DNSBL deny all except whitelisted
-
@NollipfSense Thanks, however, this is required for the purpose in a secure isolated environment.
Would you be able to let me know how you have done it using DNSBL in pfsense? -
@PaulMon123 said in DNSBL deny all except whitelisted:
this is required for the purpose in a secure isolated environment.
I am not sure what you mean by isolated environment; however, here are screen shots what I have set up. Note, the best way to guarantee an isolated environment is not connecting to a public IP address.
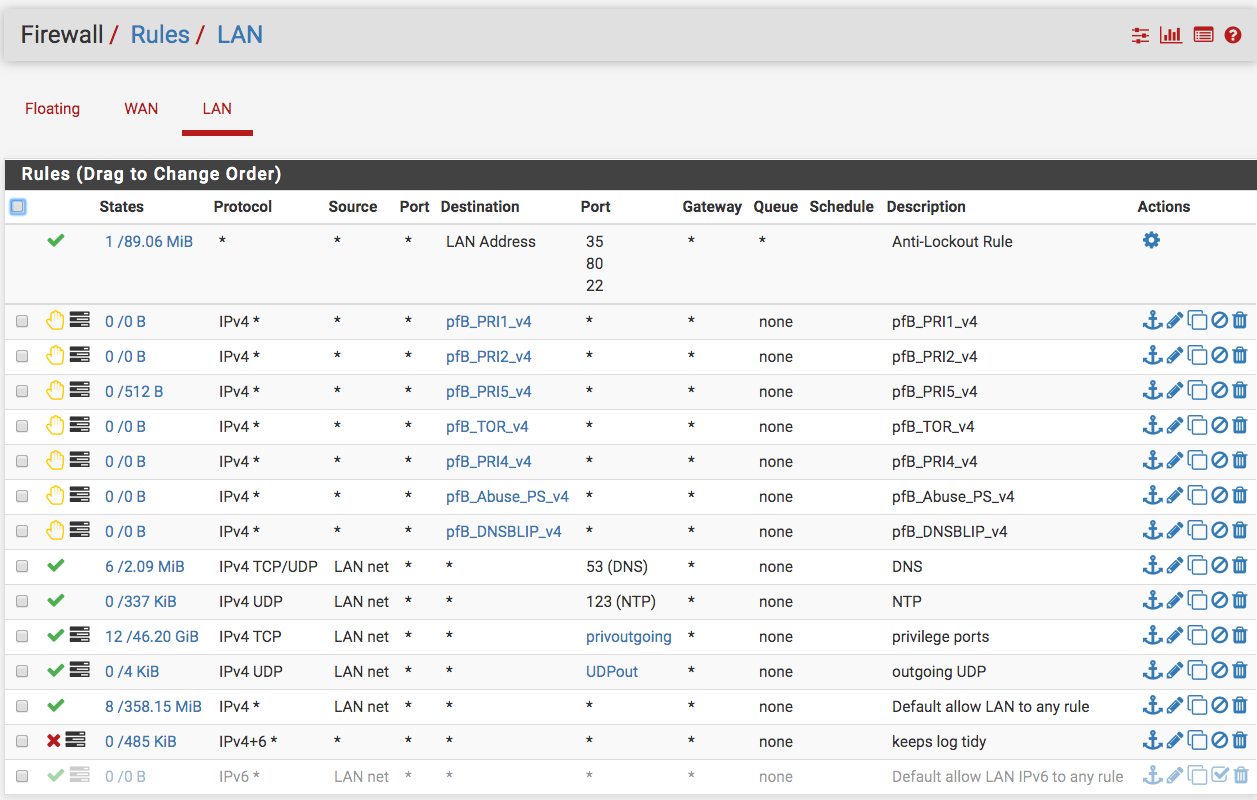
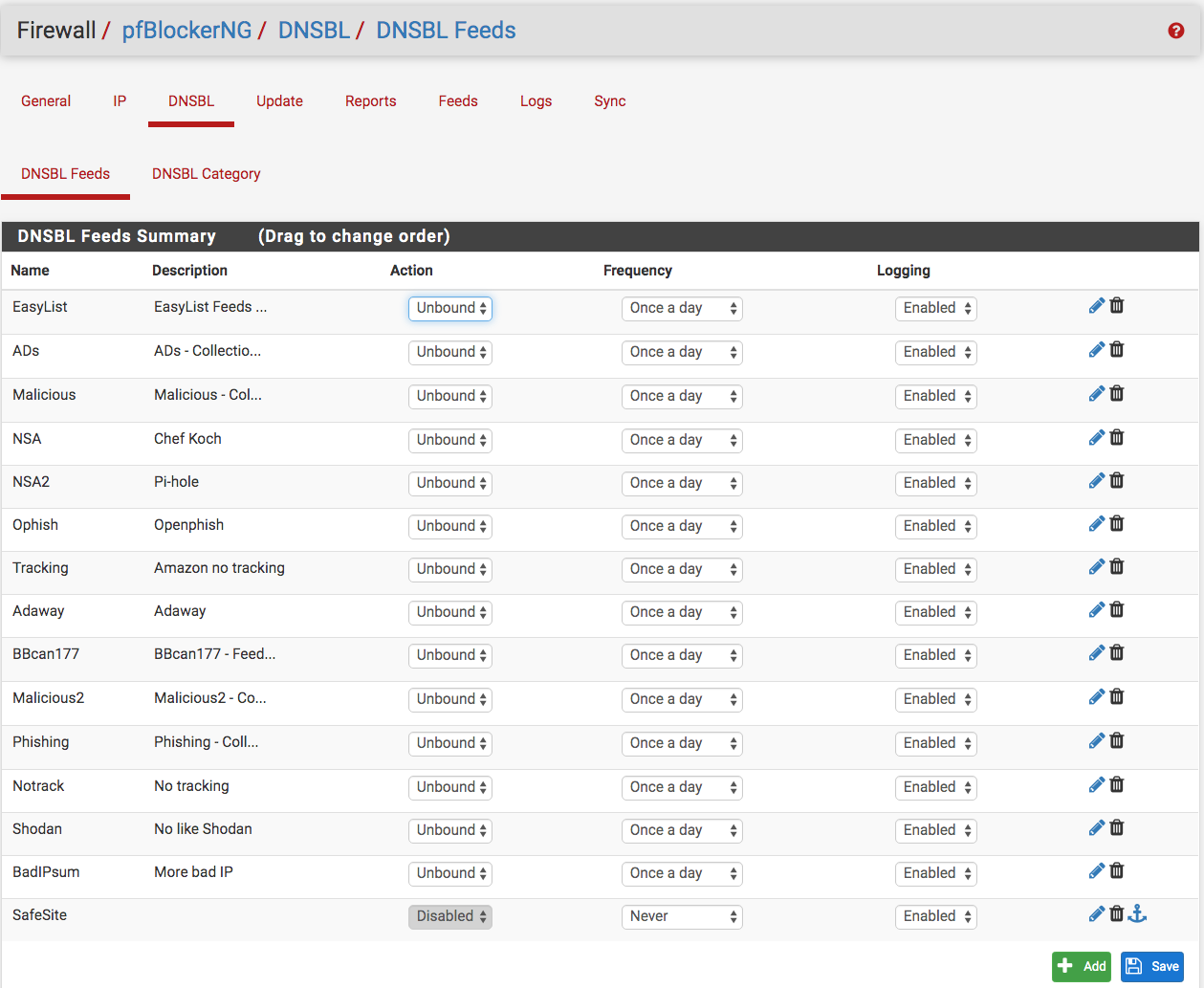
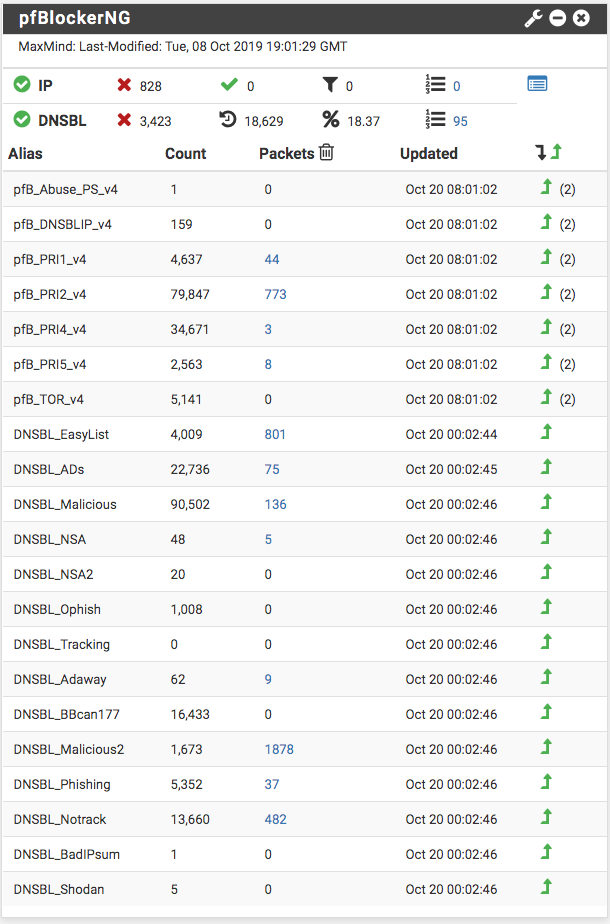
-
OK, let's put it this way. What is the syntax I can use in this field to block all domains?
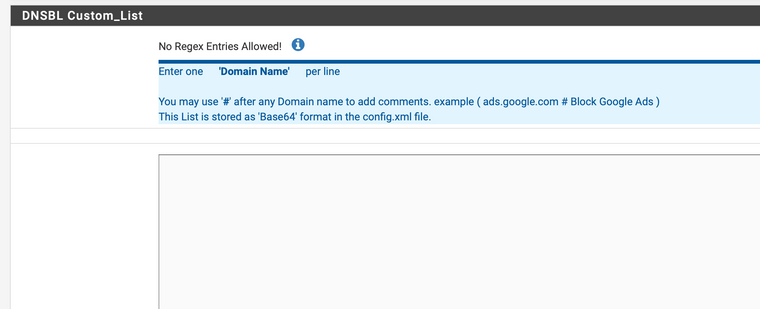
-
@PaulMon123 You will need to wait for @BBcan177 to respond and guide you. My list is only to allow.
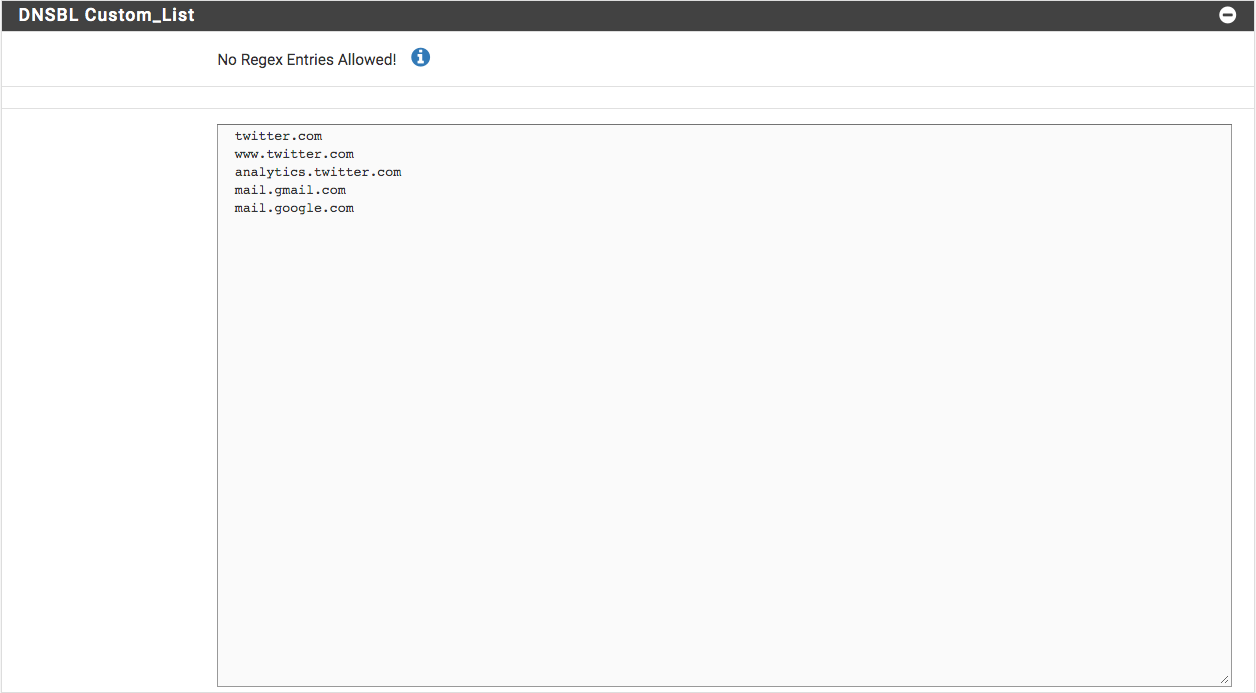
-
@PaulMon123 said in DNSBL deny all except whitelisted:
What is the syntax I can use in this field to block all domains?
Well did you even try to click on the ?
No Regex Entries Allowed! Enter one Domain Name per line Prefix Domain with a "." to Whitelist all Sub-Domains. IE: (.example.com) You may use "#" after any Domain name to add comments. IE: (example.com # Whitelist example.com) This List is stored as 'Base64' format in the config.xml file. Note: These entries are only Whitelisted when Feeds are downloaded or on a 'Force Reload'. Use the Alerts Tab '+' Whitelist Icon to immediately remove a Domain (and any associated CNAMES) from Unbound DNSBL. Note: When manually adding a Domain to the Whitelist, check for any associated CNAMES ie: 'drill @8.8.8.8 example.com' -
Did you even read my response with the screenshot? I'm talking about blocking all, not whitelisting all.
Here is the field:
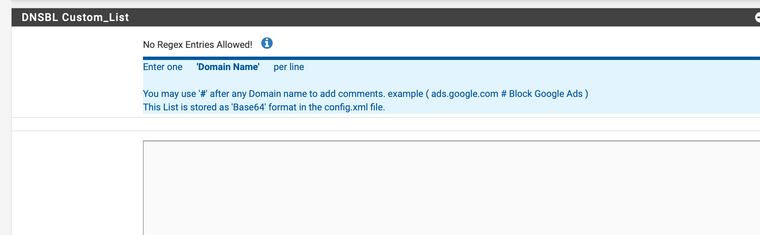
-
@PaulMon123 said in DNSBL deny all except whitelisted:
Did you even read my response with the screenshot? I'm talking about blocking all, not whitelisting all.
Here is the field:

Turn your problem around a bit and think about it using this approach.
You say you want to "block all domains" except a few whitelisted ones. The way to "block all domains" is to simply put a "deny-all" rule in place or else use a negation destination so that you block all traffic except that which is not in the destination set. In your case a negation might be the best option, so something like this --
-
Create a pfBlockerNG alias with the domains you want to allow or "whitelist". By creating the alias, pfBlockerNG will auto-update its IP addresses for the FQDNs you put in the whitelist. Or if the whitelist is a known quantity of relatively stable IP addresses, you could simply use a pfSense alias and dispense with pfBlockerNG entirely.
-
Next, create a Block rule on your LAN where the SOURCE is ANY ANY (IP and port) and the DESTINATION is "!<alias_name>" ANY. Replace <alias_name> with the actual name of your created alias. Also note the negation rule. You can choose this option in the RULE setup section. Put this rule near the top of your LAN rule set.
-
Finally, make sure you follow the above rule with a PASS all (or you could certainly be more restrictive is you want).
So the combination of the two rules above create a situation where attempts from clients on the restricted LAN to contact any IP address that is not in the <alias_name> whitelist are blocked. You could also turn the example above around and do it this way --
-
Create the kind of alias as before.
-
Now create a rule to PASS ANY ANY to <alias_name> ANY.
-
Now immediately follow that rule with a REJECT ANY ANY to ANY ANY rule.
Don't forget, though, that your restricted clients will still need to access a DNS server for domain-to-IP lookup. So you will need to have a rule permitting that up early in the rule chain. Remember that for regular firewall rules (meaning all but Floating Rules), the first match wins and no further rules are evaluated for that traffic.
-
-
@bmeeks Very well presented Bill...after reading your reply, I though a floating rule with quick set enabled too.
-
@NollipfSense said in DNSBL deny all except whitelisted:
@bmeeks Very well presented Bill...after reading your reply, I though a floating rule with quick set enabled too.
A Floating Rule could also work, but I am usually leary of using those unless there is no other choice. They can be a bit tricky because you must set direction, too.
-
Wondered what happened with OP...the answer didn't make sense and Op didn't appreciate?
-
@bmeeks
Thanks for that,
I'd prefer to avoid any dynamic IP rules on a firewall.
In terms of blocking all external traffic it is already done, that's not the point of my question.All I want to do is to block any DNS requests (except ones to specific services) to prevent data leaks using DNS tunneling.
-
@PaulMon123 said in DNSBL deny all except whitelisted:
@bmeeks
Thanks for that,
I'd prefer to avoid any dynamic IP rules on a firewall.
In terms of blocking all external traffic it is already done, that's not the point of my question.All I want to do is to block any DNS requests (except ones to specific services) to prevent data leaks using DNS tunneling.
Still not 100% clear on what you are asking. Do you want to steer all DNS requests to just certain authorized DNS servers? That's not the way I read your initial post.
Or do you mean you want say a lookup for cnn.com to succeed but one for pornsite.com to fail? If so, that is going to be hard to pull off. However, you can certainly intercept and redirect DNS lookups to a specific server or servers. You could then define your own domains there, or you could redirect to some other filtered DNS server.
-
Client requesting cnn.com IP => request goes via pfsense resolver to the external resolver and the client gets CNN IP.
Client requesting ponsite.com => once request hits pfsense resolver it gets blocked and client gets a timeout. -
@PaulMon123 said in DNSBL deny all except whitelisted:
Client requesting cnn.com IP => request goes via pfsense resolver to the external resolver and the client gets CNN IP.
Client requesting ponsite.com => once request hits pfsense resolver it gets blocked and client gets a timeout.To do what you want will require you to configure the
unbound.conffile yourself. Details can be found here and elsewhere on the web.I'm not sure since I'm not an
unboundexpert, but sounds like you need a list of "okay domains" that resolve normally and then a wildcard entry to match all other domains and you want that one to resolve to basically NXDOMAIN. -
Thanks, that's what I thought, I was hoping I can have it done via DNSBL with nice graphical logging and whitelisting.
-
@PaulMon123 said in DNSBL deny all except whitelisted:
All I want to do is to block any DNS requests (except ones to specific services) to prevent data leaks using DNS tunneling.
It seems that most of what I shared geared to accomplishing this, especially when an IPS/IDS is added to the mix. I take it others has physical access to the "secure environment" or it's a server.
This data leaks using DNS tunneling is a hot topic, a potential headache, and I am hoping a package with DNS quarantine coming soon.