Router behind Pfsense VLAN Setup
-
Hi all,
I have Pfsense with 3 VLANs. VLAN 1 is using 192.168.1.0, VLAN 2 is using 10.0.0.0 and VLAN 3 is using 192.168.3.0.
VLAN 2 is where I have some question. The department have all servers and pc setup for 192.168.1.0. In order to preserve that and since VLAN 1 is already using 192.168.1.0, I added a router. Router WAN port going to VLAN 2 port. VLAN 2 Interface IP 10.0.0.1, Router WAN IP 10.0.0.2. I have pc in the range from 192.168.1.10 to 192.168.1.30 on Router LAN.
How do I allow external ssh login through pfsense WAN all the way through VLAN 2 to router LAN ip?
Or is there a better setup? I saw some google results showing downstream gateway setup but I have no idea what that will do.
I am stumped...
Thanks for all your help in advance!
-
@sho1sho1sho1 said in Router behind Pfsense VLAN Setup:
How do I allow external ssh login through pfsense WAN all the way through VLAN 2 to router LAN ip?
Unless I've misread your description, that sounds like you are trying to go from one side of that router to the other. If so, it has nothing to do with pfSense, as you're just passing through that router. Also, I hope you realize that you will not be able to connect between VLAN1 and that router LAN, as they both are on the same subnet.
I'd say change the subnet for VLAN1 or the router LAN, so that the subnets don't conflict. You'll then be able to get rid of the router can put those computers directly on VLAN2.
-
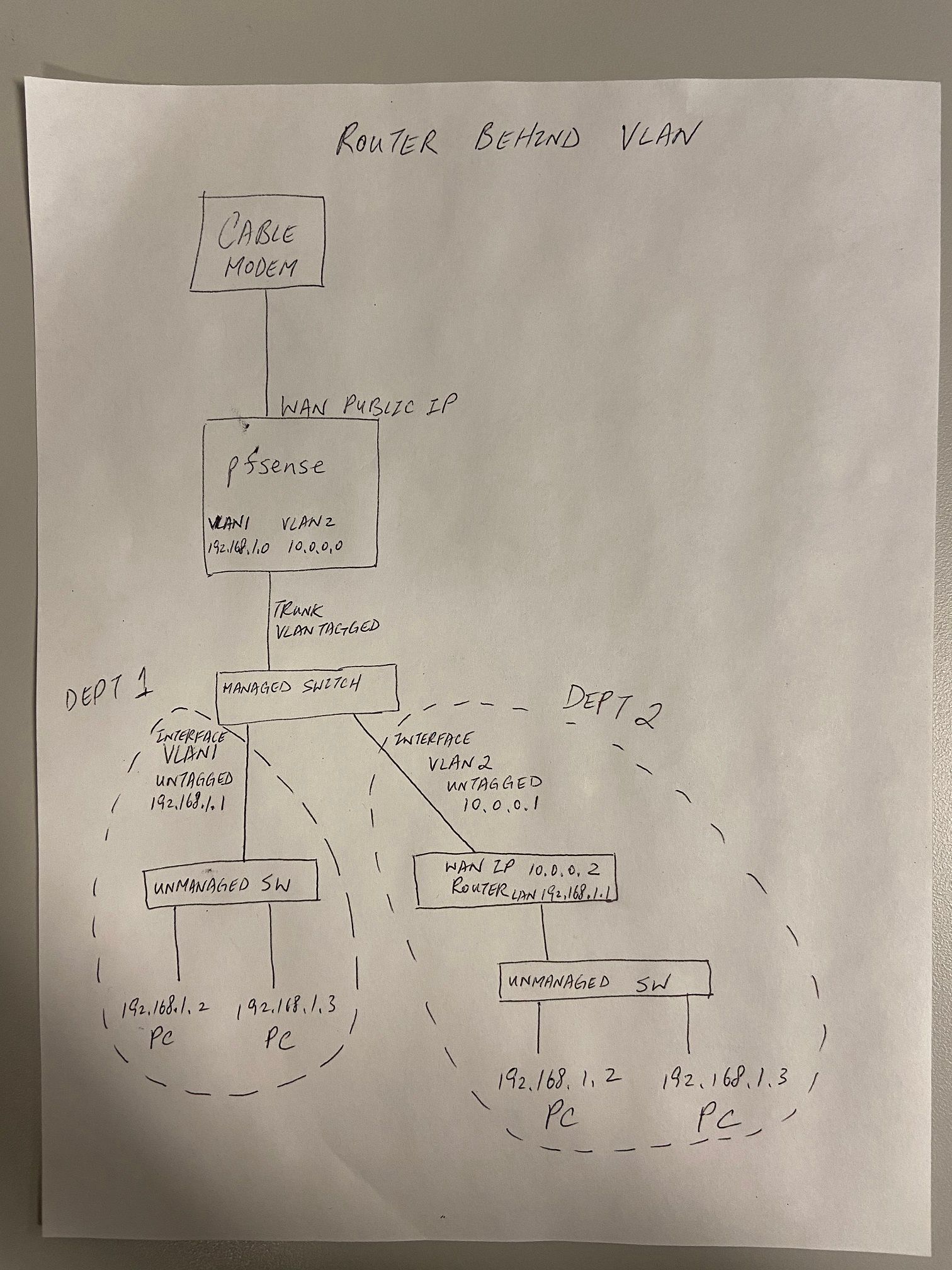
Hi,
I drew a network diagram clarify what my setup is. With the diagram in mind, I am trying to allow an employee to ssh Cable Modem WAN public with port 12000 (for example: ssh 169.0.1.xxx -p 12000) and this would port forward to VLAN 2 PC 192.168.1.2 port 22.
I have a port forward rule in place for Router behind VLAN 2, which forwards 10.0.0.2 port 12000 to 192.168.1.2 port 22.
I am having trouble with the rule to forward 169.0.1.xxx port 12000 to Router behind VLAN2 10.0.0.2 port 12000.
I hope this clarifies by question!
I am aware that changing the subnet for VLAN1 or changing the subnet for LAN behind VLAN2 router would be an easy fix... But the infrastructure is already there and it would be really hard to get the sysadmin to change their ip subnet since there are a lot of static assignment. VLAN1 does not need to ever communicate with LAN behind the VLAN2 router if that makes it easier...
I am open to any suggestions...
-
@sho1sho1sho1 said in Router behind Pfsense VLAN Setup:
I hope this clarifies by question!
I see it's as I mentioned, with the router between 10.0.0.0 and 192.168.1.0 and again, as I mentioned, pfSense is not part of that. It's strictly getting through that router you're worried about.
BTW, where is 169.0.1.0 on your diagram? I don't see it anywhere.
-
@JKnott 169.0.1.xxx is the WAN Public IP on pfsense.
-
You'd have to configure port forwarding from the WAN to the router and then again through the router. You can use Packet Capture to see what's happening, between pfSense and the router, when you try to connect.
-
Under Firewall/NAT/Port Forward, I added the following rule:
Interface Protocol Source address Source Ports Dest. Address Dest. Ports NAT IP NAT Ports Description
WAN TCP/UDP * * WAN address 13000-13010 10.0.0.2 13000-13010 Access to PCIt seems like it's working. Is there any security concern? Are only ports 13000 to 13010 forwarded? Is there any concern that hackers can get to the other VLAN?
On the router behind pfsense, I have port forward port 13000 to port 22 for ssh to one PC.
-
Only the ports you open are exposed. However, why are you using those ports. Ssh is port 22.