VPN Client, Policy Based Routing and Pi Hole
-
Hi and thanks for reading.
My goal is to use my pfsense as a OpenVPN client with policy based routing to allow only certain devices to access the internet through the VPN. I already have a Pi Hole working well as a local DNS server using DNS Resolver on the pfsense.
I am only a beginner when it comes to networking so i followed this guide: https://www.reddit.com/r/PFSENSE/comments/6edsav/how_to_proper_partial_network_vpn_with_kill_switch/
I have:
- Assigned all devices I want to use the vpn a static ip and put them under one alias
- Set up the vpn
- Set the NAT outbound settings
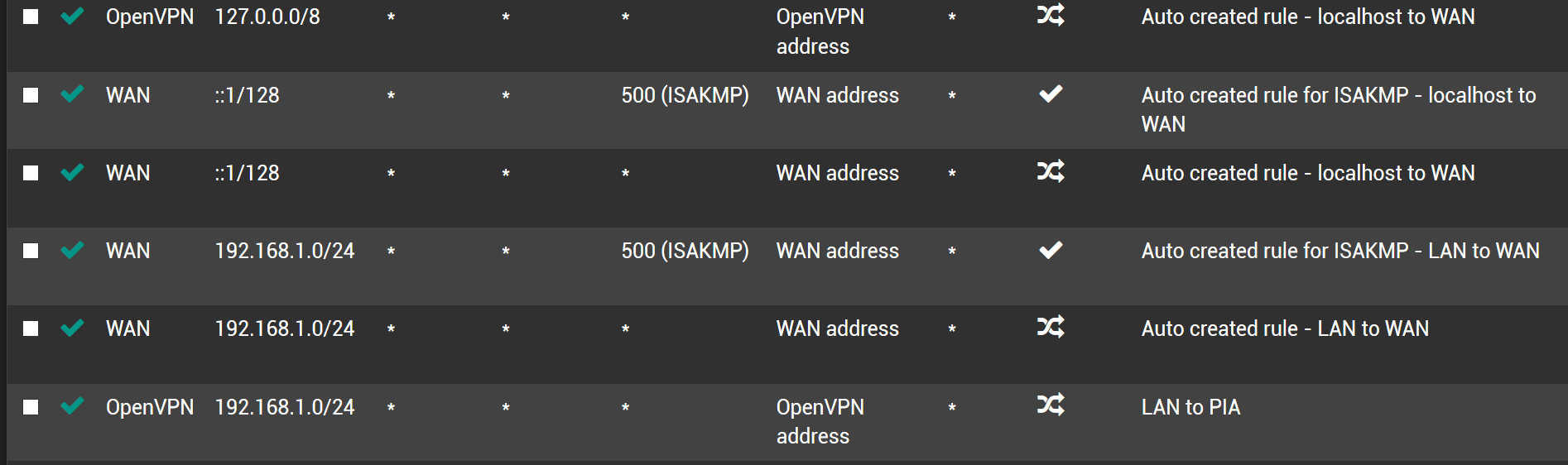
- Created an interface for the vpn
- Added the firewall LAN rules to block local DNS leaks, drop all all IPv6 traffic and to force all traffic from devices in the vpn alias through the vpn interface, also tagging the traffic
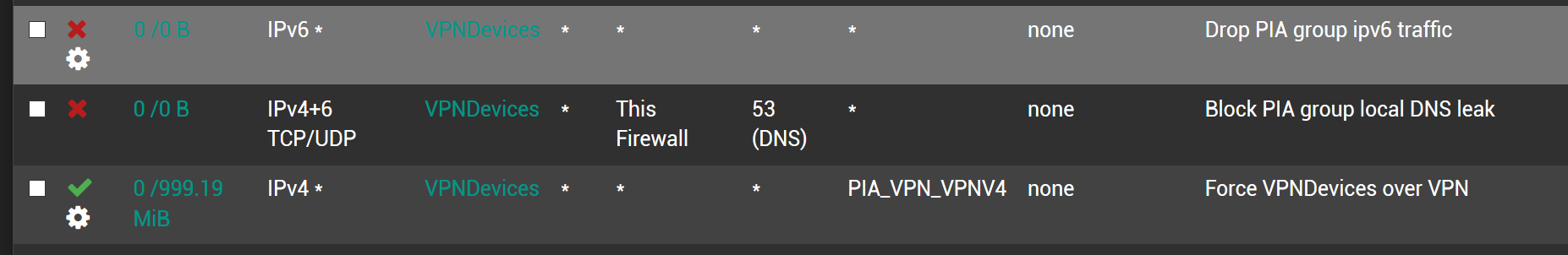
- Assigned DNS servers (8.8.8.8 and 1.1.1.1) to the VPN devices
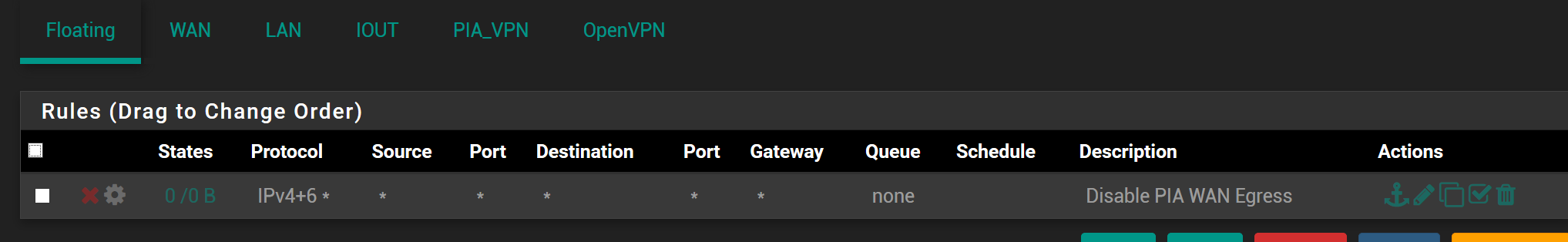
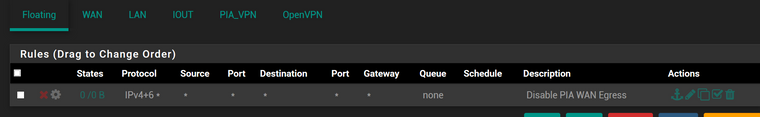
However, when I set the floating firewall rule for the “Kill Switch”, which blocks all traffic on the WAN interface which is tagged in step 5 above, I lose connection to the internet on every single device, VPN or not.
I can’t see why, but I assume it must be related to me using the Pi-hole as a local DNS server.
Before enabling the kill switch rule if I use a device in the VPN alias I can see its definitely on the VPN and ipleak confirms all DNS queries are also going over the VPN. For devices not in the VPN alias I can see that they are definitely using my ISP IP and DNS queries are not going over the VPN.The reason why I did that test was that I thought all DNS queries might be going out of the VPN and that the floating rule might be blocking all DNS queries. But I “think” I’ve proved that it isn’t…
Can anyone see where I might have gone wrong?
Thanks again!
-
This post is deleted!