Please Enable TLSv1.3 On pfSense 2.5.0
-
Dear Developers/ Administrators,
Hello and I hope that you are doing well. I have not written you in a while and in the interim I have been enjoying your excellent pfSense 2.5.0 RC. Now - I have a question / request for you. I run Stubby ( DNS OVER TLS ) along with Unbound. pfSense 2.5.0 has OpenSSL 1.1.1 and since OpenSSL 1.1.1 there is included support for TLSv1.3 - with that being said - Is it possible to configure pfSense 2.5.0 so that TLSv1.3 is enabled in the kernel or whatever needs to be done to put TLSv1.3 in effect. See here : https://www.openssl.org/blog/blog/2017/05/04/tlsv1.3/ 1 and here : https://wiki.openssl.org/index.php/TLS1.3 - no rush or pressure - it is just that I am trying to be as safe and secure as possible.
Stubby supports TLSv1.3 as do many of the DNS PRIVACY SERVERS.The most salient point from these articles is this point of reference
" In order to compile OpenSSL with TLSv1.3 support
you must use the “enable-tls1_3” option to “config” or “Configure”Anyway - thanks for all you do for all of us in what I fondly refer to as " The Community "
Peace and I am OUT ! -
TLS 1.3 is already enabled, and used by nginx to run the WebGUI and Captive Portal: https://redmine.pfsense.org/issues/9607
Do you see something specifically that is not using TLS 1.3 which you think should be using it?
-
@jimp Thanks for your swift reply - no I have not tested TLSv1.3 yet - I made an assumption that it was not active. Please forgive me for that. The command which I am looking to run centers around determining TLSv1.3 when connecting to DNS OVER TLS Servers - see below fromhttps://blahdns.com/ :
TLS1.3 support check openssl s_client -connect 108.61.201.119:853 The return message should be : New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384 Server public key is 2048 bit Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated Early data was not sent Verify return code: 0 (ok) --- --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_256_GCM_SHA384Thanks - I will test this later when I fire up my pfSense 2.5.0 Box
-
@ubernupe said in Please Enable TLSv1.3 On pfSense 2.5.0:
openssl s_client -connect 108.61.201.119:853
Well that commands a bit off, you don't need the -connect, but guess you could use it.
Yeah comes back with 1.3
[2.5.0-DEVELOPMENT][admin@pfSense.localdomain]/root: openssl s_client 108.61.201.119:853 CONNECTED(00000003) depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3 verify return:1 depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 verify return:1 depth=0 CN = dot-jp.blahdns.com verify return:1 --- Certificate chain 0 s:CN = dot-jp.blahdns.com i:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 1 s:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 i:O = Digital Signature Trust Co., CN = DST Root CA X3 --- Server certificate -----BEGIN CERTIFICATE----- MIIFcTCCBFmgAwIBAgISBHeZ4Ga5WxtwnBYu7hPy/XvAMA0GCSqGSIb3DQEBCwUA MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0xOTEwMzExMjE1MDRaFw0y MDAxMjkxMjE1MDRaMB0xGzAZBgNVBAMTEmRvdC1qcC5ibGFoZG5zLmNvbTCCASIw DQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMMnlE6AoKSdgywHVcXP/gWssVg6 sb6XQyEpNwkv7n8S0hP2I9QS7x6JotFJ3Ne8IycXa6elthsRmK6ou5AEHrYYJvsz 8slHGONWLOLHYH1yJje4aJtznbsHFl14MV4pXhwbMR1xr0aVCbR7QTAq/RMPPlxe 5LKbRnM8t0h+NDOsm6wNbZyLKXLXSuIo1xi6TMiccoESEWCLgZsCLH4GEslGe57X kj5Uh5eUFEO9OhNbZ7ZnhtQtw2lVWKhfcJ5TQz6A7yuf8u4ctuhRiHJQGFUuDhL/ /wHe+lbmJ+pw20Bay1OSy0wffIiNDBC552JYtKAoZNLJTx6cxIPoENhfPusCAwEA AaOCAnwwggJ4MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYI KwYBBQUHAwIwDAYDVR0TAQH/BAIwADAdBgNVHQ4EFgQU5/svwCYZojj/+xsClZe/ DabxzD4wHwYDVR0jBBgwFoAUqEpqYwR93brm0Tm3pkVl7/Oo7KEwbwYIKwYBBQUH AQEEYzBhMC4GCCsGAQUFBzABhiJodHRwOi8vb2NzcC5pbnQteDMubGV0c2VuY3J5 cHQub3JnMC8GCCsGAQUFBzAChiNodHRwOi8vY2VydC5pbnQteDMubGV0c2VuY3J5 cHQub3JnLzAxBgNVHREEKjAoghJkb2gtanAuYmxhaGRucy5jb22CEmRvdC1qcC5i bGFoZG5zLmNvbTBMBgNVHSAERTBDMAgGBmeBDAECATA3BgsrBgEEAYLfEwEBATAo MCYGCCsGAQUFBwIBFhpodHRwOi8vY3BzLmxldHNlbmNyeXB0Lm9yZzCCAQUGCisG AQQB1nkCBAIEgfYEgfMA8QB2ALIeBcyLos2KIE6HZvkruYolIGdr2vpw57JJUy3v i5BeAAABbiH0i9cAAAQDAEcwRQIhAKIUGZL14iLIjUvzdhaLtgIx8Vg5k1EaPlsb K8PPrT+UAiBdARoq3M/R/zWmQ/0w+9cpsIg5qcL6Xai38ubxG8T/jwB3AG9Tdqwx 8DEZ2JkApFEV/3cVHBHZAsEAKQaNsgiaN9kTAAABbiH0jAkAAAQDAEgwRgIhANPI x0dDHQd7Lxavxi47nY0tGkKwm11RU47nJncJoyeRAiEAzV2zYmjcnEkHf7gg0QJv 6nROQEKZdkFu8ayR13FIMuAwDQYJKoZIhvcNAQELBQADggEBAHfl4Wh1c6tA5qHA XAntT66XqtcbD4IxgbA2tA6NkhE0zlxwwWPoIftRTnbrWcqMUd9SCpgPpeKr6rZC mAh3HvBJSDg7tHaGuHaCdYQ5iNPtzo75yxxCFrHyX3p65p0JfJ1+x5q/h3IVZeZR IFJP45HKt6ZeR+3pfSBNFNe3KeuAkK8arLld0EW2RXvIPzAP4fInh4KGyhrH8UCV zxz0c+620QSHsLLbsenNU8K0IVHIKI3MVYKjorkKn7eIOMr0koirI750qOyI9OsS 39KMVJsft+08w3Uk7+lY7xo/bUTgOPNE5TalKxCDQMZWAMVK3j1XMSWI1leCRCxh DdXNW0o= -----END CERTIFICATE----- subject=CN = dot-jp.blahdns.com issuer=C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 --- No client certificate CA names sent Peer signing digest: SHA256 Peer signature type: RSA-PSS Server Temp Key: X25519, 253 bits --- SSL handshake has read 3120 bytes and written 382 bytes Verification: OK --- New, TLSv1.3, Cipher is TLS_AES_128_GCM_SHA256 Server public key is 2048 bit Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated Early data was not sent Verify return code: 0 (ok) --- --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_128_GCM_SHA256 Session-ID: 0E50089A38D36D776715A92F1B51812F706999C5408E6341E13768D7FABFD52D Session-ID-ctx: Resumption PSK: 8163EEAA5065913DFAB9579AB9CDE40AE2AD074A1428C7EBB78778950E0F35FB PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 600 (seconds) TLS session ticket: 0000 - 85 81 17 34 e9 38 d3 da-da 41 80 43 71 f4 9e 95 ...4.8...A.Cq... 0010 - be 4b 77 7c 11 cb 04 63-f3 51 b2 97 9e bf e9 74 .Kw|...c.Q.....t Start Time: 1573693619 Timeout : 7200 (sec) Verify return code: 0 (ok) Extended master secret: no Max Early Data: 0 --- read R BLOCK --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_128_GCM_SHA256 Session-ID: 0BA860A298E78932AF04192DD119A5EE0B72710E441E5812EBA7F45D9AFB00F2 Session-ID-ctx: Resumption PSK: A17984B7AED7769102A653EB72123395B49FF4C99CFD4617A7BA58B1BFA694AA PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 600 (seconds) TLS session ticket: 0000 - 69 c3 3f 31 eb 27 bf 60-4b fe 2b 06 e0 0c 7c 93 i.?1.'.`K.+...|. 0010 - 2d a0 7f 0e 8c dc a3 09-66 ad 42 01 b5 4f 65 76 -.......f.B..Oev Start Time: 1573693619 Timeout : 7200 (sec) Verify return code: 0 (ok) Extended master secret: no Max Early Data: 0 --- read R BLOCK closed [2.5.0-DEVELOPMENT][admin@pfSense.localdomain]/root:And just for validation - yeah the gui defaults to 1.3
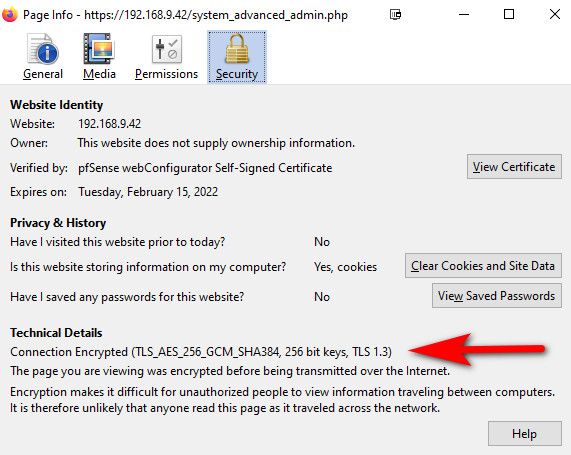
-
@johnpoz
Dear johnpoz,
Hello and I hope that you are well. I am reporting back by way of feedback. My results mirror yours exactly. So, I am very pleased to thank you and the pfSense team for ensuring that the most up to date secure protocols are used and deployed. Once again, I appreciate your time and effort in responding to my inquiry. Lastly, thanks for informing me as to the correct command to run when checking connection to TLSv1.3 Server.
Peace and God Bless Always -
FYI- After trying a few tools and finding that the common ones I'm used to (
sslscanandnmap --script ssl-enum-ciphers) do not support TLS v1.3, I happened across one that does and has a nice set of tests: testssl.shAmong its other (very verbose) output:
Testing server preferences Has server cipher order? yes (OK) Negotiated protocol TLSv1.3 Negotiated cipher TLS_AES_256_GCM_SHA384, 253 bit ECDH (X25519) Cipher order TLSv1.2: ECDHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES256-SHA384 ECDHE-RSA-AES256-SHA DHE-RSA-AES256-CCM8 DHE-RSA-AES256-CCM DHE-RSA-AES256-SHA256 DHE-RSA-AES256-SHA TLSv1.3: TLS_AES_256_GCM_SHA384 TLS_CHACHA20_POLY1305_SHA256 TLS_AES_128_GCM_SHA256