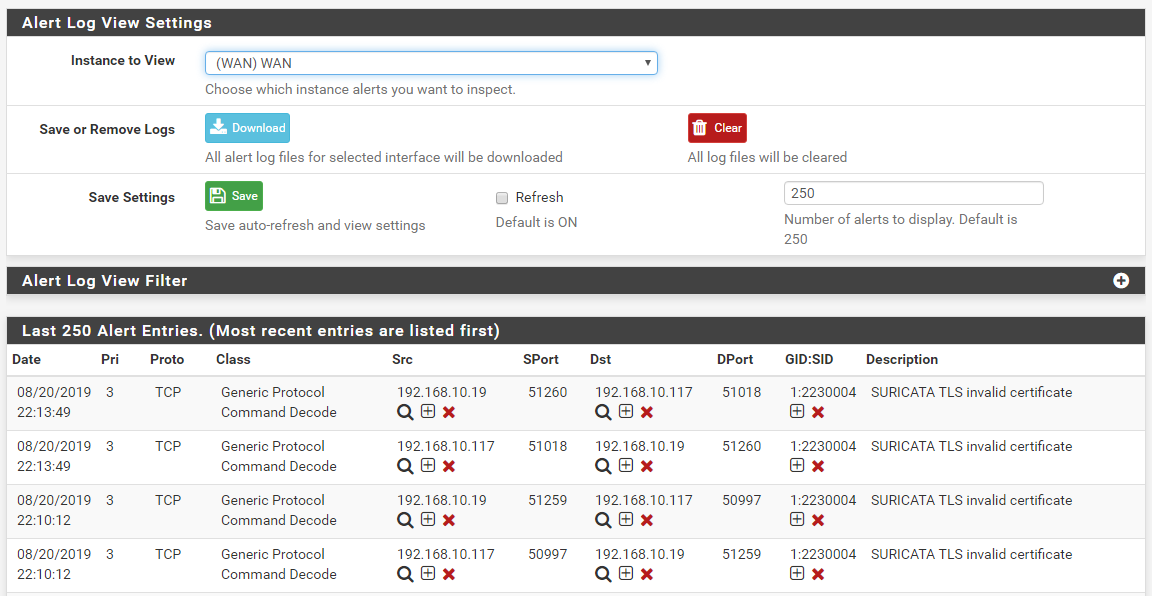
So it's not just IPv6 addresses that block, the IPv4 addresses are blocking as well. Since Legacy Mode puts the interface in promiscuous mode, it is seeing all of my local LAN traffic on the VM's WAN interface because the WAN of this virtual machine is connected to my LAN. -
when i remove my passlist, it show below...
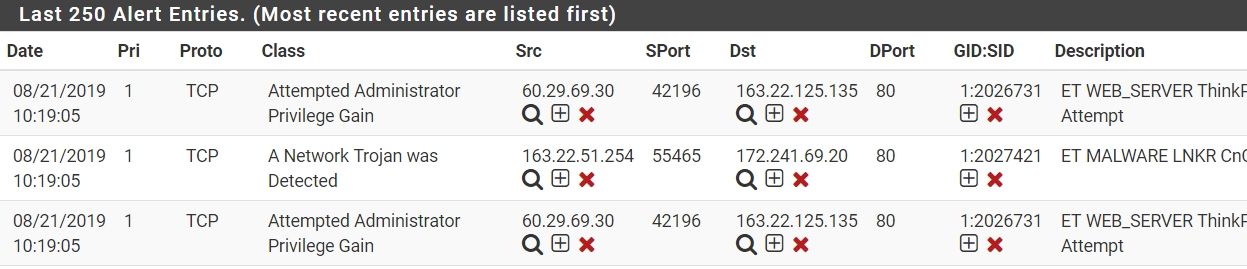
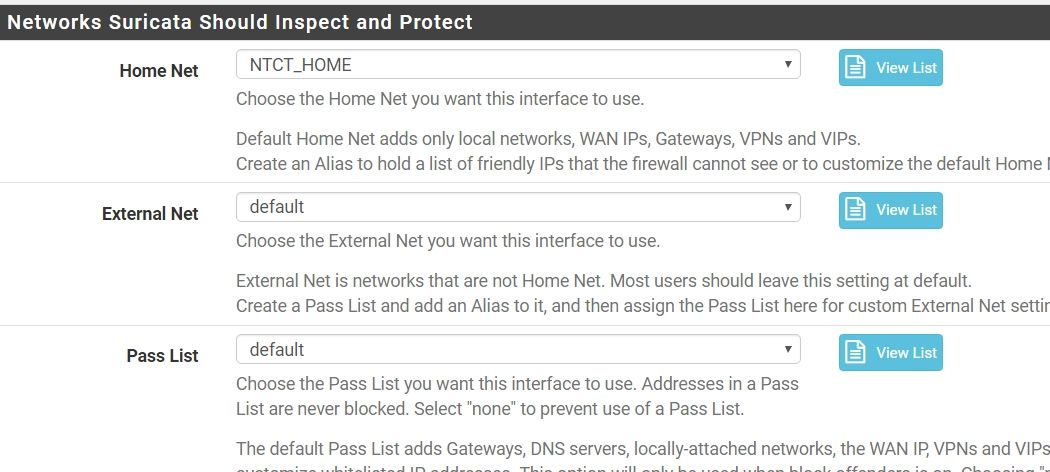
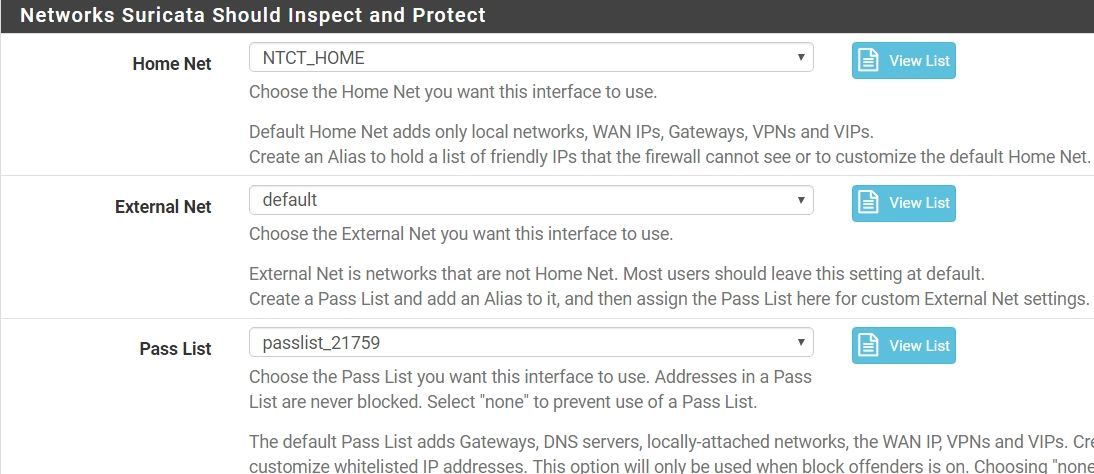
-
@everfree said in Suricata Not Blocking legacy mode:
when i remove my passlist, it show below...


Then your Pass List is too broad. It is whitelisting more IP address space than you think. The default Pass List will include your WAN IP address (just the actual IP, not the whole subnet), your LAN subnet, your DNS server IPs (if defined on the firewall setup), your WAN gateway IP, any VPN addresses and any Virtual IP addresses.
You need to examine the actual contents of the Pass List you had assigned to see what's up. I suspect a subnet is defined too large and is thus adding a lot of extra unintended IP space to the Pass List. Click the View List button beside Pass List to see what addresses are in the default list, then assign your custom Pass List and click View List for it to see what's different.
I think your last screen shot proves what I said several posts earlier. Your configuration is not exactly how you believed it to be. In this case, I suspect your Pass List is overly broad and thus whitelisting a large chunk of IP space (and therefore you get no blocks on those IPs as is proper when an IP address is covered by a Pass List entry).
-
I modify my passlist it only
127.0.0.1/32 163.22.0.0/16 ::1/128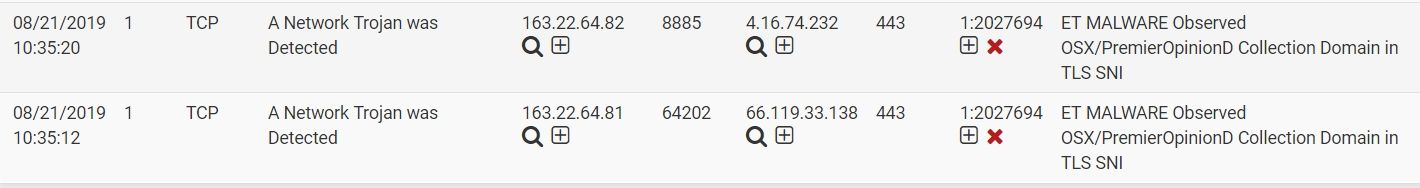
it still not works. -
@everfree said in Suricata Not Blocking legacy mode:
I modify my passlist it only
127.0.0.1/32 163.22.0.0/16 ::1/128
it still not works.Post the content of your Pass List. Assign it on the INTERFACE SETTINGS tab and then click the View List button. Paste the content of that modal dialog back here to the forum. Better yet, post the content of both the default list and your custom list so we can examine the differences.
Since it works when you set the Pass List to "default", that means the underlying binary code works fine. Something is incorrect within your custom Pass List. At least that is the best theory I have.
-
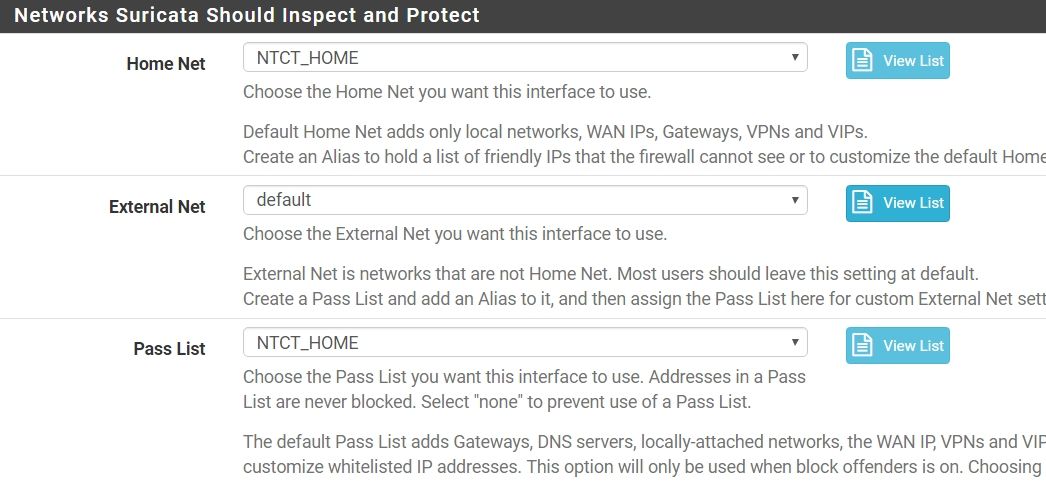
NTCT_HOME127.0.0.1/32 163.22.0.0/16 ::1/128default
!127.0.0.1/32 !163.22.0.0/16 !::1/128