Cannot connect to internet (firewall rules)
-
@noaboa said in Cannot connect to internet (firewall rules):
I got the pfSense Version 2.3.4 running
Why in the world would you install a version from 2017? EOL for over a year now..
You need to post a picture your rules if you want anyone to help you figure out what your doing wrong.. But yes if traffic is not allowed it would be blocked by the default deny rule..
-
Thanks for your reply,
well as I said, we got the pfSense VM preinstalled from our school and I didn't bother.But why is it blocking it? I have a rule which allows all traffic or should...
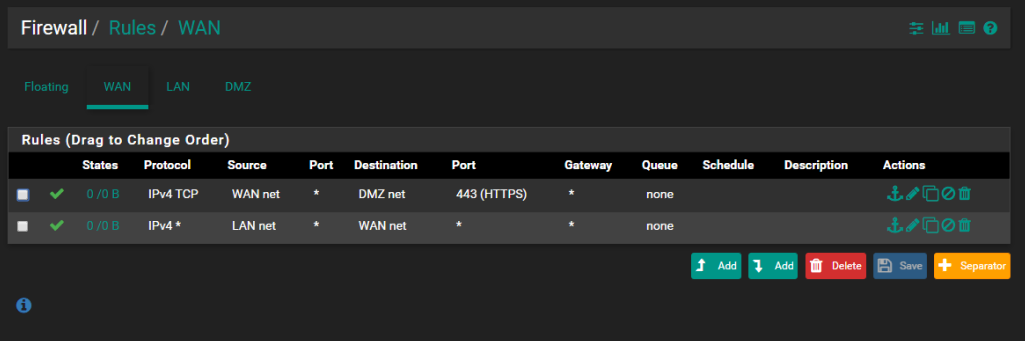
WAN Rules
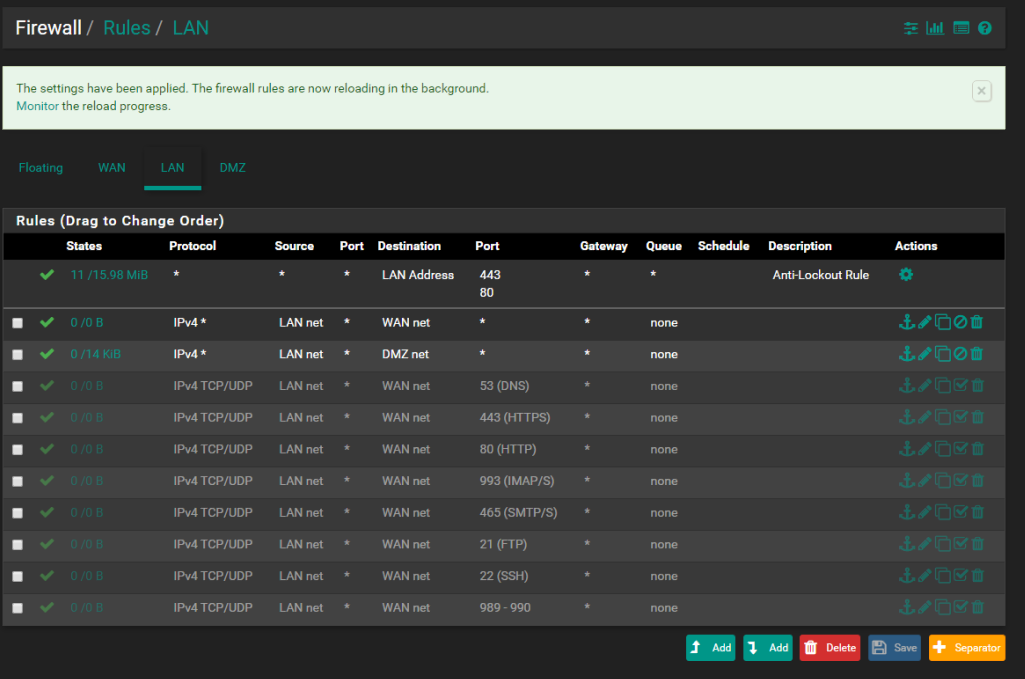
LAN Rules
DMZ Rules
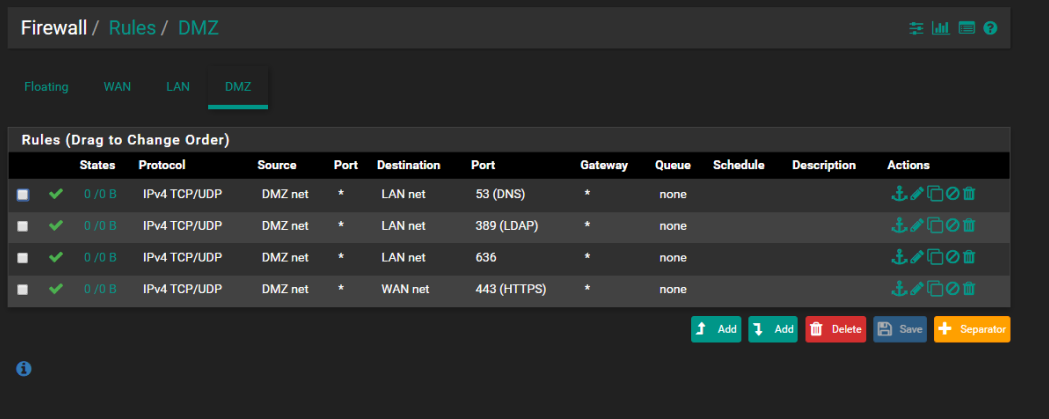
From the firewall I can ping 1.1.1.1 or 8.8.8.8 also on my host for the vm's I can surf normally. WAN Interface is DHCP.
-
Well for starters lan net would never be a source of traffic into the wan..
Wan net is just that wan network.. nothing else. (wan net does not = internet, it equals the network on the wan) So you rules on dmz would not allow any traffic to say 1.1.1.1, do do any of your rules on dmz allow for ping (icmp)
Rules are evaluated as traffic enters the interface from the network its attached too. Top Down, first rule to trigger wins - no other rules would be evaluated.
-
So wich net would I use then? How would it be done properly?
Yes I do know wan =/ Internet. Yes and in my case my computers network card is wan net and I get the ip from my router.
yes indeed but my Linux Server is in the LAN and there I've got the rule in lan and wan which should allow traffic on all ports.Ok that's good to know so all the stuff that goes out of LAN needs to be in the wan tab?
-
@noaboa : where all all these rules come from ??
Normally, on WAN, there shouldn't be any rules.
Normally, rules should de activated - not removed (example : the initial firewall rule you found on LAN).
Normally, you should add one rule, and test it. Only then you'll add the next one.Maybe "Normally" isn't the right word. Although I advise everybody to proceed like that.
Btw : a firewall like pfSense isn't really a good study object. All the answers are already here.
Add these to the "1000 or so more videos" from other sources, and you go straight into a PhD without ever leaving home.@noaboa said in Cannot connect to internet (firewall rules):
Ok that's good to know so all the stuff that goes out of LAN needs to be in the wan tab?
No.
The WAN tab stays empty.
Always.
Exception : you saw the NAT video and want use NAT rules (expert level here !) - then rules on WAN are created for you. -
@noaboa said in Cannot connect to internet (firewall rules):
So wich net would I use then?
To get to the "internet" that would be ANY... Unless your wanting to create rules for every possible IP on the internet ;)
-
we got the firewall from school and they already configured some stuff so that it's a reall life scenario they did any any rules and told us that's wrong change it that's part of the challenge.
well we can't choose what we want to do. They just give us the projects and we have to write the documentation and set up the virtual lab/infrastructure as we planned it.
-
@noaboa said in Cannot connect to internet (firewall rules):
so that it's a reall life scenario they did any any rules and told us that's wrong change it that's part of the challenge.
Ok. lol.
Some one did a good job after all ^^Reset the thing to default.
This wall take care of all other tricky issues that would take a lot of time to find.
Go discover what interfaces, network ports, are. How firewall rules are handled - see pfSense full manual, there is some really need-to-know info there.
When all ok, draw up a plan, connect to pSense, and set it up by a one to one step. -
so a new rule
source: any
destination: wan
port : anyor what do you mean?
Still that does not resolve my problem.
I want to have rules which allow only some ports like the ones I created in LAN and only allow those into the internet and block everything else. Same for rules from DMZ -> LAN should also only allow the stuff I need and block the rest.
-
I should know the basics, we learnd that in school but it's not beahving as I would expect it to. That's why I'm asking what I'm missing.
They didn't change tricky stuff to drive us crazy just the anyrules as if some stupid guy did this who had no idea what he was doing.
But still are my rules wrong? what am I missing?
-
@noaboa said in Cannot connect to internet (firewall rules):
so a new rule
Which interface ?
@noaboa said in Cannot connect to internet (firewall rules):
source: any
destination: wan
port : anyFor starters, make it look like this :
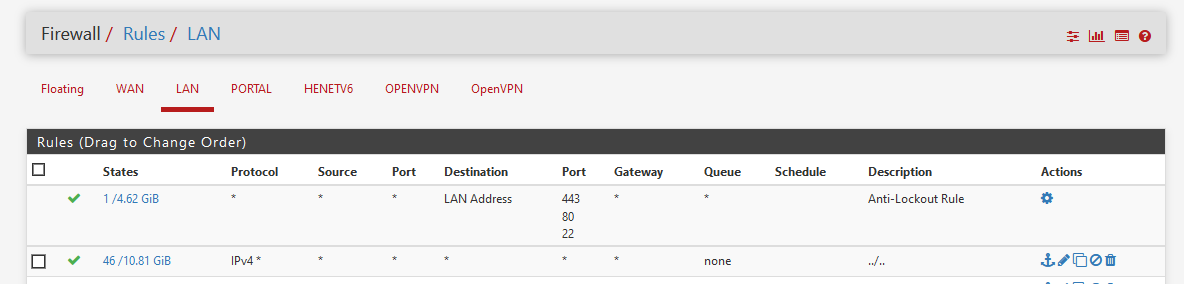
The first rule is a menu option - it's build automatically.
The second rules is the one you have to make - it's the default rule. -
I kind of don't understand why we have three tabs for the rules. Is it just for filtering and nice display?
Or when do I put one in WAN, LAN or DMZ?The first rule is a menu option - it's build automatically.
yeah I know so that I cant lock myself out of the webinterface. right?
The second rules is the one you have to make - it's the default rule.
Well that works of course but we can't have any any rules. only specific rules
-
Well the internet is ANY so not sure how your going to allow "internet" without an ANY rule as dest.. Unless your going to create rules to only allow access to the specific IPs on the internet.
But the rule/rules you create wouldn't really need to be a true any any... you would have a source network, ie your lan. You can set specific destination ports say only 80/443 for example. But unless your going to create rules to allow traffic to every possible IP your going to talk to the dest IP/Network would need to be any.
Tabs - you mean your interfaces, and floating?
You place rules on the specific interfaces for the traffic that will enter that interface. Floating is a special case where you can do specific things, like filter on outbound traffic, or apply rules to more than one interface.
Normally that tab doesn't need to be used.
-
Well internet is any but I can still say only dns, http and https and that not into the dmz how would I do that?
And for what are LAN net and WAN net then used for?
Okay got that with the tabs.
-
exactly you can limit what ports, sure dns (tcp/udp 53) and http https sure.
Normally clients on the lan would just ask pfsense for dns.. So you would need a rule to allow dns to pfsense IP.. You wouldn't need to allow dns to some outside IP unless your client was going to be sending specific queries to some outside nameserver. Which you could limit to IP of those nameservers.
the lan and wan tabs would be used to put rules on those interfaces.. Not sure how that isn't obvious?
-
Okay great thanks. Yeah but they want us to have a linux server that does dhcp, dns and some other stuff so I have to do it that way.
So for example if I a server in the dmz must connect to the dns server in the lan then I would but LAN net as destination and https in the internet but not in the LAN I put WAN net as destination right?
Mostly I worked with ipfire and there you just have a list of all rules in one place so I got confused also ubiquiti has 6 tabs with lan in, lan out and so on
-
@noaboa said in Cannot connect to internet (firewall rules):
n the LAN I put WAN net as destination right?
Why would you think you need to put wan net as destination? Is there something in the wan network you need to talk to from lan?
You could put specific IP as dest if you know it. But keep in mind the any rule would allow access to any IP be it in your wan or dmz or where ever.
If you don't want say lan to talk to dmz netnwork, then you would put a block rules above the any rule in lan.
You do not need return traffic rules, those are handled by state that is created.
-
Why would you think you need to put wan net as destination? Is there something in the wan network you need to talk to from lan?
because I don't want it to be able to talk to stuff in the lan but if I say any wouldn't allow it to talk to lan if it's https 443?It's for Seafile Server which is going to be in the DMZ and the client on the phone or pc connects over https. And I don't want it to access the lan
If you don't want say lan to talk to dmz netnwork, then you would put a block rules above the any rule in lan.
Ahh makes sense.
You do not need return traffic rules, those are handled by state that is created.
Ahh right how can I forget.