Setting up OpenVPN for new remote office
-
On the client side, I don't want to make anything available.
On the server side, I just want to make 10.0.3.0/24,10.0.4.0/24 available.
-
You have to put the networks you are sourcing from in the remote networks on the other side in order to route traffic. Else you have to assign an interface and perform outbound NAT to the tunnel address.
You can determine what connections can be made into that side using firewall rules on the OpenVPN tab.
-
So basically, on the CLIENT side I should put 10.0.3.0/24,10.0.4.0/24 in IPv4 Remote network(s)
and on the SERVER side I should leave blank.
Right?
-
Check out
https://www.netgate.com/resources/videos/site-to-site-vpns-on-pfsense.html
to get a basic understanding how it works. :-)-Rico
-
@BlazeStar said in Setting up OpenVPN for new remote office:
So basically, on the CLIENT side I should put 10.0.3.0/24,10.0.4.0/24 in IPv4 Remote network(s)
and on the SERVER side I should leave blank.
Right?
No. You have to put the remote networks on each side to be able to route traffic (or implement tunnel address NAT). You control who can connect to what using firewall rules.
Yeah, some study into exactly what is going on is likely in order.
-
@Rico said in Setting up OpenVPN for new remote office:
Check out
https://www.netgate.com/resources/videos/site-to-site-vpns-on-pfsense.htmlThat's the video I watched to set up my stuff.
Yet I'm still very puzzled why it doesn't work.
Around the end of the video, a few tests are recommended, and when I try them they fail.
For example, I try to ping host 10.0.3.20 which is a server I have on the server-side.
On the client-side, from pfSense, it works:
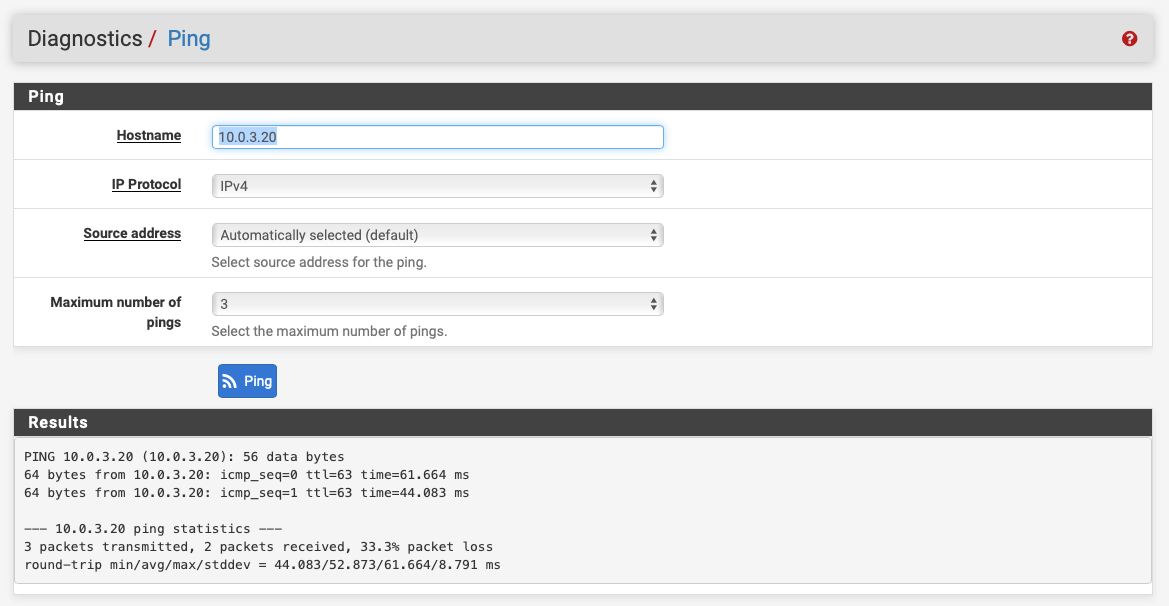
On the client-side, from LAN, it fails!!
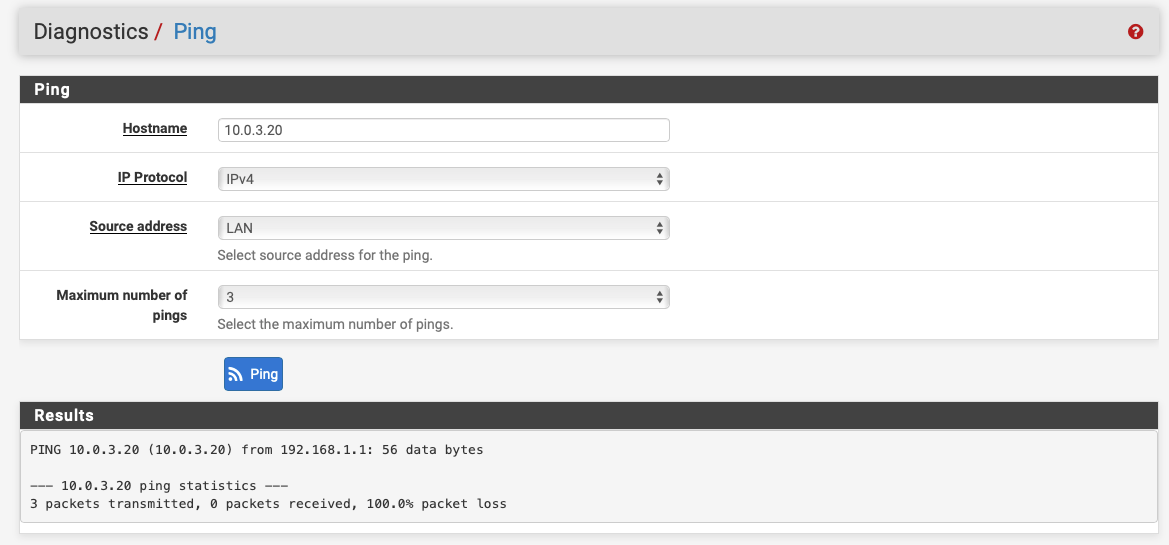
And in the routing tables I see this:
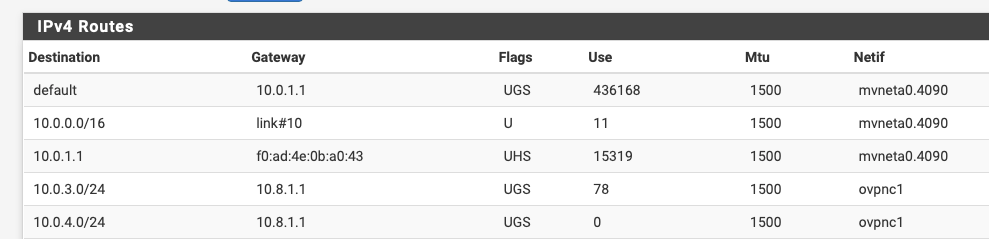
Which appears to me like, once again, this should work!
Anything I'm not seeing here??
-
Does the server side have a route back to 192.168.1.1?
-
@Derelict on the server-side I can see this entry in my routing table:

So I would say yes there's a route back.
Is that what you meant?
-
And both side have this firewall rule in OpenVPN tab
-
That doesn't look like a route back to me. How does the server side firewall know to route traffic back to 192.168.1.1 over the VPN?
Add 192.168.1.0/24 to the remote networks in the OpenVPN instance on the server side.
-
Damn.
So I made a typo in the IPv4 Remote network(s) on the server-side.
Now everything works.
Thank you so much for you help @Derelict