Block outgoing connections ?
-
Another image :
My LAN IP :
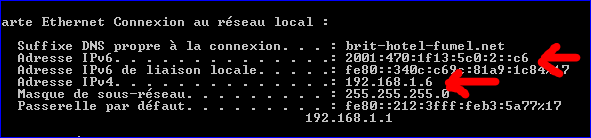
My IP has two IP's : an IPv4 and IPv6.
I'll block them on the LAN firewall page :
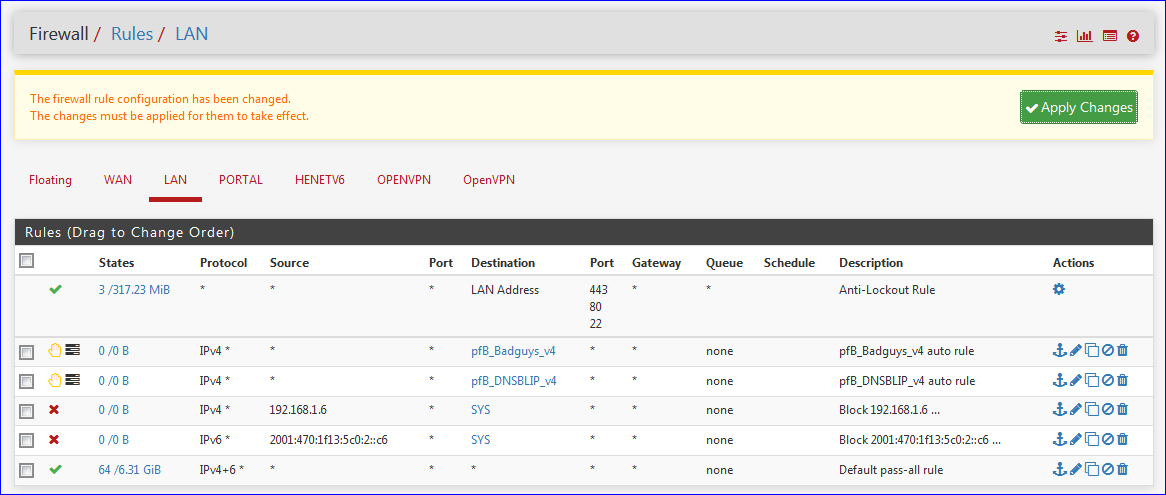
Nothing special on this tab, just de classic anti lockout rule, two pfBlockerNG rules my two "test block rules" and a final pass all rule.
When I hit the green button (Apply Change) my PC can still access the pfSense GUI ...... because states are still up.
So, I reset states :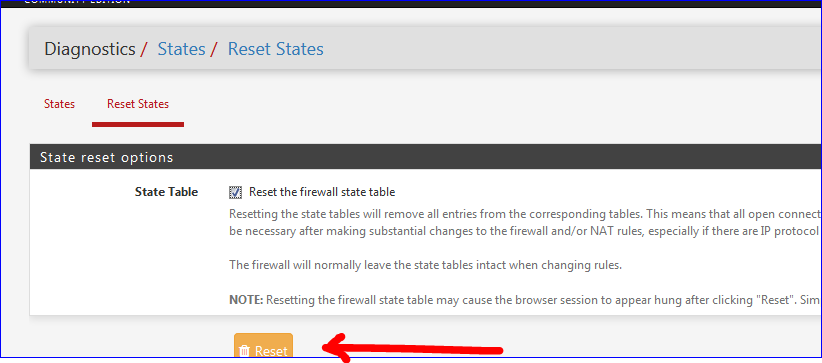
After that, the browser hangs .... My PC has no IPv4 / IPv6 so everything came to a halt (note ICMP still passes ^^).
I block all connections going into the LAN interface.
Local LAN traffic is still possible of cours, that traffic isn't seen by pfSense. -
Yes, but what exactly has this to do with my rule, i've created ?
From the docs:
"Floating rules are not limited to the inbound direction like interface rules"The rule is created on the LAN interface with any as the destination ? So because the traffic comes back, it "automatically" becomes an inbound rule ?
-
" you have for sure misunderstood something"
you never use floating rules if not in a realy not common scenario
"only for ingoing connections, and not outgoing" where did you read this?
rules for LAN interface go on the LAN tab and they are needed for outgoing traffic for sure -
This post is deleted! -
@kiokoman
Yes, its highly likely :)E.g. here:
https://docs.netgate.com/pfsense/en/latest/book/firewall/floating-rules.html#direction
It states "Floating rules are not limited to the inbound direction like interface rules. "And here:
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.html
"Firewall rules on Interface and Group tabs process traffic in the Inbound direction and are processed from the top down," -
Both statements are right. Nevertheless you only use floating rules if you absolutely need them. Otherwise it's simply not necessary to filter the traffic going out one interface if you just filtered it before it got IN on the other side. That's why pfSense Docs states that it filters inbound on all interfaces.
So what's your point or what are you missing to understand how to create rules? I still don't get your OP?
-
ok first, forget about floating rules, never use it
inbound = traffic generated by your clients are entering the LAN interface and going out from LAN to internet -
@kiokoman said in Block outgoing connections ?:
ok first, forget about floating rules, never use it
inbound = traffic generated by your clients are entering the LAN interface and going out from LAN to internetAaaaah, yes. That explanation, for the stupid people, like me, makes sense. Thank you!

I was thinking it like this..
 , which are obviously wrong..
, which are obviously wrong..
inbound -> to LAN network
outbound -> from LAN network to X .... -
@lbm_ said in Block outgoing connections ?:
outbound -> from LAN network to X ....

Now review my post above, and try t block yourself ....
You'll see, it works.
( have another PC (IP) ready to unblock ) -
@Gertjan said in Block outgoing connections ?:
@lbm_ said in Block outgoing connections ?:
outbound -> from LAN network to X ....

Now review my post above, and try t block yourself ....
You'll see, it works.
( have another PC (IP) ready to unblock )Yes, thats easy, and got it working, and that was the part which I do not really understood why i really did work, because I was not understanding the terms af "inbound" correctly.
-
It's a bit tricky at first but just think about the pfSense Box as some sort of blackbox with lines going into it. WAN being one, LAN being another. Filtering is done "inbound" so whereever a packet "touches" the blackbox first, that's where you should filter it (pass/block etc.) :)