Setting up a VLAN with pfSense, Ubiquiti, and ESXi
-
@Derelict I've read and reread these a couple of times and am having a hard time understanding. I have an "ok" grasp of networking but these just don't make sense.
Is there somewhere I can read more about these two points?
-
They would be what you want - there is no possible way to show someone the rules that they would want.. Everyones setup is going to be different. I would start with an any any rule to validate connectivity works, and then set them how you want them.. My rules are going to be different than your rules, etc.
edit?
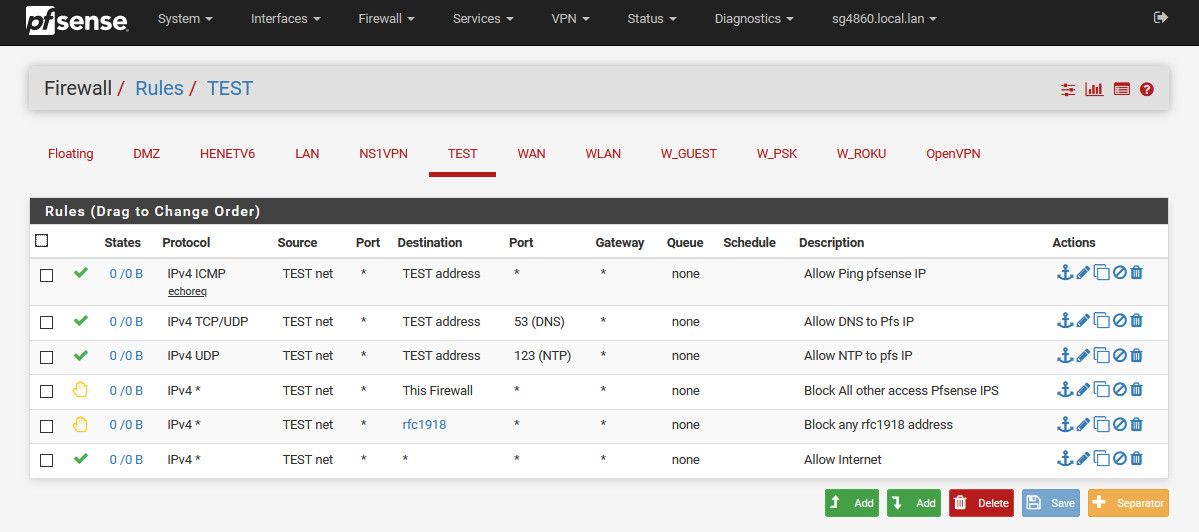
You don't know how to setup a any any rule??Here is basic vlan rules that allows basic services but blocks access to all other vlans (rfc1918)..
-
-
That is not an ANY rule - its only allowing tcp.. So no dns which is udp, and no ping which icmp.
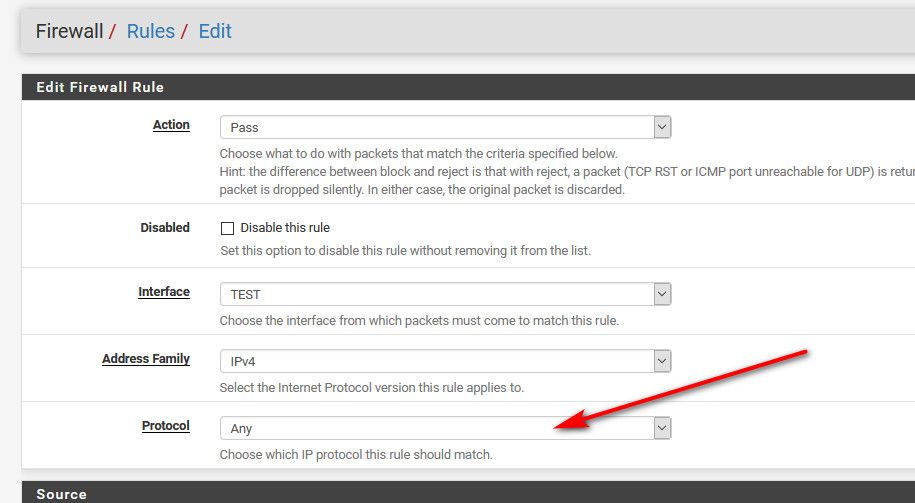
-
Got it now.
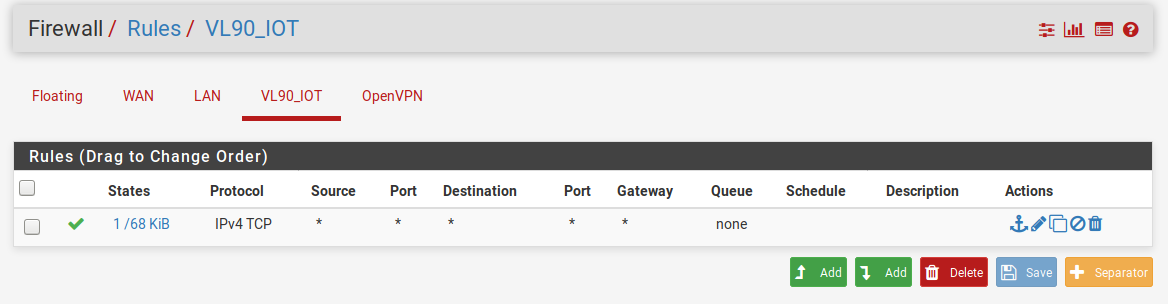
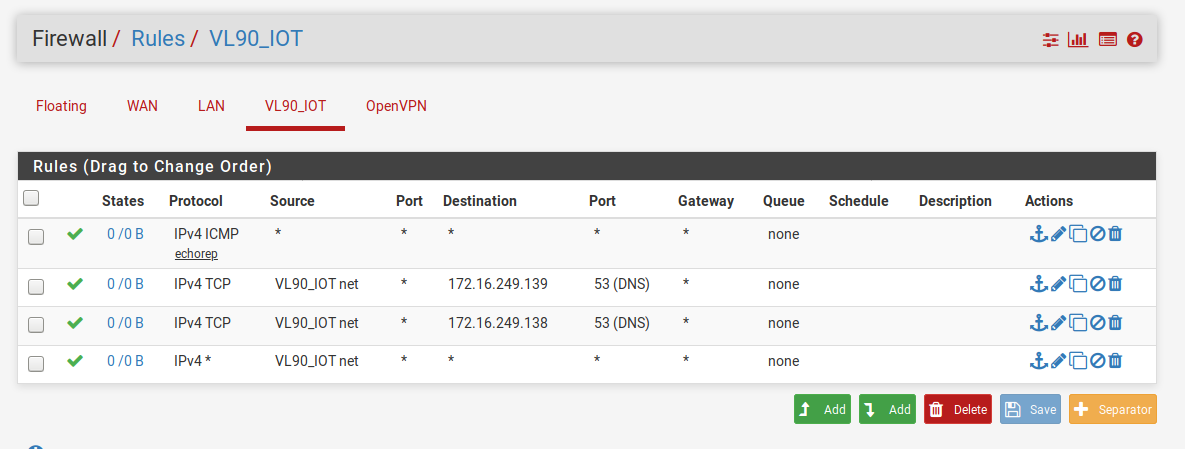
I've created this an will test tomorrow; the goal is to allow the devices on this VLAN access to the internet and access to the specified DNS servers on the local LAN (I hope that term is correct):
-
You have dns set to TCP only - while dns CAN use tcp, it defaults to UDP... You reallly should make those rules UDP/TCP
But since you have any rule there at the bottom those 2 allow rules for dns are pretty pointless.
And that any rule at the end is going to allow access to your lan as well.. You need to put a block rule above the any and below your dns rules, that blocks access your LAN net, if you dont want your vlan to talk to your lan..
Rules are evaluated as traffic enters the interface from the network its attached too, top down, first rule to trigger wins, no other rules are evaluated.
-
Ok, I think I'm getting closer. Here's the new rules:
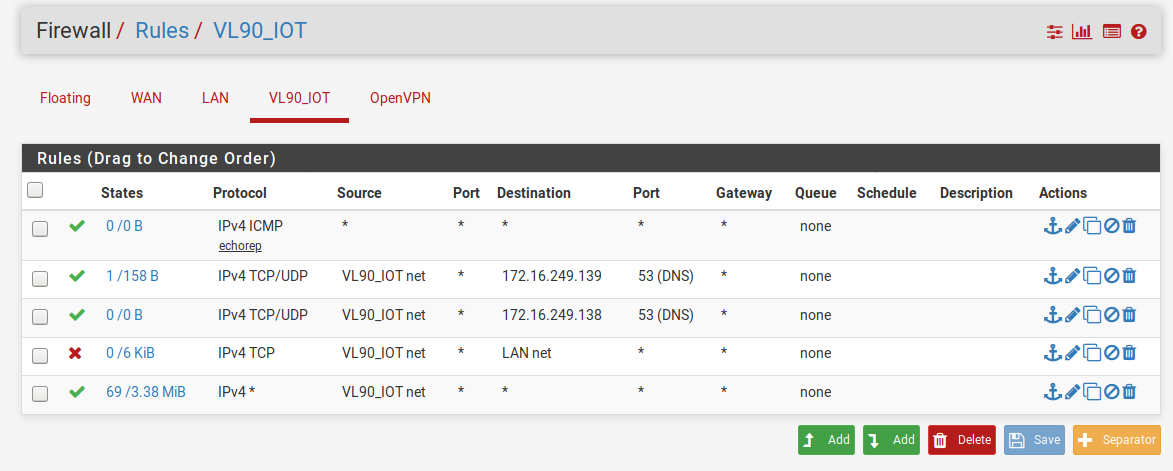
If I understand correctly the rules flow from the top down to the bottom. I'm allowing (on the VLAN90):
-
Ping responses anywhere (but should probably tighten this up to only allow responses out to the internet if I'm trying to segregate this traffic from my internal LAN)
-
DNS traffic ONLY to 172.16.249.139 and then .138
-
Blocking all communication from the VLAN90 to the local LAN
-
All connectivity out to the internet (although, like rule 1, I'm guessing that this rule is too broad and can be tightened up).
For rules 1 and 4, to "tighten" them up to be just applicable to the internet would I change the destination to "WAN net"?
-
-
Wan net is not the internet - its just the network connect to your wan.. It would be something/mask like mine is 64.53.x.x/23 The internet is really anything.. There is no way to tighten that up... Can you put in all address blocks that make up the internet ;)
If you don't want clients on your vlan to ping stuff on your lan, then put a rule that blocks that before you allow ping any..
If you want to tighten it up more, you might want to use the "this firewall" alias to prevent access to your wan IP, this alias includes all IPs that firewall has, a block rule to that on your vlan would prevent access to say the pfsense gui via the wan IP.. See my example rules.
If you ever have a question to if something is allowed or deny, just run through the rules with where your going and what protocol.. Is it denied or allowed in the rules - if it gets to the end without being allowed then it would be denied.. Since the default is denied (not shown).
-
THANK YOU for your help so far; I've almost got it. Here's my rules now (I plan on renaming the descriptions later):
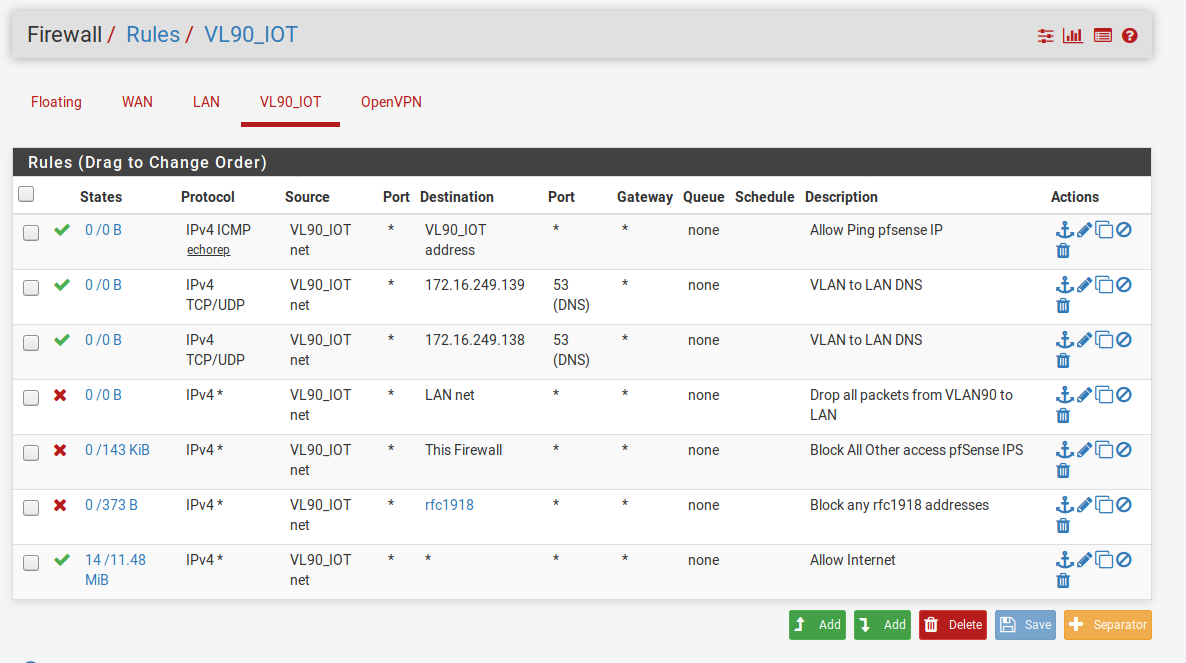
My only remaining issue is that I can't get DNS to work with the rules the way they are now. From the VLAN I'm trying to use the DNS server on my LAN. I thought that rules 2 & 3 would allow the traffic to pass but after putting the 4th rule in place (to prevent the devices on VLAN90 form being able to see the devices on the LAN) DNS stops working entirely.
Should rules 2 & 3 just be the firewall IP address (which would then pass it off to the DNS servers on the LAN) or is there something I'm missing?
Also, I installed Avahi as one of my goals was to have my Apple devices on VLAN90 but still be able to Airplay to them; it seems to be working so far.
Thank you again.
-
@johnpoz Would it make sense to start a new post at this point?
Thank you again for all your (and everyone else's help).
-
I see no hits on your rules for dns.. see the 0/0's - so your clients never sent anything to those IPs on port 53, or you would see hits there..
Do you have anything in floating?
VLAN90 form being able to see the devices on the LAN) DNS stops working entirely.
Only way that would be is if your clients where actually asking pfsense for dns, or different IPs then what you have listed.. Yes your rfc1918 rule is getting hits. And so is your this firewall rule.
-
Is the goal for this to be an internet-only VLAN? Building on that question, is this for your own internal equipment or is this going to be a "guest" VLAN? In either case, many of these rules can be collapsed into a simpler ruleset, IMO:
For an internet-only Guest VLAN:
- Configure DHCP to hand out PFsense (or public DNS) for DNS. Then collapse your rules down to:
Block -> TCP/VL90 net/This firewall/port (alias for 22 and whatever port your GUI is listening on)
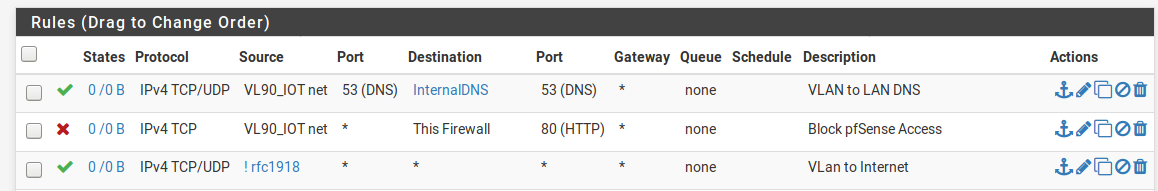
Allow -> VL90 net/Invert match rfc1918 aliasFor an internal, internet-only VLAN where you want your devices to use your internal DNS servers:
Allow -> (TCP/UDP)/VL90 net/Alias for DNS servers/port 53
Block -> TCP/VL90 net/This firewall/port (alias for 22 and whatever port your GUI is listening on)
Allow -> VL90 net/Invert match rfc1918 aliasand TBH, unless there is a specific need for your internet-only traffic to use your internal DNS servers (which I assume are your DC's), I'd go with the first option.
-
@marvosa The idea is an internet only VLAN (it would be nice if Airplay worked between the VLAN and LAN but not necessary) HOWEVER DNS would be pointed to my two internal DNS servers. Anything and everything else on the VLAN would not have access to the LAN.
This is my IoT VLAN; I'm looking to use my internal DNS servers for filtering purposes. For any VLAN I setup I'd want to point it to my internal DNS servers but everything else would be Internet only.
-
@pfSenseUser78 Then I'd go with the 2nd set of rules I posted. They'll be more streamlined for your use case.
-
@marvosa Ok. In the second setup you state "Alias for DNS servers"; I'm not sure what that means. Would I be putting in the 172.x.x.x addresses or am I creating something else?
Thanks!
Edit: Ok, found where to make the alias. Trying now.
-
-
@pfSenseUser78 Edited
I first said yes, but the looked at your rules again...hold on
-
@marvosa SSH is enabled. I created the port alias but I can't figure out how to apply that to the second firewall rule. It doesn't appear in the list of ports to block.
Edit: Found it here: https://docs.netgate.com/pfsense/en/latest/book/firewall/aliases.html
Testing now!
-
@pfSenseUser78 The last rule should be
Protocol = any
Source = VL90_IOT net
Destination = Invert match rfc1918 alias -
@marvosa Fixed.
When I join that network with my laptop I connect and get an IP. I cannot ping 8.8.8.8 or 1.0.0.1 nor can I ping the internal DNS servers (172.16.x.x). If I try to load a website nothing happens.
Not sure where I'm going wrong - is there anything else I can post that might help? I'll continue to google and see if I can find anything myself.