Default Bogon and RFC 1918 rules for interface groups
-
I have two interfaces in my pfSense connected to external networks and I want the same ACL to apply on both of them without replicating it for both interfaces. I created an interface group for both of them, but I am unable to set up the default Bogon and RFC 1918 rules for the group itself.
I want to add some "allow" rules to the group ACL, but I want the Bogon and RFC 1918 rules to take precedence over them. Under the current architecture of the pfSense firewall, the group rules (allow) will take precedence over the ACLs of the individual interfaces.
Any idea on how I can add the default rules to the group. I think I can define an alias for the private networks and add a custom rule to block the RFC 1918 traffic, but I have no idea how I can access the bogon list that is maintained and updated by the system.
Thanks
-
You understand those bogon and rfc1918 are kind of antiquated best practices sorts of rules.. Neither bogon or rfc1918 route over the internet - so for them to hit your wan are highly unlikely... I have never seen a hit on bogon rules on wan to be honest ;)
If your creating ACLs to allow specific source, to your wan - then those sorts of rules make zero sense, since the only thing that would be allowed in are in your ACL anyway.
And default is deny..
example
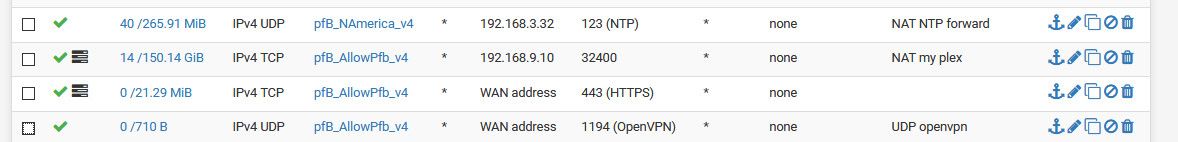
Since bogon or rfc1918 are not part of these allowed sources in the above wan rules. bogon or rfc1918 would never be allowed for those rules anyway and would just hit the default deny.
So its pretty pointless to have a deny for bogon or rfc1918 above them..
-
So, you're suggesting to ignore them altogether.
The default deny will not give me the same effect because the "allow" rules in my ACL are based on the destination only. So, if I want to allow traffic going to 192.168.2.0/24, for example, the traffic destined to that subnet will be allowed at the group ACL regardless of its source (i.e., even if it is bogon traffic), before getting to the interface ACL or the default deny.
-
But to be honest how would a bogon even get to your wan? They don't route over the internet, nor does rfc1918.. The only way they would be allowed into your allow rules would be if your isp was messed up..
edit:
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.htmlwhere do you get that your group rules would be applied before group rules? So if you leave the block bogon and rfc on the interface they would be processed before your allow rules in your group
-
Well, honestly, I don't really know. I have never seen or heard these rules before I started using pfSense. Not really sure if that might impose a risk, but I believe eventually, I might just ignore them.
-
It is on the page you shared
User-defined rules: Rules defined on the floating tab Rules defined on interface group tabs (Including IPsec and OpenVPN) Rules defined on interface tabs (WAN, LAN, OPTx, etc)Did I misunderstand this?
-
Back in the day - yes it was best practice to block bogon ;) Which is really shrinking anyway ;) hehehe Not many IPv4 address not assigned..
To be honest I wouldn't worry about it too much if those rules... In the 10 years running pfsense, never ever seen a hit on bogon rules.. rfc1918 - sure you see some noise to those from your isp now and then.. Mostly broadcast.
edit: Yeah from that it does look like your group rules would be evaluated first.. Not really a fan of putting any sort of allow rules on wan in group... I would call them out specific on the interface!! But group rules are still user defined, while bogon and rfc are not.
To be SURE the order of the rules, and how they would be processed is to look at the raw rules via
https://docs.netgate.com/pfsense/en/latest/firewall/viewing-the-full-pf-ruleset.htmlBut see here from the order of rules linked too
Internal automatic rules (pass and block for various items like lockout, snort, DHCP, etc.)Bogon and Rfc should be evaluated there - which is before your user rules and group rules and the interface rules, etc.
-
@johnpoz said in Default Bogon and RFC 1918 rules for interface groups:
But to be honest how would a bogon even get to your wan? They don't route over the internet, nor does rfc1918.
Several years ago, my ISP was using addresses in the 10.0.0.0 block for internal routing. I could see them with traceroute. Also, a few years back, I was reading about how Comcast didn't even have enough RFC 1918 to meet the needs of managing it's network, without segmentation. So, some might be coming from an ISP.
They will route just fine, just like any other address, which is why they're supposed to be blocked, so they can't escape from internal routing. So yes, misconfigured routing by the ISP can cause that. I would hope that any ISP that uses those addresses internally blocks them from leaving their network.
-
Very true - even if the isp let them out, no other isp should route them... There is a bit different though when your a backbone isp router and and end user firewall ;)
I don't see it a big deal if you didn't enable them on your wan, I don't have them currently enabled - they are eye sore.. And all my rules are locked to specific source anyway. So doesn't matter either way.. If your not in the allowed list your not being allowed.. Bogon and RFC not in the allow list ;)
Either way - from my understanding of the rule order, if you have them enabled they would be evaluated before your group or interface rules..
To be 100% sure you could look at the full rule set... I don't have any current groups setup, nor do I have bogon or rfc enabled on my wan... So would take a bit of work I don't really feel like doing to validate that.. I am like 99% sure the way I read the rule order that they are evaluated before your group rules..
Does someone want to look at the full rule set and say yeah or nay for sure?
edit: Ok just validated. enabled bogon and rfc blocks and those are way up high in the rule list
block drop in quick on igb1 from <bogons> to any label "block bogon IPv4 networks from WAN" block drop in quick on igb1 from <bogonsv6> to any label "block bogon IPv6 networks from WAN" block drop in quick on igb1 inet from 10.0.0.0/8 to any label "Block private networks from WAN block 10/8" block drop in quick on igb1 inet from 127.0.0.0/8 to any label "Block private networks from WAN block 127/8" block drop in quick on igb1 inet from 172.16.0.0/12 to any label "Block private networks from WAN block 172.16/12" block drop in quick on igb1 inet from 192.168.0.0/16 to any label "Block private networks from WAN block 192.168/16"Then way farther down the list is my test rule for testgoup
pass in quick on testgroup inet proto tcp from any to 1.2.3.4 port = mdqs flags S/SA keep state label "USER_RULE: allow 666"So yeah the bogon and rfc block rules you enable would be evaluated before any group rule you created anyway. Just enable bogon and rfc blocks on both your wan interfaces.
-
Thank you @johnpoz for taking the time to validate that. That's really helpful.
-
No problem, only took a couple of minutes to validate ;) I was pretty sure without doing it - but always good to be "extra" sure..
Again though in the big picture not really an issue anyway if you ask me.. I turned bogon and rfc back off once I validated ;)