Captive portal ignoring MACs in latest version and allowing all machines access
-
@theworkingcentre said in Captive portal ignoring MACs in latest version and allowing all machines access:
removing all MAC address listings does NOT fix the problem
Question: are you using a custom Captive Portal login page? Or the stock firewall login page?
Thank you -
@h2professor It is a custom login page.
Unlike your situation we do ask for a username and password, using the local database.
-
@theworkingcentre said in Captive portal ignoring MACs in latest version and allowing all machines access:
It is a custom login page
If it's no trouble, may I suggest that you delete your custom page and see if the problem resolves without it?
In a non-production setup last July (with the same configuration) we ended up in a situation where everything was working until we added the custom page. If this happens with yours as well, then we might narrow down the problem a bit.
Thanks -
No, when I delete the custom login page and use the default I get the same behavior.
-
@theworkingcentre said in Captive portal ignoring MACs in latest version and allowing all machines access:
I get the same behavior
okay thank you for trying. We'll proceed with our testing here and will share anything that might be useful.
Cheers -
@h2professor said in Captive portal ignoring MACs in latest version and allowing all machines access:
Nobody in this forum believes there's a real problem,
You had side-long talks in this topic about your problem and say nobody believes you? I find that hard to believe.
As the last of this was talked about in June/July, did you @h2professor ever try to re-create the steps manually to "create" the problem you have?
After reading through, I was always stuck with "and then I re-imported my whole/part of my config and the problem was back". Is it possible to re-trace the steps for the problem to appear? As @Gertjan said: seeing is (no, not believing) half way to fix a potential bug. But as this always re-appeared after updating/re-importing the config I'm wondering if it's a problem with the configuration as it is.
Also did anyone try and open a bug report at the pfsense redmine and link this thread? Might be helpful for hunting down a potential bug!
https://redmine.pfsense.org/projects/pfsense/issues -
@JeGr said in Captive portal ignoring MACs in latest version and allowing all machines access:
I find that hard to believe
How ironic.
We tried everything that was suggested, but the client ran out of patience for the problem, so we were forced to use the last working cold mirror to get it back online.
Here's a summary:
It worked prior to 2.4.4-p3. It has worked for years.
We upgraded to p3: it no longer works.
We did a clean installation of p3: confirmed captive portal works as advertised in a basic installation on the hardware.
We imported the original configuration: no longer works.
We did a clean installation of the older 2.4.4-p1 and imported configuration: worked just fine.
We tried dozens of suggestions, including removing packages, reinstalling, cutting sections out of the configuration, etc.We had to conclude that the problem is in version 2.4.4-p3 despite people insisting that "no changes were made to the captive portal section" bla bla bla. Hence, it's not a believable problem.
I have a week with the client out of their building so I have time to figure this out, if it is possible.
-
Well, I solved the problem in my installation, but I expect it won't help @h2professor . We have some allowed IPs in "Allowed IP addresses." One of our local IPs was listed there. However, that dialog allows you to set a subnet mask, and the IP in that subnet had been set to /24, not /32. So it was allowing the entire subnet through!
In the process of finding this, I rebuilt my captive portal:
- I created a dummy interface and assigned the old captive portal there.
- I made the configurations the same for the new portal.
- I added all of the IP addresses and hostnames (but idiot that I was, I inadvertently used a /32 for the offending IP in my new build, and not a /24 like in the old one)
- I added the allowed MAC addresses one by one
- I re-added my custom login page
and sure enough the new portal worked, but the old one didn't. (I tested the new captive portal after adding each component, hoping to find the one that broke the build.)
I also exported the captive portal config for these two captive portals and compared them, but I was not able to see any significant differences.
The only thing that occurred to me was whether there might be a duplicate MAC address in the list? Due to a copy and paste error when transcribing entries I thought I had one. The current pfSense interface will not let me add a duplicate MAC address, but maybe some old one did?
-
It is not quite true to say that the XML for the two captive portal backups were identical. There were some extra lines in the old one that were not present in the new one:
<radius_protocol></radius_protocol> <redirurl></redirurl> <radiusip></radiusip> <radiusip2></radiusip2> <radiusip3></radiusip3> <radiusip4></radiusip4> <radiusport></radiusport> <radiusport2></radiusport2> <radiusport3></radiusport3> <radiusport4></radiusport4> <radiusacctport></radiusacctport> <radiuskey></radiuskey> <radiuskey2></radiuskey2> <radiuskey3></radiuskey3> <radiuskey4></radiuskey4> <radiusvendor>default</radiusvendor> <radiussrcip_attribute>wan</radiussrcip_attribute>(
redirurlis actually in both).I notice that
radiussrcip_attributeis set towanin my listing and set tolanin yours. I tried changing mine toopt1(my captive portal interface) in my backup file and restoring, but it made no difference. -
@theworkingcentre said in Captive portal ignoring MACs in latest version and allowing all machines access:
I solved the problem in my installation
That's excellent work, thank you very much. We're going to try that. It's something we haven't considered. I'll report back in a couple of days.
Cheers -
@theworkingcentre said in Captive portal ignoring MACs in latest version and allowing all machines access:
I notice that radiussrcip_attribute is set to wan in my listing and set to lan in yours. I tried changing mine to opt1 (my captive portal interface) in my backup file and restoring, but it made no difference.
When the config file version moved from 18.6 to 18.7 (august 2018), that's several updates in the past, we're 19.1 now - "radiussrcip_attribute" was created and set to 'wan' as de default value.
It's a radius related setting, and if radius isn't used it isn't important.
<captiveportal> <cpzone1> <zone>cpzone1</zone> <descr><![CDATA[cpzone1]]></descr> <zoneid>2</zoneid> <interface>opt1</interface> ...... <radiussrcip_attribute>opt1</radiussrcip_attribute> ...... </cpzone1> </captiveportal>I'm using FreeRadius - my portal is running on OPT1.
-
@h2professor said in Captive portal ignoring MACs in latest version and allowing all machines access:
We had to conclude that the problem is in version 2.4.4-p3 despite people insisting that "no changes were made to the captive portal section" bla bla bla. Hence, it's not a believable problem.
People don't "insist" anything. My post also wasn't meant as an insult or attack, I was simply wondering why you wrote that. The devs simply said in another thread, that they did check the portal code and there was no commit or anything else belonging to the portal code in between -p1 and -3. So it either has to be a dependency like e.g. radius or some other thing that links into the portal like IP lists etc. what @theworkingcentre wrote.
I also am not "ironic" but I find it quite a bit "unfair" to write sth like "nobody believes me" after page-long tries to help you debug the problem Also your list in "things we did do" lists "importing the configuration" EVERY time. So like I wrote above, how about simply debugging the thing with a fresh installation and configuring step by step the way it is now in your clients environment? Why do you insist of always importing the config.xml when it could very well be some thing that doesn't get imported the right way or perhaps was a problem with importing and updating this installation every time? I had small problems like that a few times. Rarely but they do exist. Changes in config format and old configs that have some duplicate lines or sth along those lines.
So why not trying one of this things instead of being sarcastic yourself and accuse us for doing "nothing"? At the end of the day we are simply other users and/or private persons here. This is not the official Netgate pfSense bug tracking support system.
And as much as I would like to see you/us succeed in tackling that problem: If your client is that sensitive and you have that narrow a margin in errors, wouldn't it be a better job to buy support for that device and ask the devs to have a look / fix it in your client's setup instead of getting angry with us for trying to help you? Or at least before going the support route submit that case with all details as a an official bug in the bugtracker? Sorry, I'm just trying to help here. And I'm not related or employed by Netgate after all. :)
Best wishes!
-
I"m still reading here .... trying to figure out.
Last couple of weeks I loaded a Hyper-VM on my 2012 Win server, it has 3 NIC's, so I can simulate and test without disturbing my companie network. Also : I'm using a second PC @home loaded with pfSense (using VM also).
Detail these 2 phrases :
@h2professor said in Captive portal ignoring MACs in latest version and allowing all machines access:
After, with 28:c6:8e:0f:95:9b set to Block
after.txt
I note that the MAC is not found in the second output.As soon as the captive portal is activated on an interface, everybody (MAC, IP, whatever) is blocked.
Even when you have this :
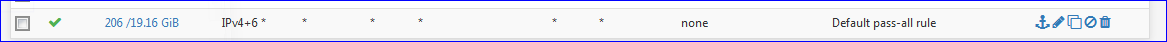
on the LAN interface.ipfw takes precedence of the ip firewall. ip being the firewall you set up with the GUI.
When you add a MAC on the MAC tab as a "pass" , this MAC will be part of your table "default_pipe_mac":
02100 145763334 141217081935 pipe tablearg ip from any to any MAC table(default_pipe_mac)This is a snaphot of your "default_pipe_mac" :
dc:ef:09:9b:a8:c0 any 2671 1155484 1699152753 1560263421 any dc:ef:09:9b:a8:c0 2670 11 0 1560262129You can see the MAC, the pipe rule numbers 2670 (down) and 2671 (up) and the number of bytes received and send.
These are the related pipe rules 2670 and 2671 :
..... 02670: unlimited 0 ms burst 0 q133742 100 sl. 0 flows (1 buckets) sched 68206 weight 0 lmax 0 pri 0 droptail sched 68206 type FIFO flags 0x0 16 buckets 0 active ..... 02671: unlimited 0 ms burst 0 q133743 100 sl. 0 flows (1 buckets) sched 68207 weight 0 lmax 0 pri 0 droptail sched 68207 type FIFO flags 0x0 16 buckets 0 active ...Both are unlimited pipes.
Btw :
I found one (just 1) speed limiting (half a mega / s )pipe :02223: 500.000 Kbit/s 0 ms burst 0 q133295 100 sl. 0 flows (1 buckets) sched 67759 weight 0 lmax 0 pri 0 droptail sched 67759 type FIFO flags 0x0 16 buckets 0 activePipe 2223 : so this is device
28:c6:8e:0f:95:9b any 2223 11722 14806366 1560263421 any 28:c6:8e:0f:95:9b 2222 2 0 1560262183is speed limited - this is the only device I found that was limited speed.
The blocked MAC list : as you might have understand, MAC's that are blocked are not present in the ipfw tables and rules.
When you add a MAC as blocked, it's been put in a list handled by the GUI.
The Captive portal web server, when intercepting a (in your case : http) visitor web browser http requests, are redirected to this page page :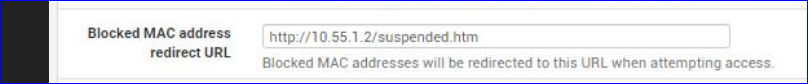
(some conditions have to be met, like this page must is on the same LAN segment as the captive portal - there must be a http web server that can serve the page, etc - it might, it might not. For me, using an iphone, it didn't redirect well )
If no URL, the device is blocked, for any IP, for any port, for any protocol.
But : when a MAC isn't present on the MAC tab, or it's set as a red block, it won't pass.
I advice you to use and old PC to test - make sure there is a second NIC, and setup pfSense for yourself. Although I strongly advise you to use a captive portal on a dedicated - OPT1 - NIC, and leave the LAN for administrative purposes.
When applied the minimal setup as per Netgate's video (there are 3 videos on Youtube, the Netgate channel, take a recent one that handles basic operations) no device can connect, and they will show the default Login when you use a web browser on a visiting device. https restrictions might apply.
Now, when you add ONE MAC as a pass, this device can pass to the net. Right ?
Still, no other device can pass. Right ?
Add another MAC as a pass. It passes right ?
An still, no other devices can pass.
For the fun, add a MAC of a device that you own, as a BLOCK. It can not pass, right ?
And again, other, non listed MAC's still can't pass.
Etc etc.You could even import your entire "300 MAC" list.
I would do this by exporting the config.xml - then use notepad++ to insert the block of.... <passthrumac> <action>pass</action> <mac>xx:8d:79:91:ec:52</mac> <bw_up></bw_up> <bw_down></bw_down> <descr><![CDATA[Sophie]]></descr> </passthrumac> <passthrumac> <action>pass</action> <mac>7c:bb:35:f2:a9:0e</mac> <descr><![CDATA[Serge Nouveau portable]]></descr> </passthrumac> .....in the correct section, and import that file back in again.
Still, unlisted device you own can't pass as they are not part of the list.
I ended up listing all my devices (9) as blocked : they didn't pass.
I removed them from the MAC tab, so not listed as a pass or block : they still didn't pass.Btw : do not hesitate to reset firewall states. I don't know if it is really needed, but it would harm to reset they all the time, after changes.
My main question is : can you replicate your issue on a barebone system, after a manual minimal setup.
And if so, after which change your issue happens ?Also : export your
.... <passthrumac> <action>pass</action> <mac>xx:8d:79:91:ec:52</mac> <bw_up></bw_up> <bw_down></bw_down> <descr><![CDATA[Sophie]]></descr> </passthrumac> <passthrumac> <action>pass</action> <mac>bb:bb:35:f2:a9:0e</mac> <descr><![CDATA[Serge Nouveau portable]]></descr> </passthrumac> .....section, and drop it in here.
Mistify all MAC's be replacing the first byte by placing 'bb', as I did above.I'll import your list.
I wonder if I see the issue then ...