Firewall Rule to Allow RDP from WAN to LAN......Need help
-
It would then for its clients hand out some other IP range, pointing to itself for gateway and to itself for dns..
I have configured DHCP as below in my Asus router :
DHCP : 192.168.50.2 to 192.168.50.100
Gateway 192.168.50.1
DNS : 8.8.8.8, 8.8.4.4When a client asks for dns, the router would ask pfsense for dns, etc.
I have configured primary 8.8.8.8 and seconday 8.8.4.4 in pfsense DNSYour not trying to redirect or block other dns at pfsense or your asus router? If your asus router is saying it not connected to internet.. Then yeah you have some sort of problem
I am not blocking any DNS at pfsense or asus routerdoes its wan get an IP from pfsense dhcp server?
Asus router is not getting WAN IP from Windows DHCP server... Note : I have not used pfsense DHCP...instead of it I have Windows DHCP server.So if your going to go that route, then why not just use your asus as AP and as a vlan off pfsense directly?
I have tried with AP as well I have same issue, unable to access internet but able to tracert 8.8.8.8...... Thats what I have surprise now... even in AP mode I am unable to access the internet. -
Are you allowing udp? What are you firewall rules on your lan? And your saying your other clients can access, just not your wifi?
-
And your saying your other clients can access, just not your wifi?
Yes my other clients(ie) Windows machine sitting in LAN able to access internet..but not wifi clients... -
So when your AP mode your clients get an IP from dhcp from yoru lan network, your windows dhcp server? They point to pfsense for gateway?
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
They point to pfsense for gateway?
Yes correct...
-
You can ping pfsense IP? But dns does not work? Sniff on pfsense do you see traffic from your wifi client for dns?
Pfsense can not tell the difference between something on lan that is wired, or something that is wireless and bridged via AP to your lan..
Your not running a captive portal on pfsense are you? Your not doing any sort of thing with static arps? Validate the traffic for your dns query is actually getting to pfsense.. If you see it, then sniff on pfsense wan while you do the same test - do you see pfsense send on the query out its wan?
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
You can ping pfsense IP? But dns does not work? Sniff on pfsense do you see traffic from your wifi client for dns?
Yes I can able to ping pfsene gateway IP from my wifi client.. but dns is not working... let me do sniff and let you know..
Attached screenshot of my wifi router WAN is getting IP from LAN DHCP Server after reboot of pfsense...
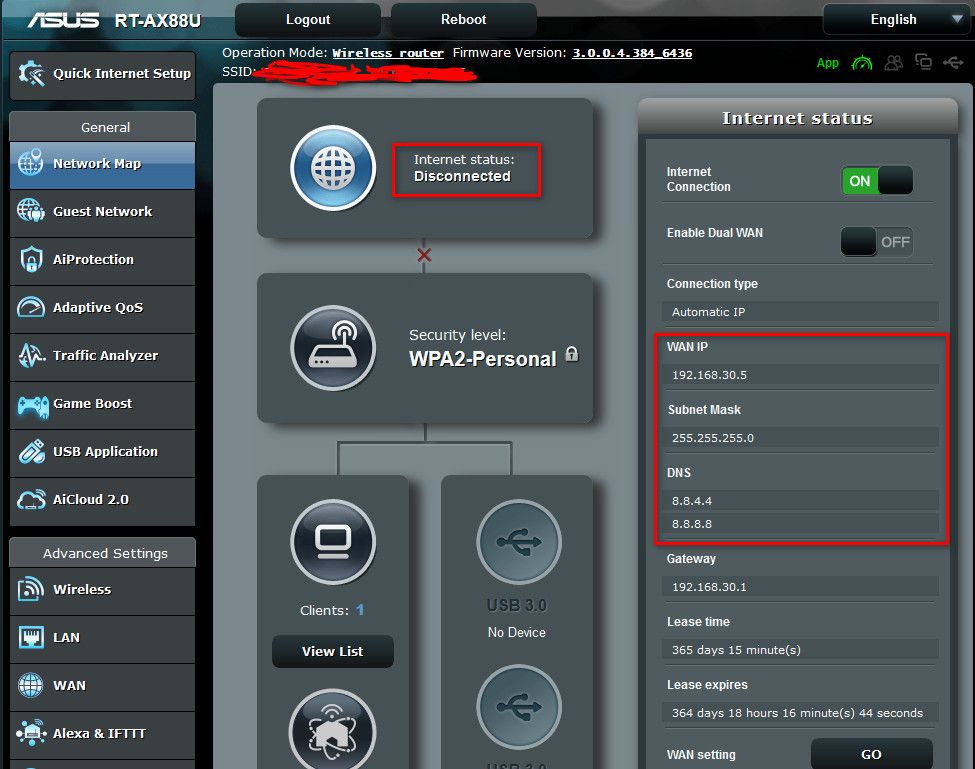 but internet is not working because of DNS issue...
but internet is not working because of DNS issue... -
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Validate the traffic for your dns query is actually getting to pfsense.. If you see it, then sniff on pfsense wan while you do the same test - do you see pfsense send on the query out its wan?
can you guide me how to do that ?
-
I have created nameservers pointing to 8.8.8.8 & 8.8.4.4 in Windows DHCP server as well.
In Windows DNS server I have created forwarders to 8.8.8.8 and 8.8.4.4 as well...
I have another question here, I have connected cable between LAN network(Second physical NIC card and router WAN port .. I can see IP's are getting from DHCP server including gateway and DNS... as I have posted screen shot...
-
@DINU said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Validate the traffic for your dns query is actually getting to pfsense.. If you see it, then sniff on pfsense wan while you do the same test - do you see pfsense send on the query out its wan?
From Wifi client dns query is not working because it dont have internet connection and also it is sitting on differnt subnet...pfsense is sending the dns query out its WAN already I have informed that in my LAN windows machine internet is working fine...note : my LAN windows clients are connected to domain...
-
Lets troubleshoot 1 issue at a time... Look on your client specifically for what its using for dns.. Your clients behind some nat wifi router is normally going to get the wifi routers IP for its dns.. Doesn't always matter what you set in the wifi routers wan settings. Be it static or via dhcp.
Look on your client.. what does it show for its dns? windows simple ipconfig /all will show you this.
From you wifi client can you ping pfsense IP? 192.168.30.1? Using your fav dns tool on your client - can it resolve anything?
$ ping 192.168.9.253 Pinging 192.168.9.253 with 32 bytes of data: Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.9.253: Packets: Sent = 2, Received = 2, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms Control-C ^C$ nslookup www.google.com Server: pi-hole.local.lan Address: 192.168.3.10 Non-authoritative answer: Name: www.google.com Addresses: 2607:f8b0:4009:804::2004 172.217.4.36$ dig www.google.com ; <<>> DiG 9.14.4 <<>> www.google.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26297 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.google.com. IN A ;; ANSWER SECTION: www.google.com. 1214 IN A 172.217.4.36 ;; Query time: 2 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Sun Sep 29 08:26:07 Central Daylight Time 2019 ;; MSG SIZE rcvd: 59To validate your actually getting to pfsense for anything.. Sniff on pfsense for the traffic, on your lan interface under diag packet capture menu
dig @192.168.9.253 www.sljfdljdsflsjlfd.com
8:28:51.351448 00:13:3b:2f:67:63 > 00:08:a2:0c:e6:24, ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 128, id 35658, offset 0, flags [none], proto UDP (17), length 93) 192.168.9.101.56267 > 192.168.9.253.53: [udp sum ok] 3723+ [1au] A? www.sljfdljdsflsjlfd.com. ar: . OPT UDPsize=4096 (65)Set your capture for lan, port 53, udp.. set the level of detail to full... See above on the sniff it shows what I did a query for www.sljfdljdsflsjlfd.com
If your behind your natting asus router, your getting an IP from its dhcp server, and its different than that 192.168.30.x right? 192.168.50/24 ?? not 192.168.50/16 for example which would overlap your asus wan network.
-
@johnpoz
Screen shot is from my wifi client :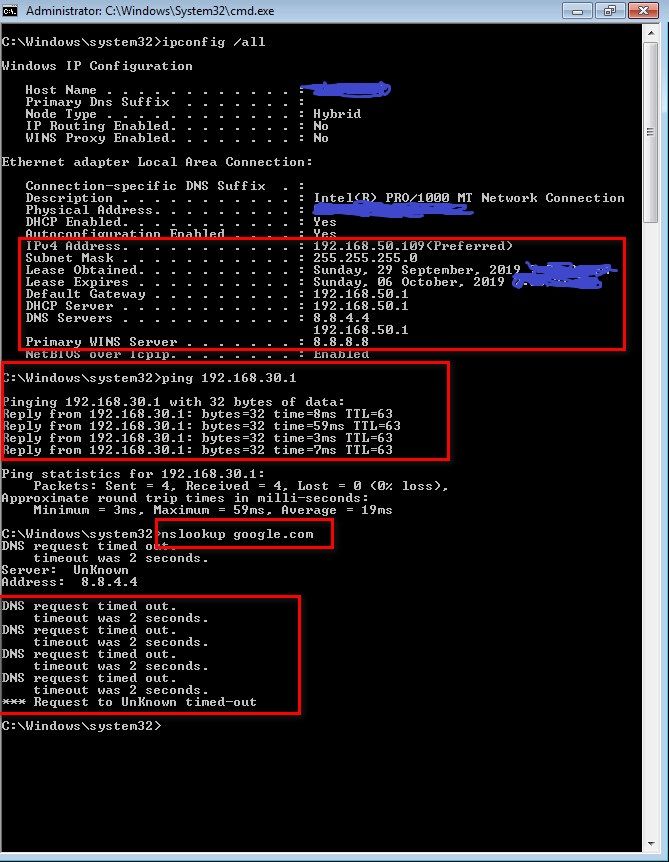
As you have mentioned IP's including gateway and DNS are getting from router itseld where DHCP is enabled.
I can able to ping pfsense LAN gateway 192.168.30.1. When do nslookup google.com I don't see any DNS resolution...
and its different than that 192.168.30.x right? 192.168.50/24 ?? not 192.168.50/16 for example which would overlap your asus wan network.
yes my wifi router is 192.168.50/24.I have tried to capture the dns on port 53 using udp I dont see any queries coming from wifi client.. all queries I can see is from my LAN windows clients...
19:37:44.876422 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 86: (tos 0x0, ttl 128, id 21739, offset 0, flags [none], proto UDP (17), length 72)
192.168.30.10.65503 > 192.168.30.1.53: [udp sum ok] 40714+ A? tiles.services.mozilla.com. (44)
19:37:44.912301 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 240: (tos 0x0, ttl 64, id 25771, offset 0, flags [none], proto UDP (17), length 226)
192.168.30.1.53 > 192.168.30.10.65503: [bad udp cksum 0xbe3b -> 0x2983!] 40714 q: A? tiles.services.mozilla.com. 9/0/0 tiles.services.mozilla.com. CNAME tiles.r53-2.services.mozilla.com., tiles.r53-2.services.mozilla.com. A 52.33.184.165, tiles.r53-2.services.mozilla.com. A 52.39.125.254, tiles.r53-2.services.mozilla.com. A 52.33.192.41, tiles.r53-2.services.mozilla.com. A 52.24.113.72, tiles.r53-2.services.mozilla.com. A 52.89.51.22, tiles.r53-2.services.mozilla.com. A 54.186.225.209, tiles.r53-2.services.mozilla.com. A 54.149.29.182, tiles.r53-2.services.mozilla.com. A 52.39.224.180 (198)
19:37:44.926269 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 103: (tos 0x0, ttl 128, id 21740, offset 0, flags [none], proto UDP (17), length 89)
192.168.30.10.56305 > 192.168.30.1.53: [udp sum ok] 1841+ [1au] AAAA? tiles.r53-2.services.mozilla.com. ar: . OPT UDPsize=4000 DO (61)
19:37:44.938451 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 185: (tos 0x0, ttl 64, id 40211, offset 0, flags [none], proto UDP (17), length 171)
192.168.30.1.53 > 192.168.30.10.56305: [bad udp cksum 0xbe04 -> 0x1f93!] 1841 q: AAAA? tiles.r53-2.services.mozilla.com. 0/1/1 ns: r53-2.services.mozilla.com. SOA ns-1507.awsdns-60.org. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 ar: . OPT UDPsize=512 DO (143)
19:37:45.611619 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 95: (tos 0x0, ttl 128, id 21741, offset 0, flags [none], proto UDP (17), length 81)
192.168.30.10.56494 > 192.168.30.1.53: [udp sum ok] 40740+ [1au] A? snippets.cdn.mozilla.net. ar: . OPT UDPsize=4000 DO (53)
19:37:45.684196 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 322: (tos 0x0, ttl 64, id 22443, offset 0, flags [none], proto UDP (17), length 308)
192.168.30.1.53 > 192.168.30.10.56494: [bad udp cksum 0xbe8d -> 0x7940!] 40740 q: A? snippets.cdn.mozilla.net. 3/0/1 snippets.cdn.mozilla.net. CNAME d228z91au11ukj.cloudfront.net., snippets.cdn.mozilla.net. RRSIG, d228z91au11ukj.cloudfront.net. A 13.249.213.234 ar: . OPT UDPsize=512 DO (280)
19:37:45.698269 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 100: (tos 0x0, ttl 128, id 21742, offset 0, flags [none], proto UDP (17), length 86)
192.168.30.10.56630 > 192.168.30.1.53: [udp sum ok] 798+ [1au] AAAA? d228z91au11ukj.cloudfront.net. ar: . OPT UDPsize=4000 DO (58)
19:37:45.710902 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 181: (tos 0x0, ttl 64, id 51364, offset 0, flags [none], proto UDP (17), length 167)
192.168.30.1.53 > 192.168.30.10.56630: [bad udp cksum 0xbe00 -> 0xb37b!] 798 q: AAAA? d228z91au11ukj.cloudfront.net. 0/1/1 ns: d228z91au11ukj.cloudfront.net. SOA ns-889.awsdns-47.net. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 ar: . OPT UDPsize=512 DO (139)
19:37:45.824181 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 85: (tos 0x0, ttl 128, id 21743, offset 0, flags [none], proto UDP (17), length 71)
192.168.30.10.49277 > 192.168.30.1.53: [udp sum ok] 42109+ [1au] A? mail.yahoo.com. ar: . OPT UDPsize=4000 DO (43)
19:37:45.824952 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 94: (tos 0x0, ttl 128, id 21744, offset 0, flags [none], proto UDP (17), length 80)
192.168.30.10.56481 > 192.168.30.1.53: [udp sum ok] 25842+ [1au] A? youtube-ui.l.google.com. ar: . OPT UDPsize=4000 DO (52)
19:37:45.826093 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 84: (tos 0x0, ttl 128, id 21745, offset 0, flags [none], proto UDP (17), length 70)
192.168.30.10.56306 > 192.168.30.1.53: [udp sum ok] 33395+ [1au] A? www.raaga.com. ar: . OPT UDPsize=4000 DO (42)
19:37:45.836306 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 198: (tos 0x0, ttl 64, id 55217, offset 0, flags [none], proto UDP (17), length 184)
192.168.30.1.53 > 192.168.30.10.49277: [bad udp cksum 0xbe11 -> 0x6aef!] 42109 q: A? mail.yahoo.com. 5/0/1 mail.yahoo.com. CNAME fd-geoycpi-uno.gycpi.b.yahoodns.net., fd-geoycpi-uno.gycpi.b.yahoodns.net. A 106.10.236.37, fd-geoycpi-uno.gycpi.b.yahoodns.net. A 106.10.236.40, fd-geoycpi-uno.gycpi.b.yahoodns.net. A 119.161.10.11, fd-geoycpi-uno.gycpi.b.yahoodns.net. A 119.161.10.12 ar: . OPT UDPsize=512 DO (156)
19:37:45.848087 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 106: (tos 0x0, ttl 128, id 21746, offset 0, flags [none], proto UDP (17), length 92)
192.168.30.10.55843 > 192.168.30.1.53: [udp sum ok] 15938+ [1au] AAAA? fd-geoycpi-uno.gycpi.b.yahoodns.net. ar: . OPT UDPsize=4000 DO (64)
19:37:45.860524 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 218: (tos 0x0, ttl 64, id 28254, offset 0, flags [none], proto UDP (17), length 204)
192.168.30.1.53 > 192.168.30.10.55843: [bad udp cksum 0xbe25 -> 0x265e!] 15938 q: AAAA? fd-geoycpi-uno.gycpi.b.yahoodns.net. 4/0/1 fd-geoycpi-uno.gycpi.b.yahoodns.net. AAAA 2406:2000:98:800::e6, fd-geoycpi-uno.gycpi.b.yahoodns.net. AAAA 2406:2000:e4:1604::1001, fd-geoycpi-uno.gycpi.b.yahoodns.net. AAAA 2406:2000:e4:1604::1000, fd-geoycpi-uno.gycpi.b.yahoodns.net. AAAA 2406:2000:98:800::e5 ar: . OPT UDPsize=512 DO (176)
19:37:45.867140 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 128, id 21747, offset 0, flags [none], proto UDP (17), length 84)
192.168.30.10.56236 > 192.168.30.1.53: [udp sum ok] 15965+ [1au] A? star-mini.c10r.facebook.com. ar: . OPT UDPsize=4000 DO (56)
19:37:45.886164 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 190: (tos 0x0, ttl 64, id 15605, offset 0, flags [none], proto UDP (17), length 176)
192.168.30.1.53 > 192.168.30.10.56306: [bad udp cksum 0xbe09 -> 0x7dc8!] 33395 q: A? www.raaga.com. 5/0/1 www.raaga.com. CNAME ds312qwwrvmld.cloudfront.net., ds312qwwrvmld.cloudfront.net. A 54.230.71.115, ds312qwwrvmld.cloudfront.net. A 54.230.71.73, ds312qwwrvmld.cloudfront.net. A 54.230.71.75, ds312qwwrvmld.cloudfront.net. A 54.230.71.66 ar: . OPT UDPsize=512 DO (148)
19:37:45.899424 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 99: (tos 0x0, ttl 128, id 21748, offset 0, flags [none], proto UDP (17), length 85)
192.168.30.10.56466 > 192.168.30.1.53: [udp sum ok] 7561+ [1au] AAAA? ds312qwwrvmld.cloudfront.net. ar: . OPT UDPsize=4000 DO (57)
19:37:45.943366 00:0c:29:1a:fe:22 > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 86: (tos 0x0, ttl 128, id 11947, offset 0, flags [none], proto UDP (17), length 72)
192.168.30.11.59921 > 192.112.36.4.53: [udp sum ok] 22445 [1au] A? www.youtube.com. ar: . OPT UDPsize=4000 DO (44)
19:37:45.958388 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 323: (tos 0x0, ttl 64, id 3068, offset 0, flags [none], proto UDP (17), length 309)
192.168.30.1.53 > 192.168.30.10.56466: [bad udp cksum 0xbe8e -> 0x3d76!] 7561 q: AAAA? ds312qwwrvmld.cloudfront.net. 8/0/1 ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:ce00:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:5a00:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:f600:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:3e00:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:ac00:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:2800:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:7600:17:9a5f:c840:93a1, ds312qwwrvmld.cloudfront.net. AAAA 2600:9000:215c:b000:17:9a5f:c840:93a1 ar: . OPT UDPsize=512 DO (281)
19:37:45.966088 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 89: (tos 0x0, ttl 128, id 21749, offset 0, flags [none], proto UDP (17), length 75)
192.168.30.10.56014 > 192.168.30.1.53: [udp sum ok] 5923+ [1au] A? dyna.wikimedia.org. ar: . OPT UDPsize=4000 DO (47)
19:37:45.966345 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 64, id 37435, offset 0, flags [none], proto UDP (17), length 100)
192.168.30.1.53 > 192.168.30.10.56236: [bad udp cksum 0xbdbd -> 0x3eae!] 15965 q: A? star-mini.c10r.facebook.com. 1/0/1 star-mini.c10r.facebook.com. A 157.240.23.35 ar: . OPT UDPsize=512 DO (72)
19:37:45.977289 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 128, id 21750, offset 0, flags [none], proto UDP (17), length 84)
192.168.30.10.56033 > 192.168.30.1.53: [udp sum ok] 45224+ [1au] AAAA? star-mini.c10r.facebook.com. ar: . OPT UDPsize=4000 DO (56)
19:37:45.983211 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 270: (tos 0x0, ttl 64, id 18039, offset 0, flags [none], proto UDP (17), length 256)
192.168.30.1.53 > 192.168.30.10.56481: [bad udp cksum 0xbe59 -> 0xaa46!] 25842 q: A? youtube-ui.l.google.com. 11/0/1 youtube-ui.l.google.com. A 172.217.163.78, youtube-ui.l.google.com. A 172.217.163.174, youtube-ui.l.google.com. A 172.217.163.206, youtube-ui.l.google.com. A 172.217.166.110, youtube-ui.l.google.com. A 216.58.197.46, youtube-ui.l.google.com. A 216.58.197.78, youtube-ui.l.google.com. A 172.217.26.206, youtube-ui.l.google.com. A 172.217.167.142, youtube-ui.l.google.com. A 172.217.31.206, youtube-ui.l.google.com. A 172.217.160.142, youtube-ui.l.google.com. A 216.58.196.174 ar: . OPT UDPsize=512 DO (228)
19:37:45.993886 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 94: (tos 0x0, ttl 128, id 21751, offset 0, flags [none], proto UDP (17), length 80)
192.168.30.10.56858 > 192.168.30.1.53: [udp sum ok] 42011+ [1au] AAAA? youtube-ui.l.google.com. ar: . OPT UDPsize=4000 DO (52)
19:37:46.003399 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 105: (tos 0x0, ttl 64, id 45834, offset 0, flags [none], proto UDP (17), length 91)
192.168.30.1.53 > 192.168.30.10.56014: [bad udp cksum 0xbdb4 -> 0x0942!] 5923 q: A? dyna.wikimedia.org. 1/0/1 dyna.wikimedia.org. A 103.102.166.224 ar: . OPT UDPsize=512 DO (63)
19:37:46.009834 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 85: (tos 0x0, ttl 128, id 21752, offset 0, flags [none], proto UDP (17), length 71)
192.168.30.10.55903 > 192.168.30.1.53: [udp sum ok] 24774+ [1au] A? www.google.com. ar: . OPT UDPsize=4000 DO (43)
19:37:46.015812 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 89: (tos 0x0, ttl 128, id 21753, offset 0, flags [none], proto UDP (17), length 75)
192.168.30.10.56149 > 192.168.30.1.53: [udp sum ok] 37021+ [1au] AAAA? dyna.wikimedia.org. ar: . OPT UDPsize=4000 DO (47)
19:37:46.022283 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 101: (tos 0x0, ttl 64, id 43705, offset 0, flags [none], proto UDP (17), length 87)
192.168.30.1.53 > 192.168.30.10.55903: [bad udp cksum 0xbdb0 -> 0x40a9!] 24774 q: A? www.google.com. 1/0/1 www.google.com. A 172.217.31.196 ar: . OPT UDPsize=512 DO (59)
19:37:46.047489 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 117: (tos 0x0, ttl 64, id 31591, offset 0, flags [none], proto UDP (17), length 103)
192.168.30.1.53 > 192.168.30.10.56149: [bad udp cksum 0xbdc0 -> 0x9d5d!] 37021 q: AAAA? dyna.wikimedia.org. 1/0/1 dyna.wikimedia.org. AAAA 2001:df2:e500:ed1a::1 ar: . OPT UDPsize=512 DO (75)
19:37:46.054024 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 91: (tos 0x0, ttl 128, id 21754, offset 0, flags [none], proto UDP (17), length 77)
192.168.30.10.49226 > 192.168.30.1.53: [udp sum ok] 43814+ [1au] A? www.servethehome.com. ar: . OPT UDPsize=4000 DO (49)
19:37:46.073749 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 126: (tos 0x0, ttl 64, id 63885, offset 0, flags [none], proto UDP (17), length 112)
192.168.30.1.53 > 192.168.30.10.56033: [bad udp cksum 0xbdc9 -> 0xa6b5!] 45224 q: AAAA? star-mini.c10r.facebook.com. 1/0/1 star-mini.c10r.facebook.com. AAAA 2a03:2880:f137:83:face:b00c:0:25de ar: . OPT UDPsize=512 DO (84)
19:37:46.080136 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 83: (tos 0x0, ttl 128, id 21755, offset 0, flags [none], proto UDP (17), length 69)
192.168.30.10.56317 > 192.168.30.1.53: [udp sum ok] 24835+ [1au] A? in.yahoo.com. ar: . OPT UDPsize=4000 DO (41)
19:37:46.089136 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 38455, offset 0, flags [none], proto UDP (17), length 93)
192.168.30.1.53 > 192.168.30.10.49226: [bad udp cksum 0xbdb6 -> 0xb974!] 43814 q: A? www.servethehome.com. 1/0/1 www.servethehome.com. A 65.19.142.4 ar: . OPT UDPsize=512 DO (65)
19:37:46.089301 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 122: (tos 0x0, ttl 64, id 6755, offset 0, flags [none], proto UDP (17), length 108)
192.168.30.1.53 > 192.168.30.10.56858: [bad udp cksum 0xbdc5 -> 0x15c1!] 42011 q: AAAA? youtube-ui.l.google.com. 1/0/1 youtube-ui.l.google.com. AAAA 2404:6800:4007:801::200e ar: . OPT UDPsize=512 DO (80)
19:37:46.096789 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 128, id 21756, offset 0, flags [none], proto UDP (17), length 76)
192.168.30.10.56474 > 192.168.30.1.53: [udp sum ok] 31923+ [1au] A? support.mozilla.org. ar: . OPT UDPsize=4000 DO (48)
19:37:46.103770 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 91: (tos 0x0, ttl 128, id 21757, offset 0, flags [none], proto UDP (17), length 77)
192.168.30.10.64639 > 192.168.30.1.53: [udp sum ok] 24424+ [1au] AAAA? www.servethehome.com. ar: . OPT UDPsize=4000 DO (49)
19:37:46.108885 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 331: (tos 0x0, ttl 64, id 16280, offset 0, flags [none], proto UDP (17), length 317)
192.168.30.1.53 > 192.168.30.10.56474: [bad udp cksum 0xbe96 -> 0x1bde!] 31923 q: A? support.mozilla.org. 4/0/1 support.mozilla.org. CNAME prod-tp.sumo.mozit.cloud., support.mozilla.org. RRSIG, prod-tp.sumo.mozit.cloud. A 34.209.95.119, prod-tp.sumo.mozit.cloud. A 34.213.134.214 ar: . OPT UDPsize=512 DO (289)
19:37:46.114922 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 149: (tos 0x0, ttl 64, id 548, offset 0, flags [none], proto UDP (17), length 135)
192.168.30.1.53 > 192.168.30.10.56317: [bad udp cksum 0xbde0 -> 0x2408!] 24835 q: A? in.yahoo.com. 3/0/1 in.yahoo.com. CNAME atsv2-fp-shed.wg1.b.yahoo.com., atsv2-fp-shed.wg1.b.yahoo.com. A 106.10.250.11, atsv2-fp-shed.wg1.b.yahoo.com. A 106.10.250.10 ar: . OPT UDPsize=512 DO (107)
19:37:46.120223 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 95: (tos 0x0, ttl 128, id 21758, offset 0, flags [none], proto UDP (17), length 81)
192.168.30.10.56287 > 192.168.30.1.53: [udp sum ok] 18610+ [1au] AAAA? prod-tp.sumo.mozit.cloud. ar: . OPT UDPsize=4000 DO (53)
19:37:46.128392 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 100: (tos 0x0, ttl 128, id 21759, offset 0, flags [none], proto UDP (17), length 86)
192.168.30.10.64713 > 192.168.30.1.53: [udp sum ok] 57158+ [1au] AAAA? atsv2-fp-shed.wg1.b.yahoo.com. ar: . OPT UDPsize=4000 DO (58)
19:37:46.134053 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 180: (tos 0x0, ttl 64, id 63974, offset 0, flags [none], proto UDP (17), length 166)
192.168.30.1.53 > 192.168.30.10.56287: [bad udp cksum 0xbdff -> 0x2b9a!] 18610 q: AAAA? prod-tp.sumo.mozit.cloud. 0/1/1 ns: sumo.mozit.cloud. SOA ns-1513.awsdns-61.org. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 ar: . OPT UDPsize=512 DO (138)
19:37:46.142242 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 85: (tos 0x0, ttl 128, id 21760, offset 0, flags [none], proto UDP (17), length 71)
192.168.30.10.56223 > 192.168.30.1.53: [udp sum ok] 30649+ [1au] AAAA? www.google.com. ar: . OPT UDPsize=4000 DO (43)
19:37:46.146645 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 169: (tos 0x0, ttl 64, id 10862, offset 0, flags [none], proto UDP (17), length 155)
192.168.30.1.53 > 192.168.30.10.64639: [bad udp cksum 0xbdf4 -> 0x8428!] 24424 q: AAAA? www.servethehome.com. 0/1/1 ns: servethehome.com. SOA ns-180.awsdns-22.com. awsdns-hostmaster.amazon.com. 1 7200 900 1209600 86400 ar: . OPT UDPsize=512 DO (127)
19:37:46.154588 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 113: (tos 0x0, ttl 64, id 31612, offset 0, flags [none], proto UDP (17), length 99)
192.168.30.1.53 > 192.168.30.10.56223: [bad udp cksum 0xbdbc -> 0x0040!] 30649 q: AAAA? www.google.com. 1/0/1 www.google.com. AAAA 2404:6800:4007:810::2004 ar: . OPT UDPsize=512 DO (71)
19:37:46.164211 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 156: (tos 0x0, ttl 64, id 11935, offset 0, flags [none], proto UDP (17), length 142)
192.168.30.1.53 > 192.168.30.10.64713: [bad udp cksum 0xbde7 -> 0x7bf8!] 57158 q: AAAA? atsv2-fp-shed.wg1.b.yahoo.com. 2/0/1 atsv2-fp-shed.wg1.b.yahoo.com. AAAA 2406:2000:e4:a1a::11, atsv2-fp-shed.wg1.b.yahoo.com. AAAA 2406:2000:e4:a1a::10 ar: . OPT UDPsize=512 DO (114)
19:37:46.684329 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 84: (tos 0x0, ttl 128, id 21761, offset 0, flags [none], proto UDP (17), length 70)
192.168.30.10.56740 > 192.168.30.1.53: [udp sum ok] 7668+ [1au] A? ocsp.pki.goog. ar: . OPT UDPsize=4000 DO (42)
19:37:46.784894 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 303: (tos 0x0, ttl 64, id 46713, offset 0, flags [none], proto UDP (17), length 289)
192.168.30.1.53 > 192.168.30.10.56740: [bad udp cksum 0xbe7a -> 0x8203!] 7668 q: A? ocsp.pki.goog. 3/0/1 ocsp.pki.goog. CNAME pki-goog.l.google.com., ocsp.pki.goog. RRSIG, pki-goog.l.google.com. A 216.58.197.67 ar: . OPT UDPsize=512 DO (261)
19:37:46.797393 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 92: (tos 0x0, ttl 128, id 21762, offset 0, flags [none], proto UDP (17), length 78)
192.168.30.10.65048 > 192.168.30.1.53: [udp sum ok] 1915+ [1au] AAAA? pki-goog.l.google.com. ar: . OPT UDPsize=4000 DO (50)
19:37:46.886845 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 86: (tos 0x0, ttl 128, id 21763, offset 0, flags [none], proto UDP (17), length 72)
192.168.30.10.65531 > 192.168.30.1.53: [udp sum ok] 8360+ [1au] A? www.gstatic.com. ar: . OPT UDPsize=4000 DO (44)
19:37:46.896995 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 120: (tos 0x0, ttl 64, id 20559, offset 0, flags [none], proto UDP (17), length 106)
192.168.30.1.53 > 192.168.30.10.65048: [bad udp cksum 0xbdc3 -> 0x0df6!] 1915 q: AAAA? pki-goog.l.google.com. 1/0/1 pki-goog.l.google.com. AAAA 2404:6800:4007:800::2003 ar: . OPT UDPsize=512 DO (78)
19:37:46.926312 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 102: (tos 0x0, ttl 64, id 64827, offset 0, flags [none], proto UDP (17), length 88)
192.168.30.1.53 > 192.168.30.10.65531: [bad udp cksum 0xbdb1 -> 0x99b0!] 8360 q: A? www.gstatic.com. 1/0/1 www.gstatic.com. A 216.58.200.131 ar: . OPT UDPsize=512 DO (60)
19:37:46.940437 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 86: (tos 0x0, ttl 128, id 21764, offset 0, flags [none], proto UDP (17), length 72)
192.168.30.10.64984 > 192.168.30.1.53: [udp sum ok] 52274+ [1au] AAAA? www.gstatic.com. ar: . OPT UDPsize=4000 DO (44)
19:37:47.040485 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 64, id 55529, offset 0, flags [none], proto UDP (17), length 100)
192.168.30.1.53 > 192.168.30.10.64984: [bad udp cksum 0xbdbd -> 0xa1dc!] 52274 q: AAAA? www.gstatic.com. 1/0/1 www.gstatic.com. AAAA 2404:6800:4007:80e::2003 ar: . OPT UDPsize=512 DO (72)
19:37:47.144503 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 86: (tos 0x0, ttl 128, id 21765, offset 0, flags [none], proto UDP (17), length 72)
192.168.30.10.56615 > 192.168.30.1.53: [udp sum ok] 62373+ [1au] A? ssl.gstatic.com. ar: . OPT UDPsize=4000 DO (44)
19:37:47.156736 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 102: (tos 0x0, ttl 64, id 11625, offset 0, flags [none], proto UDP (17), length 88)
192.168.30.1.53 > 192.168.30.10.56615: [bad udp cksum 0xbdb1 -> 0x4595!] 62373 q: A? ssl.gstatic.com. 1/0/1 ssl.gstatic.com. A 216.58.200.131 ar: . OPT UDPsize=512 DO (60)
19:37:47.169332 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 86: (tos 0x0, ttl 128, id 21766, offset 0, flags [none], proto UDP (17), length 72)
192.168.30.10.65495 > 192.168.30.1.53: [udp sum ok] 22243+ [1au] AAAA? ssl.gstatic.com. ar: . OPT UDPsize=4000 DO (44)
19:37:47.208542 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 114: (tos 0x0, ttl 64, id 14167, offset 0, flags [none], proto UDP (17), length 100)
192.168.30.1.53 > 192.168.30.10.65495: [bad udp cksum 0xbdbd -> 0xe53c!] 22243 q: AAAA? ssl.gstatic.com. 1/0/1 ssl.gstatic.com. AAAA 2404:6800:4007:812::2003 ar: . OPT UDPsize=512 DO (72)
19:37:47.923985 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 88: (tos 0x0, ttl 128, id 21767, offset 0, flags [none], proto UDP (17), length 74)
192.168.30.10.56078 > 192.168.30.1.53: [udp sum ok] 18912+ [1au] A? plus.l.google.com. ar: . OPT UDPsize=4000 DO (46)
19:37:47.990989 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 91: (tos 0x0, ttl 128, id 21768, offset 0, flags [none], proto UDP (17), length 77)
192.168.30.10.65503 > 192.168.30.1.53: [udp sum ok] 47322+ [1au] A? adservice.google.com. ar: . OPT UDPsize=4000 DO (49)
19:37:48.018789 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 104: (tos 0x0, ttl 64, id 31975, offset 0, flags [none], proto UDP (17), length 90)
192.168.30.1.53 > 192.168.30.10.56078: [bad udp cksum 0xbdb3 -> 0x09d9!] 18912 q: A? plus.l.google.com. 1/0/1 plus.l.google.com. A 216.58.200.142 ar: . OPT UDPsize=512 DO (62)
19:37:48.025853 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 147: (tos 0x0, ttl 64, id 48451, offset 0, flags [none], proto UDP (17), length 133)
192.168.30.1.53 > 192.168.30.10.65503: [bad udp cksum 0xbdde -> 0x16d2!] 47322 q: A? adservice.google.com. 2/0/1 adservice.google.com. CNAME pagead46.l.doubleclick.net., pagead46.l.doubleclick.net. A 172.217.163.66 ar: . OPT UDPsize=512 DO (105)
19:37:48.030085 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 88: (tos 0x0, ttl 128, id 21769, offset 0, flags [none], proto UDP (17), length 74)
192.168.30.10.55601 > 192.168.30.1.53: [udp sum ok] 38158+ [1au] AAAA? plus.l.google.com. ar: . OPT UDPsize=4000 DO (46)
19:37:48.037667 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 97: (tos 0x0, ttl 128, id 21770, offset 0, flags [none], proto UDP (17), length 83)
192.168.30.10.64820 > 192.168.30.1.53: [udp sum ok] 1659+ [1au] AAAA? pagead46.l.doubleclick.net. ar: . OPT UDPsize=4000 DO (55)
19:37:48.125804 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 116: (tos 0x0, ttl 64, id 15341, offset 0, flags [none], proto UDP (17), length 102)
192.168.30.1.53 > 192.168.30.10.55601: [bad udp cksum 0xbdbf -> 0x261c!] 38158 q: AAAA? plus.l.google.com. 1/0/1 plus.l.google.com. AAAA 2404:6800:4007:808::200e ar: . OPT UDPsize=512 DO (74)
19:37:48.133635 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 125: (tos 0x0, ttl 64, id 1663, offset 0, flags [none], proto UDP (17), length 111)
192.168.30.1.53 > 192.168.30.10.64820: [bad udp cksum 0xbdc8 -> 0xa76c!] 1659 q: AAAA? pagead46.l.doubleclick.net. 1/0/1 pagead46.l.doubleclick.net. AAAA 2404:6800:4007:80b::2002 ar: . OPT UDPsize=512 DO (83)
19:37:48.158054 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 93: (tos 0x0, ttl 128, id 21771, offset 0, flags [none], proto UDP (17), length 79)
192.168.30.10.56439 > 192.168.30.1.53: [udp sum ok] 39011+ [1au] A? adservice.google.co.in. ar: . OPT UDPsize=4000 DO (51)
19:37:48.196628 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 149: (tos 0x0, ttl 64, id 9876, offset 0, flags [none], proto UDP (17), length 135)
192.168.30.1.53 > 192.168.30.10.56439: [bad udp cksum 0xbde0 -> 0x09b1!] 39011 q: A? adservice.google.co.in. 2/0/1 adservice.google.co.in. CNAME pagead46.l.doubleclick.net., pagead46.l.doubleclick.net. A 216.58.197.34 ar: . OPT UDPsize=512 DO (107)
19:37:48.329040 00:0c:29:7c:d7:bf > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 128, id 21772, offset 0, flags [none], proto UDP (17), length 84)
192.168.30.10.65327 > 192.168.30.1.53: [udp sum ok] 23525+ [1au] A? googleads.g.doubleclick.net. ar: . OPT UDPsize=4000 DO (56)
19:37:48.368070 00:0c:29:e8:7d:fd > 00:0c:29:7c:d7:bf, ethertype IPv4 (0x0800), length 139: (tos 0x0, ttl 64, id 35971, offset 0, flags [none], proto UDP (17), length 125)
192.168.30.1.53 > 192.168.30.10.65327: [bad udp cksum 0xbdd6 -> 0xf6c8!] 23525 q: A? googleads.g.doubleclick.net. 2/0/1 googleads.g.doubleclick.net. CNAME pagead46.l.doubleclick.net., pagead46.l.doubleclick.net. A 172.217.163.66 ar: . OPT UDPsize=512 DO (97)
19:37:49.182724 00:0c:29:1a:fe:22 > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 75: (tos 0x0, ttl 128, id 28443, offset 0, flags [none], proto UDP (17), length 61)
192.168.30.11.59921 > 198.41.0.4.53: [udp sum ok] 22445 A? www.youtube.com. (33)
19:37:53.723360 00:0c:29:1a:fe:22 > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 75: (tos 0x0, ttl 128, id 12837, offset 0, flags [none], proto UDP (17), length 61)
192.168.30.11.59921 > 199.7.83.42.53: [udp sum ok] 22445 A? www.youtube.com. (33)
19:37:53.724150 00:0c:29:1a:fe:22 > 00:0c:29:e8:7d:fd, ethertype IPv4 (0x0800), length 75: (tos 0x0, ttl 128, id 3968, offset 0, flags [none], proto UDP (17), length 61)
192.168.30.11.59921 > 193.0.14.129.53: [udp sum ok] 22445 A? www.youtube.com. (33) -
Ok... So couple of things... Your handing out 2 different ns there, the 8.8.4.4 and the router... You can never be sure which one the client will use in such a setup..
BTW - you understand handing out a public NS like that means your clients will never be able to resolve anything locally.. And you will be sending any queries for anything local out to google..
Also you have wins setup there.. WTF?? And it sure and the hell would not be 8.8.8.8 ;)
So something is blocking your wifi clients from talking to pfsense for dns then... More than likely your asus is doing some sort of BS dns redirect... If your not seeing the query to pfsense, then there is NO WAY it can forward it on now is there..
Vs trying to weed through all the noise, its easier to filter your traffic down on your sniff to the IP your interested in, ie the wan IP of your wifi router.. By default packet capture stops at 100, so its possible you missed it? I would limit your sniff to only the ip of your wifi router.. Then try your test again.. I would also go into AP mode and try it that way... Easy way to get into AP mode is just turn off dhcp on your wifi router, give it an IP on your network - 192.168.30 in your case, and connect the wifi router to your network via one of the LAN ports on the router vs its wan... Now your wifi clients should get dhcp from pfsense.. And this would take any nonsense filtering your router is doing out of the picture... So then sniff on pfsense again and validate your dns query is getting pfsense..
Pfsense can not do anything with traffic it never sees..
-
@johnpoz :
Just to test I have connected my Asus Wifi router in AP mode changed the router IP : 192.168.30.100 and disabled DHCP, connected cable in LAN port.
I have connected wifi client through wifi router. I can see it is taking IP from Windows DHCP server which is on LAN network. I can able to ping pfSense LAN gateway(i)192.168.30.1 but internet is not working attached screen shot below :
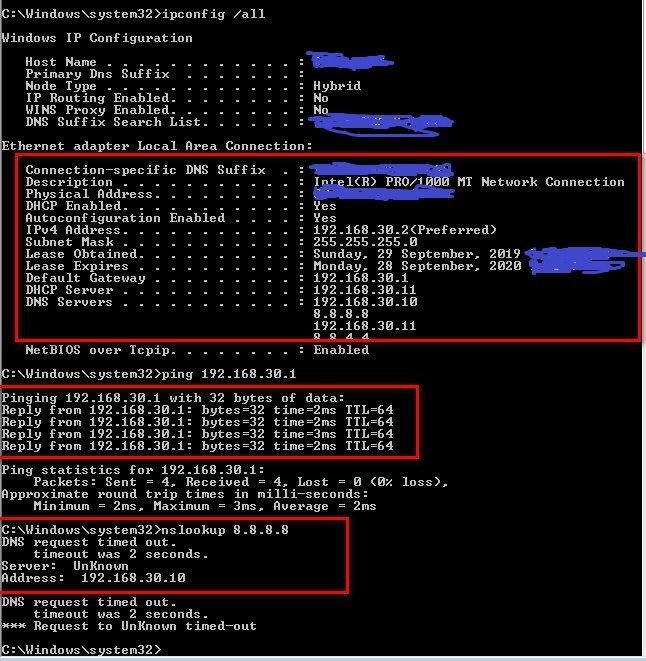
-
And did you sniff to see that traffic is getting to pfsense.. Again pfsense can not do anything with traffic that it does not see..
Not sure what you think a nslookup for 8.8.8.8 is going to do that doesn't point traffic there? And you also asked some box at 192.168.30.10..
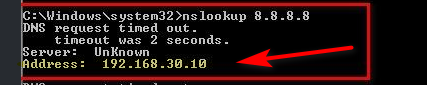
And what box is that? Your windows dhcp server?
if you want to change the server you use with nslookup you need to call it out via server command
$ nslookup Default Server: pi-hole.local.lan Address: 192.168.3.10 > server 8.8.8.8 Default Server: dns.google Address: 8.8.8.8 > google.com Server: dns.google Address: 8.8.8.8 Non-authoritative answer: Name: google.com Addresses: 2607:f8b0:4009:811::200e 216.58.192.238 -
@johnpoz :
192.168.30.10 is Windows DNS Server along with domain controller.. I have added 8.8.8.8 and 8.8.4.4 in DNS forwarder as well.
FYI : In DHCP scope I have added nameserver as 8.8.8.8 and 8.8.4.4
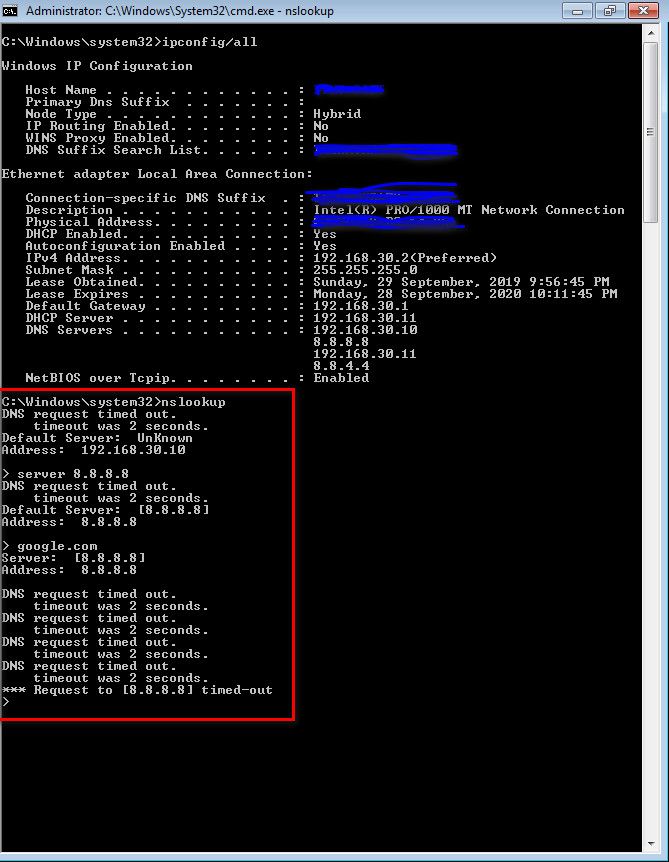
-
Ok... Again lets go over it yet again... Have you sniffed trying to go to 8.8.8.8 for your dns query.. Is pfsense showing the traffic actually got there?? Maybe your client is blocking dns queries?
You know know you can ping pfsense IP 30.1, and you know how to direct your dns to 8.8.8.8 - so validate that pfsense is actually seeing this traffic!
How about you change your dns server via the command to say pfsense IP.. does it work then?
-
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Ok... Again lets go over it yet again... Have you sniffed trying to go to 8.8.8.8 for your dns query.. Is pfsense showing the traffic actually got there?? Maybe your client is blocking dns queries?
I have tried to 8.8.8.8 for dns query from pfsense it is working.
You know know you can ping pfsense IP 30.1, and you know how to direct your dns to 8.8.8.8 - so validate that pfsense is actually seeing this traffic!
How about you change your dns server via the command to say pfsense IP.. does it work then? I have changed IP to pfsense (ie)192.168.30.1 I dont see dns query is working from wifi client.If any client passing through wifi router .. internet is not working. Any client in LAN network (ie) windows 07, windows 2012 server internet is working fine.. so I can say pfsense is routing the internet correctly..but when it comes to wifi router ..wifi client is not getting connection to internet..
-
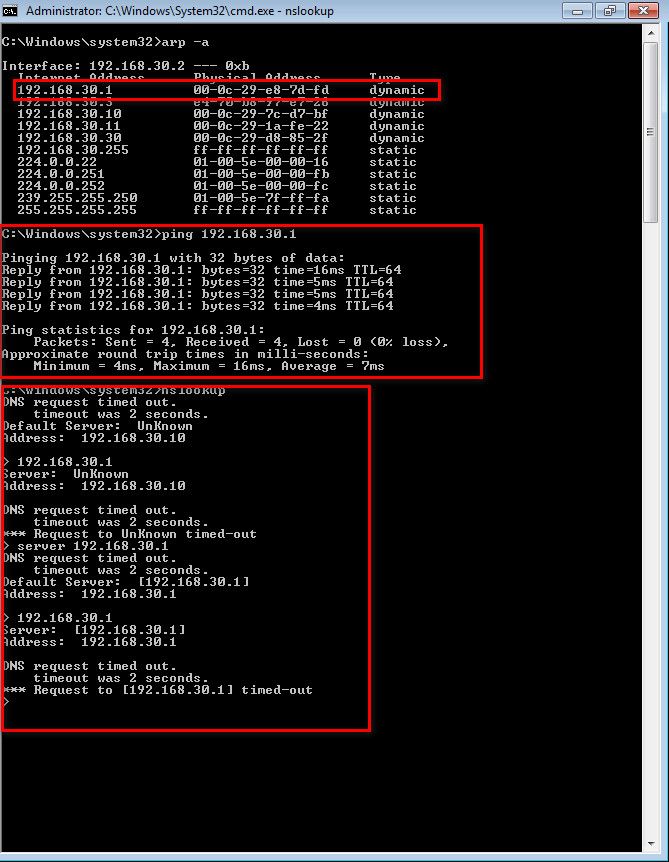
Can a wifi client ping pfsense 192.168.30.1 from your wifi client? Have you validated the pings are being answered by pfsense via say a sniff on pfsense, validating the mac address is actually pfsense?
Your never going to figure out what is happening without some basic troubleshooting.
example
$ arp -a Interface: 192.168.9.100 --- 0xf Internet Address Physical Address Type 192.168.9.8 00-1f-29-54-17-14 dynamic 192.168.9.10 00-11-32-7b-29-7d dynamic 192.168.9.11 00-11-32-7b-29-7e dynamic 192.168.9.253 00-08-a2-0c-e6-24 dynamicYou can see that mac for pfsense IP is actually pfsense interface.. Status interfaces
Status up MAC Address 00:08:a2:0c:e6:24 - ADI Engineering IPv4 Address 192.168.9.253Sniff on pfsense ping and dns query..
$ ping 192.168.9.253 Pinging 192.168.9.253 with 32 bytes of data: Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.9.253: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms12:07:05.640192 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1239, length 40 12:07:05.640235 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1239, length 40 12:07:06.646101 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1240, length 40 12:07:06.646124 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1240, length 40 12:07:07.652045 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1241, length 40 12:07:07.652069 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1241, length 40 12:07:08.657025 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1242, length 40 12:07:08.657045 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1242, length 40192.168.9.100.51363 > 8.8.8.8.53: [udp sum ok] 25160+ [1au] A? www.lasjldsjfsljflsjdslfj.com. ar: . OPT UDPsize=4096 (70) 12:10:49.834316 00:08:a2:0c:e6:24 > 00:13:3b:2f:67:62, ethertype IPv4 (0x0800), length 173: (tos 0x0, ttl 118, id 33758, offset 0, flags [none], proto UDP (17), length 159) 8.8.8.8.53 > 192.168.9.100.51363: [udp sum ok] 25160 NXDomain q: A? www.lasjldsjfsljflsjdslfj.com. 0/1/1 ns: com. SOA a.gtld-servers.net. nstld.verisign-grs.com. 1569777031 1800 900 604800 86400 ar: . OPT UDPsize=512 (131) 12:10:50.739582 00:13:3b:2f:67:62 > 00:08:a2:0c:e6:24, ethertype IPv4 (0x0800), length 73: (tos 0x0, ttl 128, id 48270, offset 0, flags [none], proto UDP -
@johnpoz said in Firewall Rule to Allow RDP from WAN to LAN......Need help:
Can a wifi client ping pfsense 192.168.30.1 from your wifi client? Have you validated the pings are being answered by pfsense via say a sniff on pfsense, validating the mac address is actually pfsense?
Your never going to figure out what is happening without some basic troubleshooting.
example
$ arp -a Interface: 192.168.9.100 --- 0xf Internet Address Physical Address Type 192.168.9.8 00-1f-29-54-17-14 dynamic 192.168.9.10 00-11-32-7b-29-7d dynamic 192.168.9.11 00-11-32-7b-29-7e dynamic 192.168.9.253 00-08-a2-0c-e6-24 dynamicYou can see that mac for pfsense IP is actually pfsense interface.. Status interfaces
Status up MAC Address 00:08:a2:0c:e6:24 - ADI Engineering IPv4 Address 192.168.9.253Sniff on pfsense ping and dns query..
$ ping 192.168.9.253 Pinging 192.168.9.253 with 32 bytes of data: Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Reply from 192.168.9.253: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.9.253: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms12:07:05.640192 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1239, length 40 12:07:05.640235 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1239, length 40 12:07:06.646101 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1240, length 40 12:07:06.646124 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1240, length 40 12:07:07.652045 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1241, length 40 12:07:07.652069 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1241, length 40 12:07:08.657025 IP 192.168.9.100 > 192.168.9.253: ICMP echo request, id 1, seq 1242, length 40 12:07:08.657045 IP 192.168.9.253 > 192.168.9.100: ICMP echo reply, id 1, seq 1242, length 40192.168.9.100.51363 > 8.8.8.8.53: [udp sum ok] 25160+ [1au] A? www.lasjldsjfsljflsjdslfj.com. ar: . OPT UDPsize=4096 (70) 12:10:49.834316 00:08:a2:0c:e6:24 > 00:13:3b:2f:67:62, ethertype IPv4 (0x0800), length 173: (tos 0x0, ttl 118, id 33758, offset 0, flags [none], proto UDP (17), length 159) 8.8.8.8.53 > 192.168.9.100.51363: [udp sum ok] 25160 NXDomain q: A? www.lasjldsjfsljflsjdslfj.com. 0/1/1 ns: com. SOA a.gtld-servers.net. nstld.verisign-grs.com. 1569777031 1800 900 604800 86400 ar: . OPT UDPsize=512 (131) 12:10:50.739582 00:13:3b:2f:67:62 > 00:08:a2:0c:e6:24, ethertype IPv4 (0x0800), length 73: (tos 0x0, ttl 128, id 48270, offset 0, flags [none], proto UDPI can see the mac of pfsense LAN network in my wifi client and also able to ping that IP of that mac, but DNS query is not working.