Firewall directions
-
@kiokoman said in Firewall directions:
if you configure openvpn on the firewall you will find yourself with a new OpenVPN tab
where you will enter the rules following the same principleI've been using multiple OpenVPN servers for months now and never added any rule to their tabs, but I was connected through the LAN which has the default allow LAN to any rule. With the other Interfaces/VLANs, wouldn't I need to add rules under their tab only? Why to even touch the OpenVPN tab?
-
did you configure the openvpn on pfsense or under some pc/server you have on your lan ?
-
I configured an OpenVPN client on pfSense. In this case NordVPN.
I think I'll just create the rules I want and post a screenshot here. Then we'll proceed.
Thanks man,
-
then a client is not a server
as we said before you are able to enter that interface because the default rule for LAN interface is to allow all
the OpenVPN tab for you is like another WAN
openvpn is another monster that have different implementation -
Yeah...My bad. When I wrote VPN "Servers" I meant my OpenVPN clients, which in turn connect to an actual VPN server haha.
@kiokoman said in Firewall directions:
you are able to enter that interface because the default rule for LAN interface is to allow all
And what about allowing all the VLANs to use the OpenVPN client as well? Their RFC1918/IPv4* blocking rule won't affect it? The local virtual addressed of these VPNs are 10.x.x.x which fall under RFC1918......I thought I understand pfSense and firewall and everything is actually working, but the deeper I dig I get a headache LOL...
-
of course, if you want another interface to be able to use the vpn interface you need to create a rule that permit that.
RFC1918/IPv4* blocking rule inside an interface like OPT1/OPT2 etc will prevent it but you just need a previus rule like
"permit OPT1 net destinatio OpenVPN" before "block OPT1 net destination RFC1918". first rule win ! -
@kiokoman That's what I thought. Thanks a bunch!
-
@JeGr said in Firewall directions:
allow DNS/NTP from opt1_net
It's either or? Or should I allow both of them UDP/53, UDP/123?
-
i think it was just an example,
port 53 is for DNS (domain name system) pretty much mandatory if you want to resolv dns and surf the web
port 123 is for NTP (Network time protocol) useful but not mandatory, it's needed to sync the clock
that said the minimum port to be able to surf the web are udp/tcp 53 for dns tcp 80 for http and tcp 443 for https -
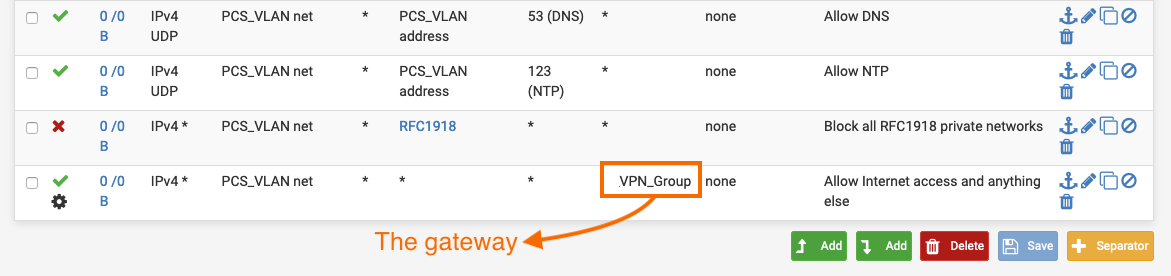
What about the VPN Group shown in the screenshot? I think that adding "Allow PCS_VLAN to OpenVPN(1194)" won't be enough, since the VPN clients' gateways are in the range of RFC1918 - 10.x.x.x.
What rule(s) exactly should I add in order for this VLAN to be: isolated from other interfaces, have internet access and connect to the internet via the VPN_Group (NO_WAN_EGRESS)?
-
that rule probably won't work,
you just need to put it before the block -
@kiokoman said in Firewall directions:
you just need to put it before the block
Put what rule? I'm already confused here man...you'd have to be more specific. Sorry :)
-
bs
-
@kiokoman I thought that's what you meant but wouldn't that make the blocking rule useless, since we allow everything else here? See @JeGr answer above. Or perhaps that's not the case because it's setup to use the VPN gateway instead of the default one?
The more I ask, the more I get confused which has never happened to me before in my life LOL...gotta read the pfSense book a little, when having the chance haha...
-
after 9 hours of work you should understand that my brain is telling me bs now

you are right i make a mistake, i was not seeing the tab and i was confusedbut you probably need a new rule that permit traffic from PCS_VLAN net with destinaton OpenVPN net before the block
but right now, i confess i'm tired, maybe try and tell us if it work or not -
This post is deleted!