Multiple Interface DNS Rule Configuration
-
Good evening,
I have multiple (OPT1, OPT2) interfaces on my firewall which I am working to keep segregated where appropriate. Here are my rules for the LAN interface for DNS.
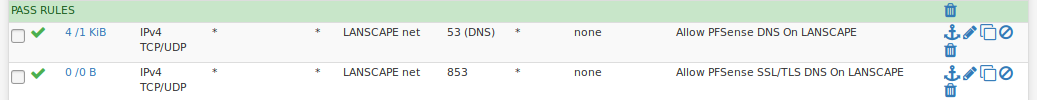
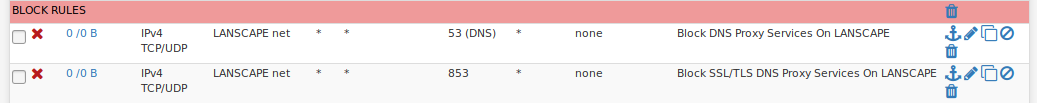
Does anyone have any suggestions on ways to improve this setup for each interface? Any issues? I have identical rules on each interface. It seems to be working, as all DNS is being forced to the servers I specify in the general setup section.
Interestingly, I've found some things don't work if you don't allow them to try and use a proxy. Phillips Hue lighting, for one... Without a firewall exception they lose internet with those rules. And that's the reason I want to restrict these things from other areas of the network. They have some hard-coded shenanigans.
Thanks in advance!
-
Which interface do you have those rules on?
You have allow to lanscape net - which is what interface?
And then block with source of lanscape net??Rules are evaluated on the interface the traffic enters pfsense on.. So if you don't want lanscape going somewhere the rules would be on the lanscape interface.
They are evaluted top down, first rule to trigger wins, not other rules are evaluted... When you post your rules - please post ALL of them, and what interface they are on.
-
All those rules are on the LAN in that order. I just have it named LANSCAPE for the hell of it.
The idea is that if the DNS is destined for the interface itself it allows it... If the DNS request is headed anywhere else it is blocked. I only want the DNS requests served by those defined in my general tab.
Not sure I’m thinking right about how to go about it though.
Steve
-
That would be lanscape address then, not net
But looks like your missing some rules there.. Since nothing would work with just those rules other than dns. Which is why you need to show ALL the rules, since they are evaluated in order.. So you have to see all of them.
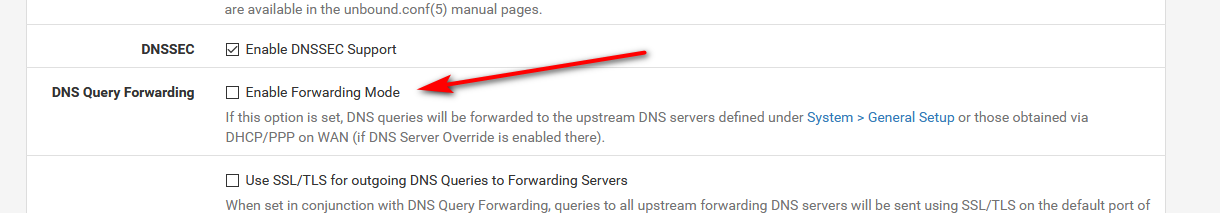
Your general tab doesn't have anything to do with it, if you are using unbound (resolver) out of the box it resolves - it doesn't forward..
Also btw dot or dns over tls (port 853) would be tcp, not udp.
-
Thanks for the help with this... Keep in mind, I'm just learning as I go here.
There are more rules obviously. LOL. I have left the default "pass all" rule at the bottom of my rules list while I'm configuring/learning. My goal (and to keep things working while I mess around) is to gradually add rules above that "pass all" rule to pass or reject traffic until, eventually, that generic rule isn't needed. Eventually I will reach a point where that last rule isn't capturing anything, and I have made a deliberate decision about each type of traffic as I get to that point.
Wikipedia shows port 853 as "official" for TCP and UDP which is what I selected. Am I missing something?
Again, thanks for putting up with us over-ambitious home users.

Steve
-
-
And again those don't do anything... Out of the box pfsense resolves, it doesn't forward...
If you do not show me all the rules... I can not help you.
dns over tls does not use UDP... It only uses TCP.. now there is another protocol DNS-over-DTLS (DNSoD) which could use udp..
-
These are what I have on the LAN...
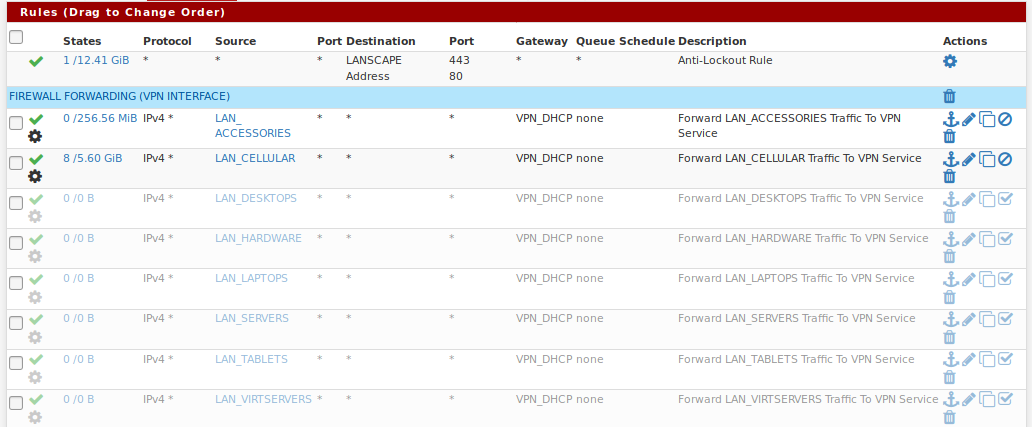
The anti-lockout rule which I'd like to kill eventually. And a series of forward rules which allow me to forward different classifications of devices out to the VPN on demand.
Then pass/block rules...
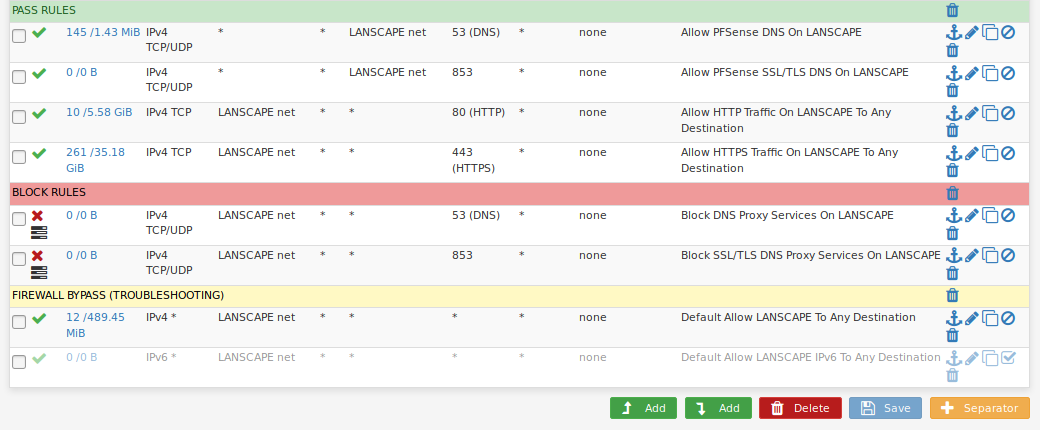
These basic rules seem to catch most everything, but there is still some stuff the "pass all" rule has to deal with.
As for the DNS rules, they are working, because on every device which I don't force to VPN, only Cloudflare is returning DNS results. 1.1.1.1
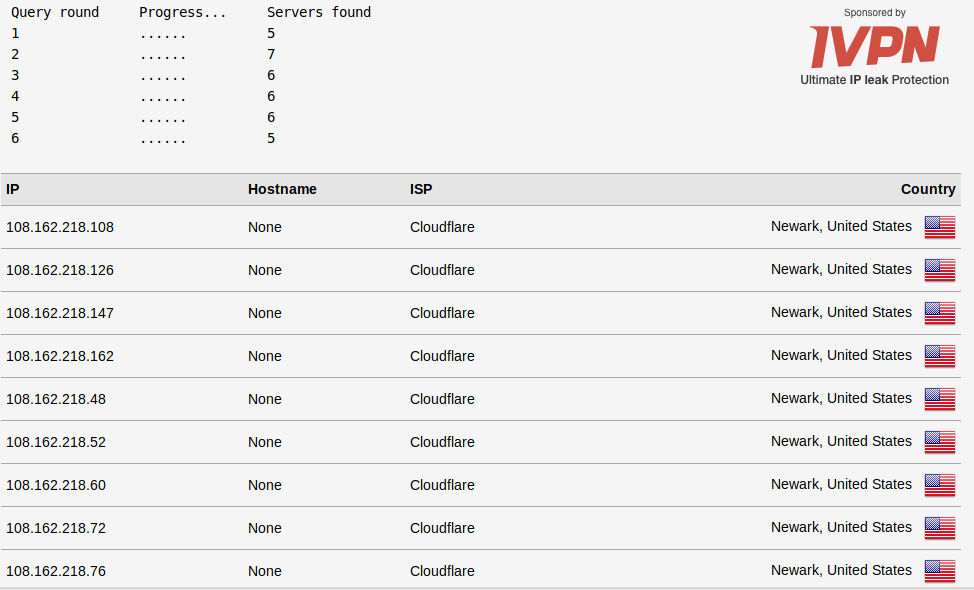
I'm not forwarding DNS, I've entered the list of servers I want to use for DNS in the section that is there to enter DNS servers you want to use. The rules should simply be allowing traffic following those guidelines, and blocking any tricky devices trying to proxy their DNS requests around what I've configured.
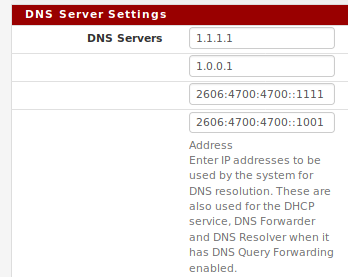
The general foundation seems to be working, but I want to get opinions about my overall structure before I get serious about making all the necessary rules and disabling the default ones.
Thanks.
-
@wormuths said in Multiple Interface DNS Rule Configuration:
I'm not forwarding DNS
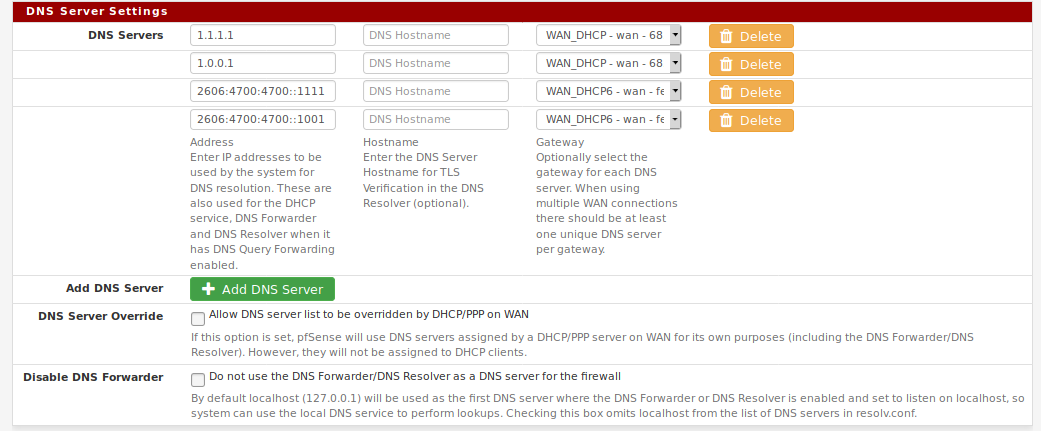
Then those IPs would not be used!!! You must be handing those IPs to clients via dhcp, or your setting them static, or the clients are using those on their own via some other means. If cloudflare is showing up that test.
Out of the box pfsense dhcp will only hand out its OWN ip for dns, unless you turned off unbound, forwarder, etc services.. Then it will hand out what you put in there, or what it got from dhcp on its wan..
The note on the bottom clearly states how they are used. Those could be used by pfsense, if say the local service crashed.. But if a client ask pfsense, it will resolve - it will not use those..
-
I'm not arguing with you. It's very possible I'm not understanding how this process works in pfSense on some fundamental level. I'm trying to ensure that I'm on the right path, and what I have configured seems to be working.
I have DHCP on each interface. I only give it a small range to assign for initial connections, guest access, etc. Anything I'm permanently adding to the network gets statically assigned by DHCP an IP in the range of the appropriate alias so rules will take over using those alias'...
From there, I simply wanted to prevent questionable devices like home automation gadgets from doing any funny business, so I started with DNS. I want to force these devices to use 1.1.1.1 as their DNS service. I told pfSense to use 1.1.1.1 and created rules which A) allow DNS heading to the interface itself, and B) block DNS heading anywhere else.
Is that incorrect? If it is, why are my DNS queries heading to 1.1.1.1 as I have configured?
Thanks again for the insight.
-
Out of the box pfsense resolves, and yes clients can ask it for dns on its IP.. And it will then resolve what they ask..
it will walk down from roots to find the authoritative nameserver in question, and then ask that ns for whatever.domain.tld your looking for.. it does not forward anywhere.. No matter what you put in the dns servers under general.
The only time those would/could be used is if pfsense itself is looking for something.
If you want unbound to forward to 1.1.1.1 then you have to tell unound to forward.