OpenVPN Client & Server Issues
-
I am having trouble running the OpenVPN Client & Server at the same time. When I have both enabled, all the traffic that that goes through the OpenVPN Client suffers a dramatic decrease in bandwidth. To better explain, my whole LAN is directed to go through PIA VPN setup on the OpenVPN client within pfSense, and I configured a OpenVPN server for remote connections back to my LAN via mobile device (road warrior). I have hardware crypto enabled within pfSense, but do not have it selected within both VPN configs. I've noticed that when I go into the OpenVPN Server setup and disable the server my WAN and OpenVPN Client throughput resumes to normal.
-
Has to be something else.
Going to need more details and actual measurements showing exactly how you are testing and what you are seeing.
-
I know it's driving me nuts. As far as the measurements go, I haven't really used any specific tools other than typical speed tests through the chrome browser and they always return really bad results when both are running. So bad that it doesn't even bother upload testing. When both are running web page loading is impossible. My google pings are at 100% loss. What details would you like to see and I will definitely post these? I can start with the rules.
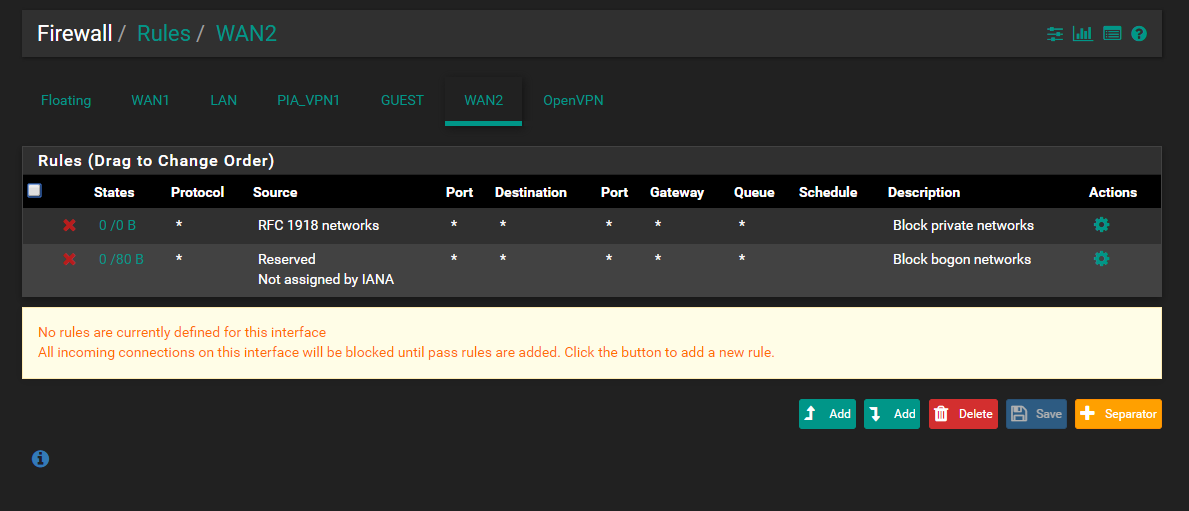
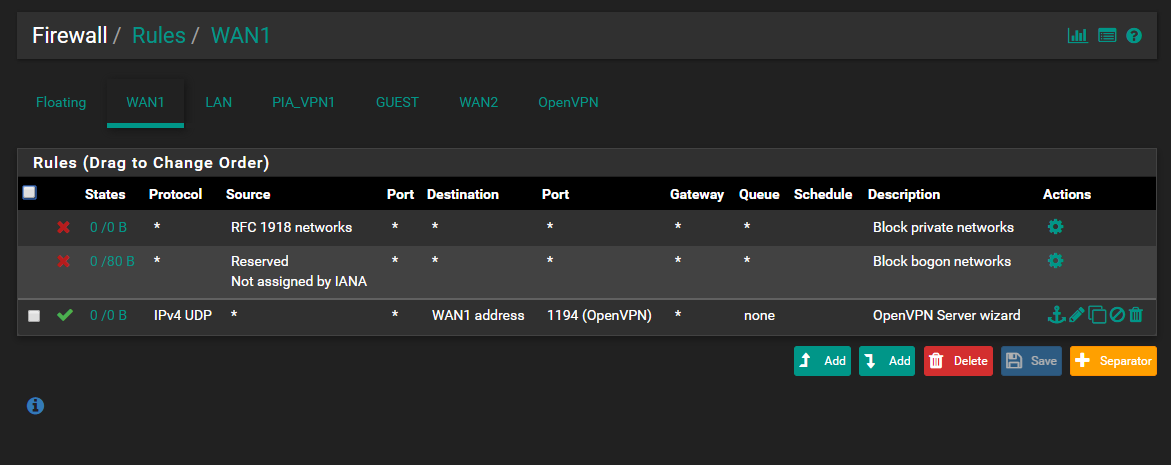
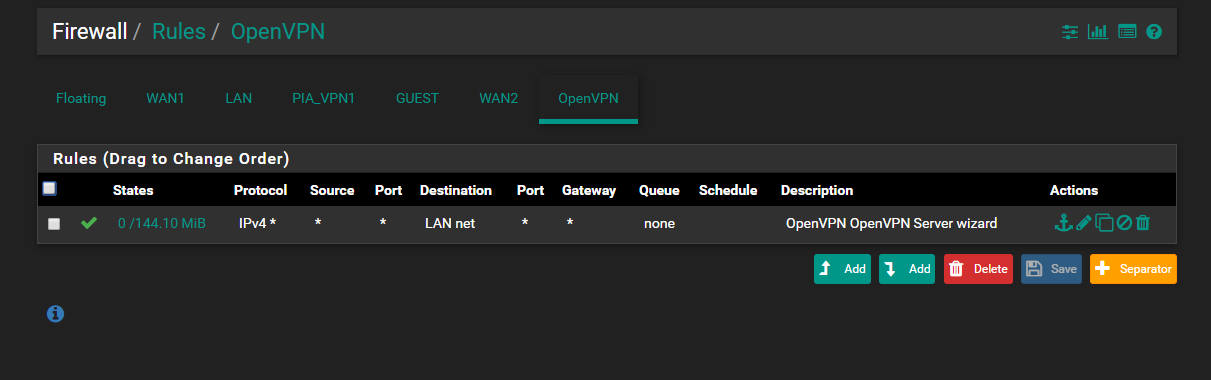
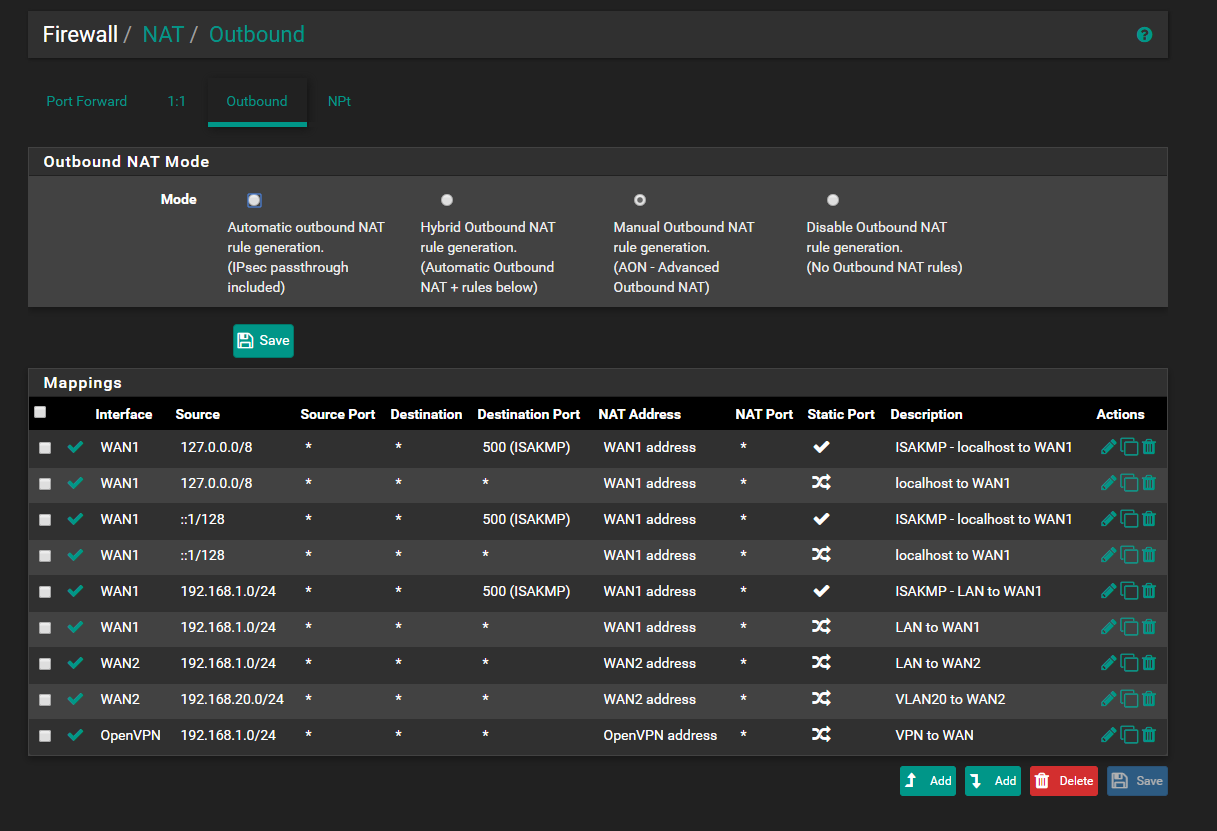
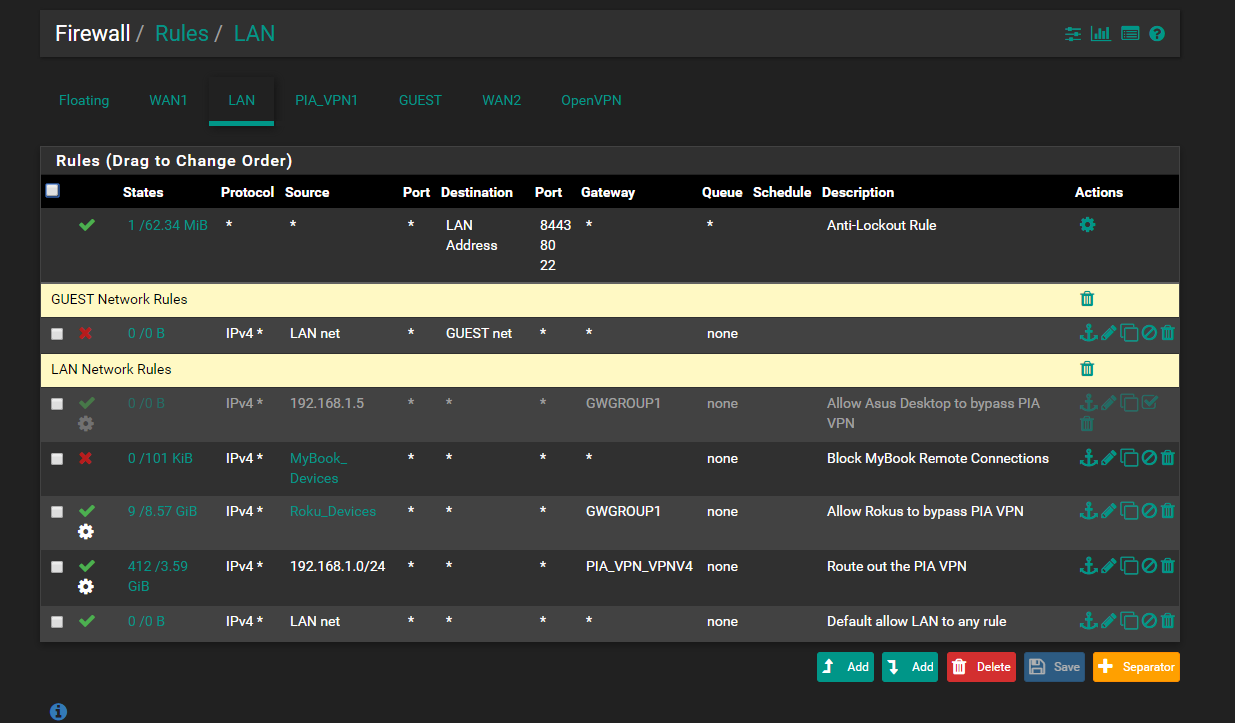
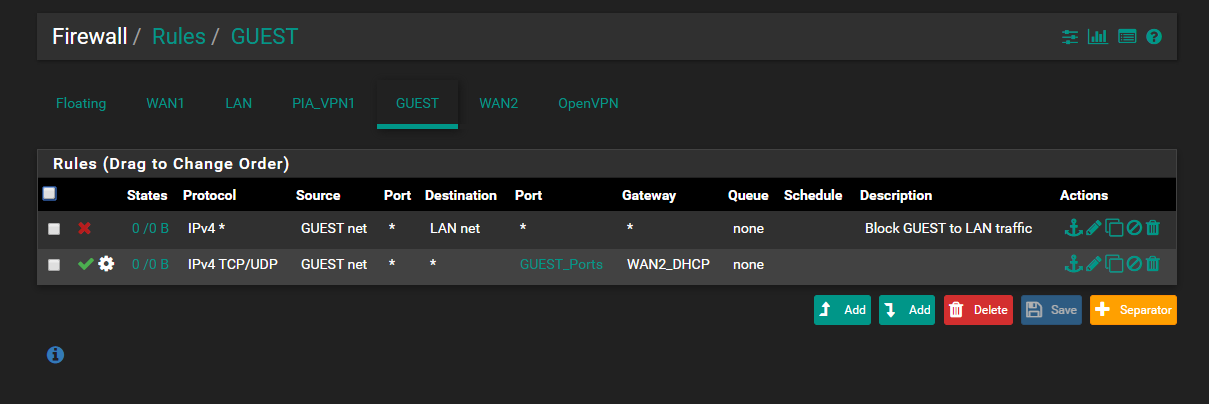 The floating rule is for blocking all traffic tagged when the PIA_VPN is down
The floating rule is for blocking all traffic tagged when the PIA_VPN is down 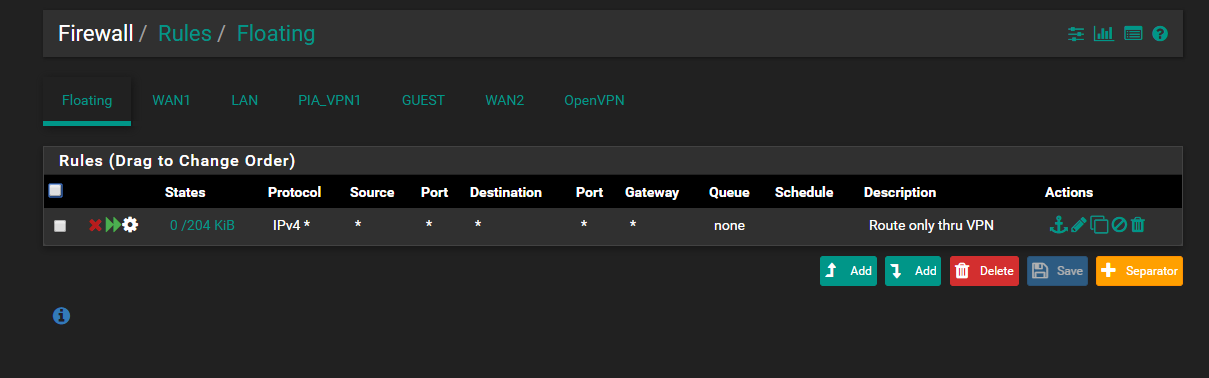
-
@Derelict The pings to google actually work, however I noticed the hosts that are routed to bypass the VPN client tunnel to PIA across WAN1 are SEVERELY crippled. I decided to turn off the floating rule that checks for tagged traffic as well as going into the LAN rules and removing the tag entry and that still did not make a difference. This is getting ridiculous. The Asus router I used before was able to connect to a VPN provider as client and run a OpenVPN Server without any problems. Looking at the CPU and RAM usage, the CPU never goes above 3% and the RAM is around 4%. This is without any client connections to the pfsense OpenVPN Server. I know this is not hardware related, but I can't wrap my head around this. I have to disable the OpenVPN Server just for my Internet speeds to return to normal. When speedtests are performed with it disabled my download/upload speeds are at my providers bandwidth of 150/150, but as soon as I turn the server on the speedtest takes what seems like an eternity to start testing and when and if it does I get 25 down and 90 up.
-
You are saying just enabling the server results in a change even with nobody connected?
-
@Derelict Yes. I'm thinking though that because I created the OpenVPN Client first, then decided to use the wizard to create an OpenVPN Server, I actually created a problem with the rules. I let the wizard create rules for the OpenVPN Server which in return created an allow all rule under the newly created OpenVPN tab under firewall rules. It also changed the Outbound NAT rule I had previously created for the OpenVPN Client to the "OpenVPN" interface. I had it set to PIA_VPN interface before it changed.
-
@Derelict I'm thinking that I should maybe create an interface for the OpenVPN Server, then create a outbound NAT rule for that OpenVPN Server, and then create LAN rules based on that interface allowing my LAN net to pass traffic to that OpenVPN Server interface. I understand that the OpenVPN interface rules under it's own tab are processed first and as a group for all VPN's which might be causing the issues considering I have a separate interface configured for the OpenVPN Client "PIA_VPN". Your thoughts?
-
Well you obviously screwed something up because what you are describing simply does not happen under normal circumstances.
About all that happens when you start an OpenVPN server is routes are inserted into the routing table for the tunnel network and any Remote Networks configured in that server. And it listens for inbound connections. Nothing else. OpenVPN client and OpenVPN server instances will be completely separate processes.
If you somehow managed to have conflicting routes or something it might affect traffic. Maybe you happened to choose a tunnel network that the OpenVPN provider also chose to use somewhere.
-
@Derelict I though so too, but I changed the remote network from a Class A to a Class B, and that didn't make a difference. Upon watching the hangout video produced by Jim Pingle "OpenVPN as a WAN on pfSense", he had answered a question from one of the chat members stating that you typically would not want 1 outbound NAT firewall rule that uses the "OpenVPN" interface when using multiple VPN's.
-
Class A to Class B, what does that mean? Why would anyone anywhere be using /8 or /16 networks in an OpenVPN? If you are doing that you are both wrong and almost certainly conflicting with a network your OpenVPN provider is using internally.
They either conflict or they don't. Look at the routing table. Look at the logs.
-
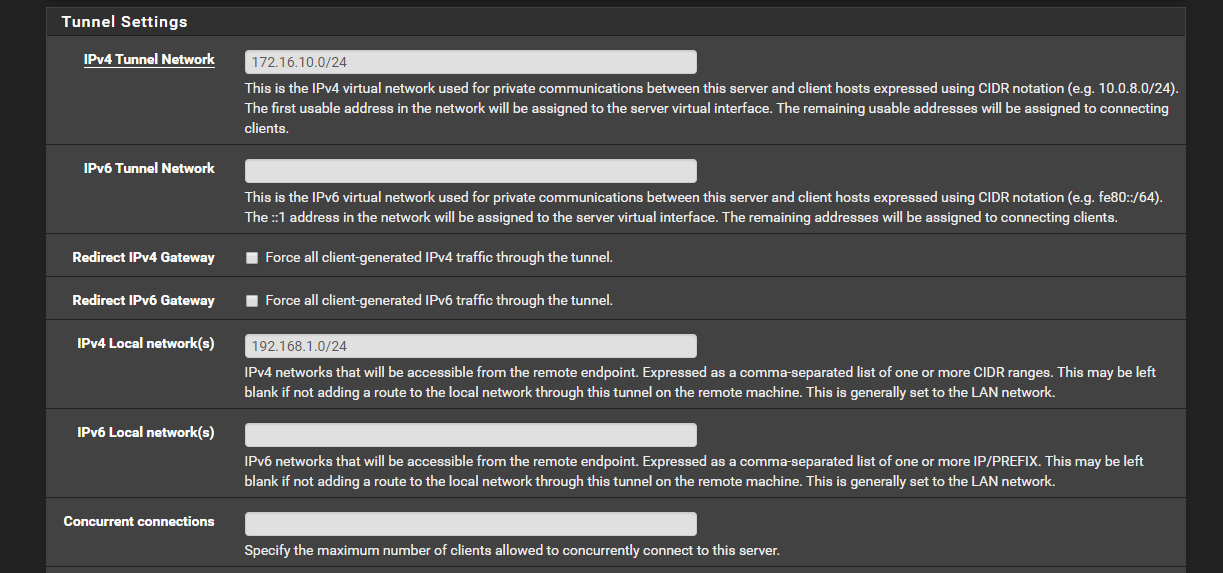
@Derelict In other words I went from using 10.8.0.0/24 to using 172.16.10.0/24 for my OpenVPN Server. And I will look at the logs to determine if there is confict. I don't think there is though.
-
Those are /24 networks, not "Class A" or "Class B" networks. If anything, they are "Class C" networks but nobody (nobody) uses classful terminology any more. Like ever.
-
That server will do two things:
Insert a route for 172.16.10.0/24 into the routing table so the firewall knows to send traffic to those addresses into that OpenVPN process.
Push a route for 192.168.1.0/24 to any clients that connect so they know to send that traffic over the OpenVPN tunnel.
None of that has anything to do with any OpenVPN client connection you have set up.
Are you going to send that status output file?
-
@Derelict I know that has nothing to do with OpenVPN client connections. The problem seems to affect my WAN too. I run my whole LAN net through PIA_VPN but have rules in place to allow a few devices to bypass that PIA_VPN. They are also affected when the OpenVPN Client and OpenVPN Server are running simultaneously. I can send a status output file, but you'll need to be specific with me exactly which status file you are talking about and before sending it I would need to edit it if need be as to not expose any private info.
-
@Derelict said in OpenVPN Client & Server Issues:
Those are /24 networks, not "Class A" or "Class B" networks. If anything, they are "Class C" networks but nobody (nobody) uses classful terminology any more. Like ever.
They are Non-standard
-
Nobody uses those any more. It is all Classless (CIDR) RFC1918.
-
Except a few older websites that refuse to update things..
-
@Derelict said in OpenVPN Client & Server Issues:
Nobody uses those any more. It is all Classless (CIDR) RFC1918.
I was only using this to generalize with you that there shouldn't be any conflicts between the tunnel networks.
-
Well there is obviously something wrong with what you have done or it would be working.
Pretty much at a loss to say what that is based on what we have been shown.
I sent a private asking for a complete status output that I have yet to receive. So absent that I'm not sure what to tell you.
-
@Iceman said in OpenVPN Client & Server Issues:
When I have both enabled, all the traffic that that goes through the OpenVPN Client suffers a dramatic decrease in bandwidth.
pfsense hardware??