Traffic being blocked on LAN, even though there's an ALL allow rule on the LAN interface
-
Hello,
I run pfSense version 2.4.4-RELEASE-p3 (amd64) in a VMware VM. This traffic comes from an NSX Edge, routes are being exchanged with OSPF.
I see that traffic is being blocked on LAN from the pfSense LAN to the NSX Edge (even though the traffic is initiated from the NSX Edge to the pfSense LAN. In the attachments you can see my firewall rules on LAN and the traffic being blocked.
.
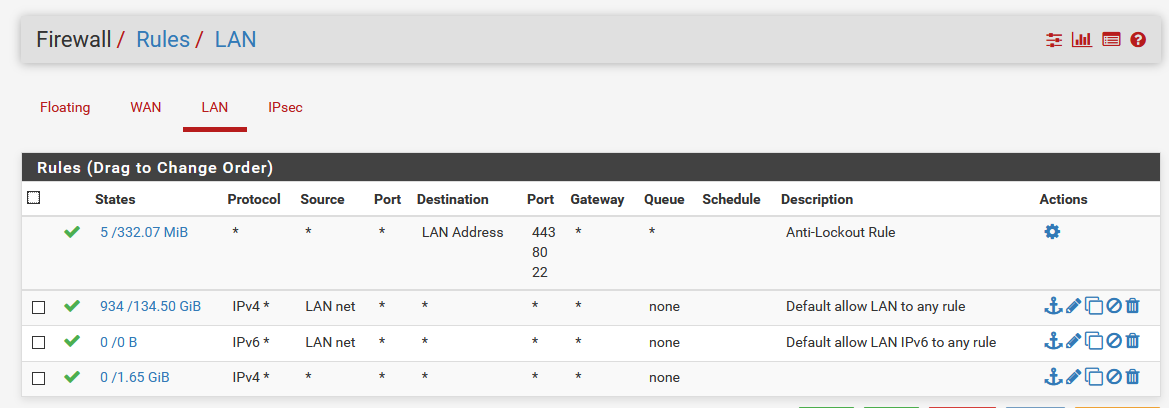
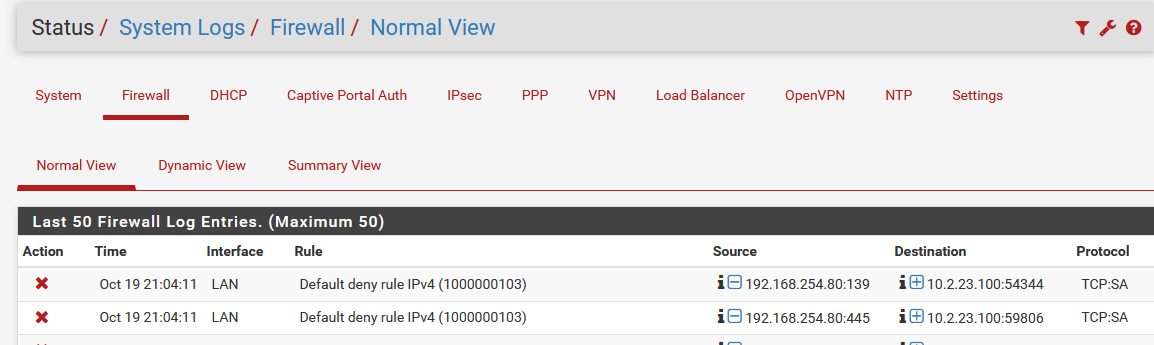
The weird thing is, it does work from other NSX Edges from what I can tell, this problem suddenly started appearing, everything worked fine before and I didn't change anything as far as I can remember
Sorry if I'm not giving enough information, I'm new to the forum.
Kind regards,
MasterWayZ -
Asymmetric Routing
If reply traffic such as TCP:A, TCP:SA, or TCP:RA is shown as blocked in the logs, the problem could be asymmetric routing. See Troubleshooting Blocked Log Entries due to Asymmetric Routing for more info. -
Hi,
I ticked the checkbox "Bypass firewall rules for traffic on the same interface" under System > Advanced, however, the issue is still there, traffic is still being blocked.
-
Fix your asymmetric routing. Based on the information we have that's the best I can do.
Are you seeing broken connections or just seeing log messages?
-
@Derelict I am seeing broken connections, which is why I asked for help. I'm not sure how I can fix asymmetric routing on my OSPF setup. The weird thing is, it used to work fine, but now suddenly it no longer works.
In the article you mentioned, I also tried manually making a firewall rule on LAN following the article.
However, now the blocked traffic in the firewall logs have an icon in front of the interface name as shown here:
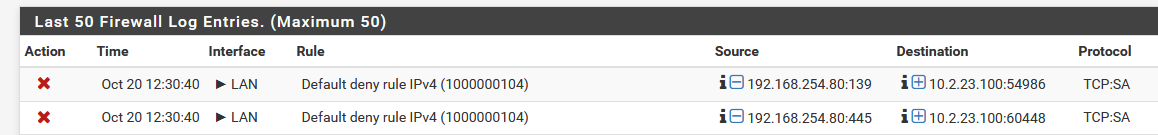
When I look at the rule I made, it does show that it's doing something as the numbers for the states and bytes went up:

-
Why not just fix your routing vs trying to do some hack to allow it..
So somehow 10.2.23.100 talked to 192.168.254.80... But 254.80 sent his syn,ack back to pfsense.. But 10.2..23.100 didn't send its syn through pfsense..
How do you have the routing between these 2 networks setup? If you have a downstream router, then it should be connected via a transit network.. It shouldn't be connected to your lan that has hosts on it.. If your going to do that, then you need to host route on each device in your "transit" network and or nat your downstream so it looks like its in the transit network your using "lan"
You understand why this is a problem right?
If your like this, this is asymmetrical and nothing but issues.
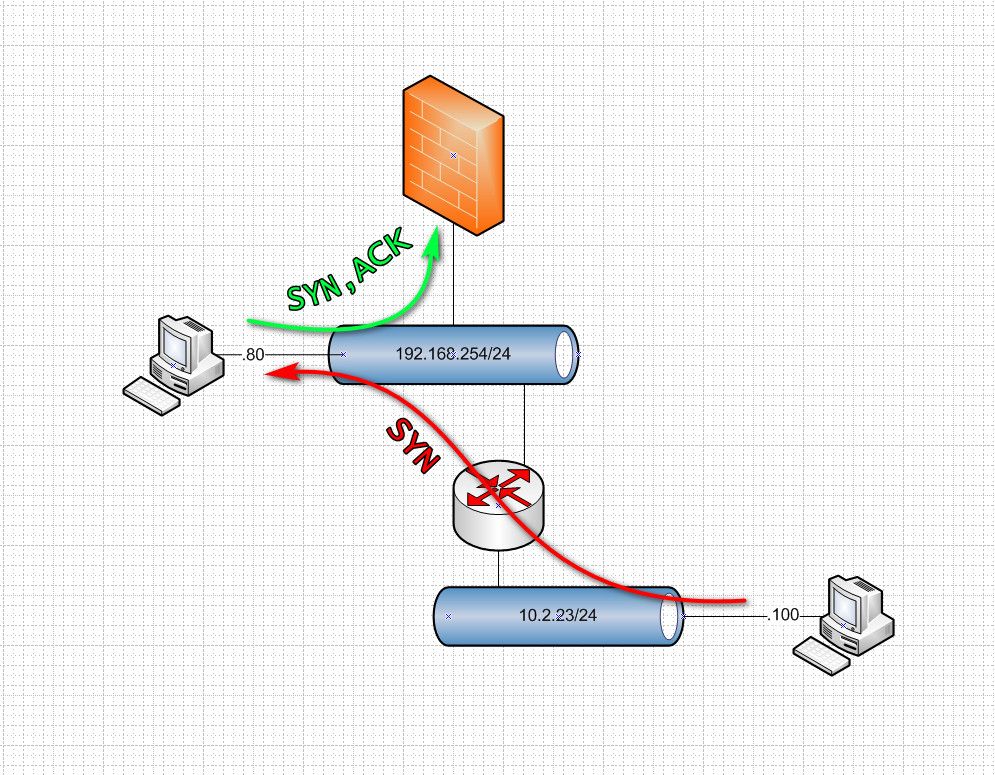
Fix your routing!!! Don't try and set pfsense to pass traffic that is not stateful.
-
@johnpoz Hey,
You're right. Thank you for the drawing, now it makes sense to me on what is happening. I will be working on a fix (in order to add a NIC I need to restart pfSense so I can't do it right now because otherwise people will be mad at me) and will update the post here with progress later today.
Question for you if you don't mind: how did you make that drawing and the arrows? It's really helpful to me.
-
You could do the transit network via a vlan that goes over the same physical network. Until such time you can add another nic.
As to the drawing, just visio (2007) and then little tool I have used for years.. Best $20 every spent on such a tool - I use pretty much daily.. https://www.faststone.org/FSCaptureDetail.htm
Its great for taking screenshots and then annotating them with stuff like the arrows, etc.
-
@johnpoz I've created a port group in VMware and set that up as the transit network. Everything works now as expected, thank you!
-
Glad to hear... Now is that much better than some hack disabling stateful firewall rules.