OpenVPN Peer to Peer Problem - Tunnel steht aber keine Daten gehen durch
-
IPv4 Tunnel Network am Client leer lassen, das bekommt er passend vom Server gepusht.
Hast du auf beiden Seiten entsprechende Firewall Regeln eingerichtet im OpenVPN Tab?
Die Clients nutzen die lokale pfSense jeweils als Gateway?-Rico
-
Schaut mal - ist das nur ein Tippfehler oder hast Du für den Tunnel am Standort A und Standort B zwei unterschiedliche Netze eingetragen? Du brauchst ein Transfernetz, ein /30 reicht bei Peer2Peer. Server nimmt sich die erste IP, Client die folgende automatisch.
Stell mal den Tunnel Am Standort A auch auf Deine 192.168.21.0/24 und teste ob es funktioniert.;-)
-
@Rico
Hi, ja die OpenVPN Regeln habe ich auf beiden Seiten erstellt und einfach auf any gestellt. Sprich es ist alles erlaubt.
Die Clients sprich in meinem Fall die Synology hängt direkt an der SG-3100 und bekommt per DHCP eine Adresse zugewiesen, die 192.168.20.5/24. Von der Synology komme ich ins Internet etc. von daher würde ich sagen das passt. Habe es aber auch nochmal nachgeschaut IP, GW und DNS sind passend. -
@roadrunner51
Hi,
ich habe mal Testweise beides gemacht. Das Transfernetz auf dem OpenVPN Client entfernt sowie das gleiche wie auf dem OpenVPN Server gesetzt. Brachte aber beides keinen Erfolg bzw. den gleichen Fehler. Der VPN Tunnel steht es gehen aber keine Daten drüber. -
Hast Du nach den Änderungen den OpenVPN Service auf beiden Seiten neu gestartet?
-
@roadrunner51
Hi,
ja, ich habe einfach beide Firewalls neu gestartet. Danach sehe ich das der Tunnel aufgebaut ist.Wenn ich auf die IP aus dem Transfernetz auf den OpenVPN Client zugreife bekomme ich auch das Firewall Admininterface im Browser auf. Nur komme ich nicht auf die Synology die "hinter" der Firewall steht.
Mal so eine generelle Frage. Kann ich von der Seite auf dem der OpenVPN Server läuft auf das Netz hinter dem OpenVPN zugreifen? Oder geht das nur anders rum sprich vom OpenVPN Client zum OpenVPN Server? Eventuell muss ich da noch was konfigurieren?
-
Zeig bitte die logs von client und server mit verb 4.
Public IP ins client log entfernen...Vors aufbauen die VPN verbindung, beide Dasboards schliessen...
-
Meine OpenVPN Konfig sieht aktuell so aus:
OpenVPN Server
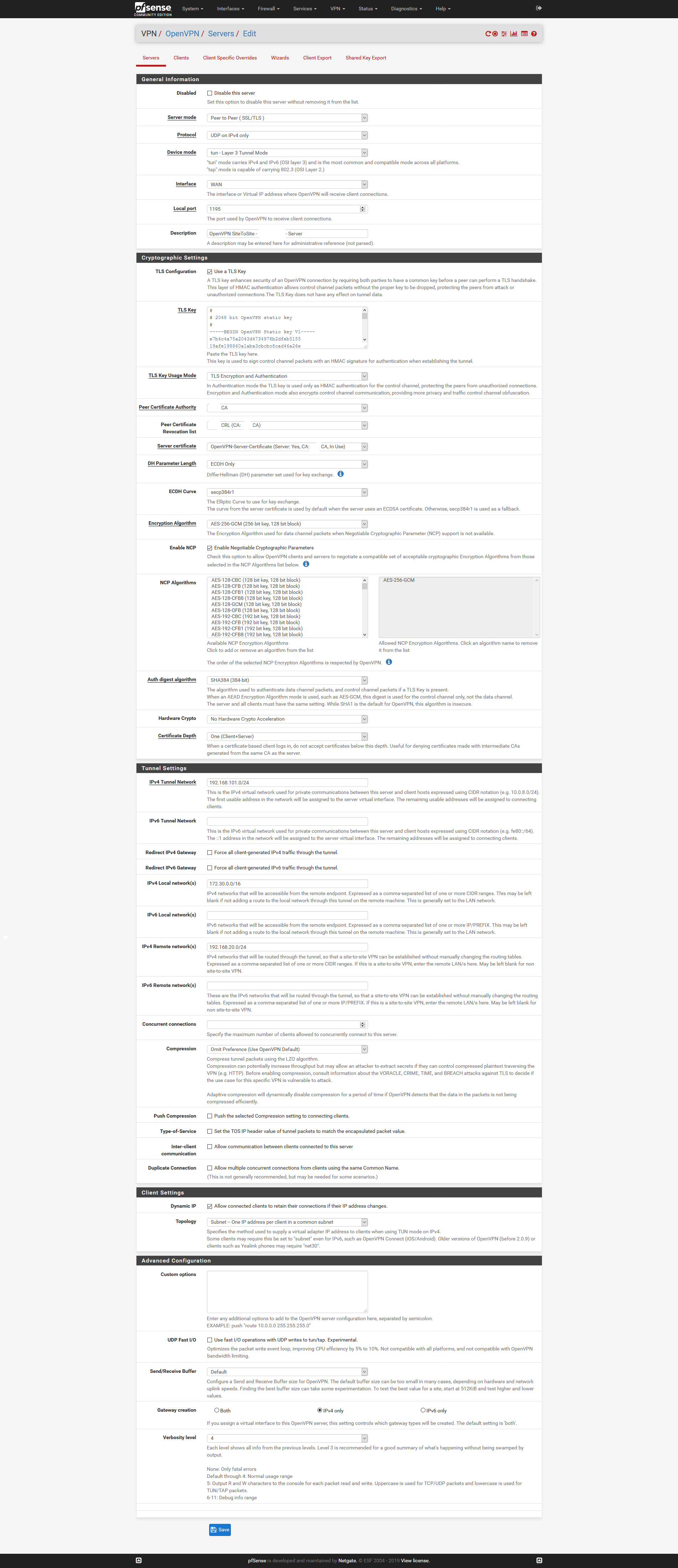
OpenVPN Client
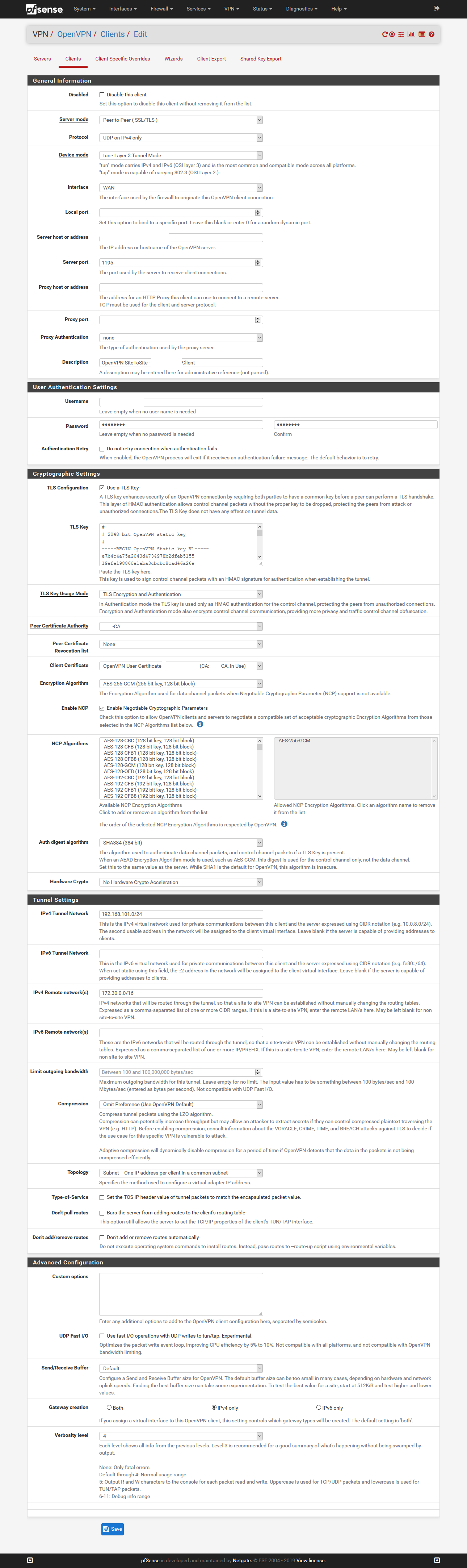
Die Logs kommen gleich.
-
Anbei die OpenVPN Logs.
OpenVPN Server Log
Aug 26 17:31:51 openvpn 4781 MANAGEMENT: Client disconnected Aug 26 17:31:51 openvpn 4781 MANAGEMENT: CMD 'quit' Aug 26 17:31:51 openvpn 4781 MANAGEMENT: CMD 'status 2' Aug 26 17:31:51 openvpn 4781 MANAGEMENT: Client connected from /var/etc/openvpn/server2.sock Aug 26 17:30:49 openvpn 4781 MANAGEMENT: Client disconnected Aug 26 17:30:49 openvpn 4781 MANAGEMENT: CMD 'quit' Aug 26 17:30:49 openvpn 4781 MANAGEMENT: CMD 'status 2' Aug 26 17:30:49 openvpn 4781 MANAGEMENT: Client connected from /var/etc/openvpn/server2.sock Aug 26 17:29:47 openvpn 4781 MANAGEMENT: Client disconnected Aug 26 17:29:47 openvpn 4781 MANAGEMENT: CMD 'quit' Aug 26 17:29:47 openvpn 4781 MANAGEMENT: CMD 'status 2' Aug 26 17:29:46 openvpn 4781 MANAGEMENT: Client connected from /var/etc/openvpn/server2.sock Aug 26 17:29:29 openvpn 4781 benutzer.name/x.x.x.x:21442 MULTI: bad source address from client [::], packet dropped Aug 26 17:29:28 openvpn 4781 benutzer.name/x.x.x.x:21442 MULTI: bad source address from client [::], packet dropped Aug 26 17:29:28 openvpn 4781 benutzer.name/x.x.x.x:21442 MULTI: bad source address from client [::], packet dropped Aug 26 17:29:28 openvpn 4781 benutzer.name/x.x.x.x:21442 MULTI: bad source address from client [::], packet dropped Aug 26 17:29:27 openvpn 4781 benutzer.name/x.x.x.x:21442 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 26 17:29:27 openvpn 4781 benutzer.name/x.x.x.x:21442 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 26 17:29:27 openvpn 4781 benutzer.name/x.x.x.x:21442 Data Channel MTU parms [ L:1549 D:1450 EF:49 EB:406 ET:0 EL:3 ] Aug 26 17:29:27 openvpn 4781 benutzer.name/x.x.x.x:21442 SENT CONTROL [benutzer.name]: 'PUSH_REPLY,route 172.30.0.0 255.255.0.0,route-gateway 192.168.101.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.101.2 255.255.255.0,peer-id 0,cipher AES-256-GCM' (status=1) Aug 26 17:29:27 openvpn 4781 benutzer.name/x.x.x.x:21442 PUSH: Received control message: 'PUSH_REQUEST' Aug 26 17:29:26 openvpn 4781 MULTI: primary virtual IP for benutzer.name/x.x.x.x:21442: 192.168.101.2 Aug 26 17:29:26 openvpn 4781 MULTI: Learn: 192.168.101.2 -> benutzer.name/x.x.x.x:21442 Aug 26 17:29:26 openvpn 4781 MULTI_sva: pool returned IPv4=192.168.101.2, IPv6=(Not enabled) Aug 26 17:29:26 openvpn 4781 MULTI: new connection by client 'benutzer.name' will cause previous active sessions by this client to be dropped. Remember to use the --duplicate-cn option if you want multiple clients using the same certificate or username to concurrently connect. Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 [benutzer.name] Peer Connection Initiated with [AF_INET]x.x.x.x:21442 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_TCPNL=1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_COMP_STUBv2=1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_COMP_STUB=1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_LZO=1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_LZ4v2=1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_LZ4=1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_NCP=2 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_PROTO=2 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_PLAT=freebsd Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 peer info: IV_VER=2.4.6 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 VERIFY OK: Xpth=0, C=X, ST=X, L=X, O=X, CN=benutzer.name Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 VERIFY SCRIPT OK: Xpth=0, C=X, ST=X, L=X, O=X, CN=benutzer.name Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 VERIFY OK: Xpth=1, C=X, ST=X, L=X, O=X, emailAddress=X, CN=internal-ca Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 VERIFY SCRIPT OK: Xpth=1, C=X, ST=X, L=X, O=X, emailAddress=X, CN=internal-ca Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 TLS: Initial packet from [AF_INET]x.x.x.x:21442, sid=b49b21b9 d8600ef1 Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 Expected Remote Options String (VER=V4): 'V4,Xv-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,cipher AES-256-GCM,auth [null-digest],keysize 256,key-method 2,tls-client' Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 Local Options String (VER=V4): 'V4,Xv-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,cipher AES-256-GCM,auth [null-digest],keysize 256,key-method 2,tls-server' Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 Control Channel MTU parms [ L:1621 D:1156 EF:94 EB:0 ET:0 EL:3 ] Aug 26 17:29:26 openvpn 4781 x.x.x.x:21442 Re-using SSL/TLS context Aug 26 17:29:26 openvpn 4781 MULTI: multi_create_instance calledOpenVPN Client Log
Aug 26 17:34:56 openvpn 78417 client = ENABLED Aug 26 17:34:56 openvpn 78417 pull = ENABLED Aug 26 17:34:56 openvpn 78417 auth_user_pass_file = '/var/etc/openvpn/client1.up' Aug 26 17:34:56 openvpn 78417 OpenVPN 2.4.6 armv6-portbld-freebsd11.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Oct 3 2018 Aug 26 17:34:56 openvpn 78417 library versions: OpenSSL 1.0.2o-freebsd 27 Mar 2018, LZO 2.10 Aug 26 17:34:56 openvpn 78429 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client1.sock Aug 26 17:34:56 openvpn 78429 WARNING: using --pull/--client and --ifconfig together is probably not what you want Aug 26 17:34:56 openvpn 78429 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info. Aug 26 17:34:56 openvpn 78429 NOTE: the current --script-security setting may allow this configuration to call user-Xfined scripts Aug 26 17:34:56 openvpn 78429 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Aug 26 17:34:56 openvpn 78429 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Aug 26 17:34:56 openvpn 78429 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key Aug 26 17:34:56 openvpn 78429 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication Aug 26 17:34:56 openvpn 78429 Control Channel MTU parms [ L:1621 D:1156 EF:94 EB:0 ET:0 EL:3 ] Aug 26 17:34:56 openvpn 78429 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] Aug 26 17:34:56 openvpn 78429 Local Options String (VER=V4): 'V4,Xv-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,cipher AES-256-GCM,auth [null-digest],keysize 256,key-method 2,tls-client' Aug 26 17:34:56 openvpn 78429 Expected Remote Options String (VER=V4): 'V4,Xv-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,cipher AES-256-GCM,auth [null-digest],keysize 256,key-method 2,tls-server' Aug 26 17:34:56 openvpn 78429 TCP/UDP: Preserving recently used remote address: [AF_INET]X:1195 Aug 26 17:34:56 openvpn 78429 Socket Buffers: R=[42080->42080] S=[57344->57344] Aug 26 17:34:56 openvpn 78429 UDPv4 link local (bound): [AF_INET]192.168.178.5:0 Aug 26 17:34:56 openvpn 78429 UDPv4 link remote: [AF_INET]X:1195 Aug 26 17:34:56 openvpn 78429 TLS: Initial packet from [AF_INET]X:1195, sid=daae976f 628fd239 Aug 26 17:34:56 openvpn 78429 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Aug 26 17:34:56 openvpn 78429 VERIFY OK: Xpth=1, C=X, ST=X, L=X, O=X, emailAddress=X, CN=internal-ca Aug 26 17:34:56 openvpn 78429 VERIFY OK: Xpth=0, C=X, ST=X, L=X, O=X, emailAddress=X, CN=openvpn Aug 26 17:34:56 openvpn 78429 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA Aug 26 17:34:56 openvpn 78429 [openvpn] Peer Connection Initiated with [AF_INET]X:1195 Aug 26 17:34:57 openvpn 78429 SENT CONTROL [openvpn]: 'PUSH_REQUEST' (status=1) Aug 26 17:34:57 openvpn 78429 PUSH: Received control message: 'PUSH_REPLY,route 172.30.0.0 255.255.0.0,route-gateway 192.168.101.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.101.2 255.255.255.0,peer-id 1,cipher AES-256-GCM' Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: timers and/or timeouts modified Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: --ifconfig/up options modified Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: route options modified Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: route-related options modified Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: peer-id set Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: adjusting link_mtu to 1624 Aug 26 17:34:57 openvpn 78429 OPTIONS IMPORT: data channel crypto options modified Aug 26 17:34:57 openvpn 78429 Data Channel MTU parms [ L:1552 D:1450 EF:52 EB:406 ET:0 EL:3 ] Aug 26 17:34:57 openvpn 78429 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 26 17:34:57 openvpn 78429 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 26 17:34:57 openvpn 78429 ROUTE_GATEWAY 192.168.178.1/255.255.255.0 IFACE=mvneta2 HWADDR=00:08:a2:0d:bd:1e Aug 26 17:34:57 openvpn 78429 TUN/TAP Xvice ovpnc1 exists previously, keep at program end Aug 26 17:34:57 openvpn 78429 TUN/TAP Xvice /Xv/tun1 opened Aug 26 17:34:57 openvpn 78429 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Aug 26 17:34:57 openvpn 78429 /sbin/ifconfig ovpnc1 192.168.101.2 192.168.101.1 mtu 1500 netmask 255.255.255.0 up Aug 26 17:34:57 openvpn 78429 /sbin/route add -net 192.168.101.0 192.168.101.1 255.255.255.0 Aug 26 17:34:57 openvpn 78429 /usr/local/sbin/ovpn-linkup ovpnc1 1500 1552 192.168.101.2 255.255.255.0 init Aug 26 17:34:57 openvpn 78429 /sbin/route add -net 172.30.0.0 192.168.101.1 255.255.0.0 Aug 26 17:34:57 openvpn 78429 /sbin/route add -net 172.30.0.0 192.168.101.1 255.255.0.0 Aug 26 17:34:57 openvpn 78429 ERROR: FreeBSD route add command failed: external program exited with error status: 1 Aug 26 17:34:57 openvpn 78429 Initialization Sequence Completed -
Hallo,
Server:
MULTI: new connection by client 'benutzer.name' will cause previous active sessions by this client to be dropped. Remember to use the --duplicate-cn option if you want multiple clients using the same certificate or username to concurrently connect.Sorge dafür das sowohl server und client ein komplette neustart machen oder warte mindestens 2 minuten mit neuverbinden der client.
.
Client:/usr/local/sbin/ovpn-linkup ovpnc1 1500 1552 192.168.101.2 255.255.255.0 init Aug 26 17:34:57 openvpn 78429 /sbin/route add -net 172.30.0.0 192.168.101.1 255.255.0.0 Aug 26 17:34:57 openvpn 78429 /sbin/route add -net 172.30.0.0 192.168.101.1 255.255.0.0 Aug 26 17:34:57 openvpn 78429 ERROR: FreeBSD route add command failed: external program exited with error status: 1IPv4 Remote Networks: 172.30.0.0/16 entfernen weil der server das netz bereits pushed, darum doppelte route:
PUSH: Received control message: 'PUSH_REPLY,**route 172.30.0.0 255.255.0.0**,route-gateway 192.168.101.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.101.2 255.255.255.0,peer-id 1,cipher AES-256-GCM'.
TUN/TAP Xvice ovpnc1 exists previously, keep at program endSowie oben, komplette neustart machen.
-
Hi,
so ich habe den OpenVPN Client angepasst:
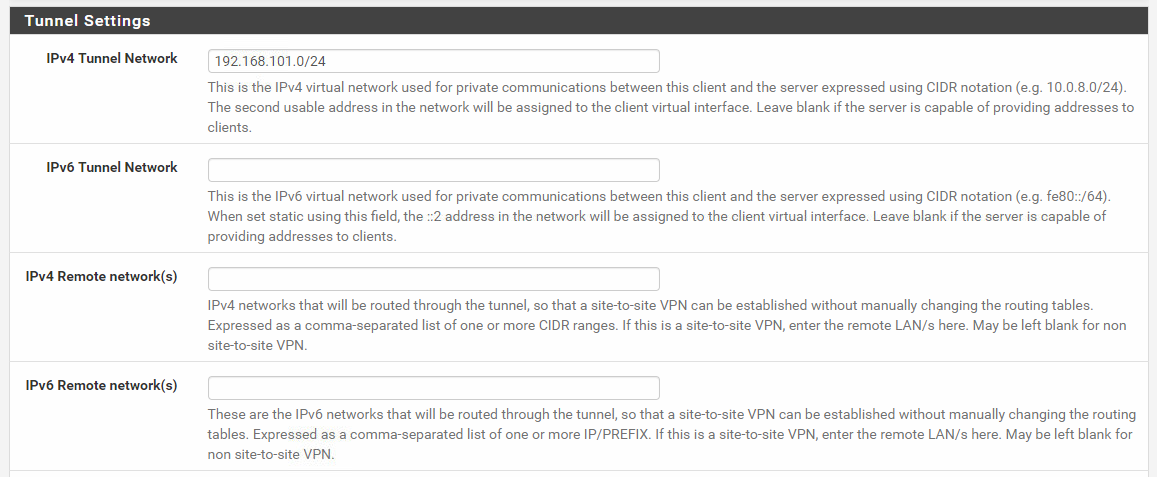
Danach habe ich beide Firewalls komplett neugestartet. Aber der Zugriff auf die internen Netze (172.30.0.0/16 sowie 192.168.20.0/24) funktioniert nicht.
OpenVPN Server Log
Aug 27 20:26:48 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:44 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:40 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:36 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:32 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:30 openvpn 73586 MANAGEMENT: Client disconnected Aug 27 20:26:30 openvpn 73586 MANAGEMENT: CMD 'quit' Aug 27 20:26:30 openvpn 73586 MANAGEMENT: CMD 'status 2' Aug 27 20:26:30 openvpn 73586 MANAGEMENT: Client connected from /var/etc/openvpn/server2.sock Aug 27 20:26:30 openvpn 46812 MANAGEMENT: Client disconnected Aug 27 20:26:30 openvpn 46812 MANAGEMENT: CMD 'quit' Aug 27 20:26:30 openvpn 46812 MANAGEMENT: CMD 'status 2' Aug 27 20:26:30 openvpn 46812 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock Aug 27 20:26:28 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:24 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:20 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:16 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:12 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:08 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:04 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:02 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:26:00 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:25:59 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:25:41 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:25:36 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:25:31 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:25:28 openvpn 73586 MANAGEMENT: Client disconnected Aug 27 20:25:28 openvpn 73586 MANAGEMENT: CMD 'quit' Aug 27 20:25:28 openvpn 73586 MANAGEMENT: CMD 'status 2' Aug 27 20:25:28 openvpn 73586 MANAGEMENT: Client connected from /var/etc/openvpn/server2.sock Aug 27 20:25:28 openvpn 46812 MANAGEMENT: Client disconnected Aug 27 20:25:28 openvpn 46812 MANAGEMENT: CMD 'quit' Aug 27 20:25:28 openvpn 46812 MANAGEMENT: CMD 'status 2' Aug 27 20:25:27 openvpn 46812 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock Aug 27 20:25:26 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: bad source address from client [192.168.20.52], packet dropped Aug 27 20:24:56 openvpn 73586 MANAGEMENT: Client disconnected Aug 27 20:24:56 openvpn 73586 MANAGEMENT: CMD 'status 2' Aug 27 20:24:56 openvpn 73586 MANAGEMENT: Client connected from /var/etc/openvpn/server2.sock Aug 27 20:24:56 openvpn 46812 MANAGEMENT: Client disconnected Aug 27 20:24:56 openvpn 46812 MANAGEMENT: CMD 'status 2' Aug 27 20:24:56 openvpn 46812 MANAGEMENT: Client connected from /var/etc/openvpn/server1.sock Aug 27 20:24:52 openvpn 73586 benutzer.name/x.x.x.x:48522 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 27 20:24:52 openvpn 73586 benutzer.name/x.x.x.x:48522 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 27 20:24:52 openvpn 73586 benutzer.name/x.x.x.x:48522 Data Channel MTU parms [ L:1549 D:1450 EF:49 EB:406 ET:0 EL:3 ] Aug 27 20:24:52 openvpn 73586 benutzer.name/x.x.x.x:48522 SENT CONTROL [benutzer.name]: 'PUSH_REPLY,route 172.30.0.0 255.255.0.0,route-gateway 192.168.101.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.101.2 255.255.255.0,peer-id 0,cipher AES-256-GCM' (status=1) Aug 27 20:24:52 openvpn 73586 benutzer.name/x.x.x.x:48522 PUSH: Received control message: 'PUSH_REQUEST' Aug 27 20:24:51 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: primary virtual IP for benutzer.name/x.x.x.x:48522: 192.168.101.2 Aug 27 20:24:51 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI: Learn: 192.168.101.2 -> benutzer.name/x.x.x.x:48522 Aug 27 20:24:51 openvpn 73586 benutzer.name/x.x.x.x:48522 MULTI_sva: pool returned IPv4=192.168.101.2, IPv6=(Not enabled) Aug 27 20:24:51 openvpn 73586 x.x.x.x:48522 [benutzer.name] Peer Connection Initiated with [AF_INET]x.x.x.x:48522OpenVPN Client Log
Aug 27 20:24:50 openvpn 29467 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info. Aug 27 20:24:50 openvpn 29467 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Aug 27 20:24:50 openvpn 29467 Re-using SSL/TLS context Aug 27 20:24:50 openvpn 29467 Control Channel MTU parms [ L:1621 D:1156 EF:94 EB:0 ET:0 EL:3 ] Aug 27 20:24:50 openvpn 29467 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ] Aug 27 20:24:50 openvpn 29467 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,cipher AES-256-GCM,auth [null-digest],keysize 256,key-method 2,tls-client' Aug 27 20:24:50 openvpn 29467 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1549,tun-mtu 1500,proto UDPv4,cipher AES-256-GCM,auth [null-digest],keysize 256,key-method 2,tls-server' Aug 27 20:24:50 openvpn 29467 TCP/UDP: Preserving recently used remote address: [AF_INET]x.x.x.x:1195 Aug 27 20:24:50 openvpn 29467 Socket Buffers: R=[42080->42080] S=[57344->57344] Aug 27 20:24:50 openvpn 29467 UDPv4 link local (bound): [AF_INET]192.168.178.5:0 Aug 27 20:24:50 openvpn 29467 UDPv4 link remote: [AF_INET]x.x.x.x:1195 Aug 27 20:24:50 openvpn 29467 TLS: Initial packet from [AF_INET]x.x.x.x:1195, sid=80b28fc0 983666d9 Aug 27 20:24:50 openvpn 29467 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Aug 27 20:24:51 openvpn 29467 VERIFY OK: depth=1, CN=OpenVPN-CA Aug 27 20:24:51 openvpn 29467 VERIFY OK: depth=0, CN=OpenVPN-Server-Certificate Aug 27 20:24:51 openvpn 29467 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Aug 27 20:24:51 openvpn 29467 MANAGEMENT: CMD 'state 1' Aug 27 20:24:51 openvpn 29467 MANAGEMENT: Client disconnected Aug 27 20:24:51 openvpn 29467 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 4096 bit RSA Aug 27 20:24:51 openvpn 29467 [OpenVPN-Server-Certificate] Peer Connection Initiated with [AF_INET]x.x.x.x:1195 Aug 27 20:24:52 openvpn 29467 SENT CONTROL [OpenVPN-Server-Certificate]: 'PUSH_REQUEST' (status=1) Aug 27 20:24:52 openvpn 29467 PUSH: Received control message: 'PUSH_REPLY,route 172.30.0.0 255.255.0.0,route-gateway 192.168.101.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.101.2 255.255.255.0,peer-id 0,cipher AES-256-GCM' Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: timers and/or timeouts modified Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: --ifconfig/up options modified Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: route options modified Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: route-related options modified Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: peer-id set Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: adjusting link_mtu to 1624 Aug 27 20:24:52 openvpn 29467 OPTIONS IMPORT: data channel crypto options modified Aug 27 20:24:52 openvpn 29467 Data Channel MTU parms [ L:1552 D:1450 EF:52 EB:406 ET:0 EL:3 ] Aug 27 20:24:52 openvpn 29467 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 27 20:24:52 openvpn 29467 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Aug 27 20:24:52 openvpn 29467 ROUTE_GATEWAY 192.168.178.1/255.255.255.0 IFACE=mvneta2 HWADDR=00:08:a2:0d:bd:1e Aug 27 20:24:52 openvpn 29467 TUN/TAP device ovpnc1 exists previously, keep at program end Aug 27 20:24:52 openvpn 29467 TUN/TAP device /dev/tun1 opened Aug 27 20:24:52 openvpn 29467 ioctl(TUNSIFMODE): Device busy (errno=16) Aug 27 20:24:52 openvpn 29467 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Aug 27 20:24:52 openvpn 29467 /sbin/ifconfig ovpnc1 192.168.101.2 192.168.101.1 mtu 1500 netmask 255.255.255.0 up Aug 27 20:24:52 openvpn 29467 /sbin/route add -net 192.168.101.0 192.168.101.1 255.255.255.0 Aug 27 20:24:52 openvpn 29467 /usr/local/sbin/ovpn-linkup ovpnc1 1500 1552 192.168.101.2 255.255.255.0 init Aug 27 20:24:52 openvpn 29467 /sbin/route add -net 172.30.0.0 192.168.101.1 255.255.0.0 Aug 27 20:24:52 openvpn 29467 Initialization Sequence Completed Aug 27 20:25:00 openvpn 29467 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Aug 27 20:25:00 openvpn 29467 MANAGEMENT: CMD 'state 1' Aug 27 20:25:00 openvpn 29467 MANAGEMENT: CMD 'status 2' Aug 27 20:25:00 openvpn 29467 MANAGEMENT: Client disconnected Aug 27 20:25:01 openvpn 29467 MANAGEMENT: Client connected from /var/etc/openvpn/client1.sock Aug 27 20:25:01 openvpn 29467 MANAGEMENT: CMD 'state 1' Aug 27 20:25:01 openvpn 29467 MANAGEMENT: CMD 'status 2' Aug 27 20:25:01 openvpn 29467 MANAGEMENT: Client disconnected -
Hi,
ich habe mal testweise das ganze als OpenVPN Server und OpenVPN Client über Peer to Peer (Shared Key) eingerichtet. Damit funktioniert es einwandfrei. Sobald ich die beiden Tunnel starte steht dieser und es gehen Daten drüber. Ich kann von beiden CLient Netzen auf jeweils das andere zugreifen.
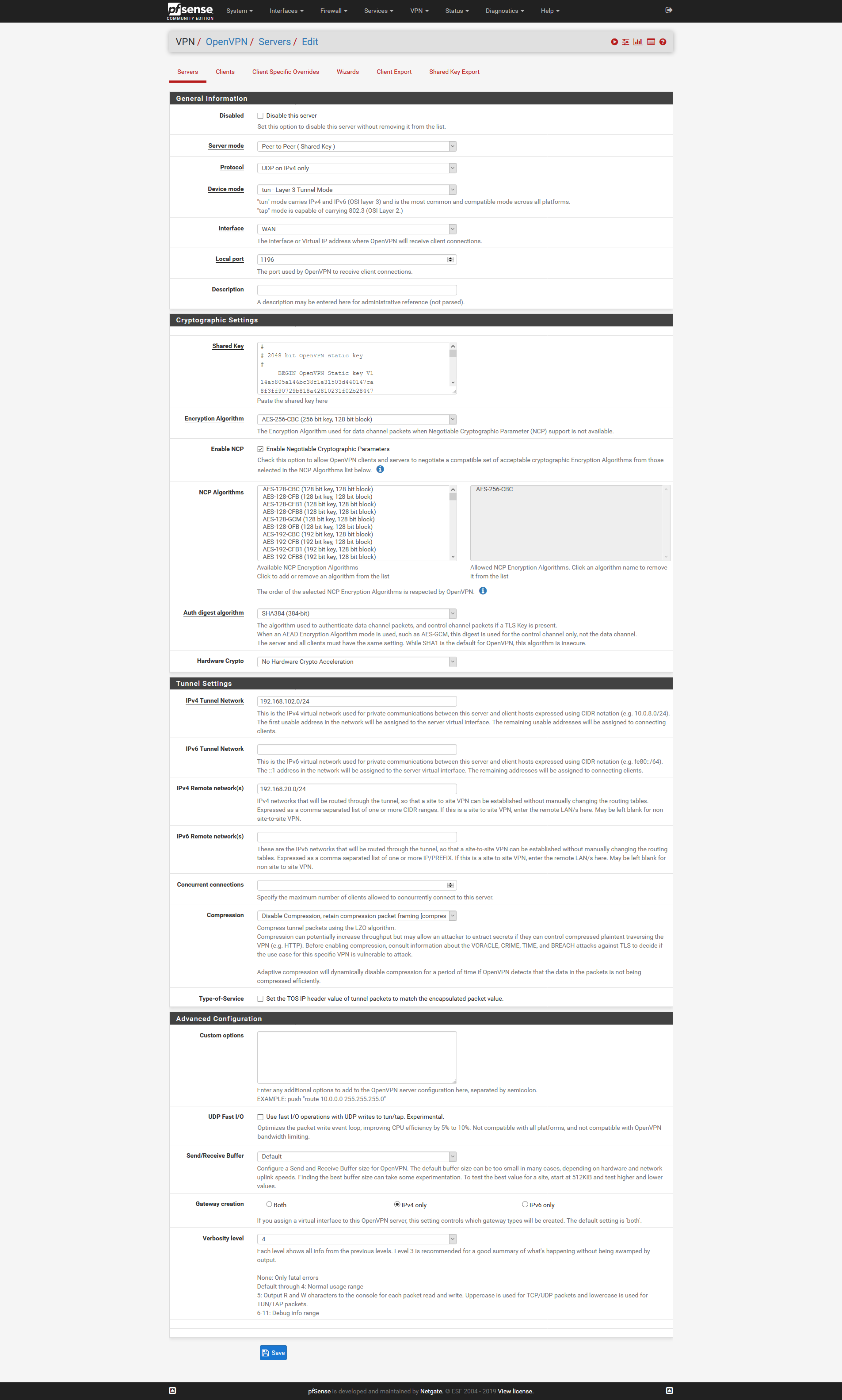
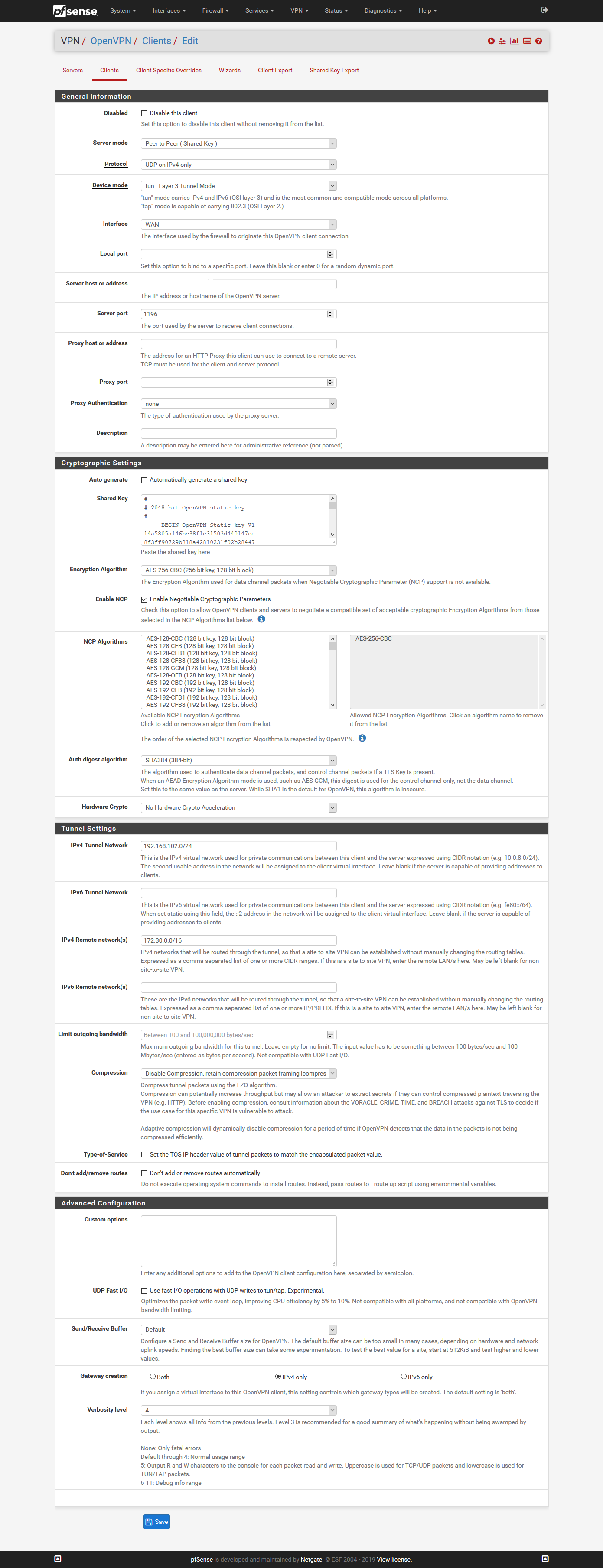
Somit passen meine Regeln usw.. Es muss also an der OpenVPN Konfig mit Peer to Peer (SSL/TLS) liegen. Ich hoffe es hat noch jemand einen Tipp?
-
CSO gesetzt unter VPN > OpenVPN > Client Specific Overrides ?
Bei Common Name den Cert Name des Client und IPv4 Remote Network/s das Netz auf der Client Seite.-Rico
-
@Rico said in OpenVPN Peer to Peer Problem - Tunnel steht aber keine Daten gehen durch:
CSO gesetzt unter VPN > OpenVPN > Client Specific Overrides ?
Bei Common Name den Cert Name des Client und IPv4 Remote Network/s das Netz auf der Client Seite.-Rico
Hi,
das habe ich nicht gemacht. Ist dies Pflicht sobald ich Peer to Peer SSL/TLS habe?
-
Bei deinem Tunnel network ja.
-Rico