Possible bug in firewall logic? Allows traffic out WAN when specified gateway is down...
-
Hi Guys. I'm no expert on this but have managed to get PFSense to do what I want over the last many years. I've encountered a rather simple situation that has left me stumped and is not behaving as one would expect. I probably missed something stupid and need you guys to point it out for me.
The situation:
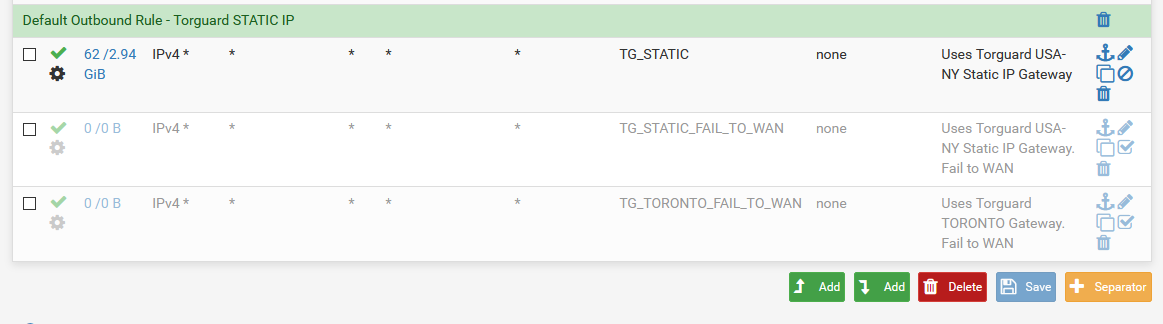
- I have a simple rule on one of my interfaces where traffic is set to go out a particular gateway. This gateway is a VPN tunnel.
- There is no provision for failover to another gateway. If this gateway is down, traffic should stop and give no connection.
- If the gateway is genuinely down (route/gateway enabled and openvpn client enabled), the traffic stops as expected.
- If I manually disable the OPENVPN instance (while leaving it in the list), the traffic immediately flows out the WAN! WHY!?
- If I log the traffic on this rule, it says that this line is letting it through.
How can I prevent this behaviour? My expectation is that no matter how the gateway is disabled that traffic should stop if that gateway is not available. I have other rules elsewhere where I want the same outcome but the behaviour is same there also.
Is this a bug or have I missed something? If I add a rule blocking traffic through the WAN after this line, the traffic still goes out the WAN based on the pass rule for the VPN gateway.
Much appreciated.
-
@osheikh
Hello
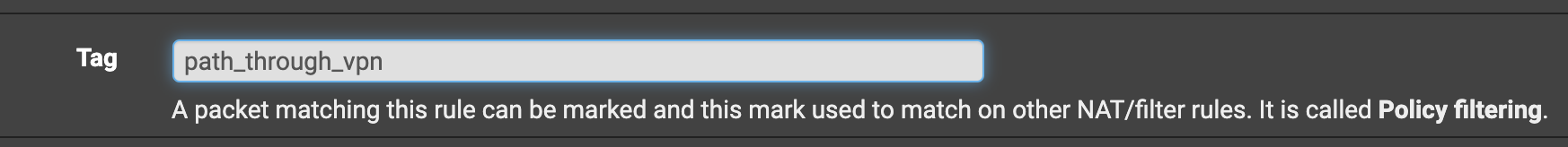
To avoid traffic leakage through the WAN interface it is necessary to use tags
On the lan interface you create a rule with a tag and you specify the interface through which the traffic should pass
For example,
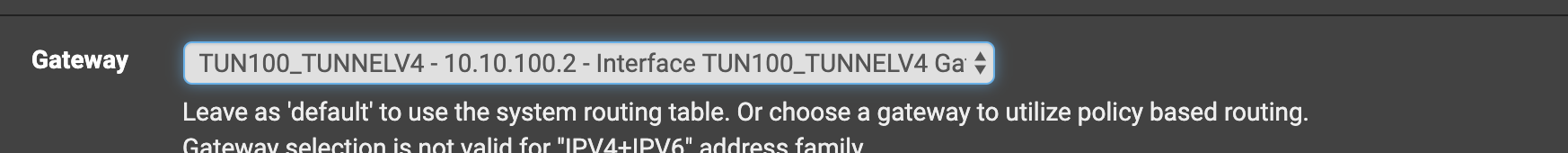
Now you need to create a blocking rule for outgoing traffic on the wan interface (section-floating rules)
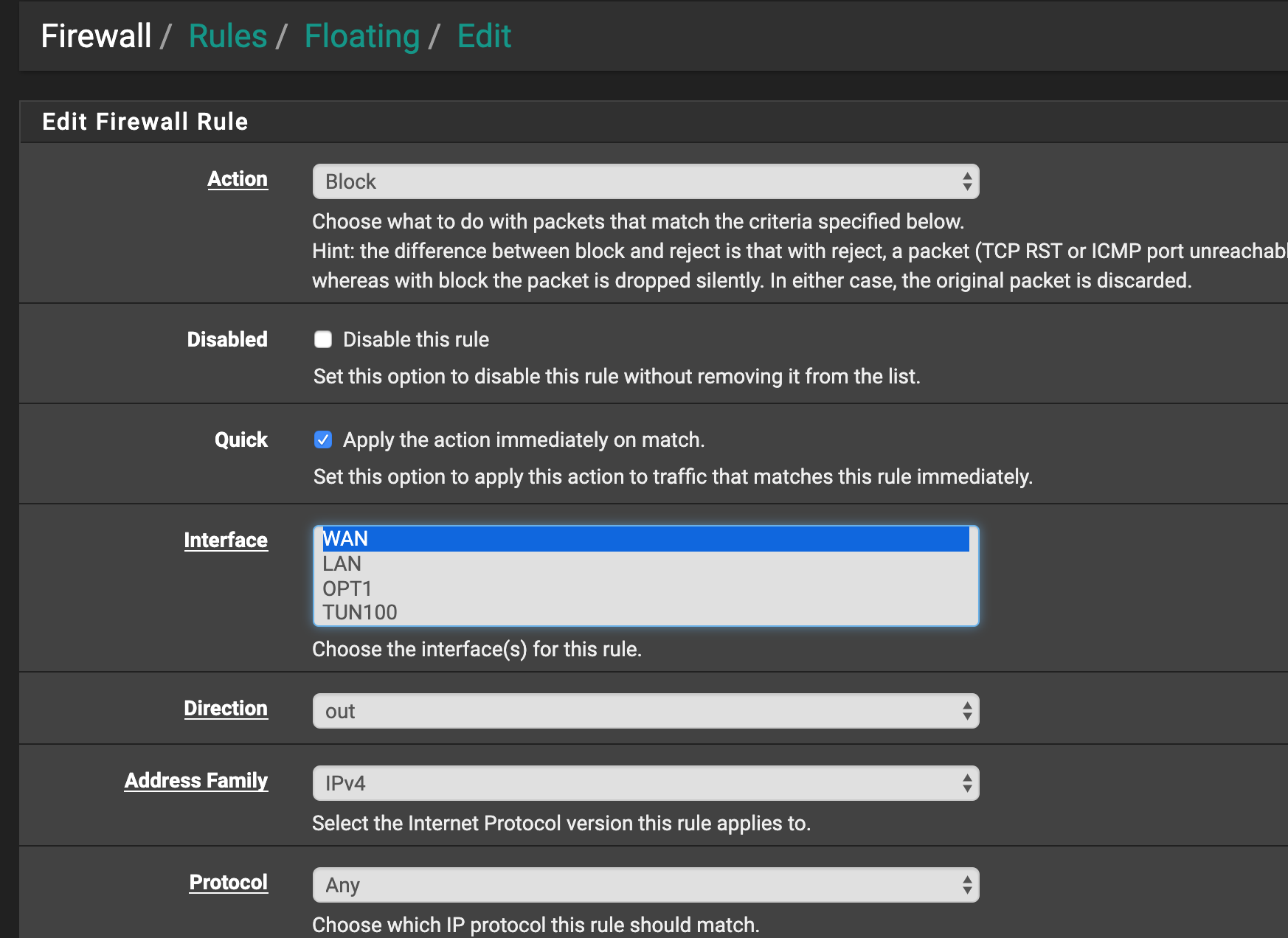
And now check the availability of tag in this same rule
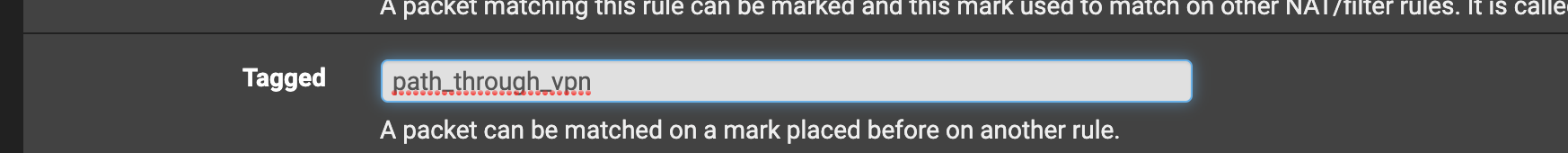
now all all traffic destined for VPN will not pass through WAN interface
-
Thank you!! This did exactly what I needed. I would have never figured this one out on my own. Tags really do open up the possibilities of what rules can be made to do.
Much appreciated.
-
What you really probably want is even easier:
System > Advanced, Miscellaneous tab: Skip rules when gateway is down
If that is unchecked (default) then when a gateway is down, the rule stays in place but without the gateway set. If that is checked, the rule is skipped (omitted from the ruleset) so it moves to the next available rule.
-
Thanks Jimp. Indeed this also does the job but there seems to be a place for both solutions depending on the situation. Much appreciated!