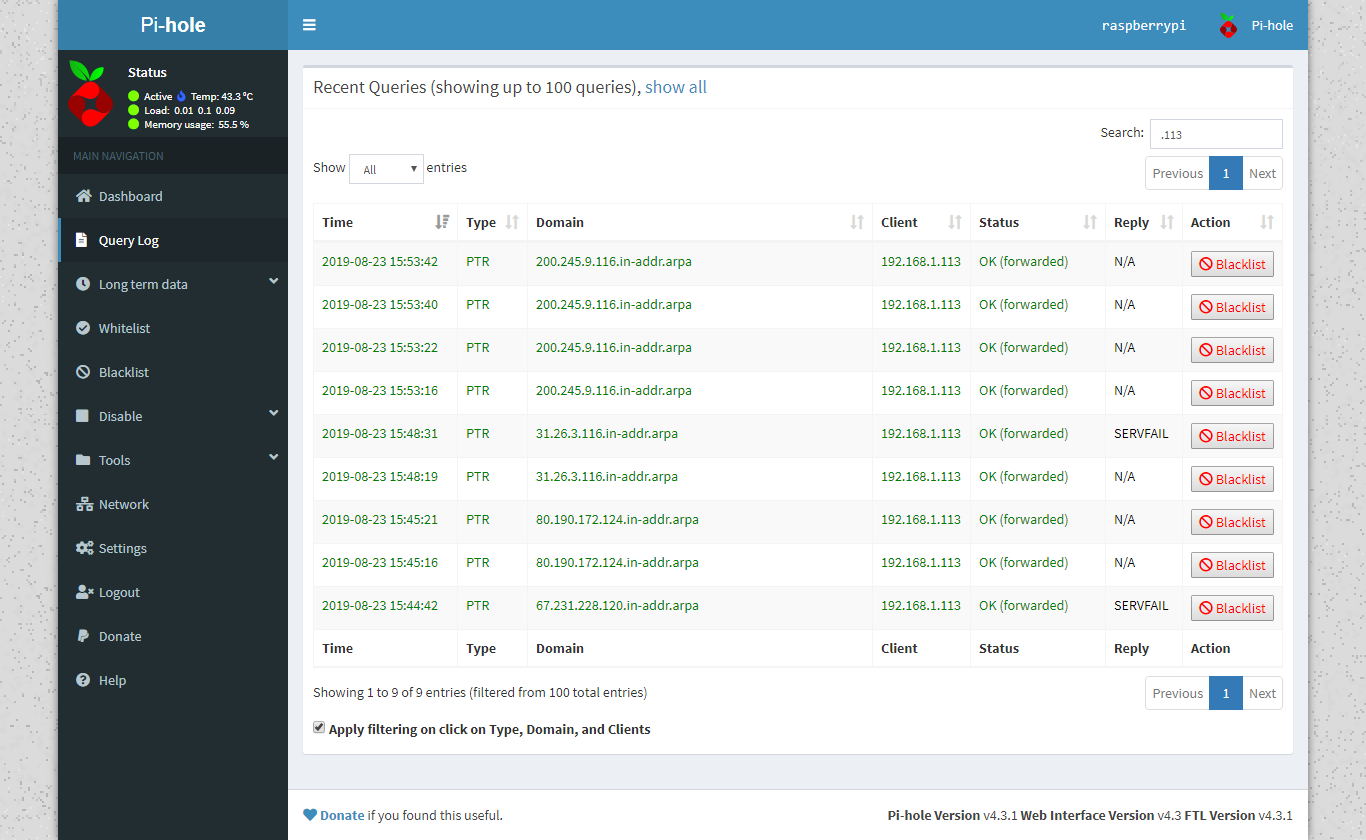
Odd IP's address in PI-hole with PFblocker (DoD for one :scream:)
-
@johnpoz said in Odd IP's address in PI-hole with PFblocker (DoD for one
 ):
):Yeah pretty sure out of the box ntop will try and resolve all the traffic it sees. Snort might/could do the same sort of thing.
Snort and Suricata behave the same as the pfSense firewall log view. They do not resolve a log entry unless the user clicks the little magnifying glass icon beside an IP on the ALERTS tab. So like the pfSense firewall log, manual user action is required for either of the IDS/IPS packages to perform a DNS lookup.
Update: I need to clarify one point. The scheduled rules update check cron tasks connect to the rule vendors via URLs, so those tasks will, as part of the CURL connection process, perform DNS lookups to convert the URL into an IP address.
-
@johnpoz your clients not going there?
not as far as I know

-
@bmeeks
Thanks for the clarification, I was not "sure" that is why made sure to say might/could ;) -
@johnpoz said in Odd IP's address in PI-hole with PFblocker (DoD for one
 ):
):@bmeeks
Thanks for the clarification, I was not "sure" that is why made sure to say might/could ;)No problemo. Just verifying how the package behaves so folks know.
-
I'm 99% curtain it's ntopng as the IP's have stopped showing in pi-hole when ntopng is turned off.
-
@randombits said in Odd IP's address in PI-hole with PFblocker (DoD for one
 ):
):I'm 99% curtain it's ntopng as the IP's have stopped showing in pi-hole when ntopng is turned off.
Packages like that try and do you a favor and turn the IP addresses they see into human-friendly domain names by doing reverse PTR lookups when writing the information to their logs. The DNS lookups are harmless unless you have a specific reason to want them turned off.
-
Most of the noise you would be seeing from the internet is not going to resolve anyway - so its pretty pointless to look for it.. None of the shit he posted resolves.. So what is the point of trying to, if 90% of its not even going to... Its wasted cycles and queries.
-
I've never used ntopng, but if the DNS lookup thingy is not a configurable option, perhaps that is a feature the maintainer/developer might want to consider adding.
-
pretty sure you can just turn off the resolving part.. I don't currently have it running - let me look
edit: yeah you can config it
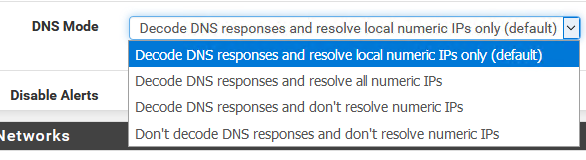
If it was default on his settings it should not have tried to resolve the public IPs, and only his local ones.
-
Spoke too soon, I removed ntopng, snort, darkstat and avahi and I'm still getting the IP's in pi-hole. My thoughts are not to use pi-hole or what I'm doing is wrong in some way. Also nothing connected on the LAN side at all - laptop off.
I think the obvious answer is Pfblocker or some weird interaction with pi-hole. Why I think this, I turn on another laptop WIFI'd to the router (so it's on the WAN side of pfsense and pi-hole starts seeing these IP's.
I'll take pi-hole out of the loop and put 9.9.9.9 into pfsense in the system/general DNS