Best practice to block traffic between local interfaces
-
Hi,
we have a Fortigate Firewall we will be replacing with pfSense 2.4.4.
The system will have plenty of local networks seperated via VLAN tagging.
Some of those local interfaces shall get access to the Internet, too.
By placing a rule that allows traffic to the Internet, traffic to all the other local nets is also permitted, right?We do not only use IPv4 but also IPv6 so every local net has RFC1918 addresses but also a public IPv6 prefix.
What is the best practice for firewall rules for interfaces that need access to the Internet but shall not route between the local nets? I don't want rules like that, because that would mean too much work
netA -> netB block
netA -> netC block
netA -> netD block
etc.
<--->
netB -> netA block
netB -> netC block
netB-> netD block
etc.
<--->
etc.
Wouldn't it be much easier if the default rule that allows access to the Internet would contain a definition about an outgoing interface? In this scenario one would not have to define any extra rule to block traffic between local interfaces. -
@pmisch
No not everyone wants to block inter subnet traffic.
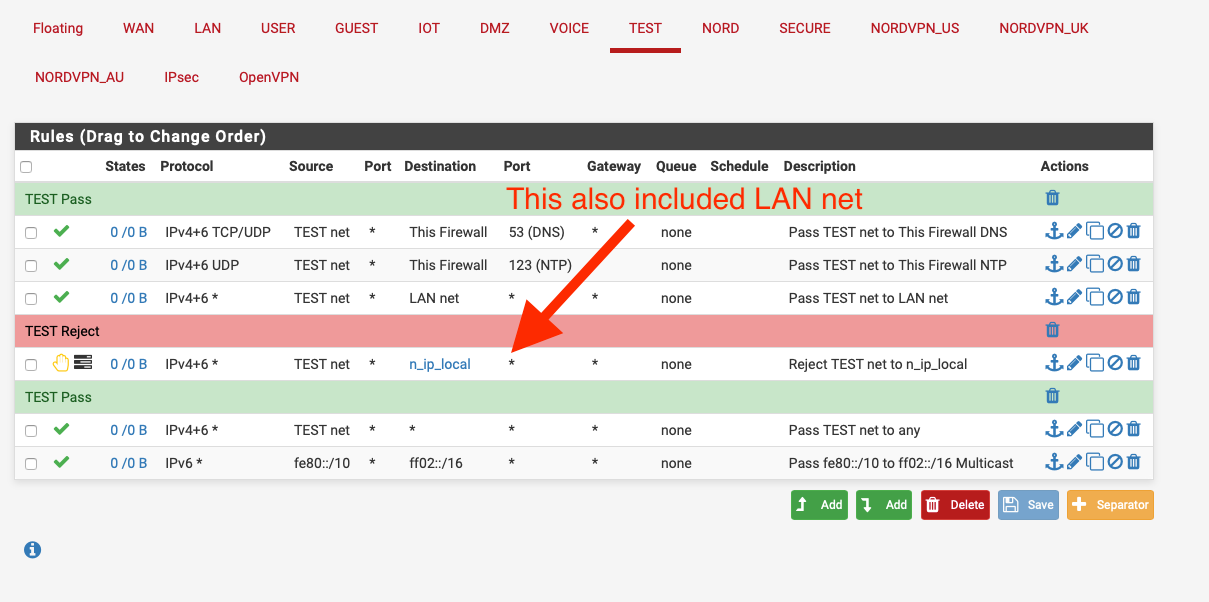
Create an alias with all your IPv6 subnets in and also add the rfc1918 subnets.
Use the alias in a rule to block LAN net to the alias.
Then create a rule under the above rule to pass LAN net to any.
If you want any specific subnet to another subnet create a pass rule above the block rule.
If you had a bunch of interfaces that were internet only you could create an interface group, but check out how the user rule processing works.
-
@NogBadTheBad said in Best practice to block traffic between local interfaces:
@pmisch
No not everyone wants to block inter subnet traffic.You could make it optional to choose an outgoing interface. I'm just a bit confused that it's not even possible for a rule to select an outgoing interface. Is there a reason for that?
Create an alias with all your IPv6 subnets in and also add the rfc1918 subnets.
Use the alias in a rule to block LAN net to the alias.
Then create a rule under the above rule to pass LAN net to any.
If you want any specific subnet to another subnet create a pass rule above the block rule.Thank you. That's what I will do.
-
Something like this:-