Please help me understand why outbound blocks are occuring.
-
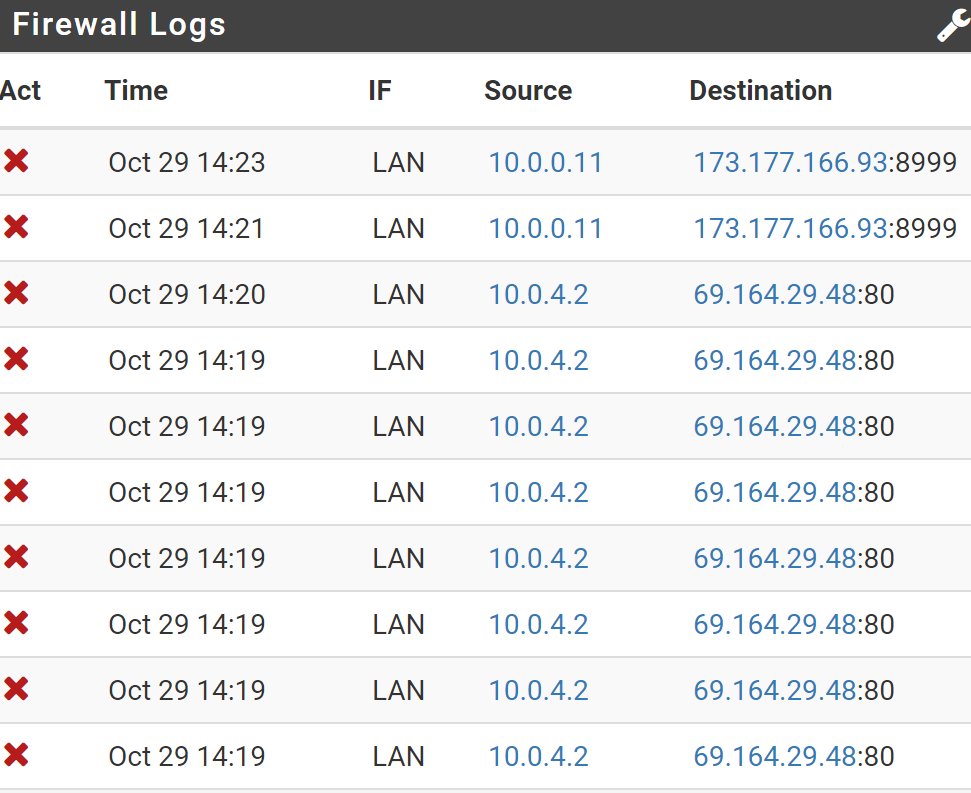
In my Dashboard, Firewall logs, I see blocked packets I didn't expect to see. I filter on IF to LAN and to block.
source IP are my internal devices, destination IPs are private Internet hosted devices. so this seems to be outbound blocking. But why?
Firewall, Rules, LAN only lists the Antilockout rule, and the default allow LAN to any ip4 / ip6 rules.
click on block icon tells me the rule that triggered the action was Default deny rule IPV4 -
Probably out of state packets. Post the whole log screen.
-
That is the whole screen from the dashboard. I can post from the system log screen if that is helpful.
-
Yes, System Logs > Firewall gives more information. Here you're missing the protocol and the TCP flag.
-
Status, System Logs, Firewall, normal view. the vast majority are WAN and inbound to my public ip, and those make sense. these are a few samples with LAN as the interface.
Oct 29 15:32:03 LAN Default deny rule IPv4 (1000000103) 10.0.3.5:62201 142.229.173.56:443 TCP:FPA Oct 29 15:32:46 LAN Default deny rule IPv4 (1000000103) 10.0.3.5:62201 142.229.173.56:443 TCP:FPA Oct 29 15:31:17 LAN Default deny rule IPv4 (1000000103) 10.0.0.11:39424 68.11.153.231:42003 TCP:PAThey are all TCP, the flag is always RA, FA, PA, or FPA that I have found
-
@mervincm
PS With your hint of the importance of the protocol + flag , my forum searching now is revealing much better results, thank you for that. -
There is also a filter function available at System Logs > Firewall.
Packets with such TCP flags are only logged if pfSense has no state for it in its state table. So may already it has already deletet the connection.
If there is no problem on the LAN devices with that like slow site reloading you may ignore that. The device will open a new connection.
Otherwise it could also indicate an asymmetric routing.The connection timeout is affected by "Firewall Optimization Options" in System > Advanced > Firewall & NAT.
It is also possible to configure individual timeouts for different packet types at this page.