DNSBL only working on DMZ NIC?
-
@provels Yes, Outbound Firewall Rules has both WAN and DMZ selected and set for Reject. Inbound is set for only WAN, Block.
Floating Rules is not enabled.
-
@TAC57 Same as me. I don't have a DMZ, but have rules enabled on LAN and OpenVPN out and get the 10.10.10.1 address on ping with both. Sorry.
-
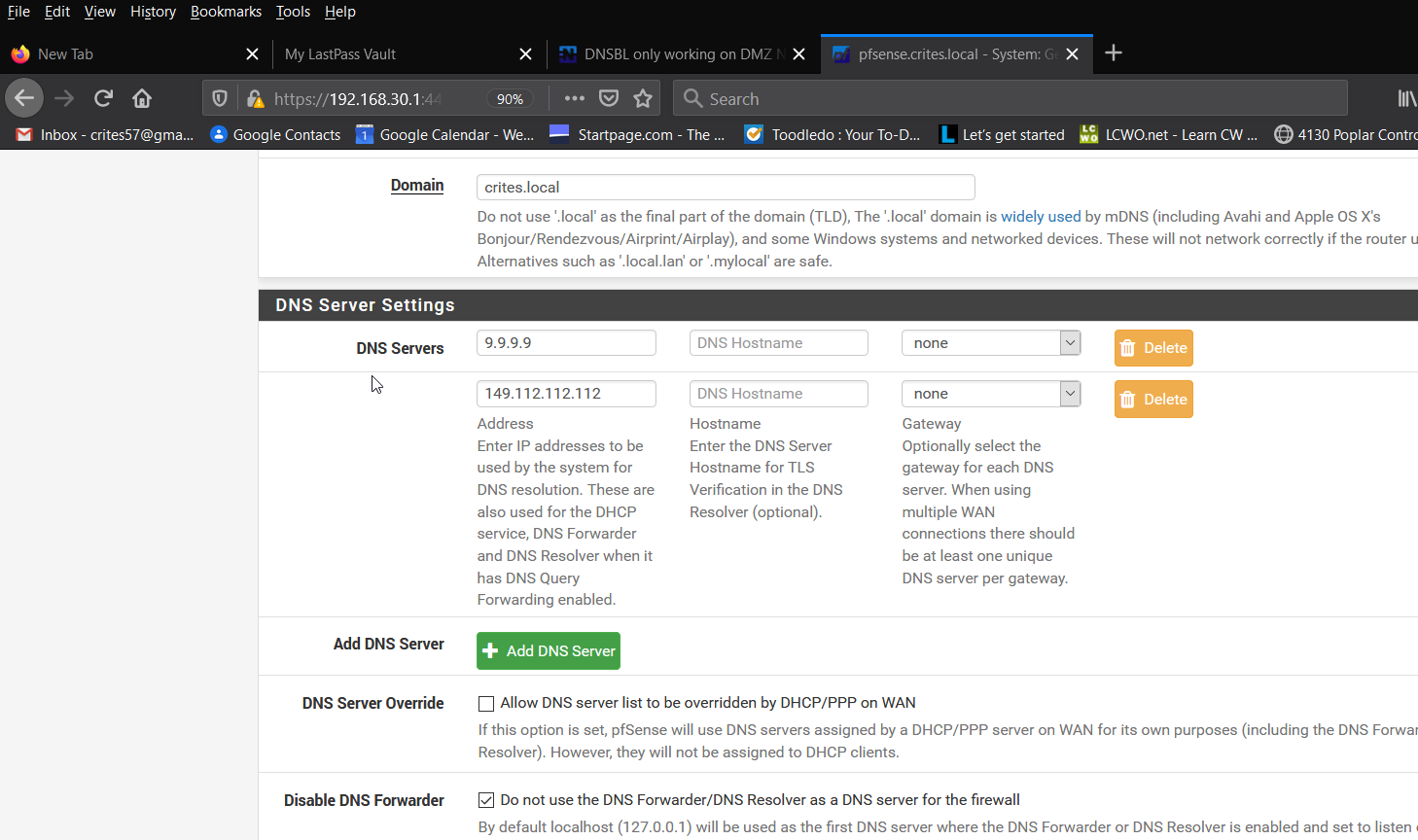
@provels From Services / DHCP Server / LAN I deleted the two DNS servers entries I had (8.8.8.8, 8.8.4.4) to match what was already set under the DMZ interface and now I'm seeing DNSBL alerts on both DMZ and LAN interfaces. But only over WiFi.
Pinging 302br.net from my CAT5 connected desktop does not receive the reply from 10.10.10.1.
-
@TAC57 said in DNSBL only working on DMZ NIC?:
Pinging 302br.net from my CAT5 connected desktop does not receive the reply from 10.10.10.1.
That's one thing.
Did it resolve ?Btw : it does resolve to 199.166.0.24 so DNS is working.
199.166.0.24 replies to ping ....[2.4.4-RELEASE][admin@pfsense.brit-hotel-fumel.net]/root: ping 302br.net PING 302br.net (199.166.0.24): 56 data bytes 64 bytes from 199.166.0.24: icmp_seq=0 ttl=47 time=41.751 ms 64 bytes from 199.166.0.24: icmp_seq=1 ttl=47 time=41.341 ms 64 bytes from 199.166.0.24: icmp_seq=2 ttl=47 time=41.151 ms 64 bytes from 199.166.0.24: icmp_seq=3 ttl=47 time=41.069 ms 64 bytes from 199.166.0.24: icmp_seq=4 ttl=47 time=40.866 ms 64 bytes from 199.166.0.24: icmp_seq=5 ttl=47 time=41.162 ms .... -
@Gertjan I was under the impression 'ping 302br.net' should respond with 10.10.10.1, it does when I ping it from my WiFi connection. I do get 199.166.0.24 if I ping from a direct connect to my LAN.
-
@TAC57 said in DNSBL only working on DMZ NIC?:
everything is working great on my DMZ interface but nothing is getting blocked on my LAN interface.
and then you the explain why :
@TAC57 said in DNSBL only working on DMZ NIC?:
Outbound Firewall Rules has both WAN and DMZ selected and set for Reject. Inbound is set for only WAN, Block.
Floating Rules is not enabled.No DNSBL firewall rules on LAN == nothing will get blocked on LAN.
@TAC57 said in DNSBL only working on DMZ NIC?:
I do get 199.166.0.24 if I ping from a direct connect to my LAN.
Because traffic isn't parsed by DNSBL rules on your LAN .
Because you decided not to place DNSBL rules on LAN.Problem solved ? ^^
-
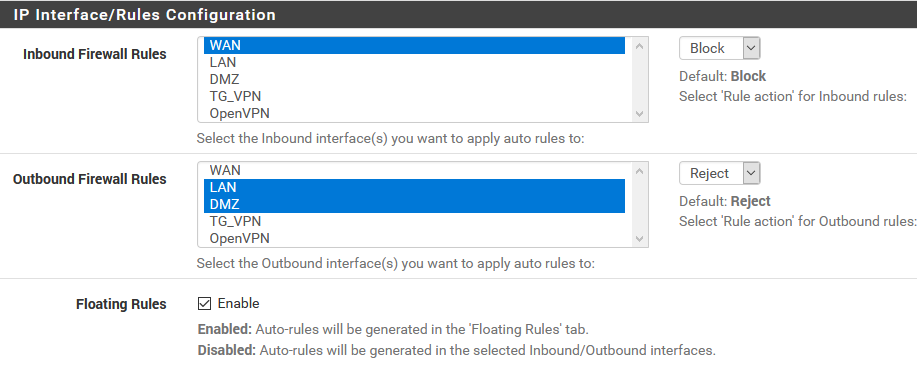
@Gertjan Sorry, in my previous post I had a typo. These are my settings Firewall / pfBlockerNG / IP:
-
Aha, ok.
And what are your DMZ firewall rules and LAN firewall rules ?
@TAC57 said in DNSBL only working on DMZ NIC?:
Floating Rules is not enabled.
Are you sure :
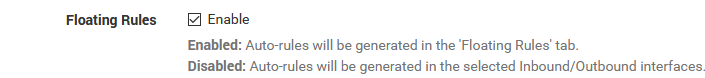
(another typo ? ;) )
edit : so list also your floating rules.
-
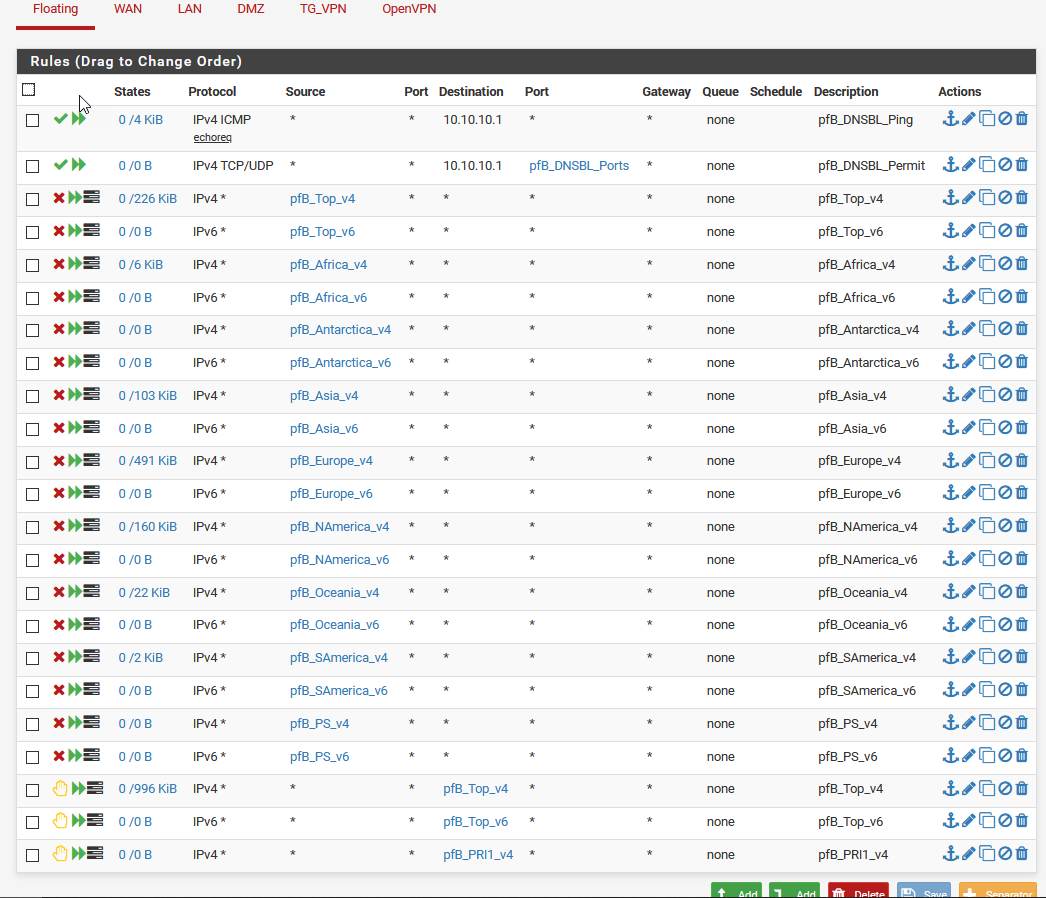
@Gertjan Yes, Floating Rules are enabled. I have been messing with settings during this conversation. :-)
Below are my floating rules. I didn't included the others since they only have rules associated with my server. BTW I really appreciate your feedback.
-
Just throwing this out there, but are you sure the LAN client isn't hard set to use a DNS source other than pfSense?
Is DNS in the DHCP server set? You can eliminate it and DHCP will just use pfSense.
You could also force all outbound DNS to use pfSense as DNS even if hard set to another DNS with an outbound rule like this:
https://docs.netgate.com/pfsense/en/latest/dns/redirecting-all-dns-requests-to-pfsense.html -