OpenVPN Server Gateway Redirect
-
@manjotsc said in OpenVPN Server Gateway Redirect:
Can you access remote devices? some yes some no
These one you can't maybe block access themselves by the OS firewalls.
What's your server config? Possibly it overrides the client settings.
Some clues in the client log? Probably it doesn't set the default route correctly.What is the client? A phone, Windows, Linux?
-
@viragomann The config https://drive.google.com/file/d/1DYdh8ikZ2x9JFrvlfViJlUBMwmvxxKJD/preview
I tried on Android Device using openvpn app.
-
So remove the "IPv4 Local Networks" and check "redirect gateway" in the server settings.
Consider that you also have to add a outbound NAT rule for the OpenVPN tunnel network for internet access from VPN clients.
-
@viragomann What that rule would be?
-
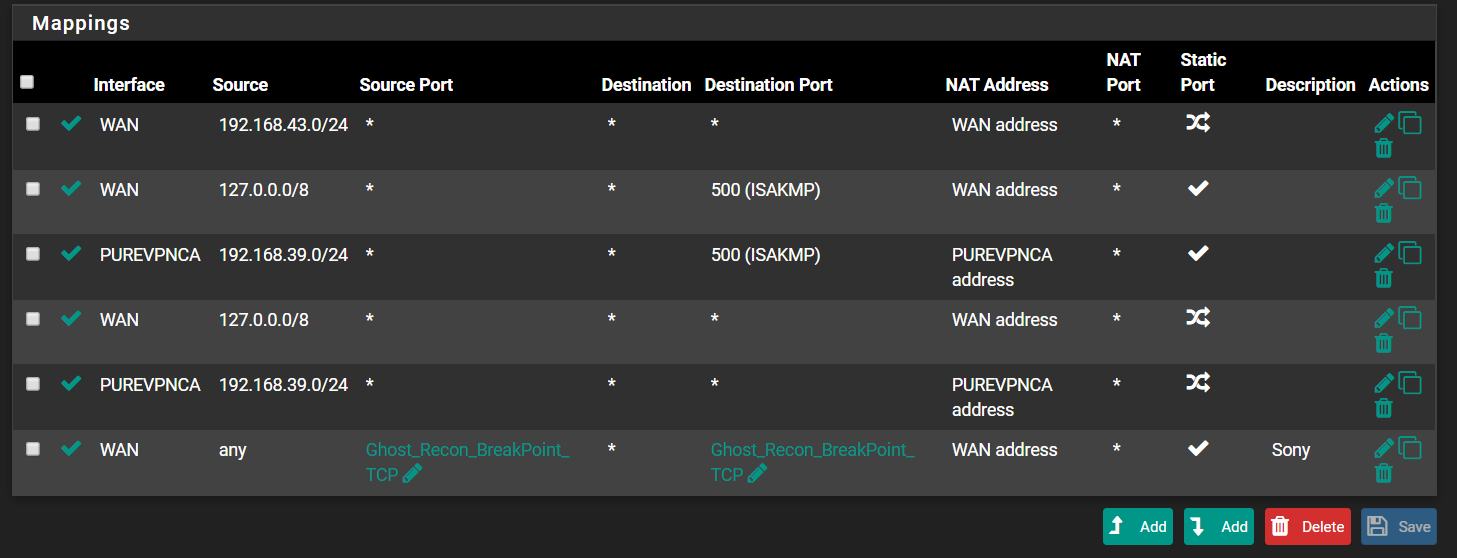
When packets from private sources are sent out to the internet, the router has to translate the source addresses into its WAN address.
pfSense does this automatically for internal subnets, but not for OpenVPN clients.To configure this, go to Firewall > NAT > Outbound
Assuming it is still working in automatic mode, switch to hybrid mode and save it at first.
Then add a new rule:
interface: WAN
source: <OpenVPN tunnel network>
destination: any
translation: interface address -
@viragomann Now I when connected can't visit any website
-
Try to reboot pfSense.
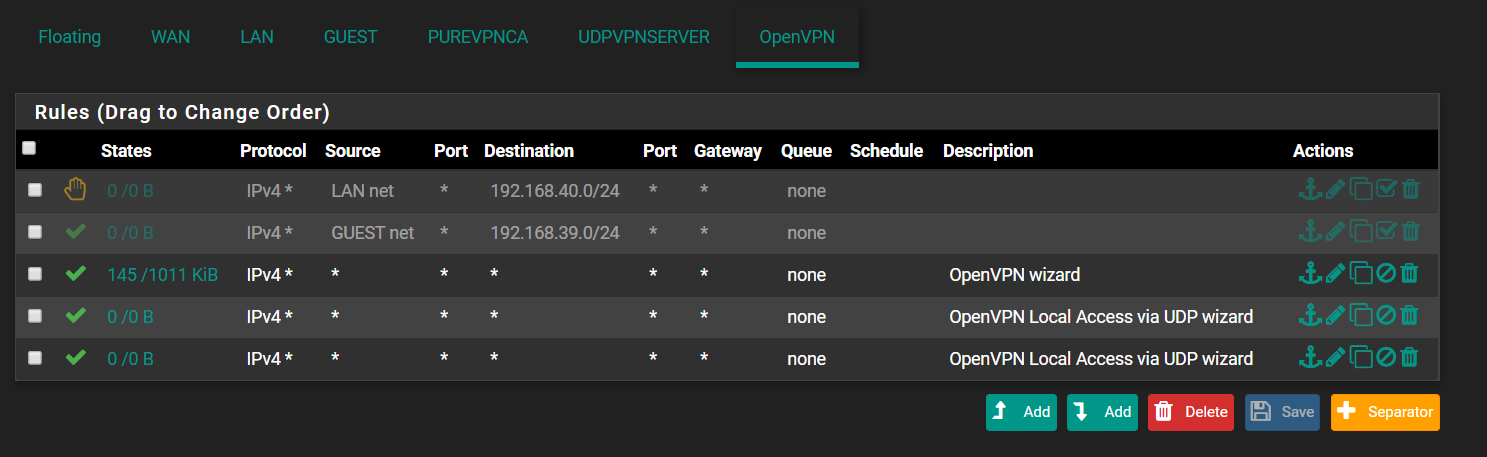
If that doesn't resolve, check the firewall rule on the OpenVPN tab.
-
-
Can't see, what's the rule for the OpenVPN tunnel, since I don't know the network.
You must not allow access from any to any, since you're obviously running VPN services. This way you open your network to the VPN service networks.
You have to restrict the access to your acess server clients. -
@viragomann
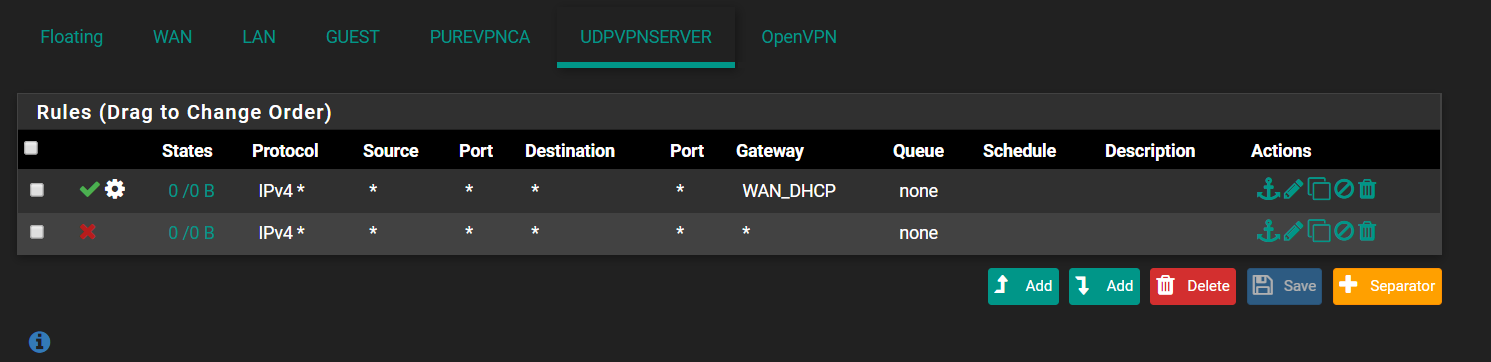 UDPVPNSERVER is the interface I created for The VPN Server,
UDPVPNSERVER is the interface I created for The VPN Server, -
But PUREVPNCA may be a VPN service you're connecting to.
-
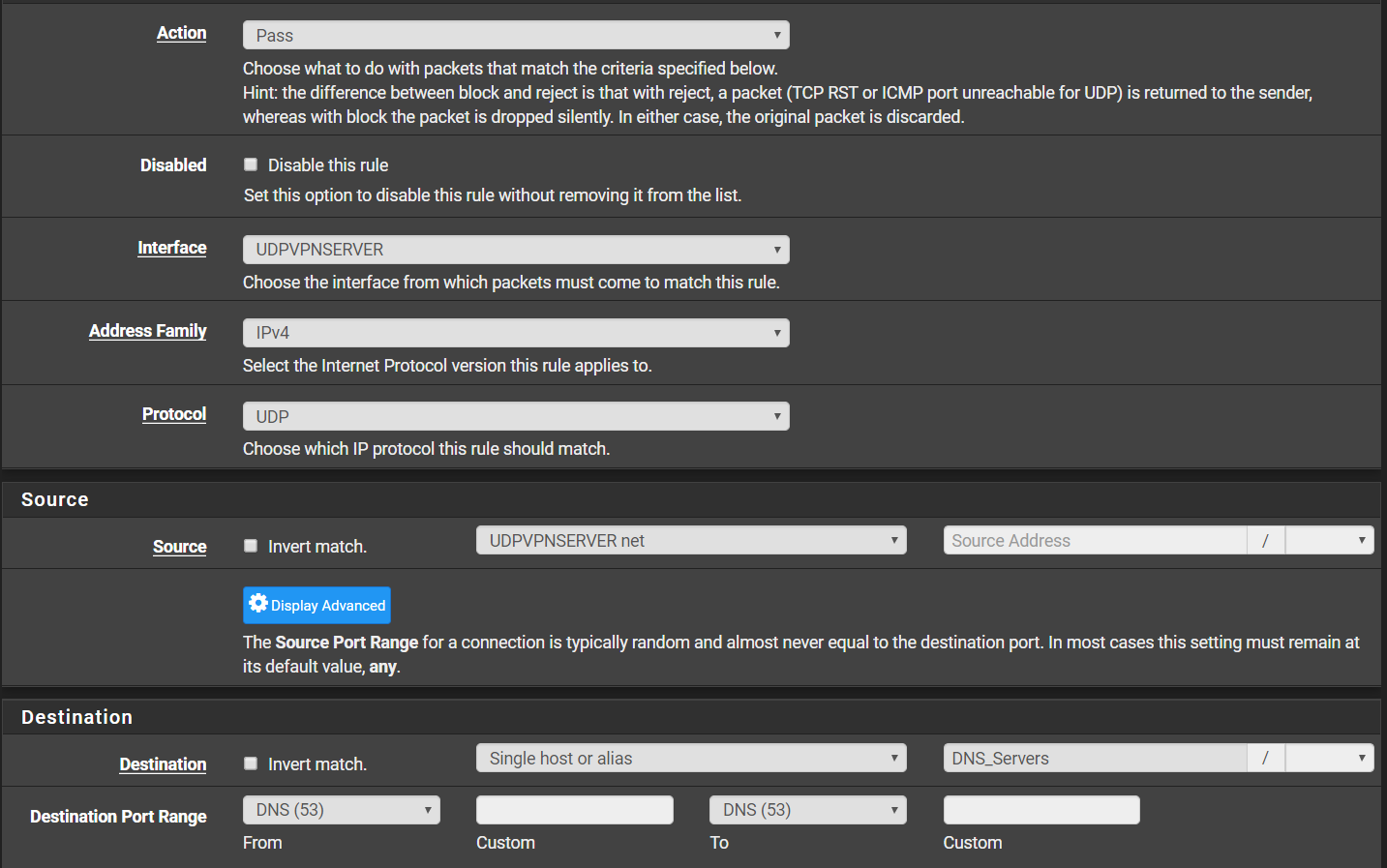
If you disable the rule on the OpenVPN interface you have to add a rule to the UDPVPNSERVER to allow access to your DNS server. The existing rule only allow access to the WAN gateway.
-
@viragomann What Should go in Source and Destination, for dns
-
The source should be the access server tunnel network.
The destination is the DNS servers you provide to the clients. Taking a look at your server settings, these are 192.168.40.4 and 192.168.40.1. -
@viragomann Still not working , DNS_Server is alias for DNS ip address,
-
For troubleshooting only provide public DNS servers on the OpenVPN server settings. The firewall rule you've set on UDPVPNSERVER actually allows access to any, so that should work.
If it doesn't determine if it's an DNS issue by accessing an Internet site by its IP. -
@viragomann Even by ip I cannot access....
-
Everything looks correctly.
To investigate use the Packet Capture feature from the pfSense Diagnostic menu.
Start a capture on the UDPVPNSERVER interface while you try to connect to a public site on the vpn client device and check what you get.
Take an additional capture from WAN, in the IP box put the destination IP you try to access for filtering. Here you should see the packets as well, but with your WAN address as source. -
@viragomann FROM UDPVPNERVER
00:32:29.439062 IP 192.168.43.2.60730 > 192.168.40.4.53: UDP, length 45
00:32:29.442286 IP 192.168.43.2.45976 > 192.168.40.4.53: UDP, length 39
00:32:29.551224 IP 192.168.40.4.53 > 192.168.43.2.60730: UDP, length 61
00:32:29.566385 IP 192.168.40.4.53 > 192.168.43.2.45976: UDP, length 90
00:32:29.719377 IP 192.168.43.2.42234 > 108.128.165.138.5223: tcp 0
00:32:29.731783 IP 192.168.43.2.49548 > 173.194.202.188.5228: tcp 0
00:32:30.549329 IP 192.168.43.2.42234 > 108.128.165.138.5223: tcp 0
00:32:30.729830 IP 192.168.43.2.49548 > 173.194.202.188.5228: tcp 0
00:32:32.548850 IP 192.168.43.2.42234 > 108.128.165.138.5223: tcp 0
00:32:32.737575 IP 192.168.43.2.49548 > 173.194.202.188.5228: tcp 0
00:32:36.560154 IP 192.168.43.2.42234 > 108.128.165.138.5223: tcp 0
00:32:36.740280 IP 192.168.43.2.49548 > 173.194.202.188.5228: tcp 0
00:32:38.888502 IP 192.168.43.2.1699 > 192.168.40.4.53: UDP, length 33
00:32:38.980506 IP 192.168.43.2.29475 > 192.168.40.4.53: UDP, length 32
00:32:39.006726 IP 192.168.40.4.53 > 192.168.43.2.1699: UDP, length 49
00:32:39.011566 IP 192.168.43.2.35915 > 192.168.40.4.53: UDP, length 37
00:32:39.042072 IP 192.168.43.2.55278 > 172.217.13.195.443: tcp 0
00:32:39.042388 IP 192.168.43.2.55280 > 172.217.13.195.443: tcp 0
00:32:39.046913 IP 192.168.40.4.53 > 192.168.43.2.35915: UDP, length 53
00:32:39.064722 IP 192.168.43.2.37576 > 192.168.40.4.53: UDP, length 37
00:32:39.065159 IP 192.168.40.4.53 > 192.168.43.2.37576: UDP, length 53
00:32:39.079351 IP 192.168.43.2 > 192.168.40.4: ICMP 192.168.43.2 udp port 35915 unreachable, length 89
00:32:39.101370 IP 192.168.40.4.53 > 192.168.43.2.29475: UDP, length 111
00:32:39.321619 IP 192.168.43.2.33004 > 192.168.40.4.53: UDP, length 37
00:32:39.322114 IP 192.168.40.4.53 > 192.168.43.2.33004: UDP, length 53
00:32:39.326088 IP 192.168.43.2 > 192.168.40.4: ICMP 192.168.43.2 udp port 37576 unreachable, length 89
00:32:39.326112 IP 192.168.43.2 > 192.168.40.4: ICMP 192.168.43.2 udp port 29475 unreachable, length 147
00:32:39.356992 IP 192.168.43.2.47762 > 172.217.13.173.443: UDP, length 1350
00:32:39.379553 IP 192.168.43.2.56989 > 192.168.40.4.53: UDP, length 35
00:32:39.380290 IP 192.168.40.4.53 > 192.168.43.2.56989: UDP, length 51
00:32:39.416312 IP 192.168.43.2.45712 > 172.16.1.1.443: tcp 0
00:32:39.422976 IP 192.168.43.2.47762 > 172.217.13.173.443: UDP, length 1350
00:32:39.423049 IP 192.168.43.2.54192 > 172.217.13.173.443: tcp 0
00:32:39.423092 IP 192.168.43.2.10136 > 192.168.40.4.53: UDP, length 35
00:32:39.499082 IP 192.168.40.4.53 > 192.168.43.2.10136: UDP, length 87
00:32:39.563255 IP 192.168.43.2.40236 > 172.217.13.131.443: UDP, length 1350
00:32:39.565727 IP 192.168.43.2.47762 > 172.217.13.173.443: UDP, length 1350
00:32:39.580383 IP 192.168.43.2.20303 > 192.168.40.4.53: UDP, length 31
00:32:39.581121 IP 192.168.40.4.53 > 192.168.43.2.20303: UDP, length 47
00:32:39.612426 IP 192.168.43.2.40236 > 172.217.13.131.443: UDP, length 1350
00:32:39.613464 IP 192.168.43.2.45716 > 172.16.1.1.443: tcp 0
00:32:39.635817 IP 192.168.43.2.45718 > 172.16.1.1.443: tcp 0
00:32:39.674561 IP 192.168.43.2.54198 > 172.217.13.173.443: tcp 0
00:32:39.708538 IP 192.168.43.2.40236 > 172.217.13.131.443: UDP, length 1350
00:32:39.821403 IP 192.168.43.2.47762 > 172.217.13.173.443: UDP, length 1350
00:32:39.840581 IP 192.168.43.2.45722 > 172.16.1.1.443: tcp 0
00:32:39.893650 IP 192.168.43.2.40236 > 172.217.13.131.443: UDP, length 1350
00:32:39.914130 IP 192.168.43.2.30101 > 192.168.40.4.53: UDP, length 33
00:32:39.952079 IP 192.168.40.4.53 > 192.168.43.2.30101: UDP, length 49
00:32:40.142092 IP 192.168.43.2.55299 > 192.168.40.4.53: UDP, length 32
00:32:40.142138 IP 192.168.43.2.5063 > 192.168.40.4.53: UDP, length 39
00:32:40.144286 IP 192.168.43.2.54270 > 192.168.40.4.53: UDP, length 38
00:32:40.144552 IP 192.168.43.2.1647 > 192.168.40.4.53: UDP, length 45
00:32:40.145112 IP 192.168.40.4.53 > 192.168.43.2.1647: UDP, length 61
00:32:40.156936 IP 192.168.43.2.60590 > 172.217.13.142.443: UDP, length 1350
00:32:40.156988 IP 192.168.43.2.60182 > 172.217.13.142.443: tcp 0
00:32:40.157013 IP 192.168.43.2.31543 > 192.168.40.4.53: UDP, length 40
00:32:40.165080 IP 192.168.40.4.53 > 192.168.43.2.5063: UDP, length 103
00:32:40.178922 IP 192.168.43.2.21722 > 192.168.40.4.53: UDP, length 35
00:32:40.179791 IP 192.168.40.4.53 > 192.168.43.2.21722: UDP, length 51
00:32:40.183803 IP 192.168.43.2.45726 > 172.16.1.1.443: tcp 0
00:32:40.198438 IP 192.168.43.2.2401 > 192.168.40.4.53: UDP, length 36
00:32:40.212076 IP 192.168.40.4.53 > 192.168.43.2.31543: UDP, length 139
00:32:40.221308 IP 192.168.43.2.45728 > 172.16.1.1.443: tcp 0
00:32:40.223297 IP 192.168.43.2.49760 > 52.204.139.6.443: tcp 0
00:32:40.250374 IP 192.168.43.2.44220 > 23.38.214.238.443: tcp 0
00:32:40.262503 IP 192.168.43.2.40236 > 172.217.13.131.443: UDP, length 1350
00:32:40.301141 IP 192.168.43.2.60590 > 172.217.13.142.443: UDP, length 1350
00:32:40.334125 IP 192.168.43.2.47762 > 172.217.13.173.443: UDP, length 1350
00:32:40.338010 IP 192.168.40.4.53 > 192.168.43.2.2401: UDP, length 73
00:32:40.348026 IP 192.168.40.4.53 > 192.168.43.2.54270: UDP, length 86
00:32:40.372123 IP 192.168.43.2.59850 > 172.217.13.166.443: UDP, length 1350
00:32:40.372171 IP 192.168.43.2.43614 > 172.217.13.166.443: tcp 0
00:32:40.381106 IP 192.168.43.2.56098 > 69.171.250.25.443: tcp 0
00:32:40.404616 IP 192.168.43.2.60196 > 172.217.13.142.443: tcp 0
00:32:40.407604 IP 192.168.43.2.45712 > 172.16.1.1.443: tcp 0
00:32:40.411368 IP 192.168.43.2.44228 > 23.38.214.238.443: tcp 0
00:32:40.422809 IP 192.168.43.2.54192 > 172.217.13.173.443: tcp 0
00:32:40.434559 IP 192.168.43.2.11017 > 192.168.40.4.53: UDP, length 37
00:32:40.435122 IP 192.168.43.2.45742 > 172.16.1.1.443: tcp 0
00:32:40.441913 IP 192.168.43.2.59850 > 172.217.13.166.443: UDP, length 1350
00:32:40.491041 IP 192.168.40.4.53 > 192.168.43.2.11017: UDP, length 173
00:32:40.525823 IP 192.168.43.2.57612 > 35.174.149.52.443: tcp 0
00:32:40.564655 IP 192.168.43.2.43404 > 192.168.40.4.53: UDP, length 40
00:32:40.576487 IP 192.168.43.2.59850 > 172.217.13.166.443: UDP, length 1350
00:32:40.583033 IP 192.168.40.4.53 > 192.168.43.2.43404: UDP, length 132
00:32:40.602218 IP 192.168.43.2.60590 > 172.217.13.142.443: UDP, length 1350
00:32:40.605290 IP 192.168.43.2.59697 > 192.168.40.4.53: UDP, length 33
00:32:40.607493 IP 192.168.43.2.45716 > 172.16.1.1.443: tcp 0
00:32:40.621301 IP 192.168.43.2.40778 > 45.33.3.7.443: tcp 0
00:32:40.631047 IP 192.168.43.2.43628 > 172.217.13.166.443: tcp 0
00:32:40.631094 IP 192.168.43.2.45718 > 172.16.1.1.443: tcp 0
00:32:40.657380 IP 192.168.40.4.53 > 192.168.43.2.59697: UDP, length 113
00:32:40.667389 IP 192.168.43.2.54198 > 172.217.13.173.443: tcp 0
00:32:40.682317 IP 192.168.43.2.57618 > 35.174.149.52.443: tcp 0
00:32:40.686557 IP 192.168.43.2.10717 > 192.168.40.4.53: UDP, length 34
00:32:40.693562 IP 192.168.43.2.59072 > 104.16.114.39.443: tcp 0
00:32:40.737336 IP 192.168.40.4.53 > 192.168.43.2.10717: UDP, length 79
00:32:40.923604 IP 192.168.43.2.40786 > 45.33.3.7.443: tcp 0
00:32:40.923646 IP 192.168.43.2.45722 > 172.16.1.1.443: tcp 0 -
@viragomann I tired connecting from inside the netowork and outside the network, doesn't work.
Dec 6 14:28:36 openvpn 51068 MULTI_sva: pool returned IPv4=192.168.44.2, IPv6=(Not enabled)
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 [setup] Peer Connection Initiated with [AF_INET]38.---.--.49:54709
Dec 6 14:28:36 openvpn user 'setup' authenticated
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_GUI_VER=OpenVPN_GUI_11
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_TCPNL=1
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_COMP_STUBv2=1
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_COMP_STUB=1
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_LZO=1
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_LZ4v2=1
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_LZ4=1
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_NCP=2
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_PROTO=2
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_PLAT=win
Dec 6 14:28:36 openvpn 51068 38.---.--.49:54709 peer info: IV_VER=2.4.7
Dec 6 14:27:12 openvpn 51068 setup/192.168.40.11:53775 MULTI_sva: pool returned IPv4=192.168.44.2, IPv6=(Not enabled)
Dec 6 14:27:11 openvpn user 'setup' authenticated
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 [setup] Peer Connection Initiated with [AF_INET]192.168.40.11:53775
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_GUI_VER=OpenVPN_GUI_11
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_TCPNL=1
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_COMP_STUBv2=1
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_COMP_STUB=1
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_LZO=1
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_LZ4v2=1
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_LZ4=1
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_NCP=2
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_PROTO=2
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_PLAT=win
Dec 6 14:27:11 openvpn 51068 192.168.40.11:53775 peer info: IV_VER=2.4.7