Allow internet-only access to VLAN members
-
I am in learn mode so please excuse me if this is a dumb question.
I set up a VLAN using my new SG-5100 and some new managed switches. L2 is working for IPv4. DHCP is issuing addresses on the VLAN and DNS Resolver is resolving host names (I will be making another post related to IPv6 which is posing its own challenge).
At the moment, my firewall rules are wide open on this VLAN. This was done solely to avoid confusion when setting up L2. However, I need to constrain VLAN members.
The requirement is easily described. Interfaces on this VLAN should only be allowed to use the internet and nothing else, similar to "guest" SSIDs offered by some access points. This is what I am thinking:
-
Define an alias comprising all private subnets (192.168.0.0, 10.0.0.0., etc.)
-
VLAN rule 1: ALLOW access to the SG-5100's address on the VLAN. This address provides DHCP, DNS and is the gateway, e.g. 192.168.139.1/32
-
VLAN rule 2, DENY all traffic destined for the private subnets alias
-
VLAN rule 3, ALLOW all traffic (should be only internet at this point?)
Will this meet the requirement?
Is there a better way?
Is there an answer already in the forum? If so I couldn't find it.
-
-
something like this should work, only http/https allowed
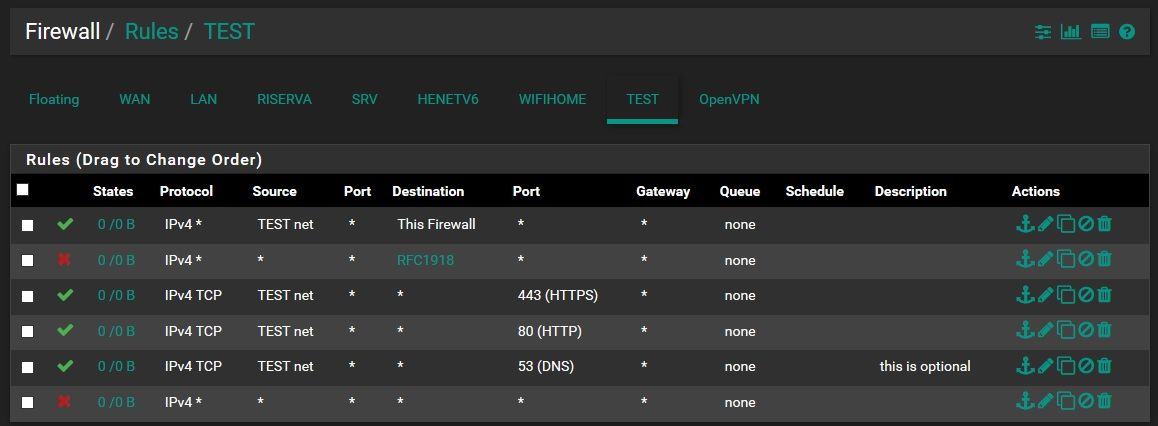
sorry, i was in a hurry, a little error dns should be UDP also
-
That last rule not needed either, unless on purpose you do not want any logging of blockes.
Also the rule to allow access to firewall would mean vlan users could access web gui, which is normally blocked on such vlans that are only suppose to have internet..
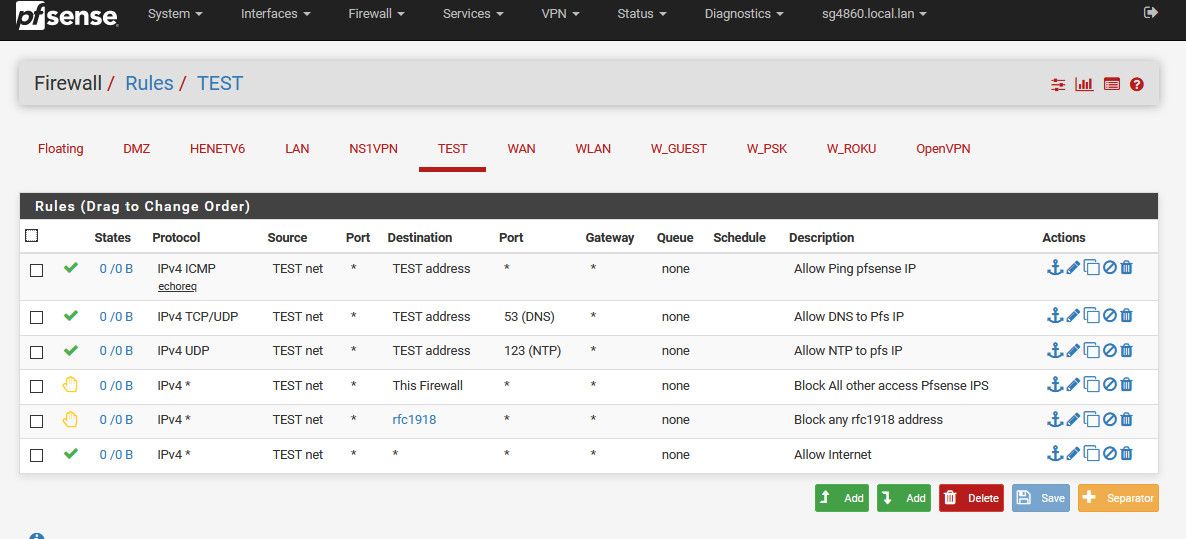
Here are my example rules for doing what your asking... Internet is way more than just 433/80 as well... Why would you care what port some guest talks to something on the internet on? Maybe they want to stream a plex server that is on 32400 for example.
-
@kiokoman Thanks! I am pretty sure that I understand what you're advising, which means I'm learning. I hadn't thought about limiting outbound ports. It's great advice, especially if I configure DHCP to dispense public DNS server addresses (e.g. Google or MS), rather than the one on my firewall. There doesn't seem to be much of anything exposed to attack, exactly what I need. Thanks!
-
@johnpoz Excellent advice as well. In this case I am going to go really tight and loosen as needed. In fact there may be a version of this for children that further restricts access using a white list of allowed sites.
I am also planning VLANs for IOT devices which will allow some interaction with each other and with local networks. The primary goal will be to limit the attack surface available to anyone who might gain control of the device (miscreant vendor or hijacker). The above suggestions will be great starting points for that scenario.
In any event, it's good to know that the general approach is sound. That's what I really needed.