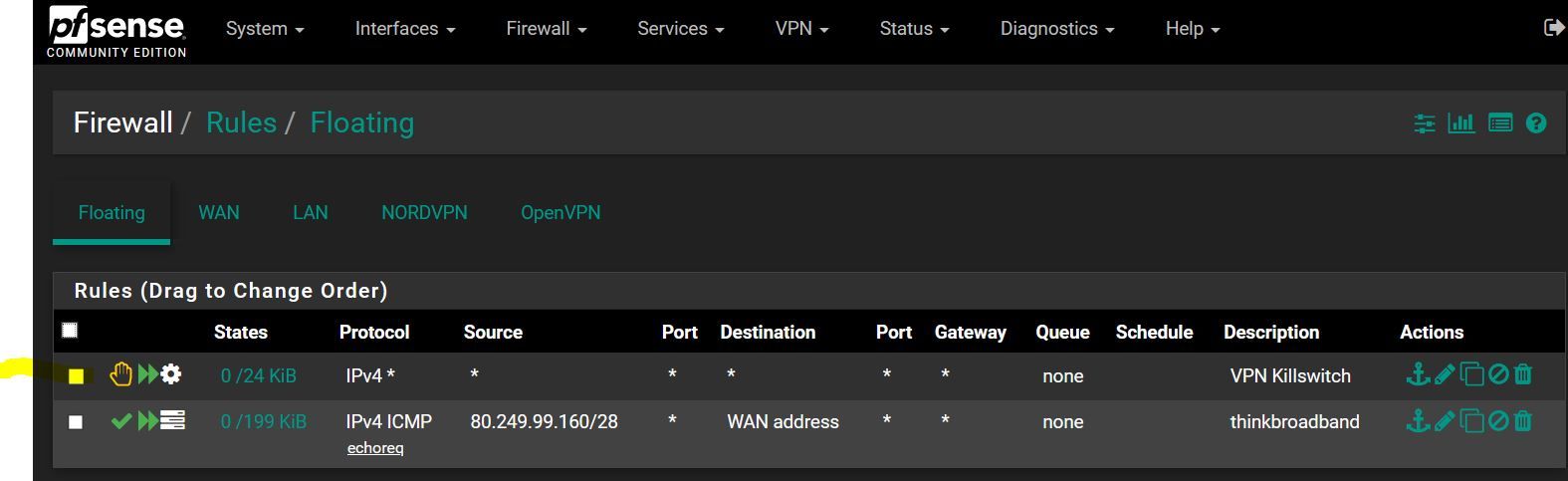
DNS Leak OpenVPN-Client Solution
-
So I did some testing with this site https://www.dnsleaktest.com but it seems kinda hard because sometimes I needed to reboot pfSense to get meaningful results... Anyway, I came up with this, which seems to work for me...
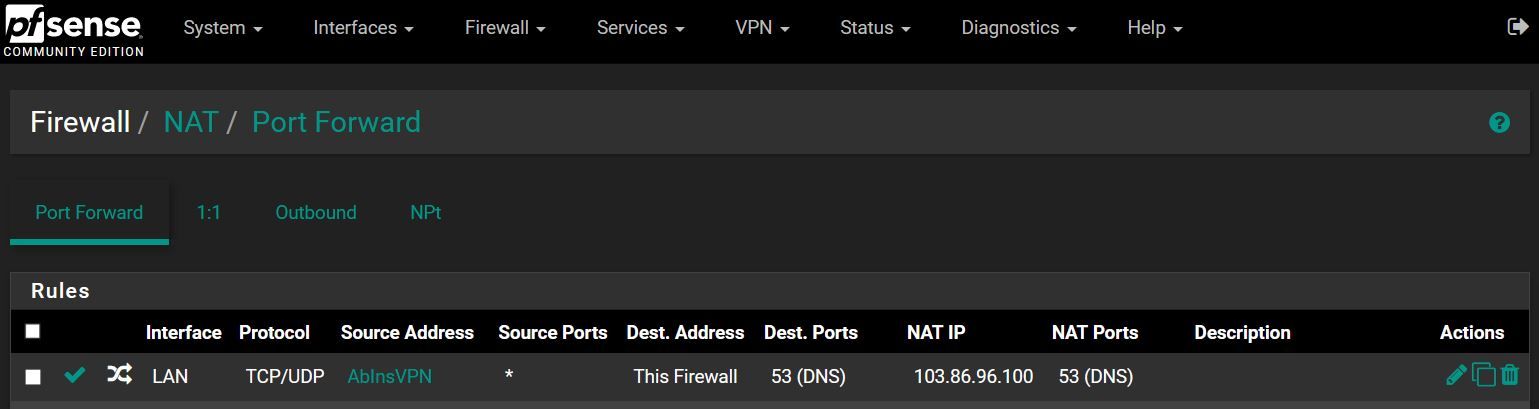
The "NAT-IP" is the DNS-Server of the VPN-Provider.My goal was not to have to define that DNS-server for every client which uses that VPN in the dhcp-Server but leave the default there (pfSense).
So I wish some of the Pros around here could take a look at it and "rate" my solution. Like I said, testing wasn't easy for me.
If it is any good, I want to ask If I could do anything about the following: If that DNS-Server goes offline, where to put the second DNS-Server the VPN-Provider provided...Also interesting was the firewall rule for that. In my testing it made a difference when the first marked rule was at the bottom. So I guess the VPN-redirect-rule in the middle didn't got activated because of the NAT-Redirect by the firewall and then got loose because of the default allow LAN to any rule. So that DNS-rule with that VPN-Gateway had to go to the top.
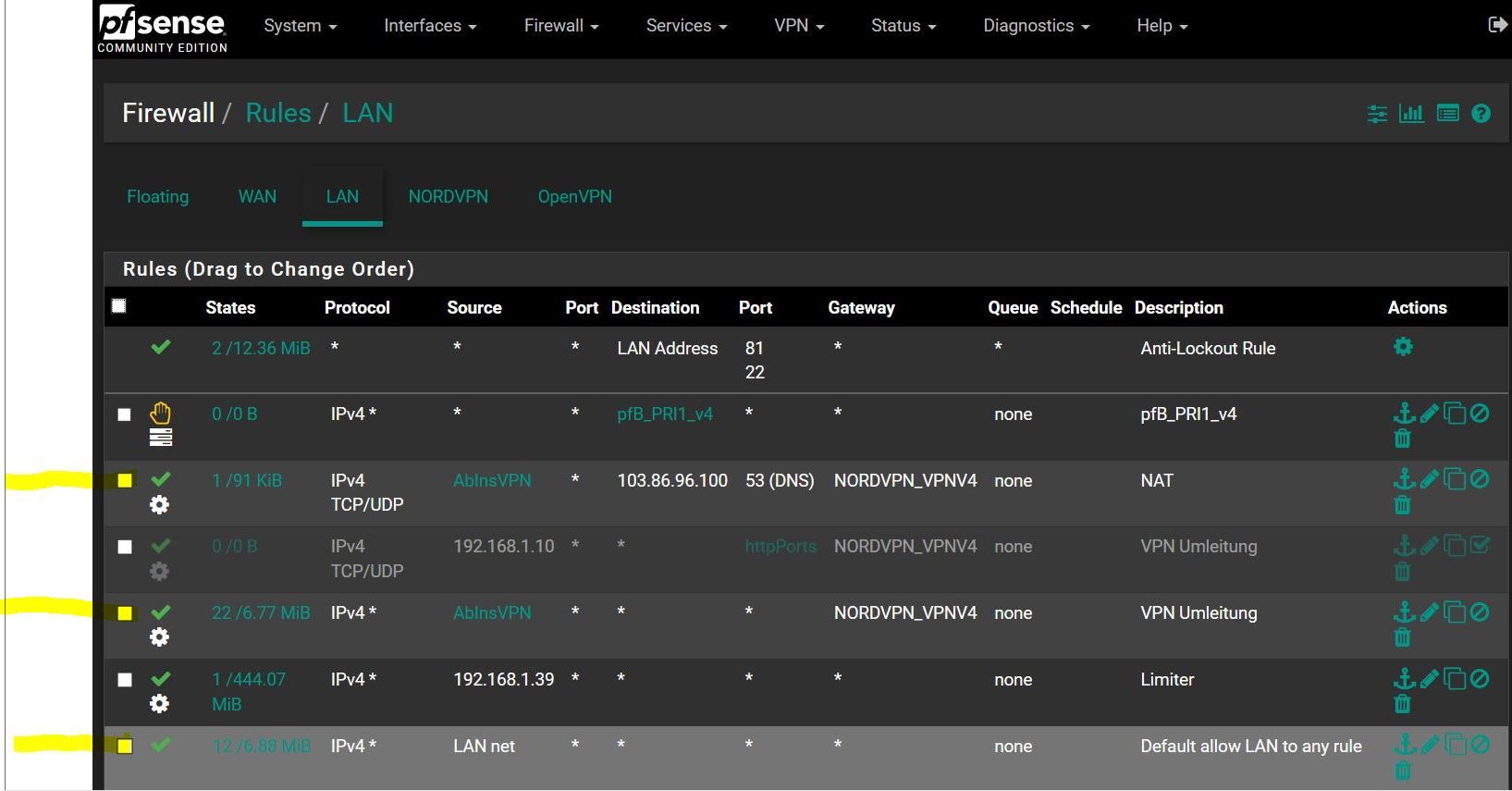
I use the DNS-Resolver without forwarding in pfSense and also have a vpn-killswitch defined as a floating rule via tagging.