Android saying "Connected, no Internet"
-
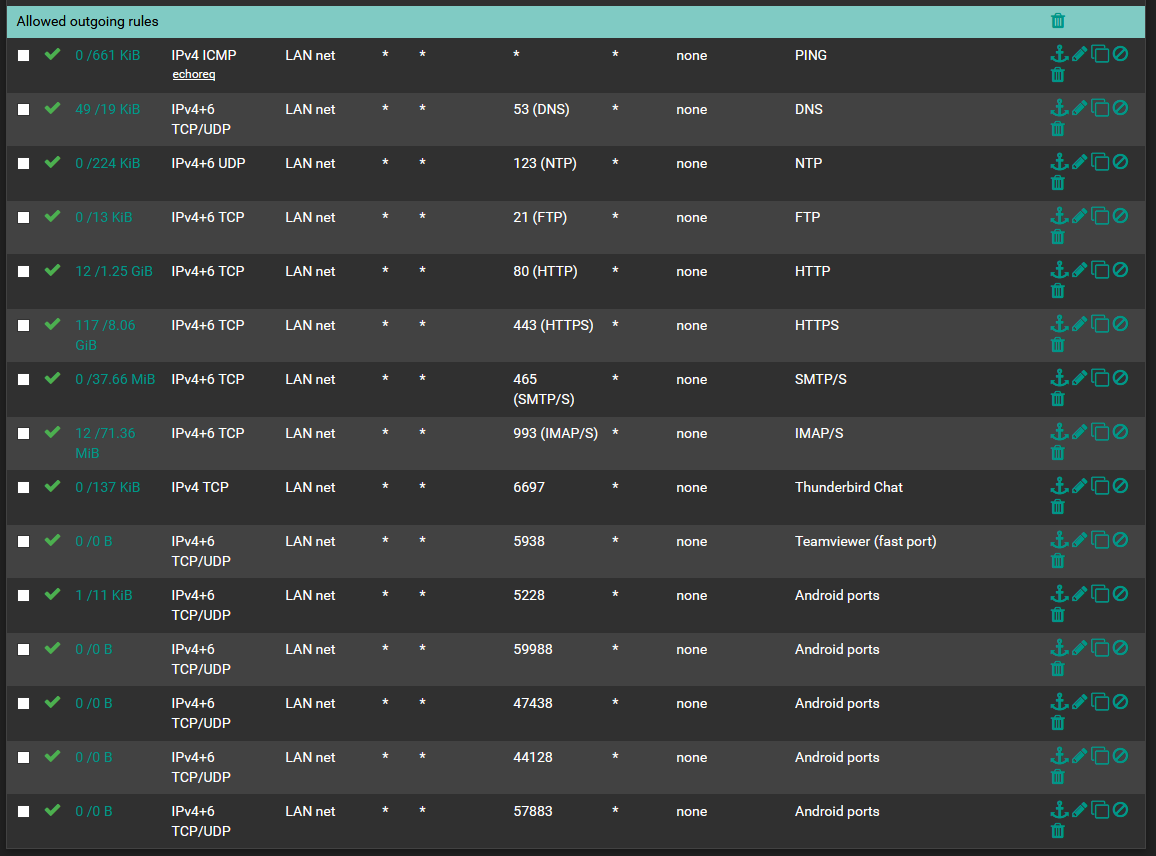 image url)
image url)been testing with ports at bottom. but not working.
-
rules are processed from the top down, stopping at the first match, so i hope you don't have anything over "Allowed outgoing rules"
-
@kiokoman i have a block on one LAN ip, because its xp machine lol
but yes allow is on that order. PCs work fine on ethernet.
and also PCs work fine on WIFI
its just android saying "connected, no internet" even if i open up the ports i see being logged.
recon if theres anyhting in ICMP required?
-
what version of pfsense are you running?
-
@kiokoman
2.4.4-RELEASE-p3 (amd64)
built on Wed May 15 18:53:44 EDT 2019
FreeBSD 11.2-RELEASE-p10i keep seeing random ports being blocked. when i open said ports and retry it cahnges to differenet ports
-
more info
my wifi AP is a DD-wrt router in AP mode, connected to pfsense via network switch
i have windows 2019, acting as AD, DNS, NTP, DHCP
AP and pfsense is ported to win server for all the above.
-
android always try to go to different services (whatsapp / play store / google drive / huawai is probably stealing your data and sending it to china / samsung do the same but at least they tell you / etc etc )
you should check if dns is working
maybe try to disable ipv6 for the moment and see if it work via ipv4 only
check day and time on your phone .. -
I think you are confusion source port with destination port.
Client's will almost always use a random source port to communicate with a well known destination port. Furthermore the firewall may reassign a random source port to the connection on the WAN side as well.
For instance, in your packet capture list presented earlier, we can see host 10.1.1.20 source port 59988 communicating with a Google IP 172.216.169.68 on port 443.
Return traffic is going to be implicitly allowed, this is the purpose of a stateful firewall. It knows and recognizes an allowed outbound connection and expects that return traffic is going to come back to the request and it will allow it, but only if there was an initial outbound connection. Basically, it doesn't just leave stuff open from outside unless you've initiated a connection. -
@kiokoman
ipv6 is disabled by defaultive got custom rom,
i see android is trying to get a google IP, then trys a DNS ip15:57:40.216282 IP 10.1.1.20.47570 > 172.217.169.67.80: tcp 0 15:57:40.216322 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0 15:57:40.229403 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 0 15:57:40.230392 IP 172.217.169.67.80 > 10.1.1.20.47570: tcp 0 15:57:40.379510 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0 15:57:40.379569 IP 10.1.1.20.47570 > 172.217.169.67.80: tcp 0 15:57:40.380885 IP 10.1.1.20.47570 > 172.217.169.67.80: tcp 232 15:57:40.381306 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 180 15:57:40.394470 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 0 15:57:40.394901 IP 172.217.169.67.80 > 10.1.1.20.47570: tcp 0 15:57:40.394910 IP 172.217.169.67.80 > 10.1.1.20.47570: tcp 83 15:57:40.402846 IP 10.1.1.20.47570 > 172.217.169.67.80: tcp 0 15:57:40.405092 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 1418 15:57:40.405522 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 1133 15:57:40.424643 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0 15:57:40.429217 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0 15:57:40.446462 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 85 15:57:40.460026 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 276 15:57:40.465991 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 238 15:57:40.479929 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 152 15:57:40.530769 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0 15:57:40.557255 IP 10.1.1.20.44262 > 1.0.0.1.853: tcp 0 15:57:40.557306 IP 10.1.1.20.58017 > 1.1.1.1.853: tcp 0 15:57:41.569937 IP 10.1.1.20.58017 > 1.1.1.1.853: tcp 0 15:57:41.571296 IP 10.1.1.20.44262 > 1.0.0.1.853: tcp 0 15:57:43.647856 IP 10.1.1.20.58017 > 1.1.1.1.853: tcp 0 15:57:43.648647 IP 10.1.1.20.44262 > 1.0.0.1.853: tcp 0 15:57:47.594139 IP 10.1.1.20.58017 > 1.1.1.1.853: tcp 0 15:57:47.595599 IP 10.1.1.20.44262 > 1.0.0.1.853: tcp 0 15:58:31.207046 IP 10.1.1.20.47575 > 172.217.169.67.80: tcp 0 15:58:31.207078 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 0 15:58:31.220075 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 0 15:58:31.220821 IP 172.217.169.67.80 > 10.1.1.20.47575: tcp 0 15:58:31.224669 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 0 15:58:31.405049 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 517 15:58:31.418632 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 0 15:58:31.418643 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 154 15:58:31.500980 IP 10.1.1.20.47575 > 172.217.169.67.80: tcp 0 15:58:31.501001 IP 10.1.1.20.47575 > 172.217.169.67.80: tcp 232 15:58:31.512938 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 0 15:58:31.512958 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 43 15:58:31.514883 IP 172.217.169.67.80 > 10.1.1.20.47575: tcp 0 15:58:31.514914 IP 172.217.169.67.80 > 10.1.1.20.47575: tcp 83 15:58:31.521415 IP 10.1.1.20.47575 > 172.217.169.67.80: tcp 0 15:58:31.529562 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 0 15:58:31.820584 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 238 15:58:31.833817 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 0 15:58:31.833848 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 152 15:58:32.062625 IP 216.58.206.100.443 > 10.1.1.20.53303: tcp 152 15:58:32.198460 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 0 15:58:32.553957 IP 10.1.1.20.53303 > 216.58.206.100.443: tcp 0 15:58:32.900797 IP 10.1.1.20.58020 > 1.1.1.1.853: tcp 0 15:58:32.900812 IP 10.1.1.20.44267 > 1.0.0.1.853: tcp 0 15:58:33.930800 IP 10.1.1.20.58020 > 1.1.1.1.853: tcp 0 15:58:33.930813 IP 10.1.1.20.44267 > 1.0.0.1.853: tcp 0 15:58:35.795403 IP 10.1.1.20.58020 > 1.1.1.1.853: tcp 0 15:58:35.796295 IP 10.1.1.20.44267 > 1.0.0.1.853: tcp 0 15:58:39.959164 IP 10.1.1.20.58020 > 1.1.1.1.853: tcp 0 15:58:40.047545 IP 10.1.1.20.44267 > 1.0.0.1.853: tcp 0 -
@Solway said in Android saying "Connected, no Internet":
im just locking down LAN so i know whats going outbound
its quiet random ports from phone..
Not that random
tcp/853 - DNS over TLS to cloudflares servers. Either configured on your phone or on autoselect and you use CF as DNS so they are probed.
tcp/80, tcp/443 no problemalso your "random ports" are exactly that but that is expected from answers to 80/443 traffic - after all that are answers to valid traffic. You should really check the System/Firewall Log for your phone and filter for your phone IP and check, what gets actually blocked instead of looking at a tcpdump with all data packets ;)
@Solway said in Android saying "Connected, no Internet":
been testing with ports at bottom. but not working.
Explained above. They are NOT used. You read the dump wrong :) Check your TCP Flags. Everything other than "S" (Syn) isn't really relevant to your cause as it's data, resets, endings etc.
-
@JeGr
you lost me there lol. as you might see im new to pfsense
i understand the stateful firewall thing... was hoping to allow known ports and not random stuff.
-
When you go for :
@Solway said in Android saying "Connected, no Internet":
disabled the "allow all on LAN"
then you need to know for every application on your network ... :
@kiokoman said in Android saying "Connected, no Internet":
whatsapp / play store / google drive /
what outgoing ports they are using. No exception.
You'll be in for some Google time ^^ -
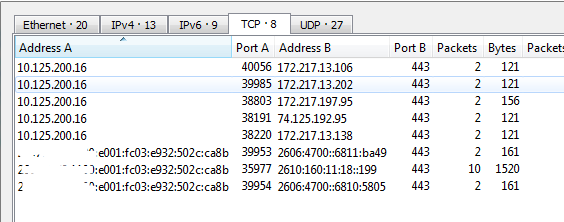
I've found that using Wireshark to capture or read in a tcpdump file and using the Statistics -> Conversations feature to be particularly helpful.
It will display who is talking to whom and on what port.
For instance below we can see many connections going to Address B and port B, this is what you're interested in. In this case all port 443. Be sure to also look at the UDP tab to see what UDP traffic is going out. Google also uses QUIC which is a stateless HTTPS over UDP port 443.
-
@Solway said in Android saying "Connected, no Internet":
i understand the stateful firewall thing... was hoping to allow known ports and not random stuff.
No problem :) Point is, you were reading your capture "wrong" or better "not completely". As you perhaps know, stateful filters filter the traffic by matching the first packet (a SYN packet) against your filter table and allow or block it, then create a state and match traffic to that state so it doesn't have to repeat the lookup process for every single packet of e.g. a download but the first.
So you had this part in your capture:
15:57:40.216322 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0 15:57:40.229403 IP 216.58.206.100.443 > 10.1.1.20.53298: tcp 0 15:57:40.379510 IP 10.1.1.20.53298 > 216.58.206.100.443: tcp 0and read it like "I must open port 53298". But look what has happened: your client (IP .20) requested a HTTPS connection (port 443 on the remote IP xyz.100) and got an answer from it (2nd line) and afterwards sent data to it (3rd line). So your port 53298 is just that: a random high port a client has to use as per protocol when connecting to a remote server speaking HTTPS. That is specified as "client with random high port >1023 [source] to server port 443 [destination]". All other traffic belonging to this connection is passed through the stateful filter. So no need for opening random ports as it isn't the problem you are looking for.
That's why I was telling you, you should instead have a look in "System Logs / Firewall" as there passes or blocks are only listed when matching the filter so no unnecessary packets (like in a tcpdump) are on display. So I'd enable logging on all block/pass rules on your interface the smartphone is connected, disable its WiFi, re-enable it and then check and filter the logs for your android's IP so you only get it to display packets coming from your smartphone and them being passed or blocked. If you see blocked entries, check where they are going and on what port. I assume there are some checking IPs to see if the device has internet connectivity similar to those IPs/Domains/URLs they check to discover if you are behind a portal so they can display their notification that you need to do some portal login.