Setting up pfSense for VLAN and trunk port
-
Hi,
I’m fairly new to pfSense, VLAN, etc...I need some help to renew my network.
The network now is like in this image
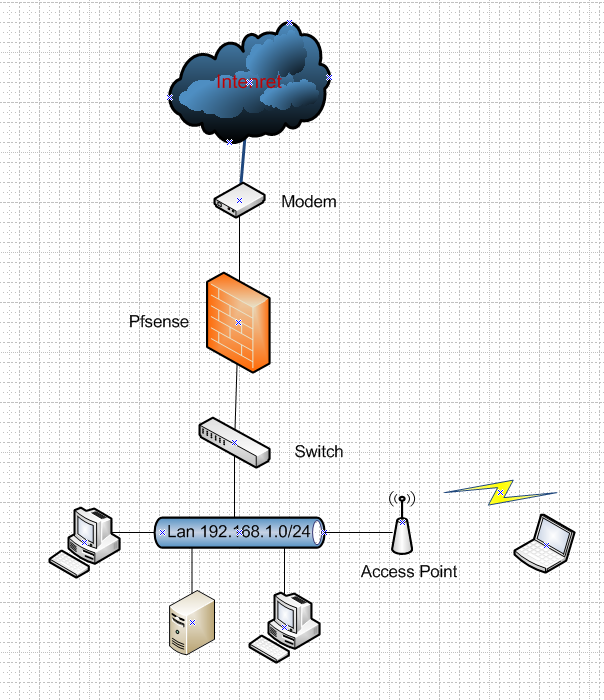
I would like to implement a setup similar to this image
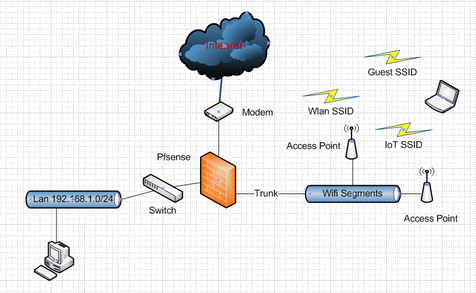
because I don't want buy three AP, one for the three network (private LAN, GUEST, IOT)
SETUP:
WAN igb0
LAN igb1 connected to a unmanaged switch (private LAN)
TRUNK igb2 connected with a access point (with 3 ssid)VLAN10 (wifi for private LAN)
VLAN20 (wifi for guest with captive portal)
VLAN30 (wifi for IoT)
I do VLAN in Interfaces/Assignment/VLAN tag:
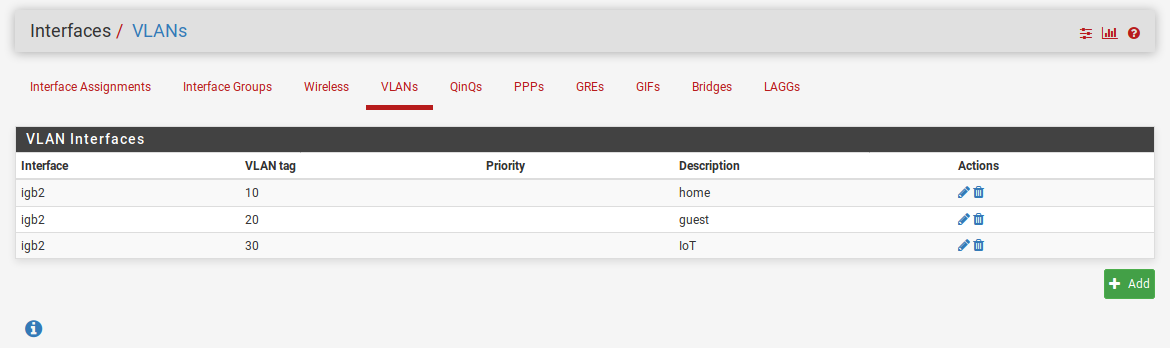
In Interface/Assignment/Interface assignment tag I assigned
VLAN10 to OPT1
VLAN20 to OPT2
VLAN30 to OPT3Now my goals are:
- set pfsense so that VLAN10 (private wifi) and LAN are in the same (private) network 192.168.10.0/24
somewhere in this forum I saw the WEBgui page Interfaces/switch/ but I don't have it! - use the same DHCP server (set up in LAN interface) for private network ( LAN and wifi VLAN10)
- connect to access point for managment
For third point I don't know if it is better create another vlan (managment) or use private lan
I was hoping for your advise and tips about best practice or for a little different setup(s)
Luca - set pfsense so that VLAN10 (private wifi) and LAN are in the same (private) network 192.168.10.0/24
-
If the switch can handle VLANS i'd be tempted to connect the AP to the switch, not all IOT stuff is Wi-Fi, my Phillips Hue bridge for example.
Here's my setup:-
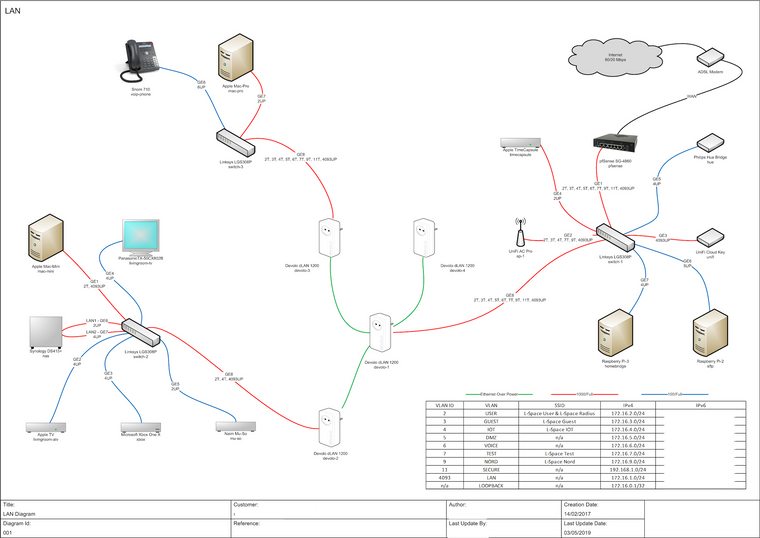
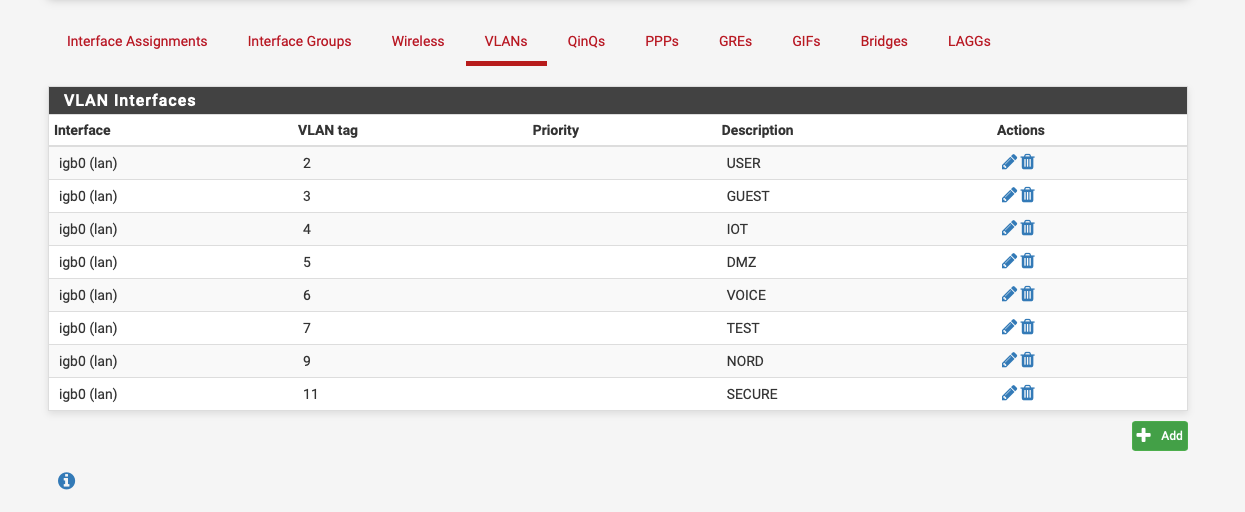
-
@tronix said in Setting up pfSense for VLAN and trunk port:
VLAN10 (wifi for private LAN)
Why use VLAN instead of native? Your computers on the network will likely be native. Just use the native LAN and add the 2 VLANs to it. As mentioned in another post, why not just put the AP on the switch. That's what I have here and it works fine.
-
@NogBadTheBad said in Setting up pfSense for VLAN and trunk port:
If the switch can handle VLANS i'd be tempted to connect the AP to the switch
Please explain why a switch could not handle VLANs. Here is a list of Ethertype numbers and any switch that can't handle all of them is defective. The only difference between a VLAN tagged frame and untagged is the value of the Ethertype and 4 more bytes to hold the tag. The 802.3ac extension was added to the spec 21 years ago, to support VLAN tags, and it's very unlikely you'll ever come across switches that don't support it. However, if you do manage to find something that ancient, then all you have to do is reduce the MTU to 1496, to allow room for the tag.
-
A switch that you can define what ports are in what vlan and if the port is tagged, untagged or is a trunk port.
-
Those drawings look strangely familiar ;) hehehe
Do you happen to have the link to the thread where I posted those?
I am not quite understanding question 1 to be honest?
You can tag the vlan for your ssid to be anything you want, 10, 100, whatever.. That really has nothing to do with putting it on the same network as lan for pfsense. Pfsense doesn't have to know its tagged.. You connect your AP to the switch, you set your ssid to vlan whatever you want to use on your switch.. And just put the port untagged connected to pfsense lan in that same vlan as the ssid you want on the lan network. it only has to be tagged on interfaces where there will be other vlans carried, ie to your AP that will have other ssids in other vlans.
as to
WEBgui page Interfaces/switch/ but I don't have it!
That would be only on boxes that actually have a switch for ports, say a 3100 or 5100 as examples.
-
@NogBadTheBad said in Setting up pfSense for VLAN and trunk port:
If the switch can handle VLANS i'd be tempted to connect the AP to the switch,
Nowadays the switch GS108 is unmanaged, but I'm about to buy a managed one. In this test network the setup don't change with only a trunk router --- AP or two trunk router ---- switch ---- AP
I agree with you the second one is more flexible.@JKnott said in Setting up pfSense for VLAN and trunk port:
Why use VLAN instead of native?
There's no particular reason, I followed the https://docs.netgate.com/pfsense/en/latest/book/vlan/pfsense-vlan-configuration.html
I understand that I have two ways:
-
delete VLAN10
how does pfsense know to assign wifi host to LAN? -
create another VLAN interface VLAN10toigb1 and assign to LAN
next? Do I have to connect in some way LAN and OPT1?
Luca
-
-
@johnpoz https://www.neowin.net/forum/topic/1317426-pfsense-first-time-build-question/
with a little bit of gimp....
What program did you use? visio? dia?
-
If your going to play with vlan - yes get a vlan capable switch.. While sure a dumb switch should not strip the tags.. Its not going to isolate any tagged traffic either.. So any broadcast traffic is going to go tall all ports! So anything connected to the switch will see all broadcast traffic no matter what vlan its tagged for.
edit: those were done in visio.
edit2: Ah my alias over on neowin.. Sssh - don't spread that around ;)
-
@johnpoz said in Setting up pfSense for VLAN and trunk port:
While sure a dumb switch should not strip the tags.
Why would any dumb switch strip the tags? A tag is just 4 more bytes, with the new Ethertype field set to indicate a VLAN.
-
I didn't say it would.. Dude you and your running vlans over a dumb switch.. Get over it already.. It has nothing to do with the switch won't strip them... Its the fact that it won't actually isolate the traffic like it should ;)
edit:
And while security might not be a major concern in a "home" network.. Since the switch doesn't actually understand tags, and has no way of limiting what tags can be used on specific ports.. Anyone that plugs into such a network can just set their device to tag their traffic for whatever vlan ID they want to be on. And its not like it would be hard to see even what IDs are play because every port is going to see all the different vlan ID via the broadcast traffic.If say the min cost of a vlan switch was like 100's of dollars or something, I might see taking a shortcut in a home setup.. But a vlan capable switch can be had for less than a 4 pack of good beer ;)
If your wanting to run vlans, then you need vlan capable switch - PERIOD! Its the cost of wanting to run vlans.. Put your dumb switches downstream of the smart switch, where all the devices on the dumb switch will be in 1 vlan, etc.
So its not like your dumb switches have sit on a shelf or get thrown away, they can still be quite useful in a growing network.
-
@johnpoz said in Setting up pfSense for VLAN and trunk port:
I didn't say it would.. Dude you and your running vlans over a dumb switch.. Get over it already.. It has nothing to do with the switch won't strip them... Its the fact that it won't actually isolate the traffic like it should ;)
I wasn't advocating one way or the other re using VLANs, although I do recommend them. My issue is with those who seem to think there's something magic that keeps a dumb switch from passing tagged frames, when the difference between tagged and untagged is the contents of the Ethertype field, which a dumb switch is incapable of even recognizing, let alone blocking.
-
I have had non-dot1q gear refuse to pass dot1q frames. If the spec sheet doesn't say 802.1q, you get what you get if you try to pass dot1q frames with it. Don't expect a lot of sympathy here if it doesn't work for you or you have strange problems.
-
@Derelict said in Setting up pfSense for VLAN and trunk port:
I have had non-dot1q gear refuse to pass dot1q frames.
How was it doing that? In order to block a tagged frame, it has to recognize it. I don't see an unmanaged switch doing that. A switch is supposed to pass all valid Ethernet frames, regardless of the Ethertype/length field contents. On the other hand, a managed switch could be configured to block them.
-
No idea, dude. Untagged would pass, tagged wouldn't. It was a MoCA bridge that has since been punted downrange with prejudice.
-
Whatever you decide to do make the 3rd octet of the IPv4 addresses ( assuming your using /24s ) the VLAN ID, makes things easier in the long run

-
The switch chips used may support tagging, so the default behaviour is depending on the setup the manufacturer uses. This can vary from batch to batch as they often change chip vendors or the setup. The behavior of a cheap unmanaged switch and a cheap smartmanaged/managed switch of the same vendors can be identical/with little difference. Most low end switch chips support tagged frames, the setup is stored in the eeprom or microcontroller but it's not always the case. for the others vlan tag are considered invalid frames
-
@kiokoman said in Setting up pfSense for VLAN and trunk port:
The switch chips used may support tagging
What's to support? A tag is simply a different Ethertype and 4 more bytes. Since a switch is supposed to pass all Ethertypes, why should it block VLAN?
Take a look at an Ethernet frame. It has the destination and source MACs, Ethertype/length, payload and CRC. That's it. Why should an unmanaged switch consider the VLAN tag or any other Ethertype?
On the other hand I have come across some computers (notebooks) that don't support VLANs.
Incidentally, I'm probably the only one here who's actually hand wired an Ethernet controller. A bit over 30 years ago, I wired up a couple on prototyping boards for Data General Eclipse computers.
-
sorry it was not clear, the setup stored in the eeprom or microcontroller tell the chip to consider vlan tag invalid frames or not. so you can possible end up with a unmanaged switch that make it pass or not.
-
@kiokoman said in Setting up pfSense for VLAN and trunk port:
sorry it was not clear, the setup stored in the eeprom or microcontroller tell the chip to consider vlan tag invalid frames or not. so you can possible end up with a unmanaged switch that make it pass or not.
Why would an unmanaged switch even care? What's it supposed to do, if it's unmanaged? In order to not pass a frame, the switch would have to read the Ethertype field and say I don't want to pass this. Why go to all that trouble, when a switch is supposed to pass all Ethertype/length values?
BTW, in those Eclipse computers I used to work with, I actually worked at the microcode level, which is the programming within the CPU. Those systems used 4 AMD 4 bit slice processors to create a 16 bit CPU.