Site-to-Site VPN between pfSense & openWRT
-
I am tying to establish a S2S openVPN between a pfSense & openWRT but nothing works.
pfSense (VM) : 2.4..4-RELEASE-p3
WAN - xxx.xxx.xxx.xxx behind 1:1 NAT
LAN - 192.168.19.0/24
Role - ServeropenWRT (TL-WR1043ND 1.x) :
WAN - DHCP
LAN - 192.168.0.0/24
Role - ClientIf I replace openWRT with pfSense, its works like a charm but with openWRT its not. Some configuration mistake I believe.
Kindly suggest.
-
Well, you haven't told us anything other than "it doesn't work", and you've provided almost no detail about your configuration so it's going to be impossible to help you.
I might suggest that you go to the OpenWRT forums and ask there since it is the client that is having issues or you can provide details about your exact problem and config and maybe we can guess about the OpenWRT side.
-
@KOM Really sorry about.
Actually I tried uisng luci-app which I really don't know what it was doing. However I did via CLI following a similar post and below is the config;
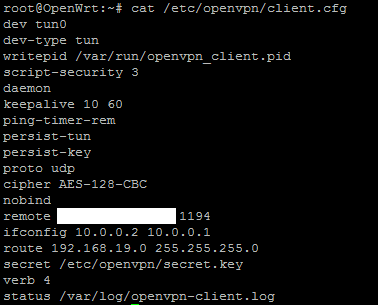
openWRT
dev tun0
dev-type tun
writepid /var/run/openvpn_client.pid
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp
cipher AES-128-CBC
nobind
remote xxx.xxx.xxx.xxx 1194
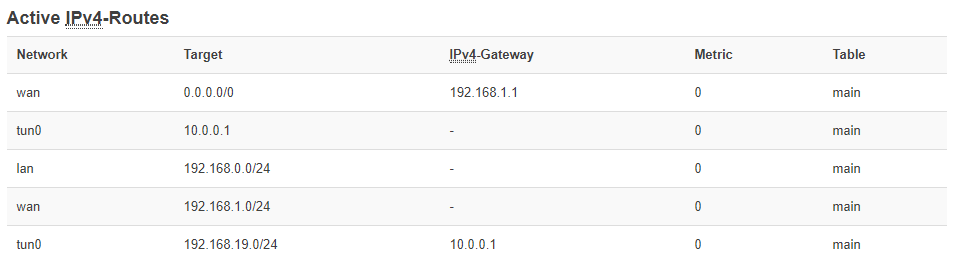
ifconfig 10.0.0.2 10.0.0.1
route 192.168.19.0/24
secret /etc/openvpn/secret.key
verb 4
status /var/log/openvpn-client.logpfSense
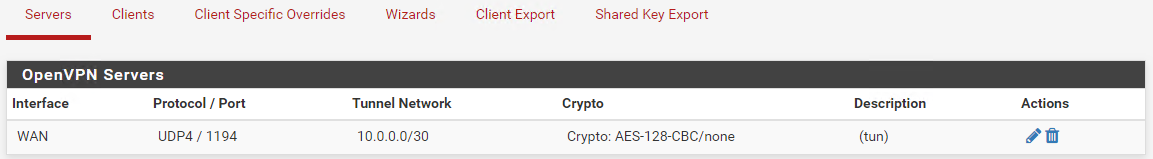
peer to peer (shared key)
protocol UDP
device mode TUN
interface WAN
port 1194
tunnel network : 10.0.0.0/30
remote network : 192.168.0.0/24
Cipher AES-128-CBC
No AUTH -
I'll ask again: what is the specific problem you are having? Does it fail to connect? Does it connect but no traffic flows? Does it connect and some traffic flows but websites don't work?
What does Status - System Logs - OpenVPN say? What do the logs on the OpenWRT box say?
If you could get it working with two pfSense instances but cannot with OpenWRT then there must be something specific to that OpenWRT box.
-
-
@KOM said in Site-to-Site VPN between pfSense & openWRT:
What does Status - System Logs - OpenVPN say? What do the logs on the OpenWRT box say?
If you're using the same parameters and it works with a pfSense instance but not OpenWRT then there is something specific about the OpenWRT box that is causing the problem. If there is nothing helpful in the logs then your best option is to go to the OpenWRT forum and approach it from that angle.
-
@KOM I guess I got something worked
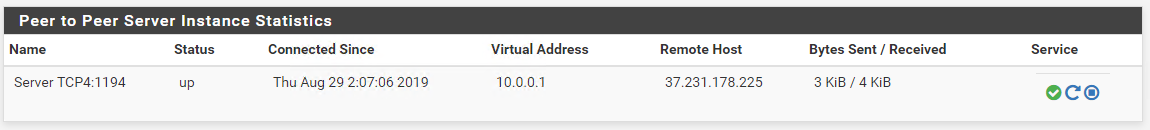
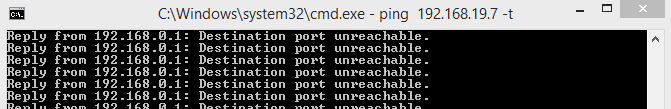
I could ping the pfSense tunnel IP from the OpenWRT box.
I guess the firewall is blocking the traffic now.
-
Both should have default allow rules but check to be sure. What's with that ifconfig line in the OpenWRT client config? I don't recall seeing that before. You should note that client PC's software firewall will often block traffic from outside their own subnet, so make sure the thing you're pinging will actually reply.
-
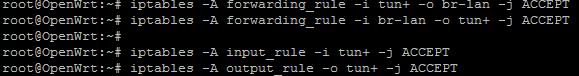
@KOM Below are my rules at openWRT and pfSense is anything allowed.
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'ACCEPT'
option forward 'ACCEPT'config forwarding
option src 'lan'
option dest 'wan'config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'config include
option path '/etc/firewall.user'The ifconfig line was always there .. it defines the tunnel interface.
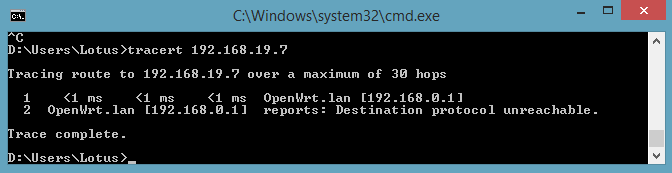
And yes I can ping 192.168.19.7 from the other side internal network.
-
This is a pfSense forum. I have no idea about OpenWRT's ipchains rules or whatever they are, sorry.