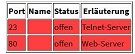
How to close Port 23, 53 and 80 on WAN?
-
And you clearly stated you did not configure any of that...
My VPN provider supports it, but I have not changed any settings on my VPN account, it is turned off by default
And sure they might offer you to forward port 32456 to your port 80.. But it has to be freaking configured!!! And that is not 80... If it was 80 they could do it once for each IP...
Again what your seeing is you scanning freaking google.com and asking why they show 80 open... Turn off your vpn and actually scan pfsense WAN IP... Not your vpn endpoint.. Now what do you see open??
-
Again what your seeing is you scanning freaking google.com and asking why they show 80 open...
Lol no, I scan my OWN public VPN ip, I dont understand how you get on google ...
Turn off your vpn and actually scan pfsense WAN IP... Not your vpn endpoint.. Now what do you see open??
How am I supposed to do that?
PfSense is behind a router and has an internal IP. -
So what if you are scanning your vpn public IP... That IP is being used by 100 other clients at the same time... Its NOT yours - its the vpn service... You have zero control over what services they run on it.. They are NOT!!!! sent down your tunnel.. Unless you specifically set that up
You might as well scan www.google.com and be concerned..
So pfsense is behind a nat... Well again HOW AND THE F!!! do you think ports are open on pfsense wan then...
Turn off your vpn, and scan your routers IP.. Now sniff on pfsense do you see any traffic get to pfsense? Did you setup any port forwards on your router? To pfsense wan IP?
-
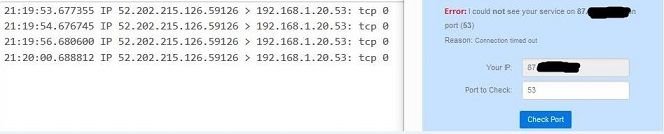
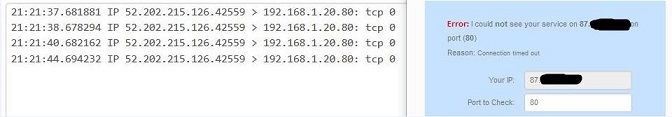
I've forwarded ALL ports from the router to pfSense for the test, here are the results.
Tests were done WITHOUT VPN.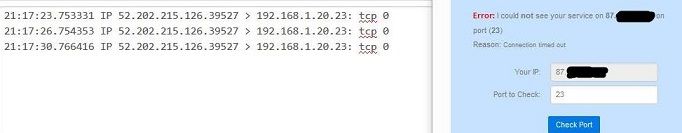
-
And there you go - you see the traffic get there and ZERO answers... So are we done now?
Doing exactly what it should be doing..
-
Does that mean, even if it comes from VPN, it still blocked?
-
OMG dude - what part are you not getting about it is NOT coming down your freaking vpn!!
The vpn is like your router in front of pfsense - pfsense didn't see shit until you forwarded the ports... Have you forwarded them on your vpn? Then they wouldn't be coming down your tunnel to pfsense..
But you can block them all you want on the vpn interface you created that connects to your vpn.
-
I think I got it now, so I actually had what I wanted the whole time.
But why are the Ports displayed as open, if stopped on VPN NAT?
-
Dude they are showing open because your VPN service is running them - NOT that they are being sent down the tunnel to you... This has been like talking to a wall!!
If you enable remote access on your router and have it listen to port 80.. Does it send that 80 to some client behind it..
Your vpn service is just like a nat router.. And the clients using it are like your devices behind your router..
Your not connected to that vpn service now right - well scan that IP you had.. What does it show open - while your not even connected to it.
-
You cannot control what traffic arrives on your outside interfaces. All you can do is block it (not pass it) which is exactly what it happening there.
the pfSense firewall, at its basic level, blocks all traffic into and out of any interface unless otherwise passed.
There are some pass rules placed by default, like passing anything initiated by LAN hosts.
If you do not put pass rules on your WAN, or your OpenVPN/assigned interface tab if that is also a WAN (as in the case of using a VPN provider) then any traffic initiated from the outside into those interfaces will be blocked (not passed - because there are no pass rules).
I provided the answer to your question two days ago:
Derelict 2 days ago
Something in front of your pfSense firewall is likely responding on those. -
Your not connected to that vpn service now right - well scan that IP you had.. What does it show open - while your not even connected to it.
VPN turned off and all ports forwarded to pfSense.
Online scans show no open ports.
Nmap also shows no open ports, although I've run all 65535 TCP and even all UDP.That's a relief, thank you for clarifying.
I provided the answer to your question two days ago:
You're right, it's just that I'm new to pfSense, so I'm not really confident to work with sensitive data, if I don't understand the basics.
-
@Bernd6560 said in How to close Port 23, 53 and 80 on WAN?:
VPN turned off and all ports forwarded to pfSense.
Online scans show no open ports.The pfSense firewall would not be responding even if ports were forwarded to it.
Something UPSTREAM of it was responding. Maybe they turned that off.
-
The pfSense firewall would not be responding even if ports were forwarded to it.
(VPN ON, Portforwarding OFF)
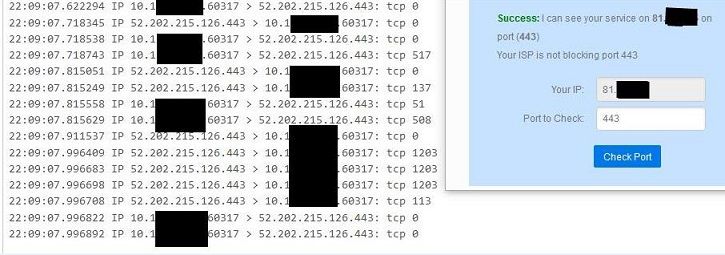
Whats going on here?
-
Those look like outbound connections again. You are showing a test to 81.X.X.X and a packet capture on 52.202.215.126.
I have no idea how you can think those are related.
-
Dude you seem to be just over your head is all... As derelict stated those are outbound.. Your seeing your own connection to the site your using to test
canyouseeme.org [52.202.215.126]
with would be my guess. That port for the 52 address is 443, that is the dest port of your test.. Yeah when you GO to that site you will see traffic to that site on the port you go too, ie https would be 443..
Then you have a 10 address.. Which your hiding? Why??? Its rfc1918 address..