pfBlockerNG Alias Firewall Rule Question
-
Hi all - just wanted to bump this to see if anyone had any idea whether I described is normal behavior?
If I have an IPv4 UDP Pass firewall rule with a pfBlockerNG created alias in the source and VPN server and port in the destination fields, will pfBlockerNG pick up all UDP packets on that firewall rule even if the packets do not match the IP and port of VPN server (i.e. just random IPv4 UDP traffic)?
Thanks again for your help, I really appreciate it.
-
Post a screenshot of your rules..
-
From previous posts looks like you run OpenVPN.
If you use IPsec you need UDP 4500 & 500.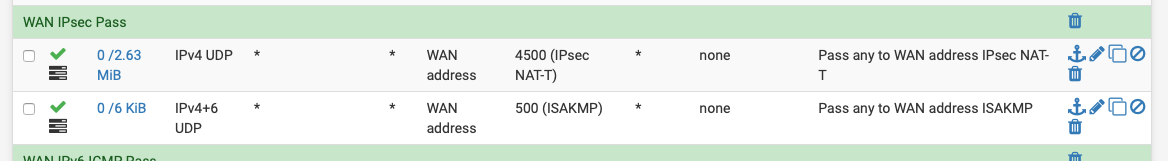
-
Hi @johnpoz and @NogBadTheBad - thanks for getting back to me. Here is a screenshot of my WAN rules - as you can there are only just a couple rules related to OpenVPN, with the pass rule having the pfBlockerNG created alias in the source field:
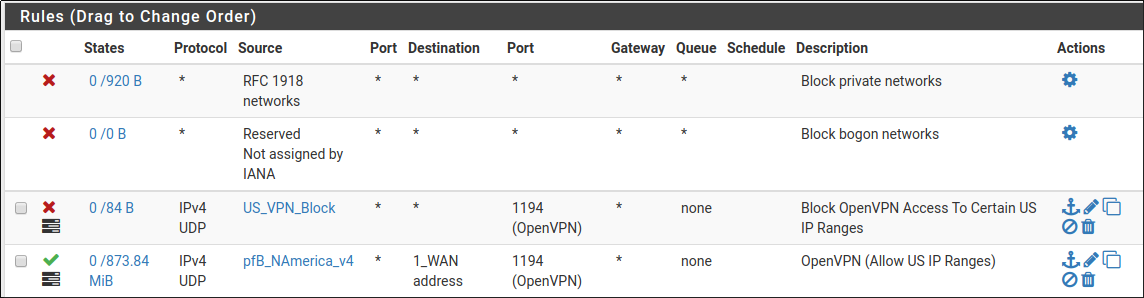
Nevertheless, I still see the packet count going up in the Dashboard widget even though no traffic UDP traffic is going destined for the OpenVPN server / port.
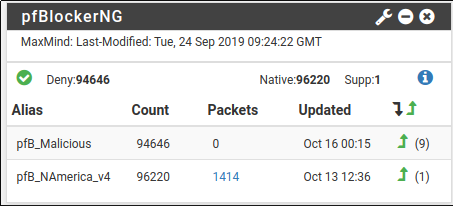
By cross-referending again the firewall logs it seems like all UDP traffic is being counted by the widget somehow. That other UDP traffic is being blocked by the firewall though according to the logs.
Do you guys have any ideas? Thanks again for your help.
-
Shouldn't both point to the WAN interface ?
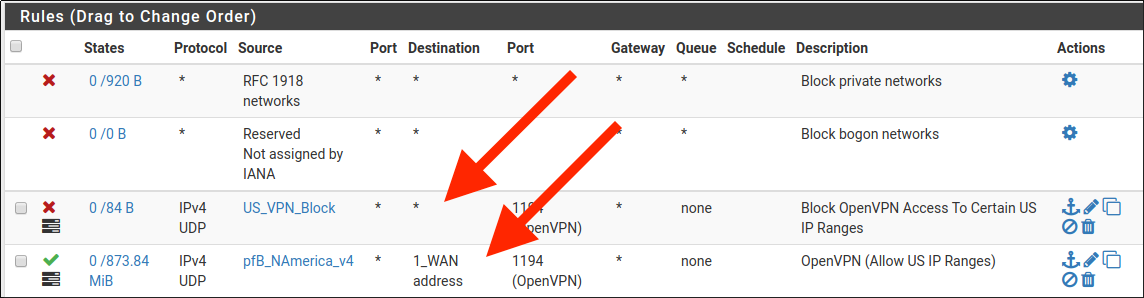
Post the screenshots from your pfBlocker alias, here's what my SSHPERMIT looks like:-
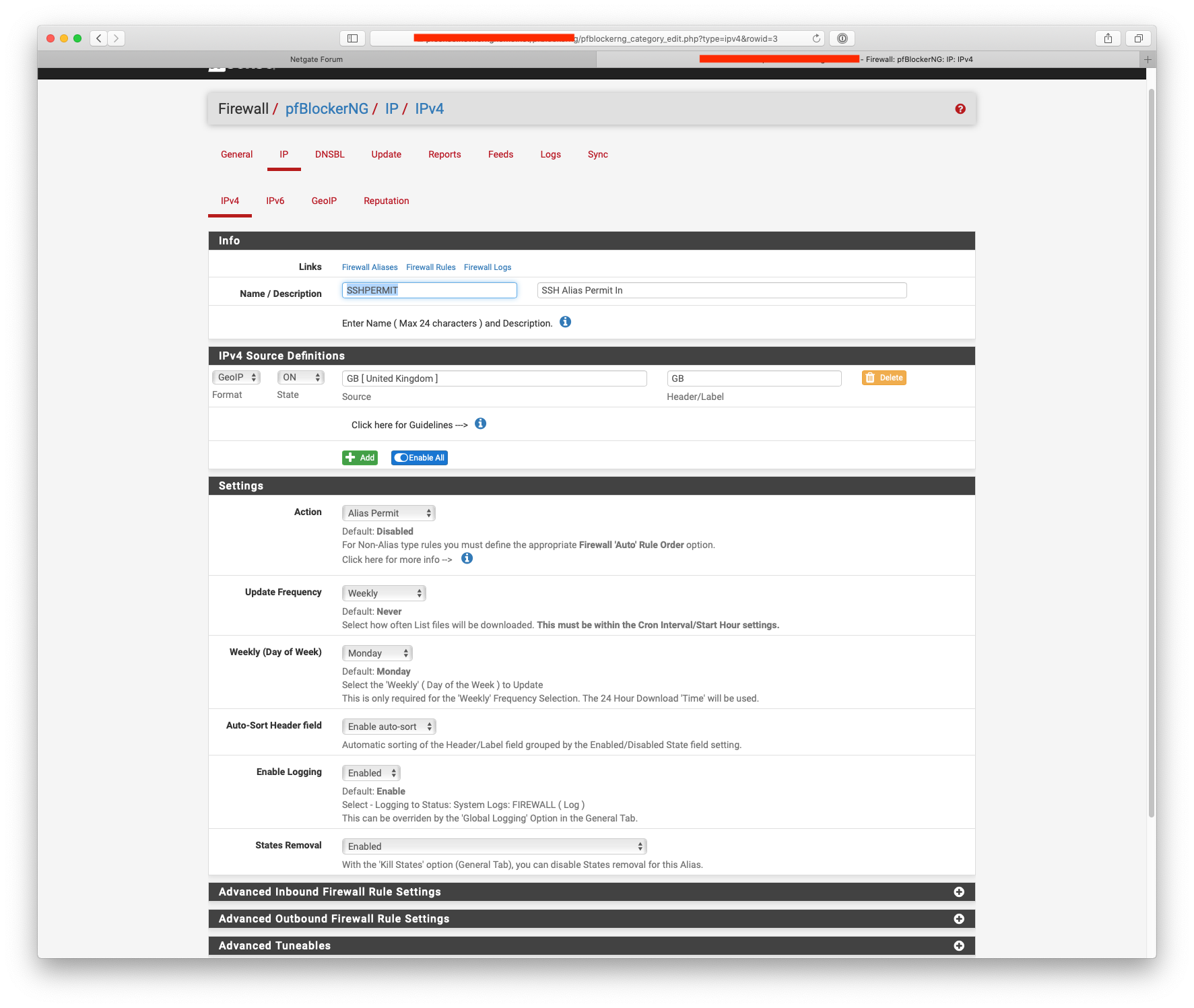
You've not told pfBlocker to create an alias match have you ?
-
HI @NogBadTheBad - thanks for getting back to me. I made the change to the WAN rule.
Also, I'm using the original pfBlockerNG, not pfBlockerNG-devel. Here are the settings for this GeoIP alias:
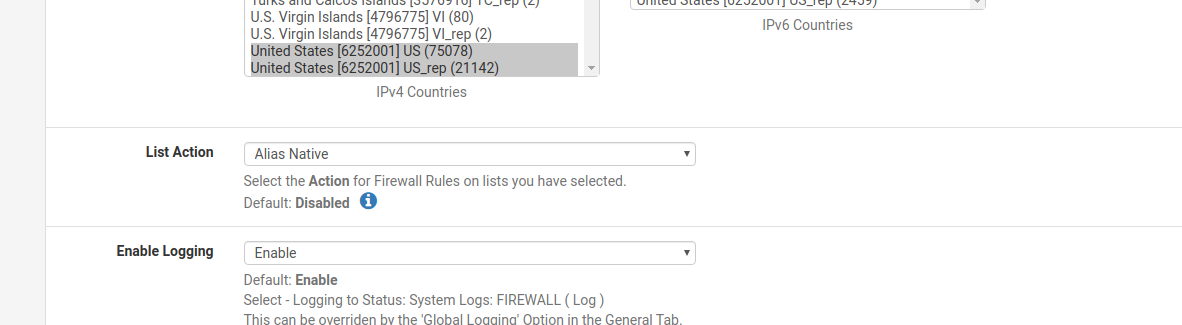
I did to choose "Alias Native" - is that not correct? Thanks again.
-
I'd upgrade to pfBlockerNG-devel.
-
@NogBadTheBad said in pfBlockerNG Alias Firewall Rule Question:
I'd upgrade to pfBlockerNG-devel.
Thanks @NogBadTheBad - is the upgrade seamless? That is, will my settings stick between the two or do I have to reconfigure everything? Also, I assume the upgrade process would be to uninstall the hold pfBlockerNG first and then install pfBlockerNG-devel? Thanks again.
-
Not sure TBH I went straight to pfBlockerNG-devel, maybe @BBcan177 could advise.
-
This post is deleted! -
Thanks @NogBadTheBad - I really appreciate the help. Hopefully @BBcan177 could advise me as well on what the best path forward here would be. Thanks again!
-
Well, I went ahead and wiped out my pfBlockerNG install tonight and reinstalled with pfBlockerNG-devel including my block lists. Set up a Permit Alias for VPN similar to what @NogBadTheBad did for SSH in the screenshot above. Applied this alias as the source on the inbound VPN firewall rule on WAN. However, I still see all UDP traffic (packets) being picked up and counted by the widget in the dashboard. Cross-checking against the firewall logs the UDP traffic is being blocked by the default deny rule. I just don't quite understand why it is being counted as a PASS packet. Does anyone have any ideas? Does the traffic hit pfBlockerNG first before the default deny rule? Thanks again.
Edit: I also found this all thread on Alias which indicates that a Permit Alias would be the right choice in this case:
https://forum.netgate.com/topic/121185/pfblockerng-alias
-
@tman222 said in pfBlockerNG Alias Firewall Rule Question:
I just don't quite understand why it is being counted as a PASS packet.
Remember, the NIC sees the packet before the firewall does!
-
@NollipfSense said in pfBlockerNG Alias Firewall Rule Question:
@tman222 said in pfBlockerNG Alias Firewall Rule Question:
I just don't quite understand why it is being counted as a PASS packet.
Remember, the NIC sees the packet before the firewall does!
Thanks @NollipfSense, I appreciate your response.
So that does that mean that pfBlockerNG sees the packets before they hit the firewall's default deny rule and that's why they are being counted? Unfortunately I don't know enough about how the package works to be certain on this.
Thanks again.
-
@tman222 Well, I think it would be pfSense that provided pfBlockerNG widget the packet info.