Subnets not reachable on created VLANs
-
So I realize I have a little bit of a complicated setup here. I've gone this route because I'm working with the hardware that I have at the moment but am open to suggestions to achieve ways to serve up multiple separate networks that have different gateways. I know I'm close with VLANs...probably just missing a setting in ESXi maybe...
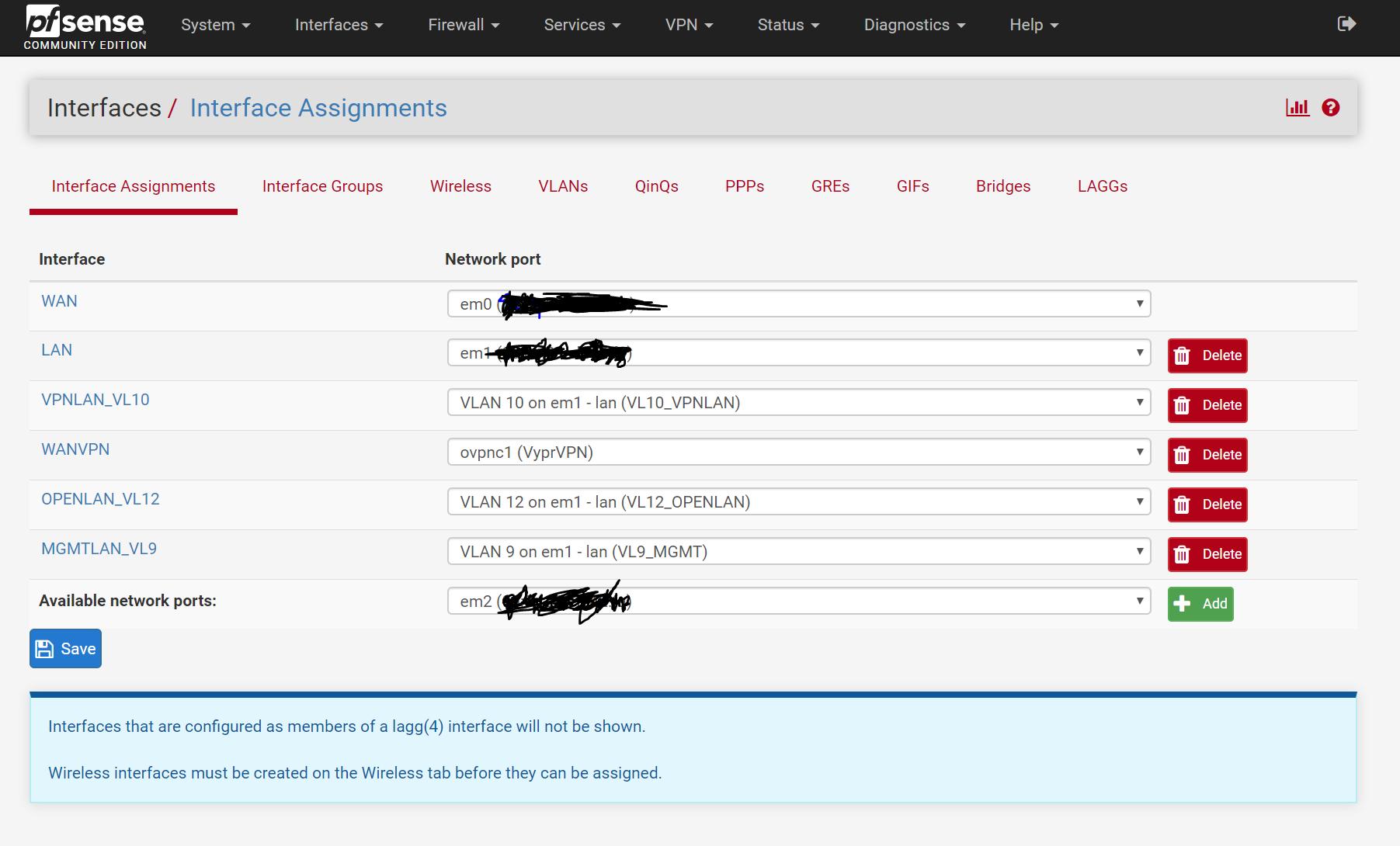
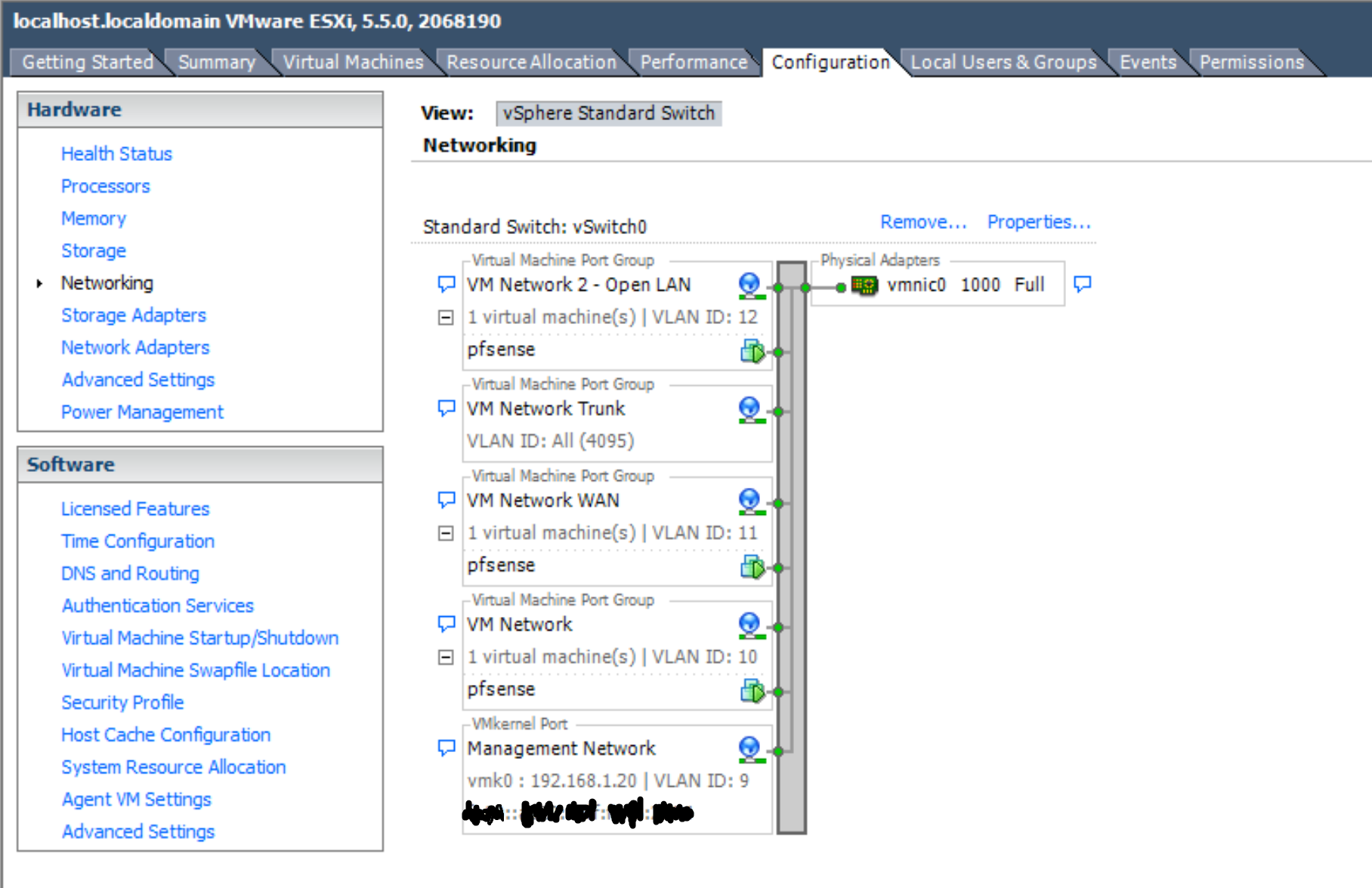
I have Pfsense running virtualized in ESXi on a Mac Mini with 1 NIC. I have not been able to get the Thunderbolt NIC working with this host. I am exercising VLAN trunking so that I can use the single NIC as both the WAN interface and as an interface to the LAN and VLANs. I have what I believe is a Layer 2 switch (the Netgear GS108PE) and have configured the 802.1Q VLAN settings on the switch, in Pfsense and in the vSphere management portal for ESXi.
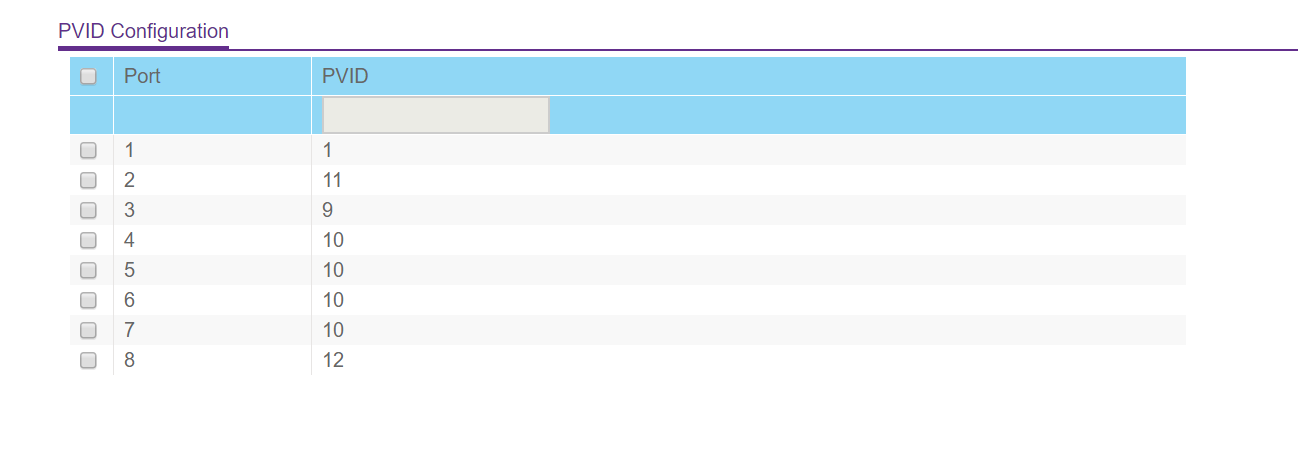
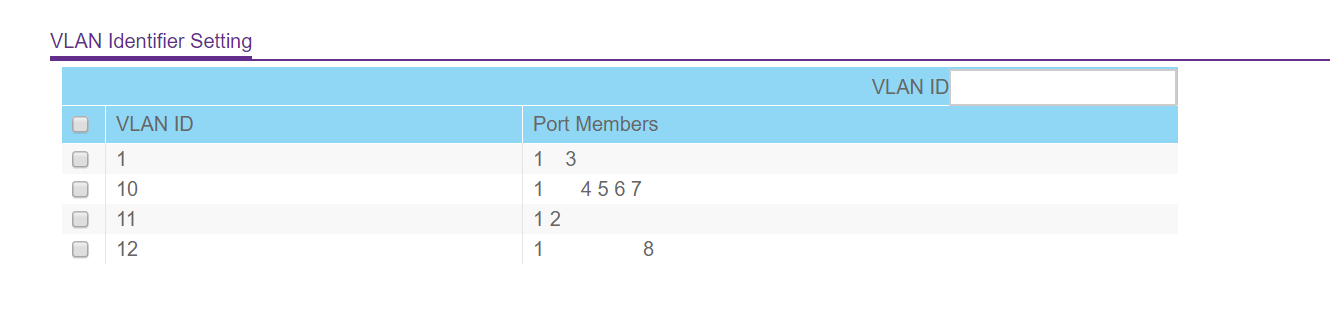
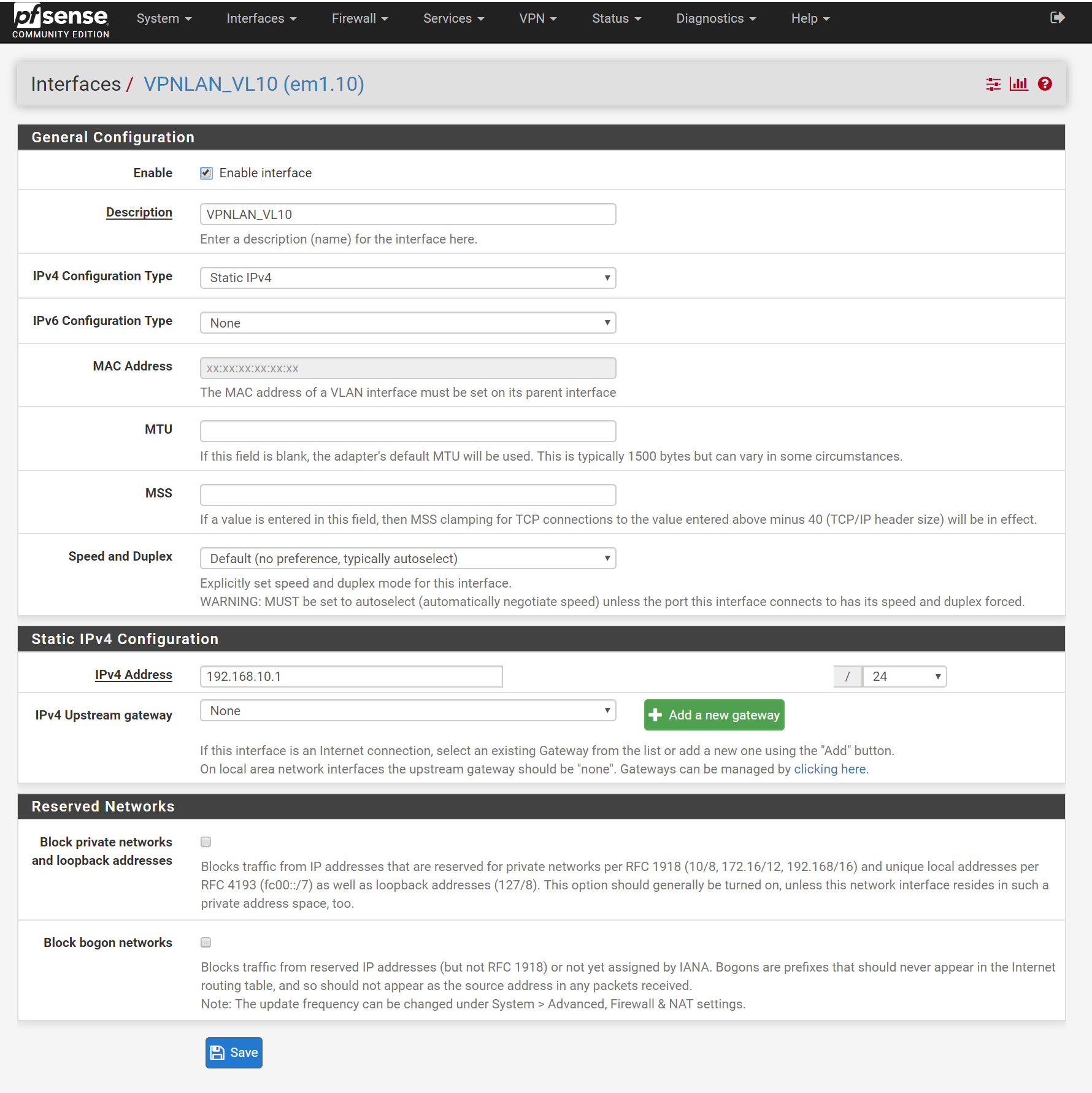
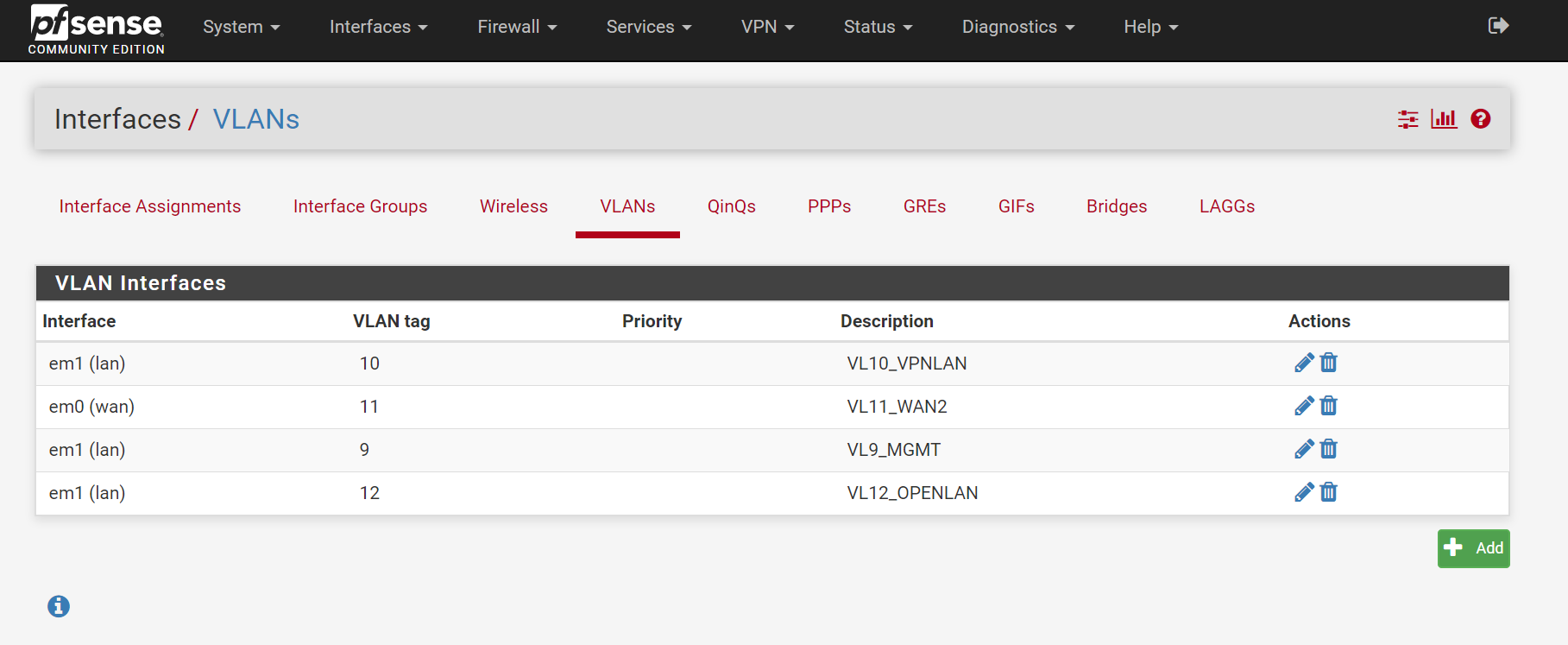
VLAN 10 is for what will be my VLAN subnet that goes through my OpenVPN gateway (tagged on physical switch port 1). VLAN 11 is for my WAN connection (tagged on 1 as well since that is the trunk port). VLAN 12 is for my 'CLEARNET' VLAN that will eventually go around the OpenVPN gateway and instead go straight to my ISP. I think I needed to give port 3 a different PVID so I can talk to my switch on a different subnet.
Here's my problem description: right now, the LAN interface in Pfsense is serving up IPs with DHCP on 192.168.1.1. What is strange to me is why I am getting an IP in this subnet on any untagged port on my switch. Shouldn't the other ports 4 through 7 work on the subnet I have defined in the virtual interface that is connected with VLAN10?
In practice, if I set those clients to DHCP, they get a lease from 192.168.1.1. If I disable the DHCP server on the LAN interface and enable DHCP on all the virtual interfaces associated with a VLAN, I'm unable to access the internet. If I set them to a static ip in 192.168.1.x, they can't reach the Pfsense management portal (expected since it appears that part of my setup is working), but they also can't reach my WAN. I also have a firewall rule to allow any protocol to allow anything from the VLAN10 virtual interface to any destination. I also tried disabling the firewall altogether but I think this is a switching or VLAN configuration issue.
At this point I am really truly completely lost and would really appreciate any help I can collaborate with the community here on. Thank you!
-
Take note I'm not completely versed in the whole OSI model and differences between Layer 2/3 switches and am picking this all up as I go, so if I'm doing something silly feel free to explain the simple bits.
-
Here is my VLAN page in Pfsense:
-
@RPisces said in Subnets not reachable on created VLANs:
Here's my problem description: right now, the LAN interface in Pfsense is serving up IPs with DHCP on 192.168.1.1. What is strange to me is why I am getting an IP in this subnet on any untagged port on my switch. Shouldn't the other ports 4 through 7 work on the subnet I have defined in the virtual interface that is connected with VLAN10?
What do you have for the LAN? Normally that would be native, not VLAN. Then anything on it would appear at any untagged port.
-
Why are you creating vlan port groups in esxi and attaching this to pfsense.. But your running pfsense vlans on em1.. This would be connected to your 4095 port group if you want pfsense to see and work with the tags. The 4095 setting tells esxi not to strip tags.
If your going to set a vlan ID on a port group in esxi, then that tag would be stripped and pfsense would never see it, so the interface in pfsense would be native and connected to that port group.
-
@JKnott I don't know if I understand all of your question properly but I believe you're asking something similar to what johnpoz has.
I'll try to answer you but also direct my response at johnpoz.
So @johnpoz, i was wondering about that, but when I configure the ESXi virtual switch (not my physical switch) for what I believe is called native VLAN (single portgroup with 4095 set to the VLAN ID right?), this is what you recommend? Then remove the other VLAN portgroups in my virtual switch settings? I guess that makes sense now that I think about how VLAN tagging works at the switch level.
If I do this, I think I just have to have the 802.1Q VLAN trunking driver installed in my guest, Pfsense? Or should it just work? You're referring to ESXI VGT mode for VLANS and I've seen VST referred to (where you configure the VLANs as portgroups too in the virtual switch) but it just seems simpler and more logical to do it the VGT way as you described. I haven't been able to find information on where to find this driver (I do have the VMWare tools package installed in Pfsense if that is a part of it) so I'm just going to give it a try.
I'll give the VGT mode a try. It would be nice because then I don't have to open the ESXI client tool every time I need to change how my VLANs are laid out. I also have an issue where the ESXI webui portal has no permissions to make any changes to my configuration, so I'm stuck with having to use this ESXI management program.
Thanks for the input, I'll get back within the next day or so when I am back in my home office.
-
You sure do not need to install any drivers in your guest for 4095 to work.. When I ran pfsense on esxi, I used both methods.. It has some interfaces that were native, and other that were tagged and connected to 4095 port group..
Or you could just create a bunch of port groups and more vnics for pfsense and connect them to the different port groups. All comes down to how you want to skin the cat.
-
@RPisces said in Subnets not reachable on created VLANs:
I don't know if I understand all of your question properly but I believe you're asking something similar to what johnpoz has.
If you were to set up any firewall/router, you would have your LAN, which all your computers etc. attach to on the native or untagged LAN. Do you have that? I don't see it mentioned anywhere in your description. Also, given you don't know the difference between L2 & L3, I suspect you're tackling something beyond your abilities. L2 refers to Ethernet and is where switches operate. L3 is IP and where routers work. I get the impression you're making things overly complex because you do not understand how things work.'