pfSense firewall log analysis help request
-
Hello forum,
My pfSense box is behind my ISP's modem, and there is no port forwarding from it (modem) to my pfSense WAN port (192.168.2.2). Everything on the WAN port is blocked and I log it if is isn't a private IP.
In the following snippet, can someone explain to me how a Public IP is able to target the WAN port if there is no port forwarding of any kind on the ISP's modem?
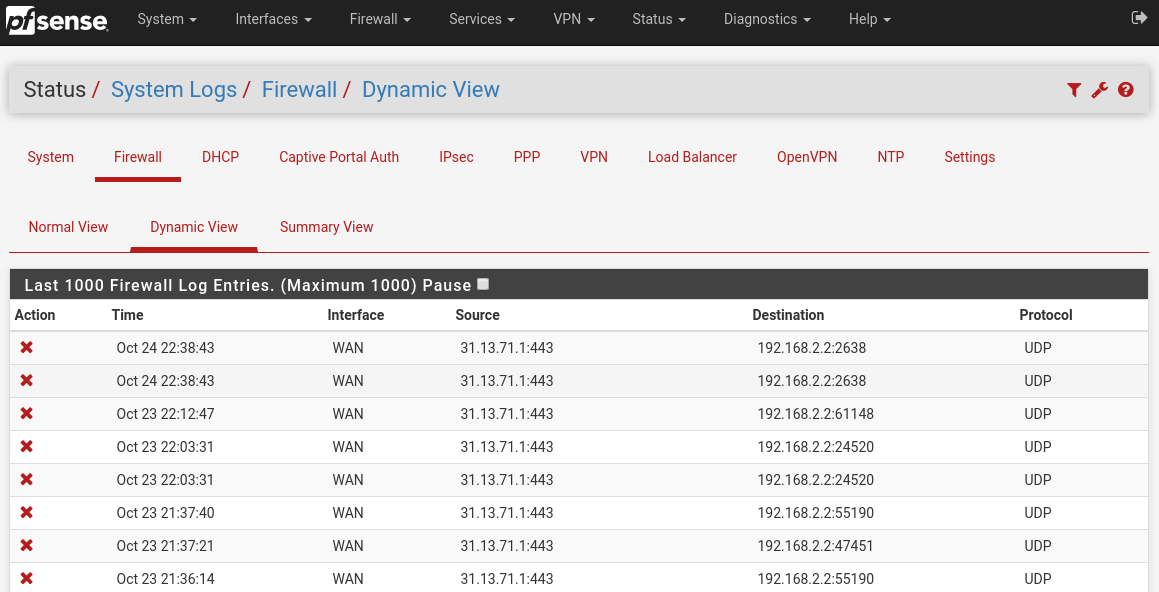
Among all the entries in my log, that IP 31.13.71.1 (and another 31.13.80.8) who seemed to be continuously hammering my WAN port to find something open with HTTPS, is flagged as Facebook crawlers.
What am I missing here and how is that even possible?
Firewall logs snippet:
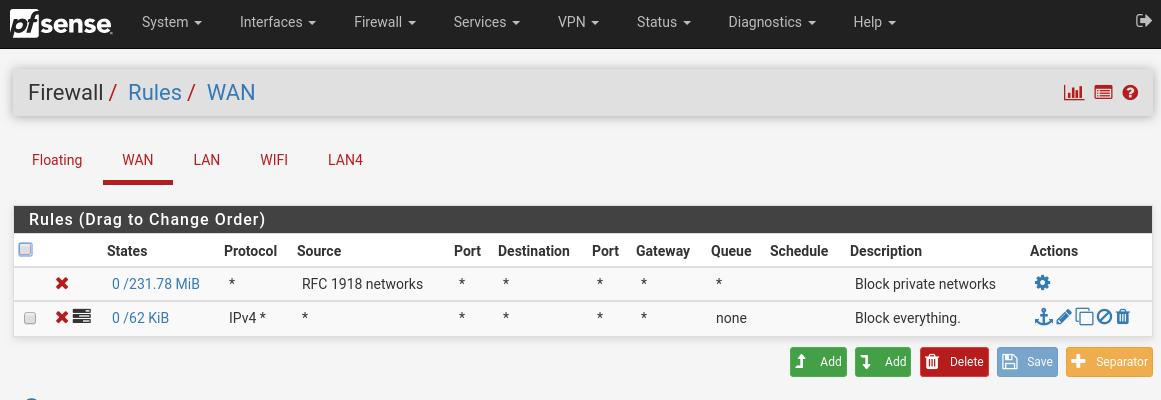
Rules for WAN port:
Thank you for any pointers.
-
@P-J said in pfSense firewall log analysis help request:
31.13.71.1
Your last rule is blocking everything inbound and logging.
-
Read the post again.
How without port forwarding, can a public IP target my WAN port address directly. That's the question.
I am using a Bell Hub 2000 if that can help.
-
@P-J said in pfSense firewall log analysis help request:
Read the post again.
How without port forwarding, can a public IP target my WAN port address directly. That's the question.
I am using a Bell Hub 2000 if that can help.
You'd need to talk to your ISP, they're doing something to forward a non RFC1918 address to a RFC1918 address.
-
@P-J said in pfSense firewall log analysis help request:
Read the post again.
How without port forwarding, can a public IP target my WAN port address directly. That's the question.
I am using a Bell Hub 2000 if that can help.
Did a quick Google search on that modem. It appears to be somewhat of a weird animal with something called PPPoE pass-through, but not a true bridge mode like many other modems offer. I suspect you are seeing the weirdness because of that.
-
@bmeeks said in pfSense firewall log analysis help request:
PPPoE pass-through
PPPeE passthrough is for allowing a device behind the modem (a PC for example) to do the PPPoE connection instead of the modem, which is not my case. The HUB2000 itself perform a PPPoE connection to the ISP for my gigabit connectivity via fiber.
-
On the eve of year 2020, I wish everyone a Happy New Year.
On the topic of this thread, I found out that it is the Netgate SG-3100 itself that communicate to that IP address from time to time. The address is Facebook owned, registered in Ireland but hosted somewhere on the East Coast of the USA.
I don't know what process is trying to 'talk' to Facebook - I don't use it - but this is very suspicious. I did a factory reset of the device and loaded back the last backup and still I see that connection being made. Will try to reinstall pfsense from USBkey and see if that is continuing to happen.
Is this a somekind of keep-alive built-in the device that tries to 'phone-home' ?
-
@P-J said in pfSense firewall log analysis help request:
On the eve of year 2020, I wish everyone a Happy New Year.
On the topic of this thread, I found out that it is the Netgate SG-3100 itself that communicate to that IP address from time to time. The address is Facebook owned, registered in Ireland but hosted somewhere on the East Coast of the USA.
I don't know what process is trying to 'talk' to Facebook - I don't use it - but this is very suspicious. I did a factory reset of the device and loaded back the last backup and still I see that connection being made. Will try to reinstall pfsense from USBkey and see if that is continuing to happen.
Is this a somekind of keep-alive built-in the device that tries to 'phone-home' ?
No, pfSense does not "phone home" or attempt to keep tabs on you. The only traffic that pfSense would initiate is the check for a firmware update each time you load the home page. That check is done once when that page loads.
It could very well be that the IP address you see as belonging to Facebook is (1) no longer really Facebook and the ARIN lookup is outdated; or (2) the IP is within a block owned and registered to Facebook but leased out or used by other services.
It might also be reverse pointer lookups to get a domain from some installed package on the firewall. Snort does not do DNS lookups unless you click the icon, but I think a few other packages will do DNS lookups to convert IP addresses in logs to their host names when possible.
The short answer is I doubt you have anything malicious going on. If it bothers you, though, simply block the traffic and then see what breaks.