acme-challenge was passiert da
-
Hallo zusammen,
kann mir mal jemand grundsätzlich erklären was bei der acme-challenge eigentlich im Einzelnen passiert?
Wer kontaktiert wen, legt den Challange ab und für wen muss das Challange-Verzeichnis zugänglich sein?
Viele Grüße
pixel24 -
Mal angenommen du möchtest den Host "sub.inter.net" zertifizieren.
-
Mittels DNS-Verfahren:
Der ACME-Dienst stellt ein Request für "sub.inter.net" an die CA von Let's Encrypt. Die CA übermittelt jetzt einen Verification-Key an ACME. Anschließend pausiert die CA für ca. 10 Sekunden während sich ACME beim Domain-Hoster anmeldet (z.B. Cloudflare) und einen TXT-Record mit dem Verification-Key in den Host "_acme-challenge.sub.inter.net" einträgt. Nach 10 Sekunden prüft die CA den Host auf den TXT-Record. Ist er korrekt, geht die CA davon aus, dass das Request legitim ist, erstellt das Zertifikat und übermittelt es an ACME. Damit wird das Zertifikat im Speicher der pfsense abgelegt. -
Mittels FTP (webroot FTP):
Der ACME-Dienst stellt ein Request für "sub.inter.net" an die CA von Let's Encrypt. Die CA übermittelt eine Datei mit einem bestimmten Dateinamen und bestimmten Dateiinhalt an ACME und pausiert anschließend für ca. 10 Sekunden. Währenddessen lädt ACME die Datei per FTP hoch. Nach 10 Sekunden prüft die CA ob die Datei unter "http://sub.inter.net/.well-known/acme-challenge/xxxxxxxxxxxx" vorhanden ist (xxxxxxxxxxxx ist nur der Platzhalter für den Dateinamen). Wichtig: die CA prüft die Domain ohne SSL (http nicht https). Sind Dateiname und Inhalt korrekt, geht die CA davon aus, dass das Request legitim ist, erstellt das Zertifikat und übermittelt es an ACME. Damit wird das Zertifikat im Speicher der pfsense abgelegt.
Puuuh, ich hoffe, das hilft ;)
-
-
Super vielen Dank! Das hilft mir schon deshalb weil ich mal den Ablauf kenne, dieser wird in den Hotows die man so findet nie erklärt.
Webroot FTP ist das was ich realisieren möchte.
@inciter said in acme-challenge was passiert da:
Mittels FTP (webroot FTP):
Der ACME-Dienst stellt ein Request für "sub.inter.net" an die CA von Let's Encrypt. Die CA übermittelt eine Datei mit einem bestimmten Dateinamen und bestimmten Dateiinhalt an ACME und pausiert anschließend für ca. 10 Sekunden. Währenddessen lädt ACME die Datei per FTP hoch. Nach 10 Sekunden prüft die CA ob die Datei unter "http://sub.inter.net/.well-known/acme-challenge/xxxxxxxxxxxx" vorhanden ist (xxxxxxxxxxxx ist nur der Platzhalter für den Dateinamen). Wichtig: die CA prüft die Domain ohne SSL (http nicht https). Sind Dateiname und Inhalt korrekt, geht die CA davon aus, dass das Request legitim ist, erstellt das Zertifikat und übermittelt es an ACME. Damit wird das Zertifikat im Speicher der pfsense abgelegt.Ich habe ja neben den beiden Server-VM's die vom Internet aus per HTTPS auf gleichem Port anhand ihrer Subdomain angesprochen werden sollen:
gw.mydomain.de -> [WAN]-PFSense-[LAN] -> 192.168.24.6 (gw.intern.local) cloud.mydomain.de -> [WAN]-PFSense-[LAN] -> 192.168.24.11 (cloud.intern.local)noch eine gesonderte (schlanke) Server-VM als HTTP- / FTP - Server eingerichtet die im Moment lediglich im LAN verfügbar ist:
web01.intern.local (192.168.24.7)dort sollen die ACME-Challange's beider Subdomain (gw... und cloud..) abgelegt werden. Geht dies überhaupt?
Und dann bedeutet dies doch dass ich dem HA-Proxy noch mitteilen muss die HTTP-Anfragen die auf Port 80 vom WAN aus kommen und ".well-known/acme-challenge" in der aufgerufenen URL beinhalten nicht an die 192.168.24.6 oder 192.168.24.11 gehen soll sondern an die 192.168.24.7 da dort der Pfad liegt wo ja ACME die Dateien hinein geschrieben hat.
Habe ich das so richtig verstanden?
-
Die acme-challenge funtioniert bei mir einfach nicht. Ich habe zum testen ein ganz einfaches Szenario aufgebaut.
Ein lokaler Web- / FTP - Server der im LAN unter 192.168.24.7 zu erreichen ist. Der Hostname (intern) ist web01.intern.local.
Die PFSense stellt das Gateway zum Internet dar und hat eine feste WAN-IPv4: 10.20.30.40 und die LAN-IP ist 192.168.24.254Als Methode soll wie gesagt webroot FTP genutzt werden wobei die Dateien auf dem internen FTP-Server (192.168.24.7) abgelegt werden soll. Sowohl der Webserver als auch der FTP-Server läuft und ist eingerichtet. Ich habe für diesen Zweck einen gesonderten Benutzer "webftp" mit Passwort angelegt.
Zunächst teste ich intern:
[In Firefox]
http://web01.intern.local/.well-known/acme-challenge/-> Funktioniert ohne Passwort
ftp://web01.gehr.local/.well-known/acme-challenge/-> Passwort wird abgefragt -> Eingabe -> Im Verzeichnis. Also funktioniert.
Nun verbinde ich (noch immer aus dem LAN) per FileZilla mit diesen Benutzerdaten, wechsle ins Verzeichnis .well-known/acme-challenge und teste ob ich Schreibrechte habe, also Dateien und Ordner anlegen kann, auch das funktioniert.
Auf dem externen Webserver (bei All-Inkl) - dort ist lediglich meine Domain (mydomain.de) gehostet und die Mail-Accounts eingerichtet - habe ich einen A-Record gesetzt:
web01.mydomain.de -> [feste WAN IP der PFSense]An der PFSense habe ich die Kommunikation von extern auf die Firewall selbst (Port 80) zugelassen:
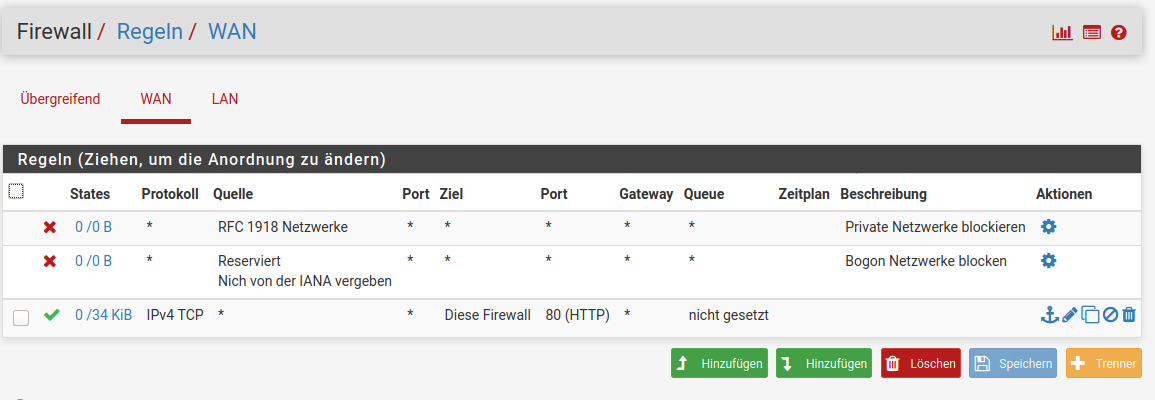
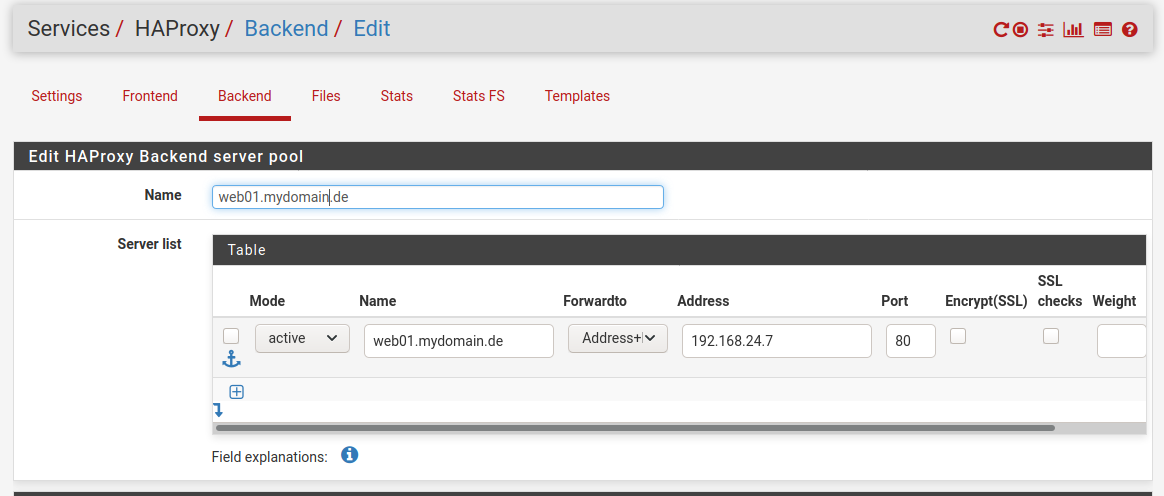
In HA-Proxy habe ich ein Backend angelegt:
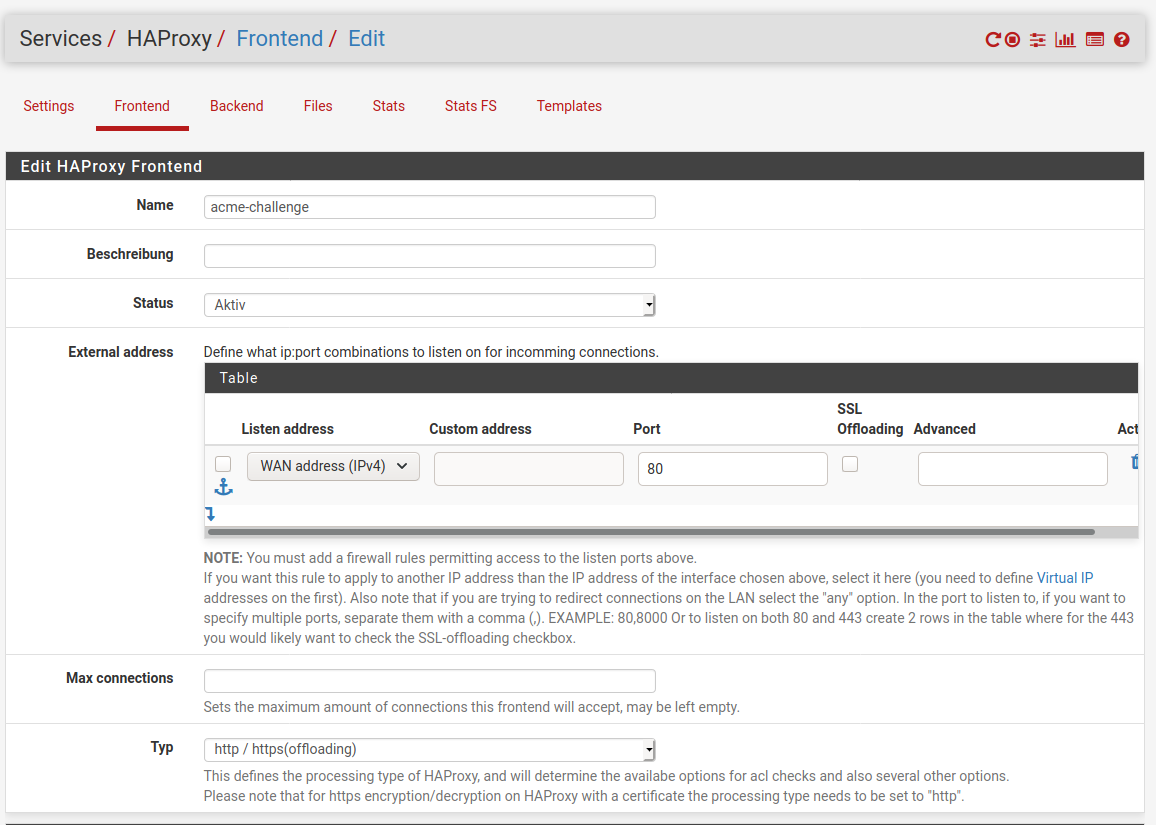
Sowie ein Frontend:
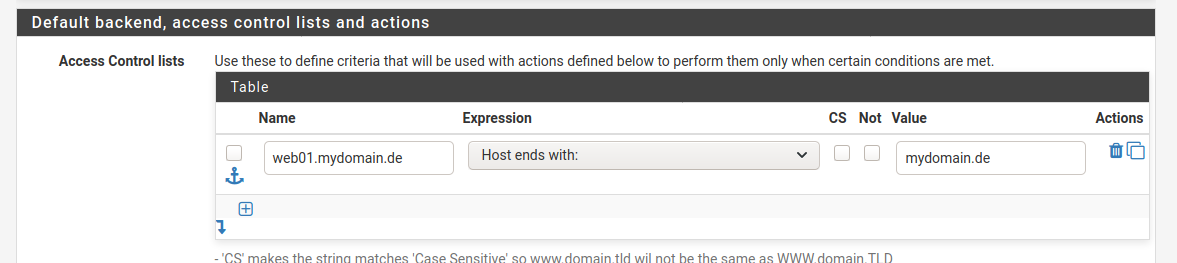
Als Aktion ist angegeben das o.g. Backend zu nutzen.
Nun teste ist ob von extern mein Verzeichnis für den acme-challenge per HTTP erreichbar ist und rufe aus dem WAN die URL auf:
http://web01.mydomain.de/.well-known/acme-challenge/Als nächstes lege ich einen Account-Key (Staging) an was problemlos klappt un ein Zertifikat für den internen Webserver:
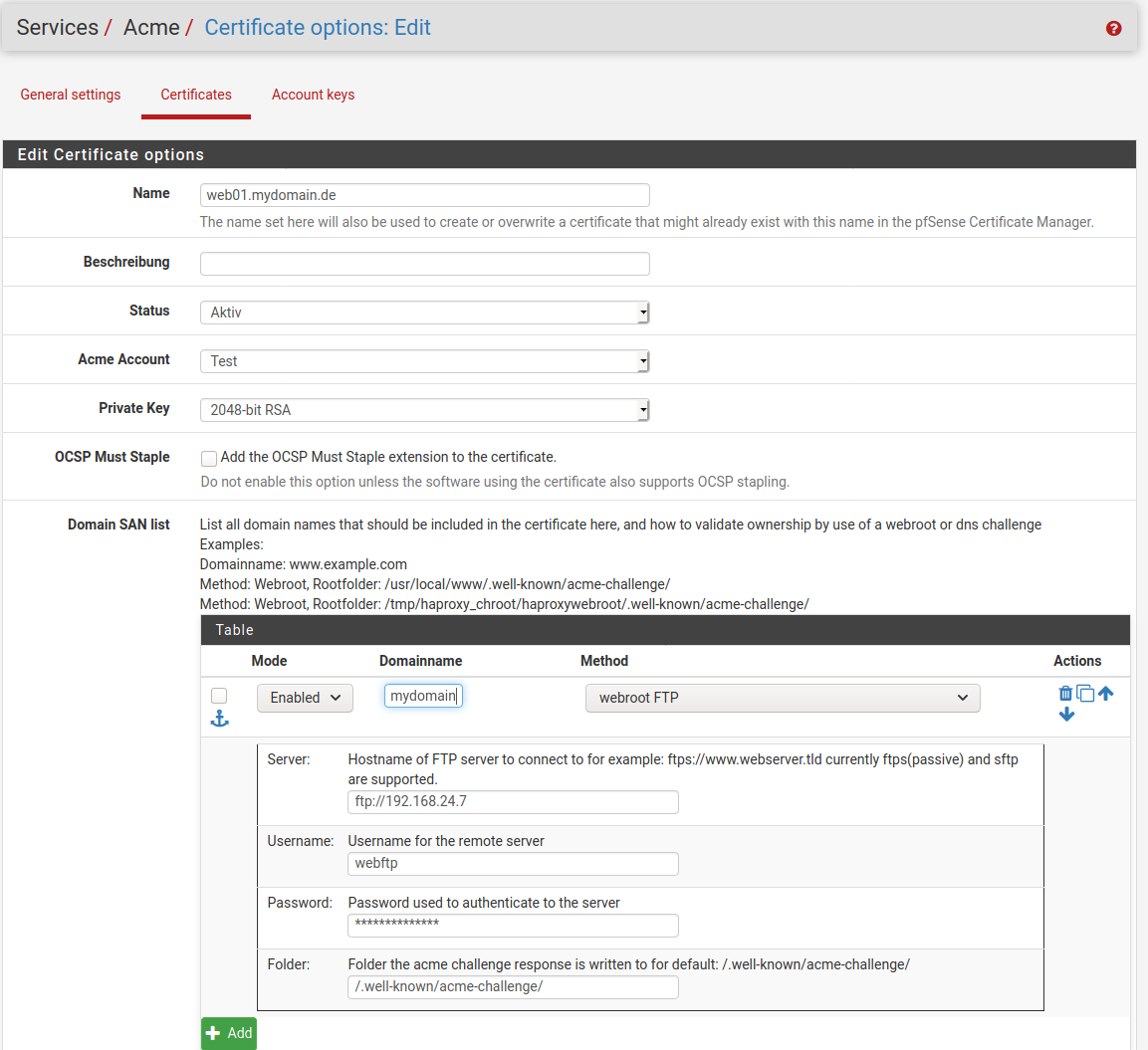
@inciter said in acme-challenge was passiert da:
Währenddessen lädt ACME die Datei per FTP hoch.
Dieser erste Schritte "der acme-Dienst läd die Datei auf den angegebenen FTP hoch - welcher bei mir ja lokal im LAN steht - funktioniert bereits nicht und ich verstehe einfach nicht warum. Dort müsste doch, sobald ich beim Zertifikat auf "Issiue/Renew" klicke der Callange hochgeladen werden, oder? Aber da passiert nichts.
-
Aus der "acme_issuecert.log" werde ich leider auch nicht schlauer:
[Mon Jan 6 12:42:16 CET 2020] readlink exists=0 [Mon Jan 6 12:42:16 CET 2020] dirname exists=0 [Mon Jan 6 12:42:16 CET 2020] Lets find script dir. [Mon Jan 6 12:42:16 CET 2020] _SCRIPT_='/usr/local/pkg/acme/acme.sh' [Mon Jan 6 12:42:16 CET 2020] _script='/usr/local/pkg/acme/acme.sh' [Mon Jan 6 12:42:16 CET 2020] _script_home='/usr/local/pkg/acme' [Mon Jan 6 12:42:16 CET 2020] Using config home:/tmp/acme/web01.mydomain.de/ [Mon Jan 6 12:42:16 CET 2020] APP [Mon Jan 6 12:42:16 CET 2020] 3:LOG_FILE='/tmp/acme/web01.mydomain.de/acme_issuecert.log' [Mon Jan 6 12:42:16 CET 2020] APP [Mon Jan 6 12:42:16 CET 2020] 4:LOG_LEVEL='3' [Mon Jan 6 12:42:16 CET 2020] LE_WORKING_DIR='/tmp/acme/web01.mydomain.de/' [Mon Jan 6 12:42:16 CET 2020] Running cmd: issue [Mon Jan 6 12:42:16 CET 2020] _main_domain='web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] _alt_domains='no' [Mon Jan 6 12:42:16 CET 2020] Using config home:/tmp/acme/web01.mydomain.de/ [Mon Jan 6 12:42:16 CET 2020] ACME_DIRECTORY='https://acme-staging-v02.api.letsencrypt.org/directory' [Mon Jan 6 12:42:16 CET 2020] _ACME_SERVER_HOST='acme-staging-v02.api.letsencrypt.org' [Mon Jan 6 12:42:16 CET 2020] CA_CONF='/tmp/acme/web01.mydomain.de//ca/acme-staging-v02.api.letsencrypt.org/ca.conf' [Mon Jan 6 12:42:16 CET 2020] DOMAIN_PATH='/tmp/acme/web01.mydomain.de//web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] 'pfSenseacme' does not contain 'dns' [Mon Jan 6 12:42:16 CET 2020] Using ACME_DIRECTORY: https://acme-staging-v02.api.letsencrypt.org/directory [Mon Jan 6 12:42:16 CET 2020] _init api for server: https://acme-staging-v02.api.letsencrypt.org/directory [Mon Jan 6 12:42:16 CET 2020] GET [Mon Jan 6 12:42:16 CET 2020] url='https://acme-staging-v02.api.letsencrypt.org/directory' [Mon Jan 6 12:42:16 CET 2020] timeout= [Mon Jan 6 12:42:16 CET 2020] curl exists=0 [Mon Jan 6 12:42:16 CET 2020] wget exists=127 [Mon Jan 6 12:42:16 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g ' [Mon Jan 6 12:42:16 CET 2020] ret='0' [Mon Jan 6 12:42:16 CET 2020] response='{ "h10b1KXrvMc": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417", "keyChange": "https://acme-staging-v02.api.letsencrypt.org/acme/key-change", "meta": { "caaIdentities": [ "letsencrypt.org" ], "termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf", "website": "https://letsencrypt.org/docs/staging-environment/" }, "newAccount": "https://acme-staging-v02.api.letsencrypt.org/acme/new-acct", "newNonce": "https://acme-staging-v02.api.letsencrypt.org/acme/new-nonce", "newOrder": "https://acme-staging-v02.api.letsencrypt.org/acme/new-order", "revokeCert": "https://acme-staging-v02.api.letsencrypt.org/acme/revoke-cert" }' [Mon Jan 6 12:42:16 CET 2020] ACME_KEY_CHANGE='https://acme-staging-v02.api.letsencrypt.org/acme/key-change' [Mon Jan 6 12:42:16 CET 2020] ACME_NEW_AUTHZ [Mon Jan 6 12:42:16 CET 2020] ACME_NEW_ORDER='https://acme-staging-v02.api.letsencrypt.org/acme/new-order' [Mon Jan 6 12:42:16 CET 2020] ACME_NEW_ACCOUNT='https://acme-staging-v02.api.letsencrypt.org/acme/new-acct' [Mon Jan 6 12:42:16 CET 2020] ACME_REVOKE_CERT='https://acme-staging-v02.api.letsencrypt.org/acme/revoke-cert' [Mon Jan 6 12:42:16 CET 2020] ACME_AGREEMENT='https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf' [Mon Jan 6 12:42:16 CET 2020] ACME_NEW_NONCE='https://acme-staging-v02.api.letsencrypt.org/acme/new-nonce' [Mon Jan 6 12:42:16 CET 2020] ACME_VERSION='2' [Mon Jan 6 12:42:16 CET 2020] Le_NextRenewTime [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 1:Le_Domain='web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 2:Le_Alt='no' [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 3:Le_Webroot='pfSenseacme' [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 4:Le_PreHook='' [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 5:Le_PostHook='' [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 6:Le_RenewHook='' [Mon Jan 6 12:42:16 CET 2020] OK [Mon Jan 6 12:42:16 CET 2020] 9:Le_API='https://acme-staging-v02.api.letsencrypt.org/directory' [Mon Jan 6 12:42:16 CET 2020] _on_before_issue [Mon Jan 6 12:42:16 CET 2020] _chk_main_domain='web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] _chk_alt_domains [Mon Jan 6 12:42:16 CET 2020] 'pfSenseacme' does not contain 'no' [Mon Jan 6 12:42:16 CET 2020] Le_LocalAddress [Mon Jan 6 12:42:16 CET 2020] d='web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] Check for domain='web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] _currentRoot='pfSenseacme' [Mon Jan 6 12:42:16 CET 2020] d [Mon Jan 6 12:42:16 CET 2020] 'pfSenseacme' does not contain 'apache' [Mon Jan 6 12:42:16 CET 2020] _saved_account_key_hash='t2LtE/OPQ5lK16ljYDp/Sy8+ZsII6Coso4iO4s5WB7k=' [Mon Jan 6 12:42:16 CET 2020] base64 single line. [Mon Jan 6 12:42:16 CET 2020] _saved_account_key_hash is not changed, skip register account. [Mon Jan 6 12:42:16 CET 2020] Read key length: [Mon Jan 6 12:42:16 CET 2020] _createcsr [Mon Jan 6 12:42:16 CET 2020] domain='web01.mydomain.de' [Mon Jan 6 12:42:16 CET 2020] domainlist [Mon Jan 6 12:42:16 CET 2020] csrkey='/tmp/acme/web01.mydomain.de//web01.mydomain.de/web01.mydomain.de.key' [Mon Jan 6 12:42:16 CET 2020] csr='/tmp/acme/web01.mydomain.de//web01.mydomain.de/web01.mydomain.de.csr' [Mon Jan 6 12:42:16 CET 2020] csrconf='/tmp/acme/web01.mydomain.de//web01.mydomain.de/web01.mydomain.de.csr.conf' [Mon Jan 6 12:42:16 CET 2020] Single domain='web01.mydomain.de' [Mon Jan 6 12:42:17 CET 2020] _is_idn_d='web01.mydomain.de' [Mon Jan 6 12:42:17 CET 2020] _idn_temp [Mon Jan 6 12:42:17 CET 2020] _is_idn_d='web01.mydomain.de' [Mon Jan 6 12:42:17 CET 2020] _idn_temp [Mon Jan 6 12:42:17 CET 2020] _csr_cn='web01.mydomain.de' [Mon Jan 6 12:42:17 CET 2020] OK [Mon Jan 6 12:42:17 CET 2020] 7:Le_Keylength='' [Mon Jan 6 12:42:17 CET 2020] Getting domain auth token for each domain [Mon Jan 6 12:42:17 CET 2020] _is_idn_d='web01.mydomain.de' [Mon Jan 6 12:42:17 CET 2020] _idn_temp [Mon Jan 6 12:42:17 CET 2020] d [Mon Jan 6 12:42:17 CET 2020] _identifiers='{"type":"dns","value":"web01.mydomain.de"}' [Mon Jan 6 12:42:17 CET 2020] url='https://acme-staging-v02.api.letsencrypt.org/acme/new-order' [Mon Jan 6 12:42:17 CET 2020] payload='{"identifiers": [{"type":"dns","value":"web01.mydomain.de"}]}' [Mon Jan 6 12:42:17 CET 2020] RSA key [Mon Jan 6 12:42:17 CET 2020] pub_exp='010001' [Mon Jan 6 12:42:17 CET 2020] base64 single line. [Mon Jan 6 12:42:17 CET 2020] xxd exists=127 [Mon Jan 6 12:42:17 CET 2020] _URGLY_PRINTF='1' [Mon Jan 6 12:42:17 CET 2020] e='AQAB' [Mon Jan 6 12:42:17 CET 2020] modulus='C40AFBD55255F2B476DB13BAAEC3FA3F9811E61820BE72FAEDD5B1727C26720E9149A5977EC8B7CFD85D88B236CCE870F4DC7C20D1D07498B75F59B33F151D5DECEBA1DA878F304BC42B667AA6FDB1E88B71F3678DD5D2C7ABC9075A36CF8C2EC8A4D0317DC7C766DF988B35B23638587157789C24DEEF7A9D27D8376796CFACC7199EED3DEB9CE2915EF5FEF76E7A425B8BD9C1A8FF720850ACCB51353C33D6F6E682E678936508F4E1F051809A481DC2ECFBE4A800380A0BD84019161715DF2748E7B3E49877419BC95BC8E005292796D929DBF5B3CADBA165B076D0707BA56D6AD50D73F17B080AECCA0E0E2171581C5C289B3A55C3DE9D4310B77D626F1881B70CAF867DB7BC144AEA3AB82190DFF3131E89A1F972E215B31208730BAC821D7989A7C39AE490DAA3A176B40F6A888EE34DB19F98AB74DB7C8DD12D587F7AEC2AF1E32BDD7E16961D45A7156E553579ACB1B0019422A7797A8D08E9CF0B638CA3BA87F593FD9D17613D0C22EE3FF6B1B13F0160A2A22E7F721E8AFCECAE3AA31CD87CA7501C1F7C532FF8E8E8982DA0E61744E86E151F9292BC93DA62BF54C9E053973409B4CD8E8AB47A81216ED3EDFFCF4759D21CA2616B757088FC44ADEF9A970AF9D8E3AA78F545115EE174DFED89F92216DDA6BFDDCE5285F441A5A5516C57D5AD3A4406027D09BCAC9DBAC3D6E93B5B24AE965BA7021FED1F4D893B' [Mon Jan 6 12:42:17 CET 2020] base64 single line. [Mon Jan 6 12:42:17 CET 2020] xxd exists=127 [Mon Jan 6 12:42:17 CET 2020] _URGLY_PRINTF='1' [Mon Jan 6 12:42:17 CET 2020] n='xAr71VJV8rR22xO6rsP6P5gR5hggvnL67dWxcnwmcg6RSaWXfsi3z9hdiLI2zOhw9Nx8INHQdJi3X1mzPxUdXezrodqHjzBLxCtmeqb9seiLcfNnjdXSx6vJB1o2z4wuyKTQMX3Hx2bfmIs1sjY4WHFXeJwk3u96nSfYN2eWz6zHGZ7tPeuc4pFe9f73bnpCW4vZwaj_cghQrMtRNTwz1vbmguZ4k2UI9OHwUYCaSB3C7PvkqAA4CgvYQBkWFxXfJ0jns-SYd0GbyVvI4AUpJ5bZKdv1s8rboWWwdtBwe6VtatUNc_F7CArsyg4OIXFYHFwomzpVw96dQxC3fWJvGIG3DK-Gfbe8FErqOrghkN_zEx6Jofly4hWzEghzC6yCHXmJp8Oa5JDao6F2tA9qiI7jTbGfmKt023yN0S1Yf3rsKvHjK91-FpYdRacVblU1eayxsAGUIqd5eo0I6c8LY4yjuof1k_2dF2E9DCLuP_axsT8BYKKiLn9yHor87K46oxzYfKdQHB98Uy_46OiYLaDmF0TobhUfkpK8k9piv1TJ4FOXNAm0zY6KtHqBIW7T7f_PR1nSHKJha3VwiPxEre-alwr52OOqePVFEV7hdN_tifkiFt2mv93OUoX0QaWlUWxX1a06RAYCfQm8rJ26w9bpO1skrpZbpwIf7R9NiTs' [Mon Jan 6 12:42:17 CET 2020] jwk='{"e": "AQAB", "kty": "RSA", "n": "xAr71VJV8rR22xO6rsP6P5gR5hggvnL67dWxcnwmcg6RSaWXfsi3z9hdiLI2zOhw9Nx8INHQdJi3X1mzPxUdXezrodqHjzBLxCtmeqb9seiLcfNnjdXSx6vJB1o2z4wuyKTQMX3Hx2bfmIs1sjY4WHFXeJwk3u96nSfYN2eWz6zHGZ7tPeuc4pFe9f73bnpCW4vZwaj_cghQrMtRNTwz1vbmguZ4k2UI9OHwUYCaSB3C7PvkqAA4CgvYQBkWFxXfJ0jns-SYd0GbyVvI4AUpJ5bZKdv1s8rboWWwdtBwe6VtatUNc_F7CArsyg4OIXFYHFwomzpVw96dQxC3fWJvGIG3DK-Gfbe8FErqOrghkN_zEx6Jofly4hWzEghzC6yCHXmJp8Oa5JDao6F2tA9qiI7jTbGfmKt023yN0S1Yf3rsKvHjK91-FpYdRacVblU1eayxsAGUIqd5eo0I6c8LY4yjuof1k_2dF2E9DCLuP_axsT8BYKKiLn9yHor87K46oxzYfKdQHB98Uy_46OiYLaDmF0TobhUfkpK8k9piv1TJ4FOXNAm0zY6KtHqBIW7T7f_PR1nSHKJha3VwiPxEre-alwr52OOqePVFEV7hdN_tifkiFt2mv93OUoX0QaWlUWxX1a06RAYCfQm8rJ26w9bpO1skrpZbpwIf7R9NiTs"}' [Mon Jan 6 12:42:17 CET 2020] JWK_HEADER='{"alg": "RS256", "jwk": {"e": "AQAB", "kty": "RSA", "n": "xAr71VJV8rR22xO6rsP6P5gR5hggvnL67dWxcnwmcg6RSaWXfsi3z9hdiLI2zOhw9Nx8INHQdJi3X1mzPxUdXezrodqHjzBLxCtmeqb9seiLcfNnjdXSx6vJB1o2z4wuyKTQMX3Hx2bfmIs1sjY4WHFXeJwk3u96nSfYN2eWz6zHGZ7tPeuc4pFe9f73bnpCW4vZwaj_cghQrMtRNTwz1vbmguZ4k2UI9OHwUYCaSB3C7PvkqAA4CgvYQBkWFxXfJ0jns-SYd0GbyVvI4AUpJ5bZKdv1s8rboWWwdtBwe6VtatUNc_F7CArsyg4OIXFYHFwomzpVw96dQxC3fWJvGIG3DK-Gfbe8FErqOrghkN_zEx6Jofly4hWzEghzC6yCHXmJp8Oa5JDao6F2tA9qiI7jTbGfmKt023yN0S1Yf3rsKvHjK91-FpYdRacVblU1eayxsAGUIqd5eo0I6c8LY4yjuof1k_2dF2E9DCLuP_axsT8BYKKiLn9yHor87K46oxzYfKdQHB98Uy_46OiYLaDmF0TobhUfkpK8k9piv1TJ4FOXNAm0zY6KtHqBIW7T7f_PR1nSHKJha3VwiPxEre-alwr52OOqePVFEV7hdN_tifkiFt2mv93OUoX0QaWlUWxX1a06RAYCfQm8rJ26w9bpO1skrpZbpwIf7R9NiTs"}}' [Mon Jan 6 12:42:17 CET 2020] base64 single line. [Mon Jan 6 12:42:17 CET 2020] payload64='eyJpZGVudGlmaWVycyI6IFt7InR5cGUiOiJkbnMiLCJ2YWx1ZSI6IndlYjAxLmdlaHItZWR2LmRlIn1dfQ' [Mon Jan 6 12:42:17 CET 2020] _request_retry_times='1' [Mon Jan 6 12:42:17 CET 2020] Get nonce with HEAD. ACME_NEW_NONCE='https://acme-staging-v02.api.letsencrypt.org/acme/new-nonce' [Mon Jan 6 12:42:17 CET 2020] HEAD [Mon Jan 6 12:42:17 CET 2020] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/new-nonce' [Mon Jan 6 12:42:17 CET 2020] body [Mon Jan 6 12:42:17 CET 2020] _postContentType='application/jose+json' [Mon Jan 6 12:42:17 CET 2020] curl exists=0 [Mon Jan 6 12:42:17 CET 2020] wget exists=127 [Mon Jan 6 12:42:17 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g -I ' [Mon Jan 6 12:42:18 CET 2020] _ret='0' [Mon Jan 6 12:42:18 CET 2020] _headers='HTTP/2 200 server: nginx date: Mon, 06 Jan 2020 11:42:18 GMT cache-control: public, max-age=0, no-cache link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index" replay-nonce: 0001tofhXLFD53iImzkpdGD-4dXj8a6mwPVvFONHTmk9q6Q x-frame-options: DENY strict-transport-security: max-age=604800 ' [Mon Jan 6 12:42:18 CET 2020] _CACHED_NONCE='0001tofhXLFD53iImzkpdGD-4dXj8a6mwPVvFONHTmk9q6Q' [Mon Jan 6 12:42:18 CET 2020] nonce='0001tofhXLFD53iImzkpdGD-4dXj8a6mwPVvFONHTmk9q6Q' [Mon Jan 6 12:42:18 CET 2020] protected='{"nonce": "0001tofhXLFD53iImzkpdGD-4dXj8a6mwPVvFONHTmk9q6Q", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/new-order", "alg": "RS256", "kid": "https://acme-staging-v02.api.letsencrypt.org/acme/acct/11986107"}' [Mon Jan 6 12:42:18 CET 2020] base64 single line. [Mon Jan 6 12:42:18 CET 2020] protected64='eyJub25jZSI6ICIwMDAxdG9maFhMRkQ1M2lJbXprcGRHRC00ZFhqOGE2bXdQVnZGT05IVG1rOXE2USIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9uZXctb3JkZXIiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ' [Mon Jan 6 12:42:18 CET 2020] base64 single line. [Mon Jan 6 12:42:18 CET 2020] _sig_t='tO0FAgeh1zyni7tgqkhcBXdYpXEa182Jcp7P3SrjD9DQ/z4sNKrZMlFEZKcjgjVnHLbE6fcFuUVzbECSVJHZ39ZgJiQUoiJMa2bmCff+f5FQi/K0SWCPQ5rfOZQqWEoxFqlIhea4lcsCMOiYGVbny1FaebgfYy/NfXR7HM+O6OI0wnl8iqbJ86+cXFUdTqwAQrcTaHpfK8jStRvPccXZzuBE0r1JpUAkY47C/noWTsnYF0h41Y8hJBKoSQA4jvtrRmFMteKwQVjPx2ef/1F511TVKequn8SPwzVpNFP8dzNlYE8jB39/NsX0yU/sz5dDj4ljKUCVHR0hmePGanUGpqzo3lfC9IKegMB5L6PrNHC4MZawLWWETTvZfh+LLvuXlt5DUYsD2V4iX5TWF0AwY2zodBaQGoyI1rzMcCOolSRUT3reEZorH+tJvcSCDnmylHv+kMKF0NvD0oM2uDdHaMG9t5NTuw6vaZE7TEgQQfU/82po/rf1s6D71eHawghZ+Safv7Cc3oghNPkRn3nHCPstvP8KjNwPsbsDwKiUI4QQWKvl8KmwtZDnRUlrGtyzJgVKK/sh2zqnu1BA2ORYAnxqrDInz4ztL/cxes7DTAHaEQuNL4CL+h84jXU9FGtHbnCpj3OAQR7AhLr7OiI80J4OEaHOH+rPnW21L3n1yPA=' [Mon Jan 6 12:42:18 CET 2020] sig='tO0FAgeh1zyni7tgqkhcBXdYpXEa182Jcp7P3SrjD9DQ_z4sNKrZMlFEZKcjgjVnHLbE6fcFuUVzbECSVJHZ39ZgJiQUoiJMa2bmCff-f5FQi_K0SWCPQ5rfOZQqWEoxFqlIhea4lcsCMOiYGVbny1FaebgfYy_NfXR7HM-O6OI0wnl8iqbJ86-cXFUdTqwAQrcTaHpfK8jStRvPccXZzuBE0r1JpUAkY47C_noWTsnYF0h41Y8hJBKoSQA4jvtrRmFMteKwQVjPx2ef_1F511TVKequn8SPwzVpNFP8dzNlYE8jB39_NsX0yU_sz5dDj4ljKUCVHR0hmePGanUGpqzo3lfC9IKegMB5L6PrNHC4MZawLWWETTvZfh-LLvuXlt5DUYsD2V4iX5TWF0AwY2zodBaQGoyI1rzMcCOolSRUT3reEZorH-tJvcSCDnmylHv-kMKF0NvD0oM2uDdHaMG9t5NTuw6vaZE7TEgQQfU_82po_rf1s6D71eHawghZ-Safv7Cc3oghNPkRn3nHCPstvP8KjNwPsbsDwKiUI4QQWKvl8KmwtZDnRUlrGtyzJgVKK_sh2zqnu1BA2ORYAnxqrDInz4ztL_cxes7DTAHaEQuNL4CL-h84jXU9FGtHbnCpj3OAQR7AhLr7OiI80J4OEaHOH-rPnW21L3n1yPA' [Mon Jan 6 12:42:18 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAxdG9maFhMRkQ1M2lJbXprcGRHRC00ZFhqOGE2bXdQVnZGT05IVG1rOXE2USIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9uZXctb3JkZXIiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "eyJpZGVudGlmaWVycyI6IFt7InR5cGUiOiJkbnMiLCJ2YWx1ZSI6IndlYjAxLmdlaHItZWR2LmRlIn1dfQ", "signature": "tO0FAgeh1zyni7tgqkhcBXdYpXEa182Jcp7P3SrjD9DQ_z4sNKrZMlFEZKcjgjVnHLbE6fcFuUVzbECSVJHZ39ZgJiQUoiJMa2bmCff-f5FQi_K0SWCPQ5rfOZQqWEoxFqlIhea4lcsCMOiYGVbny1FaebgfYy_NfXR7HM-O6OI0wnl8iqbJ86-cXFUdTqwAQrcTaHpfK8jStRvPccXZzuBE0r1JpUAkY47C_noWTsnYF0h41Y8hJBKoSQA4jvtrRmFMteKwQVjPx2ef_1F511TVKequn8SPwzVpNFP8dzNlYE8jB39_NsX0yU_sz5dDj4ljKUCVHR0hmePGanUGpqzo3lfC9IKegMB5L6PrNHC4MZawLWWETTvZfh-LLvuXlt5DUYsD2V4iX5TWF0AwY2zodBaQGoyI1rzMcCOolSRUT3reEZorH-tJvcSCDnmylHv-kMKF0NvD0oM2uDdHaMG9t5NTuw6vaZE7TEgQQfU_82po_rf1s6D71eHawghZ-Safv7Cc3oghNPkRn3nHCPstvP8KjNwPsbsDwKiUI4QQWKvl8KmwtZDnRUlrGtyzJgVKK_sh2zqnu1BA2ORYAnxqrDInz4ztL_cxes7DTAHaEQuNL4CL-h84jXU9FGtHbnCpj3OAQR7AhLr7OiI80J4OEaHOH-rPnW21L3n1yPA"}' [Mon Jan 6 12:42:18 CET 2020] POST [Mon Jan 6 12:42:18 CET 2020] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/new-order' [Mon Jan 6 12:42:18 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAxdG9maFhMRkQ1M2lJbXprcGRHRC00ZFhqOGE2bXdQVnZGT05IVG1rOXE2USIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9uZXctb3JkZXIiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "eyJpZGVudGlmaWVycyI6IFt7InR5cGUiOiJkbnMiLCJ2YWx1ZSI6IndlYjAxLmdlaHItZWR2LmRlIn1dfQ", "signature": "tO0FAgeh1zyni7tgqkhcBXdYpXEa182Jcp7P3SrjD9DQ_z4sNKrZMlFEZKcjgjVnHLbE6fcFuUVzbECSVJHZ39ZgJiQUoiJMa2bmCff-f5FQi_K0SWCPQ5rfOZQqWEoxFqlIhea4lcsCMOiYGVbny1FaebgfYy_NfXR7HM-O6OI0wnl8iqbJ86-cXFUdTqwAQrcTaHpfK8jStRvPccXZzuBE0r1JpUAkY47C_noWTsnYF0h41Y8hJBKoSQA4jvtrRmFMteKwQVjPx2ef_1F511TVKequn8SPwzVpNFP8dzNlYE8jB39_NsX0yU_sz5dDj4ljKUCVHR0hmePGanUGpqzo3lfC9IKegMB5L6PrNHC4MZawLWWETTvZfh-LLvuXlt5DUYsD2V4iX5TWF0AwY2zodBaQGoyI1rzMcCOolSRUT3reEZorH-tJvcSCDnmylHv-kMKF0NvD0oM2uDdHaMG9t5NTuw6vaZE7TEgQQfU_82po_rf1s6D71eHawghZ-Safv7Cc3oghNPkRn3nHCPstvP8KjNwPsbsDwKiUI4QQWKvl8KmwtZDnRUlrGtyzJgVKK_sh2zqnu1BA2ORYAnxqrDInz4ztL_cxes7DTAHaEQuNL4CL-h84jXU9FGtHbnCpj3OAQR7AhLr7OiI80J4OEaHOH-rPnW21L3n1yPA"}' [Mon Jan 6 12:42:18 CET 2020] _postContentType='application/jose+json' [Mon Jan 6 12:42:18 CET 2020] Http already initialized. [Mon Jan 6 12:42:18 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g ' [Mon Jan 6 12:42:19 CET 2020] _ret='0' [Mon Jan 6 12:42:19 CET 2020] responseHeaders='HTTP/2 201 server: nginx date: Mon, 06 Jan 2020 11:42:19 GMT content-type: application/json content-length: 359 boulder-requester: 11986107 cache-control: public, max-age=0, no-cache link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index" location: https://acme-staging-v02.api.letsencrypt.org/acme/order/11986107/68711985 replay-nonce: 0002_Kk7VzmaLqVJXrh7_QXXbinxlAjRp5lxBJ1Zch7GcV4 x-frame-options: DENY strict-transport-security: max-age=604800 ' [Mon Jan 6 12:42:19 CET 2020] code='201' [Mon Jan 6 12:42:19 CET 2020] original='{ "status": "pending", "expires": "2020-01-13T11:42:19.094459061Z", "identifiers": [ { "type": "dns", "value": "web01.mydomain.de" } ], "authorizations": [ "https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783" ], "finalize": "https://acme-staging-v02.api.letsencrypt.org/acme/finalize/11986107/68711985" }' [Mon Jan 6 12:42:19 CET 2020] response='{"status":"pending","expires":"2020-01-13T11:42:19.094459061Z","identifiers":[{"type":"dns","value":"web01.mydomain.de"}],"authorizations":["https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783"],"finalize":"https://acme-staging-v02.api.letsencrypt.org/acme/finalize/11986107/68711985"}' [Mon Jan 6 12:42:19 CET 2020] Le_LinkOrder='https://acme-staging-v02.api.letsencrypt.org/acme/order/11986107/68711985' [Mon Jan 6 12:42:19 CET 2020] Le_OrderFinalize='https://acme-staging-v02.api.letsencrypt.org/acme/finalize/11986107/68711985' [Mon Jan 6 12:42:19 CET 2020] OK [Mon Jan 6 12:42:19 CET 2020] 8:Le_OrderFinalize='https://acme-staging-v02.api.letsencrypt.org/acme/finalize/11986107/68711985' [Mon Jan 6 12:42:19 CET 2020] _authorizations_seg='https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783' [Mon Jan 6 12:42:19 CET 2020] _authz_url='https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783' [Mon Jan 6 12:42:19 CET 2020] url='https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783' [Mon Jan 6 12:42:19 CET 2020] payload [Mon Jan 6 12:42:19 CET 2020] Use cached jwk for file: /tmp/acme/web01.mydomain.de//ca/acme-staging-v02.api.letsencrypt.org/account.key [Mon Jan 6 12:42:19 CET 2020] base64 single line. [Mon Jan 6 12:42:19 CET 2020] payload64 [Mon Jan 6 12:42:19 CET 2020] _request_retry_times='1' [Mon Jan 6 12:42:19 CET 2020] Use _CACHED_NONCE='0002_Kk7VzmaLqVJXrh7_QXXbinxlAjRp5lxBJ1Zch7GcV4' [Mon Jan 6 12:42:19 CET 2020] nonce='0002_Kk7VzmaLqVJXrh7_QXXbinxlAjRp5lxBJ1Zch7GcV4' [Mon Jan 6 12:42:19 CET 2020] protected='{"nonce": "0002_Kk7VzmaLqVJXrh7_QXXbinxlAjRp5lxBJ1Zch7GcV4", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783", "alg": "RS256", "kid": "https://acme-staging-v02.api.letsencrypt.org/acme/acct/11986107"}' [Mon Jan 6 12:42:19 CET 2020] base64 single line. [Mon Jan 6 12:42:19 CET 2020] protected64='eyJub25jZSI6ICIwMDAyX0trN1Z6bWFMcVZKWHJoN19RWFhiaW54bEFqUnA1bHhCSjFaY2g3R2NWNCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8zMTIwMzc4MyIsICJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xMTk4NjEwNyJ9' [Mon Jan 6 12:42:19 CET 2020] base64 single line. [Mon Jan 6 12:42:19 CET 2020] _sig_t='RX8H0usnGoVcH3G/mgIiPpygz4bjB334Dhn2kq9Y4TOXefRaOwcNemTuvRYFdn85qPyiqN+Z3a2V7vGo0Xa2ApwI2TKkDhQBgFiFmp5qTOLhZdZBAA8XkkwMISWANzrqf9yEtmFLW7FMvHk5GmcmOW/S6X/ItjA5IA7I17wrSqpcV01dGzbrQsDVCSD8oa+3o4iwrwOUnmd0Fh3Zxt4z6XIue7nr9fiz4pGxJRM9iLacMEQ+OsQOPrvaB0nu+lyCXDk99Rf1pE3NHCc3RDyJ5eRKVn0Zjc91ZQuZ+C5m7Lt/DK8ICuiHV2ZrgG6tbVsw61tlcIC0lIsMkxSLNuLyuo0OYc7z2dLcwlJyY1Vfl7zu+TA0m1LovuE6CC4bvvh/GWoKhrK4Mx1CG1BqlLwe20Z0s4Kt/QII8UNbWC3Dv+4h5tCOJ2CPHxnGM5h2ZN8VZNtNp2C6BTJniWCOJBhW8dFI8n+X3+wzC9uuO7qn66GDvxUlC1cpQjLxd3pPNjIWnnAlrXlbwULwiSsqc7aTWuU7a5sCjLTtkrMrHgtaYg7Q1U+InA9zAN0wn3ZkoPGj4lju9DwkbOfnOOaHJ9tt22B/XxZvm6pUiau26jNwqQ+fwI0SSPDKWxiPmwQyEH7plVnrt6IuZ1Tvd2n4WK6QLeo5YrAT5HXlpjM7Uz8Fkz4=' [Mon Jan 6 12:42:19 CET 2020] sig='RX8H0usnGoVcH3G_mgIiPpygz4bjB334Dhn2kq9Y4TOXefRaOwcNemTuvRYFdn85qPyiqN-Z3a2V7vGo0Xa2ApwI2TKkDhQBgFiFmp5qTOLhZdZBAA8XkkwMISWANzrqf9yEtmFLW7FMvHk5GmcmOW_S6X_ItjA5IA7I17wrSqpcV01dGzbrQsDVCSD8oa-3o4iwrwOUnmd0Fh3Zxt4z6XIue7nr9fiz4pGxJRM9iLacMEQ-OsQOPrvaB0nu-lyCXDk99Rf1pE3NHCc3RDyJ5eRKVn0Zjc91ZQuZ-C5m7Lt_DK8ICuiHV2ZrgG6tbVsw61tlcIC0lIsMkxSLNuLyuo0OYc7z2dLcwlJyY1Vfl7zu-TA0m1LovuE6CC4bvvh_GWoKhrK4Mx1CG1BqlLwe20Z0s4Kt_QII8UNbWC3Dv-4h5tCOJ2CPHxnGM5h2ZN8VZNtNp2C6BTJniWCOJBhW8dFI8n-X3-wzC9uuO7qn66GDvxUlC1cpQjLxd3pPNjIWnnAlrXlbwULwiSsqc7aTWuU7a5sCjLTtkrMrHgtaYg7Q1U-InA9zAN0wn3ZkoPGj4lju9DwkbOfnOOaHJ9tt22B_XxZvm6pUiau26jNwqQ-fwI0SSPDKWxiPmwQyEH7plVnrt6IuZ1Tvd2n4WK6QLeo5YrAT5HXlpjM7Uz8Fkz4' [Mon Jan 6 12:42:19 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAyX0trN1Z6bWFMcVZKWHJoN19RWFhiaW54bEFqUnA1bHhCSjFaY2g3R2NWNCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8zMTIwMzc4MyIsICJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xMTk4NjEwNyJ9", "payload": "", "signature": "RX8H0usnGoVcH3G_mgIiPpygz4bjB334Dhn2kq9Y4TOXefRaOwcNemTuvRYFdn85qPyiqN-Z3a2V7vGo0Xa2ApwI2TKkDhQBgFiFmp5qTOLhZdZBAA8XkkwMISWANzrqf9yEtmFLW7FMvHk5GmcmOW_S6X_ItjA5IA7I17wrSqpcV01dGzbrQsDVCSD8oa-3o4iwrwOUnmd0Fh3Zxt4z6XIue7nr9fiz4pGxJRM9iLacMEQ-OsQOPrvaB0nu-lyCXDk99Rf1pE3NHCc3RDyJ5eRKVn0Zjc91ZQuZ-C5m7Lt_DK8ICuiHV2ZrgG6tbVsw61tlcIC0lIsMkxSLNuLyuo0OYc7z2dLcwlJyY1Vfl7zu-TA0m1LovuE6CC4bvvh_GWoKhrK4Mx1CG1BqlLwe20Z0s4Kt_QII8UNbWC3Dv-4h5tCOJ2CPHxnGM5h2ZN8VZNtNp2C6BTJniWCOJBhW8dFI8n-X3-wzC9uuO7qn66GDvxUlC1cpQjLxd3pPNjIWnnAlrXlbwULwiSsqc7aTWuU7a5sCjLTtkrMrHgtaYg7Q1U-InA9zAN0wn3ZkoPGj4lju9DwkbOfnOOaHJ9tt22B_XxZvm6pUiau26jNwqQ-fwI0SSPDKWxiPmwQyEH7plVnrt6IuZ1Tvd2n4WK6QLeo5YrAT5HXlpjM7Uz8Fkz4"}' [Mon Jan 6 12:42:19 CET 2020] POST [Mon Jan 6 12:42:19 CET 2020] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783' [Mon Jan 6 12:42:19 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAyX0trN1Z6bWFMcVZKWHJoN19RWFhiaW54bEFqUnA1bHhCSjFaY2g3R2NWNCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8zMTIwMzc4MyIsICJhbGciOiAiUlMyNTYiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xMTk4NjEwNyJ9", "payload": "", "signature": "RX8H0usnGoVcH3G_mgIiPpygz4bjB334Dhn2kq9Y4TOXefRaOwcNemTuvRYFdn85qPyiqN-Z3a2V7vGo0Xa2ApwI2TKkDhQBgFiFmp5qTOLhZdZBAA8XkkwMISWANzrqf9yEtmFLW7FMvHk5GmcmOW_S6X_ItjA5IA7I17wrSqpcV01dGzbrQsDVCSD8oa-3o4iwrwOUnmd0Fh3Zxt4z6XIue7nr9fiz4pGxJRM9iLacMEQ-OsQOPrvaB0nu-lyCXDk99Rf1pE3NHCc3RDyJ5eRKVn0Zjc91ZQuZ-C5m7Lt_DK8ICuiHV2ZrgG6tbVsw61tlcIC0lIsMkxSLNuLyuo0OYc7z2dLcwlJyY1Vfl7zu-TA0m1LovuE6CC4bvvh_GWoKhrK4Mx1CG1BqlLwe20Z0s4Kt_QII8UNbWC3Dv-4h5tCOJ2CPHxnGM5h2ZN8VZNtNp2C6BTJniWCOJBhW8dFI8n-X3-wzC9uuO7qn66GDvxUlC1cpQjLxd3pPNjIWnnAlrXlbwULwiSsqc7aTWuU7a5sCjLTtkrMrHgtaYg7Q1U-InA9zAN0wn3ZkoPGj4lju9DwkbOfnOOaHJ9tt22B_XxZvm6pUiau26jNwqQ-fwI0SSPDKWxiPmwQyEH7plVnrt6IuZ1Tvd2n4WK6QLeo5YrAT5HXlpjM7Uz8Fkz4"}' [ -
Mon Jan 6 12:42:19 CET 2020] _postContentType='application/jose+json' [Mon Jan 6 12:42:19 CET 2020] Http already initialized. [Mon Jan 6 12:42:19 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g ' [Mon Jan 6 12:42:19 CET 2020] _ret='0' [Mon Jan 6 12:42:19 CET 2020] responseHeaders='HTTP/2 200 server: nginx date: Mon, 06 Jan 2020 11:42:19 GMT content-type: application/json content-length: 813 boulder-requester: 11986107 cache-control: public, max-age=0, no-cache link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index" replay-nonce: 00028-YygcHVDJbShOlf1NCvpr73xSYhidUorM0lhiDvaAk x-frame-options: DENY strict-transport-security: max-age=604800 ' [Mon Jan 6 12:42:19 CET 2020] code='200' [Mon Jan 6 12:42:19 CET 2020] original='{ "identifier": { "type": "dns", "value": "web01.mydomain.de" }, "status": "pending", "expires": "2020-01-13T11:42:19Z", "challenges": [ { "type": "http-01", "status": "pending", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA", "token": "VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI" }, { "type": "dns-01", "status": "pending", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/2UEwkg", "token": "VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI" }, { "type": "tls-alpn-01", "status": "pending", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/xAZ5Bw", "token": "VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI" } ] }' [Mon Jan 6 12:42:19 CET 2020] response='{"identifier":{"type":"dns","value":"web01.mydomain.de"},"status":"pending","expires":"2020-01-13T11:42:19Z","challenges":[{"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"dns-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/2UEwkg","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"tls-alpn-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/xAZ5Bw","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"}]}' [Mon Jan 6 12:42:19 CET 2020] response='{"identifier":{"type":"dns","value":"web01.mydomain.de"},"status":"pending","expires":"2020-01-13T11:42:19Z","challenges":[{"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"dns-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/2UEwkg","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"tls-alpn-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/xAZ5Bw","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"}]}' [Mon Jan 6 12:42:19 CET 2020] _d='web01.mydomain.de' [Mon Jan 6 12:42:19 CET 2020] _authorizations_map='web01.mydomain.de,{"identifier":{"type":"dns","value":"web01.mydomain.de"},"status":"pending","expires":"2020-01-13T11:42:19Z","challenges":[{"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"dns-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/2UEwkg","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"tls-alpn-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/xAZ5Bw","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"}]} ' [Mon Jan 6 12:42:19 CET 2020] d='web01.mydomain.de' [Mon Jan 6 12:42:19 CET 2020] Getting webroot for domain='web01.mydomain.de' [Mon Jan 6 12:42:19 CET 2020] _w='pfSenseacme' [Mon Jan 6 12:42:19 CET 2020] _currentRoot='pfSenseacme' [Mon Jan 6 12:42:19 CET 2020] _is_idn_d='web01.mydomain.de' [Mon Jan 6 12:42:19 CET 2020] _idn_temp [Mon Jan 6 12:42:19 CET 2020] _candindates='web01.mydomain.de,{"identifier":{"type":"dns","value":"web01.mydomain.de"},"status":"pending","expires":"2020-01-13T11:42:19Z","challenges":[{"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"dns-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/2UEwkg","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"tls-alpn-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/xAZ5Bw","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"}]}' [Mon Jan 6 12:42:19 CET 2020] response='{"identifier":{"type":"dns","value":"web01.mydomain.de"},"status":"pending","expires":"2020-01-13T11:42:19Z","challenges":[{"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"dns-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/2UEwkg","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"},{"type":"tls-alpn-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/xAZ5Bw","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"}]}' [Mon Jan 6 12:42:19 CET 2020] base64 single line. [Mon Jan 6 12:42:19 CET 2020] entry='"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"' [Mon Jan 6 12:42:19 CET 2020] token='VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI' [Mon Jan 6 12:42:19 CET 2020] uri='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:19 CET 2020] keyauthorization='VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk' [Mon Jan 6 12:42:20 CET 2020] dvlist='web01.mydomain.de#VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk#https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA#http-01#pfSenseacme' [Mon Jan 6 12:42:20 CET 2020] d [Mon Jan 6 12:42:20 CET 2020] vlist='web01.mydomain.de#VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk#https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA#http-01#pfSenseacme,' [Mon Jan 6 12:42:20 CET 2020] d='web01.mydomain.de' [Mon Jan 6 12:42:20 CET 2020] ok, let's start to verify [Mon Jan 6 12:42:20 CET 2020] Verifying: web01.mydomain.de [Mon Jan 6 12:42:20 CET 2020] d='web01.mydomain.de' [Mon Jan 6 12:42:20 CET 2020] keyauthorization='VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk' [Mon Jan 6 12:42:20 CET 2020] uri='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:20 CET 2020] _currentRoot='pfSenseacme' [Mon Jan 6 12:42:20 CET 2020] h_api='/tmp/acme/web01.mydomain.de//httpapi/pfSenseacme.sh' [Mon Jan 6 12:42:20 CET 2020] Found domain http api file: /tmp/acme/web01.mydomain.de//httpapi/pfSenseacme.sh [Mon Jan 6 12:42:20 CET 2020] pfSenseacme_add exists=0 [Mon Jan 6 12:42:20 CET 2020] Trigger domain validation. [Mon Jan 6 12:42:20 CET 2020] _t_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:20 CET 2020] _t_key_authz='VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk' [Mon Jan 6 12:42:20 CET 2020] _t_vtype='http-01' [Mon Jan 6 12:42:20 CET 2020] url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:20 CET 2020] payload='{}' [Mon Jan 6 12:42:20 CET 2020] Use cached jwk for file: /tmp/acme/web01.mydomain.de//ca/acme-staging-v02.api.letsencrypt.org/account.key [Mon Jan 6 12:42:20 CET 2020] base64 single line. [Mon Jan 6 12:42:20 CET 2020] payload64='e30' [Mon Jan 6 12:42:20 CET 2020] _request_retry_times='1' [Mon Jan 6 12:42:20 CET 2020] Use _CACHED_NONCE='00028-YygcHVDJbShOlf1NCvpr73xSYhidUorM0lhiDvaAk' [Mon Jan 6 12:42:20 CET 2020] nonce='00028-YygcHVDJbShOlf1NCvpr73xSYhidUorM0lhiDvaAk' [Mon Jan 6 12:42:20 CET 2020] protected='{"nonce": "00028-YygcHVDJbShOlf1NCvpr73xSYhidUorM0lhiDvaAk", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA", "alg": "RS256", "kid": "https://acme-staging-v02.api.letsencrypt.org/acme/acct/11986107"}' [Mon Jan 6 12:42:20 CET 2020] base64 single line. [Mon Jan 6 12:42:20 CET 2020] protected64='eyJub25jZSI6ICIwMDAyOC1ZeWdjSFZESmJTaE9sZjFOQ3ZwcjczeFNZaGlkVW9yTTBsaGlEdmFBayIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ' [Mon Jan 6 12:42:20 CET 2020] base64 single line. [Mon Jan 6 12:42:20 CET 2020] _sig_t='t7Nn54DyfEGun1ve0VG8IWGb8/RJkxjG2kAd0xE+cRxikhsq9UPg8SjQx3KtUiZnd2euiV4vaoKlEfc6TQtiduQ/bev6r7ULcVlMmJp09ruS46JAbGTOMSX+ubn1VDh7AWEtdw1EOzMIeInZgEDcbEXYabta0SXUVaQd9HXZyIvIPbRsp67pIPjrYj62308qEN0V/2nyZrLXTUGAkGiynI6k6vsS7u9eSTQCTpAjGn/eVJH8JHW4RVKkh/IH+jh5yQCjemzbF0aIqdUw4abq183AHnjP7uGMronAZ7g1ll8kH7kX2ISKbflGC2hKx0RXy2FCK+2+px+rZS3ksIEkKFC9wppia3KbLJ1iyr7P8QrDQHIDrMESKR5Os/WZnMV79t6FUiiaTW0H8lQGFKZQ+OauXvaJ5F2YT7Hw5oTk6QCyP9AMugOAw3Zn7MvaKDxcgpKeskZhA4EeYS60pPxWlAZYceC1v5kuBeLKb+LdyZwBb0eLSb2FlzRazvJ/YwqYP5CDFsFDlGuQchNaKFIb8QDH05FLbnUvctAA3W2yEofHJTY50zVlNkxEK6acHtdlxVjFSSewttUgKl9IKSHF9yyOaYzi8Qu3GSgTYJZogDgWOocWyUzxLPr2iE3kWOoUE52zALo4dz8csOyW76vZvGKZE1Qcre1+IBR9QeAxfSg=' [Mon Jan 6 12:42:20 CET 2020] sig='t7Nn54DyfEGun1ve0VG8IWGb8_RJkxjG2kAd0xE-cRxikhsq9UPg8SjQx3KtUiZnd2euiV4vaoKlEfc6TQtiduQ_bev6r7ULcVlMmJp09ruS46JAbGTOMSX-ubn1VDh7AWEtdw1EOzMIeInZgEDcbEXYabta0SXUVaQd9HXZyIvIPbRsp67pIPjrYj62308qEN0V_2nyZrLXTUGAkGiynI6k6vsS7u9eSTQCTpAjGn_eVJH8JHW4RVKkh_IH-jh5yQCjemzbF0aIqdUw4abq183AHnjP7uGMronAZ7g1ll8kH7kX2ISKbflGC2hKx0RXy2FCK-2-px-rZS3ksIEkKFC9wppia3KbLJ1iyr7P8QrDQHIDrMESKR5Os_WZnMV79t6FUiiaTW0H8lQGFKZQ-OauXvaJ5F2YT7Hw5oTk6QCyP9AMugOAw3Zn7MvaKDxcgpKeskZhA4EeYS60pPxWlAZYceC1v5kuBeLKb-LdyZwBb0eLSb2FlzRazvJ_YwqYP5CDFsFDlGuQchNaKFIb8QDH05FLbnUvctAA3W2yEofHJTY50zVlNkxEK6acHtdlxVjFSSewttUgKl9IKSHF9yyOaYzi8Qu3GSgTYJZogDgWOocWyUzxLPr2iE3kWOoUE52zALo4dz8csOyW76vZvGKZE1Qcre1-IBR9QeAxfSg' [Mon Jan 6 12:42:20 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAyOC1ZeWdjSFZESmJTaE9sZjFOQ3ZwcjczeFNZaGlkVW9yTTBsaGlEdmFBayIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "e30", "signature": "t7Nn54DyfEGun1ve0VG8IWGb8_RJkxjG2kAd0xE-cRxikhsq9UPg8SjQx3KtUiZnd2euiV4vaoKlEfc6TQtiduQ_bev6r7ULcVlMmJp09ruS46JAbGTOMSX-ubn1VDh7AWEtdw1EOzMIeInZgEDcbEXYabta0SXUVaQd9HXZyIvIPbRsp67pIPjrYj62308qEN0V_2nyZrLXTUGAkGiynI6k6vsS7u9eSTQCTpAjGn_eVJH8JHW4RVKkh_IH-jh5yQCjemzbF0aIqdUw4abq183AHnjP7uGMronAZ7g1ll8kH7kX2ISKbflGC2hKx0RXy2FCK-2-px-rZS3ksIEkKFC9wppia3KbLJ1iyr7P8QrDQHIDrMESKR5Os_WZnMV79t6FUiiaTW0H8lQGFKZQ-OauXvaJ5F2YT7Hw5oTk6QCyP9AMugOAw3Zn7MvaKDxcgpKeskZhA4EeYS60pPxWlAZYceC1v5kuBeLKb-LdyZwBb0eLSb2FlzRazvJ_YwqYP5CDFsFDlGuQchNaKFIb8QDH05FLbnUvctAA3W2yEofHJTY50zVlNkxEK6acHtdlxVjFSSewttUgKl9IKSHF9yyOaYzi8Qu3GSgTYJZogDgWOocWyUzxLPr2iE3kWOoUE52zALo4dz8csOyW76vZvGKZE1Qcre1-IBR9QeAxfSg"}' [Mon Jan 6 12:42:20 CET 2020] POST [Mon Jan 6 12:42:20 CET 2020] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:20 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAyOC1ZeWdjSFZESmJTaE9sZjFOQ3ZwcjczeFNZaGlkVW9yTTBsaGlEdmFBayIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "e30", "signature": "t7Nn54DyfEGun1ve0VG8IWGb8_RJkxjG2kAd0xE-cRxikhsq9UPg8SjQx3KtUiZnd2euiV4vaoKlEfc6TQtiduQ_bev6r7ULcVlMmJp09ruS46JAbGTOMSX-ubn1VDh7AWEtdw1EOzMIeInZgEDcbEXYabta0SXUVaQd9HXZyIvIPbRsp67pIPjrYj62308qEN0V_2nyZrLXTUGAkGiynI6k6vsS7u9eSTQCTpAjGn_eVJH8JHW4RVKkh_IH-jh5yQCjemzbF0aIqdUw4abq183AHnjP7uGMronAZ7g1ll8kH7kX2ISKbflGC2hKx0RXy2FCK-2-px-rZS3ksIEkKFC9wppia3KbLJ1iyr7P8QrDQHIDrMESKR5Os_WZnMV79t6FUiiaTW0H8lQGFKZQ-OauXvaJ5F2YT7Hw5oTk6QCyP9AMugOAw3Zn7MvaKDxcgpKeskZhA4EeYS60pPxWlAZYceC1v5kuBeLKb-LdyZwBb0eLSb2FlzRazvJ_YwqYP5CDFsFDlGuQchNaKFIb8QDH05FLbnUvctAA3W2yEofHJTY50zVlNkxEK6acHtdlxVjFSSewttUgKl9IKSHF9yyOaYzi8Qu3GSgTYJZogDgWOocWyUzxLPr2iE3kWOoUE52zALo4dz8csOyW76vZvGKZE1Qcre1-IBR9QeAxfSg"}' [Mon Jan 6 12:42:20 CET 2020] _postContentType='application/jose+json' [Mon Jan 6 12:42:20 CET 2020] Http already initialized. [Mon Jan 6 12:42:20 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g ' [Mon Jan 6 12:42:20 CET 2020] _ret='0' [Mon Jan 6 12:42:20 CET 2020] responseHeaders='HTTP/2 200 server: nginx date: Mon, 06 Jan 2020 11:42:20 GMT content-type: application/json content-length: 191 boulder-requester: 11986107 cache-control: public, max-age=0, no-cache link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index" link: <https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783>;rel="up" location: https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA replay-nonce: 0001NW3-hay6n0K3_CapnXMSSKFzLEITRAOCnG2Adfxnrmg x-frame-options: DENY strict-transport-security: max-age=604800 ' [Mon Jan 6 12:42:20 CET 2020] code='200' [Mon Jan 6 12:42:20 CET 2020] original='{ "type": "http-01", "status": "pending", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA", "token": "VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI" }' [Mon Jan 6 12:42:20 CET 2020] response='{"type":"http-01","status":"pending","url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI"}' [Mon Jan 6 12:42:20 CET 2020] trigger validation code: 200 [Mon Jan 6 12:42:20 CET 2020] sleep 2 secs to verify [Mon Jan 6 12:42:22 CET 2020] checking [Mon Jan 6 12:42:22 CET 2020] url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:22 CET 2020] payload [Mon Jan 6 12:42:23 CET 2020] Use cached jwk for file: /tmp/acme/web01.mydomain.de//ca/acme-staging-v02.api.letsencrypt.org/account.key [Mon Jan 6 12:42:23 CET 2020] base64 single line. [Mon Jan 6 12:42:23 CET 2020] payload64 [Mon Jan 6 12:42:23 CET 2020] _request_retry_times='1' [Mon Jan 6 12:42:23 CET 2020] Use _CACHED_NONCE='0001NW3-hay6n0K3_CapnXMSSKFzLEITRAOCnG2Adfxnrmg' [Mon Jan 6 12:42:23 CET 2020] nonce='0001NW3-hay6n0K3_CapnXMSSKFzLEITRAOCnG2Adfxnrmg' [Mon Jan 6 12:42:23 CET 2020] protected='{"nonce": "0001NW3-hay6n0K3_CapnXMSSKFzLEITRAOCnG2Adfxnrmg", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA", "alg": "RS256", "kid": "https://acme-staging-v02.api.letsencrypt.org/acme/acct/11986107"}' [Mon Jan 6 12:42:23 CET 2020] base64 single line. [Mon Jan 6 12:42:23 CET 2020] protected64='eyJub25jZSI6ICIwMDAxTlczLWhheTZuMEszX0NhcG5YTVNTS0Z6TEVJVFJBT0NuRzJBZGZ4bnJtZyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ' [Mon Jan 6 12:42:23 CET 2020] base64 single line. [Mon Jan 6 12:42:23 CET 2020] _sig_t='Imp9idxOB1Tb0UVgOkh0AHtePDAhq80PmzO5Dp3ZMAS5RbS87MPI+7+NlRWbXIU/mFXU+LI6n6t51YjYe1JyMhva5m3F5hpc0oXyOX4Y952Bp1ceS7d1u5yRIIh8vvgam/DTWDGnwLkR7Lszw4PPyaFeRZlqQj0QS2lDNO+/o3SiSvRN4R7CkEV7aldsYlnMr0hIPaX0t0AZu940Ms1gEg27ZsjYlNy1TUE5Gx8F/4vV1uudPSSbdQiQGFyp4X0ml5ISWJPUjEvqBtbKy4RuuMjB99Mw9In1CaASR7bnhpl/suD3A1zT3jjy5c7AvTrKBWZZ0ouXEOhfQmdlEo6PWq9xZY/QbsWV1Jf4OAA9obd1wQ7nDTuBCrNVctPBsKGjTdc7VikQK1JcIXlYi+9mhn1ukysvo1iN7NZB3tkQRUp9I/AOX6bAnZe075hbayrUb91Y3q5kYmyN9sdB4Rs9hsY3aIgfBT5uJ1oDi84pDd9zpxjv4WpfGTdA0YpssiS+6blfYDm56m4AqXje0eCW9l04BQ9wBLtxDKd8Tr0jKqi+siSnQPSmh/PI9h7CdysxTf/ynAhIwjJPkhl20OHYu0ShWIqa2r5yQA1mnv+NiIlzwwzGIagL3YWxwAWBxv7BNWKSJUx828yO41awrjs3Cy44CivnFFSzEDcz4ZPcGcs=' [Mon Jan 6 12:42:23 CET 2020] sig='Imp9idxOB1Tb0UVgOkh0AHtePDAhq80PmzO5Dp3ZMAS5RbS87MPI-7-NlRWbXIU_mFXU-LI6n6t51YjYe1JyMhva5m3F5hpc0oXyOX4Y952Bp1ceS7d1u5yRIIh8vvgam_DTWDGnwLkR7Lszw4PPyaFeRZlqQj0QS2lDNO-_o3SiSvRN4R7CkEV7aldsYlnMr0hIPaX0t0AZu940Ms1gEg27ZsjYlNy1TUE5Gx8F_4vV1uudPSSbdQiQGFyp4X0ml5ISWJPUjEvqBtbKy4RuuMjB99Mw9In1CaASR7bnhpl_suD3A1zT3jjy5c7AvTrKBWZZ0ouXEOhfQmdlEo6PWq9xZY_QbsWV1Jf4OAA9obd1wQ7nDTuBCrNVctPBsKGjTdc7VikQK1JcIXlYi-9mhn1ukysvo1iN7NZB3tkQRUp9I_AOX6bAnZe075hbayrUb91Y3q5kYmyN9sdB4Rs9hsY3aIgfBT5uJ1oDi84pDd9zpxjv4WpfGTdA0YpssiS-6blfYDm56m4AqXje0eCW9l04BQ9wBLtxDKd8Tr0jKqi-siSnQPSmh_PI9h7CdysxTf_ynAhIwjJPkhl20OHYu0ShWIqa2r5yQA1mnv-NiIlzwwzGIagL3YWxwAWBxv7BNWKSJUx828yO41awrjs3Cy44CivnFFSzEDcz4ZPcGcs' [Mon Jan 6 12:42:23 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAxTlczLWhheTZuMEszX0NhcG5YTVNTS0Z6TEVJVFJBT0NuRzJBZGZ4bnJtZyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "", "signature": "Imp9idxOB1Tb0UVgOkh0AHtePDAhq80PmzO5Dp3ZMAS5RbS87MPI-7-NlRWbXIU_mFXU-LI6n6t51YjYe1JyMhva5m3F5hpc0oXyOX4Y952Bp1ceS7d1u5yRIIh8vvgam_DTWDGnwLkR7Lszw4PPyaFeRZlqQj0QS2lDNO-_o3SiSvRN4R7CkEV7aldsYlnMr0hIPaX0t0AZu940Ms1gEg27ZsjYlNy1TUE5Gx8F_4vV1uudPSSbdQiQGFyp4X0ml5ISWJPUjEvqBtbKy4RuuMjB99Mw9In1CaASR7bnhpl_suD3A1zT3jjy5c7AvTrKBWZZ0ouXEOhfQmdlEo6PWq9xZY_QbsWV1Jf4OAA9obd1wQ7nDTuBCrNVctPBsKGjTdc7VikQK1JcIXlYi-9mhn1ukysvo1iN7NZB3tkQRUp9I_AOX6bAnZe075hbayrUb91Y3q5kYmyN9sdB4Rs9hsY3aIgfBT5uJ1oDi84pDd9zpxjv4WpfGTdA0YpssiS-6blfYDm56m4AqXje0eCW9l04BQ9wBLtxDKd8Tr0jKqi-siSnQPSmh_PI9h7CdysxTf_ynAhIwjJPkhl20OHYu0ShWIqa2r5yQA1mnv-NiIlzwwzGIagL3YWxwAWBxv7BNWKSJUx828yO41awrjs3Cy44CivnFFSzEDcz4ZPcGcs"}' [Mon Jan 6 12:42:23 CET 2020] POST [Mon Jan 6 12:42:23 CET 2020] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:23 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAxTlczLWhheTZuMEszX0NhcG5YTVNTS0Z6TEVJVFJBT0NuRzJBZGZ4bnJtZyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "", "signature": "Imp9idxOB1Tb0UVgOkh0AHtePDAhq80PmzO5Dp3ZMAS5RbS87MPI-7-NlRWbXIU_mFXU-LI6n6t51YjYe1JyMhva5m3F5hpc0oXyOX4Y952Bp1ceS7d1u5yRIIh8vvgam_DTWDGnwLkR7Lszw4PPyaFeRZlqQj0QS2lDNO-_o3SiSvRN4R7CkEV7aldsYlnMr0hIPaX0t0AZu940Ms1gEg27ZsjYlNy1TUE5Gx8F_4vV1uudPSSbdQiQGFyp4X0ml5ISWJPUjEvqBtbKy4RuuMjB99Mw9In1CaASR7bnhpl_suD3A1zT3jjy5c7AvTrKBWZZ0ouXEOhfQmdlEo6PWq9xZY_QbsWV1Jf4OAA9obd1wQ7nDTuBCrNVctPBsKGjTdc7VikQK1JcIXlYi-9mhn1ukysvo1iN7NZB3tkQRUp9I_AOX6bAnZe075hbayrUb91Y3q5kYmyN9sdB4Rs9hsY3aIgfBT5uJ1oDi84pDd9zpxjv4WpfGTdA0YpssiS-6blfYDm56m4AqXje0eCW9l04BQ9wBLtxDKd8Tr0jKqi-siSnQPSmh_PI9h7CdysxTf_ynAhIwjJPkhl20OHYu0ShWIqa2r5yQA1mnv-NiIlzwwzGIagL3YWxwAWBxv7BNWKSJUx828yO41awrjs3Cy44CivnFFSzEDcz4ZPcGcs"}' [Mon Jan 6 12:42:23 CET 2020] _postContentType='application/jose+json' [Mon Jan 6 12:42:23 CET 2020] Http already initialized. [Mon Jan 6 12:42:23 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g ' [Mon Jan 6 12:42:23 CET 2020] _ret='0' [Mon Jan 6 12:42:23 CET 2020] responseHeaders='HTTP/2 200 server: nginx date: Mon, 06 Jan 2020 11:42:23 GMT content-type: application/json content-length: 980 boulder-requester: 11986107 cache-control: public, max-age=0, no-cache link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index" link: <https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/31203783>;rel="up" location: https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA replay-nonce: 0002woICyan05HDK5kz8xuWMPEYxzsQzoENVlIKBg2ES258 x-frame-options: DENY strict-transport-security: max-age=604800 ' [Mon Jan 6 12:42:23 CET 2020] code='200' [Mon Jan 6 12:42:23 CET 2020] original='{ "type": "http-01", "status": "invalid", "error": { "type": "urn:ietf:params:acme:error:unauthorized", "detail": "Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: \"\u003c!DOCTYPE HTML PUBLIC \\\"-//IETF//DTD HTML 2.0//EN\\\"\u003e\\n\u003chtml\u003e\u003chead\u003e\\n\u003ctitle\u003e401 Unauthorized\u003c/title\u003e\\n\u003c/head\u003e\u003cbody\u003e\\n\u003ch1\u003eUnauthorized\u003c/\"", "status": 403 }, "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA", "token": "VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI", "validationRecord": [ { "url": "http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI", "hostname": "web01.mydomain.de", "port": "80", "addressesResolved": [ "37.228.164.207" ], "addressUsed": "37.228.164.207" } ] }' [Mon Jan 6 12:42:23 CET 2020] response='{"type":"http-01","status":"invalid","error":{"type":"urn:ietf:params:acme:error:unauthorized","detail":"Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: \"\u003c!DOCTYPE HTML PUBLIC \\\"-//IETF//DTD HTML 2.0//EN\\\"\u003e\\n\u003chtml\u003e\u003chead\u003e\\n\u003ctitle\u003e401 Unauthorized\u003c/title\u003e\\n\u003c/head\u003e\u003cbody\u003e\\n\u003ch1\u003eUnauthorized\u003c/\"","status": 403},"url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI","validationRecord":[{"url":"http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI","hostname":"web01.mydomain.de","port":"80","addressesResolved":["37.228.164.207"],"addressUsed":"37.228.164.207"}]}' [Mon Jan 6 12:42:23 CET 2020] original='{"type":"http-01","status":"invalid","error":{"type":"urn:ietf:params:acme:error:unauthorized","detail":"Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: \"\u003c!DOCTYPE HTML PUBLIC \\\"-//IETF//DTD HTML 2.0//EN\\\"\u003e\\n\u003chtml\u003e\u003chead\u003e\\n\u003ctitle\u003e401 Unauthorized\u003c/title\u003e\\n\u003c/head\u003e\u003cbody\u003e\\n\u003ch1\u003eUnauthorized\u003c/\"","status": 403},"url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI","validationRecord":[{"url":"http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI","hostname":"web01.mydomain.de","port":"80","addressesResolved":["37.228.164.207"],"addressUsed":"37.228.164.207"}]}' [Mon Jan 6 12:42:23 CET 2020] response='{"type":"http-01","status":"invalid","error":{"type":"urn:ietf:params:acme:error:unauthorized","detail":"Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: \"\u003c!DOCTYPE HTML PUBLIC \\\"-//IETF//DTD HTML 2.0//EN\\\"\u003e\\n\u003chtml\u003e\u003chead\u003e\\n\u003ctitle\u003e401 Unauthorized\u003c/title\u003e\\n\u003c/head\u003e\u003cbody\u003e\\n\u003ch1\u003eUnauthorized\u003c/\"","status": 403},"url":"https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA","token":"VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI","validationRecord":[{"url":"http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI","hostname":"web01.mydomain.de","port":"80","addressesResolved":["37.228.164.207"],"addressUsed":"37.228.164.207"}]}' [Mon Jan 6 12:42:23 CET 2020] error='"error":{"type":"urn:ietf:params:acme:error:unauthorized","detail":"Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: ' [Mon Jan 6 12:42:23 CET 2020] errordetail='Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: ' [Mon Jan 6 12:42:23 CET 2020] web01.mydomain.de:Verify error:Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI [37.228.164.207]: [Mon Jan 6 12:42:23 CET 2020] h_api='/tmp/acme/web01.mydomain.de//httpapi/pfSenseacme.sh' [Mon Jan 6 12:42:23 CET 2020] Found domain http api file: /tmp/acme/web01.mydomain.de//httpapi/pfSenseacme.sh [Mon Jan 6 12:42:23 CET 2020] pfSenseacme_rm exists=0 [Mon Jan 6 12:42:23 CET 2020] pid [Mon Jan 6 12:42:23 CET 2020] No need to restore nginx, skip. [Mon Jan 6 12:42:23 CET 2020] _clearupdns [Mon Jan 6 12:42:23 CET 2020] dns_entries [Mon Jan 6 12:42:23 CET 2020] skip dns. [Mon Jan 6 12:42:23 CET 2020] _on_issue_err [Mon Jan 6 12:42:23 CET 2020] Please check log file for more details: /tmp/acme/web01.mydomain.de/acme_issuecert.log [Mon Jan 6 12:42:23 CET 2020] _chk_vlist='web01.mydomain.de#VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk#https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA#http-01#pfSenseacme,' [Mon Jan 6 12:42:23 CET 2020] start to deactivate authz [Mon Jan 6 12:42:23 CET 2020] Trigger domain validation. [Mon Jan 6 12:42:23 CET 2020] _t_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:23 CET 2020] _t_key_authz='VMrh9qu3JYFINCwq7GPZHAhzZDyTB_oz8d5XvmIBJVI.mCpEup0Wf6l93sNp46OkkLeiGEXLa4fwuQoyYU3DWTk' [Mon Jan 6 12:42:23 CET 2020] _t_vtype [Mon Jan 6 12:42:23 CET 2020] url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:23 CET 2020] payload='{}' [Mon Jan 6 12:42:23 CET 2020] Use cached jwk for file: /tmp/acme/web01.mydomain.de//ca/acme-staging-v02.api.letsencrypt.org/account.key [Mon Jan 6 12:42:23 CET 2020] base64 single line. [Mon Jan 6 12:42:23 CET 2020] payload64='e30' [Mon Jan 6 12:42:23 CET 2020] _request_retry_times='1' [Mon Jan 6 12:42:23 CET 2020] Use _CACHED_NONCE='0002woICyan05HDK5kz8xuWMPEYxzsQzoENVlIKBg2ES258' [Mon Jan 6 12:42:23 CET 2020] nonce='0002woICyan05HDK5kz8xuWMPEYxzsQzoENVlIKBg2ES258' [Mon Jan 6 12:42:23 CET 2020] protected='{"nonce": "0002woICyan05HDK5kz8xuWMPEYxzsQzoENVlIKBg2ES258", "url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA", "alg": "RS256", "kid": "https://acme-staging-v02.api.letsencrypt.org/acme/acct/11986107"}' [Mon Jan 6 12:42:23 CET 2020] base64 single line. [Mon Jan 6 12:42:23 CET 2020] protected64='eyJub25jZSI6ICIwMDAyd29JQ3lhbjA1SERLNWt6OHh1V01QRVl4enNRem9FTlZsSUtCZzJFUzI1OCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ' [Mon Jan 6 12:42:23 CET 2020] base64 single line. [Mon Jan 6 12:42:23 CET 2020] _sig_t='Lb/CSWFLBfO6N+avojiyDQTzqe/BZM2MSZwEz0faCXdzy6SYx6uFHww2rw+1euUexXSK3X4oV3gK3+66p+qUZ0jXXytRUxtERLmfN+LObu2Xw09jQ5q5kcNDQFsaguG0rBKKQYslF1AvIwIZq6UTVHjEL1rA413gVn9b9PYw4KcmKXGBNI8qWV6Cu3vxjO9XnFrD86eVUR+AWhGmsx0mMjLPcPnGqF4F6pb7VL0u+jQd5T6kOQH2uiL0X4QouxtWXTm6BqgA2y4Su1+DN7YI65aunnESWpmnK+meeQfUlE7vO8FHUVHQus6yBUAyr87o7iB0JTjVCmDrH3VVWUchxinBeF1Szz7uNOD2bhVoDCjwPdbX/BVwve0EigWsFiWnerbo8F0rwZ3feixnTPUvJjKdgqWq3dDgT9hKIsGkWhNsqL7ZJ2htEvtjp1OqJcdFS5HaWd/2EoDnffCcFwXyUAzZ4XzJl1hnKXlh1+g6CGIVGOLgAlM5MimRWH/MeDLgAkjenjJBkCEW1NDH0zQ3bJ0KFFE0H/uvkFwDKZBhRGO6uyZUmJlPpzvvmEKiuJ0W6l/kusCynWYLq5eAGLVs2SOATEluN4kHasNS4WD546Z6Ntd+/qqgZRW14QPOAYIFn1t3Y1tCKsmb4B510qYNNaPBv0OErrG3BwVgLp5xUpQ=' [Mon Jan 6 12:42:23 CET 2020] sig='Lb_CSWFLBfO6N-avojiyDQTzqe_BZM2MSZwEz0faCXdzy6SYx6uFHww2rw-1euUexXSK3X4oV3gK3-66p-qUZ0jXXytRUxtERLmfN-LObu2Xw09jQ5q5kcNDQFsaguG0rBKKQYslF1AvIwIZq6UTVHjEL1rA413gVn9b9PYw4KcmKXGBNI8qWV6Cu3vxjO9XnFrD86eVUR-AWhGmsx0mMjLPcPnGqF4F6pb7VL0u-jQd5T6kOQH2uiL0X4QouxtWXTm6BqgA2y4Su1-DN7YI65aunnESWpmnK-meeQfUlE7vO8FHUVHQus6yBUAyr87o7iB0JTjVCmDrH3VVWUchxinBeF1Szz7uNOD2bhVoDCjwPdbX_BVwve0EigWsFiWnerbo8F0rwZ3feixnTPUvJjKdgqWq3dDgT9hKIsGkWhNsqL7ZJ2htEvtjp1OqJcdFS5HaWd_2EoDnffCcFwXyUAzZ4XzJl1hnKXlh1-g6CGIVGOLgAlM5MimRWH_MeDLgAkjenjJBkCEW1NDH0zQ3bJ0KFFE0H_uvkFwDKZBhRGO6uyZUmJlPpzvvmEKiuJ0W6l_kusCynWYLq5eAGLVs2SOATEluN4kHasNS4WD546Z6Ntd-_qqgZRW14QPOAYIFn1t3Y1tCKsmb4B510qYNNaPBv0OErrG3BwVgLp5xUpQ' [Mon Jan 6 12:42:23 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAyd29JQ3lhbjA1SERLNWt6OHh1V01QRVl4enNRem9FTlZsSUtCZzJFUzI1OCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "e30", "signature": "Lb_CSWFLBfO6N-avojiyDQTzqe_BZM2MSZwEz0faCXdzy6SYx6uFHww2rw-1euUexXSK3X4oV3gK3-66p-qUZ0jXXytRUxtERLmfN-LObu2Xw09jQ5q5kcNDQFsaguG0rBKKQYslF1AvIwIZq6UTVHjEL1rA413gVn9b9PYw4KcmKXGBNI8qWV6Cu3vxjO9XnFrD86eVUR-AWhGmsx0mMjLPcPnGqF4F6pb7VL0u-jQd5T6kOQH2uiL0X4QouxtWXTm6BqgA2y4Su1-DN7YI65aunnESWpmnK-meeQfUlE7vO8FHUVHQus6yBUAyr87o7iB0JTjVCmDrH3VVWUchxinBeF1Szz7uNOD2bhVoDCjwPdbX_BVwve0EigWsFiWnerbo8F0rwZ3feixnTPUvJjKdgqWq3dDgT9hKIsGkWhNsqL7ZJ2htEvtjp1OqJcdFS5HaWd_2EoDnffCcFwXyUAzZ4XzJl1hnKXlh1-g6CGIVGOLgAlM5MimRWH_MeDLgAkjenjJBkCEW1NDH0zQ3bJ0KFFE0H_uvkFwDKZBhRGO6uyZUmJlPpzvvmEKiuJ0W6l_kusCynWYLq5eAGLVs2SOATEluN4kHasNS4WD546Z6Ntd-_qqgZRW14QPOAYIFn1t3Y1tCKsmb4B510qYNNaPBv0OErrG3BwVgLp5xUpQ"}' [Mon Jan 6 12:42:23 CET 2020] POST [Mon Jan 6 12:42:23 CET 2020] _post_url='https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/31203783/0zAeqA' [Mon Jan 6 12:42:23 CET 2020] body='{"protected": "eyJub25jZSI6ICIwMDAyd29JQ3lhbjA1SERLNWt6OHh1V01QRVl4enNRem9FTlZsSUtCZzJFUzI1OCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8zMTIwMzc4My8wekFlcUEiLCAiYWxnIjogIlJTMjU2IiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTE5ODYxMDcifQ", "payload": "e30", "signature": "Lb_CSWFLBfO6N-avojiyDQTzqe_BZM2MSZwEz0faCXdzy6SYx6uFHww2rw-1euUexXSK3X4oV3gK3-66p-qUZ0jXXytRUxtERLmfN-LObu2Xw09jQ5q5kcNDQFsaguG0rBKKQYslF1AvIwIZq6UTVHjEL1rA413gVn9b9PYw4KcmKXGBNI8qWV6Cu3vxjO9XnFrD86eVUR-AWhGmsx0mMjLPcPnGqF4F6pb7VL0u-jQd5T6kOQH2uiL0X4QouxtWXTm6BqgA2y4Su1-DN7YI65aunnESWpmnK-meeQfUlE7vO8FHUVHQus6yBUAyr87o7iB0JTjVCmDrH3VVWUchxinBeF1Szz7uNOD2bhVoDCjwPdbX_BVwve0EigWsFiWnerbo8F0rwZ3feixnTPUvJjKdgqWq3dDgT9hKIsGkWhNsqL7ZJ2htEvtjp1OqJcdFS5HaWd_2EoDnffCcFwXyUAzZ4XzJl1hnKXlh1-g6CGIVGOLgAlM5MimRWH_MeDLgAkjenjJBkCEW1NDH0zQ3bJ0KFFE0H_uvkFwDKZBhRGO6uyZUmJlPpzvvmEKiuJ0W6l_kusCynWYLq5eAGLVs2SOATEluN4kHasNS4WD546Z6Ntd-_qqgZRW14QPOAYIFn1t3Y1tCKsmb4B510qYNNaPBv0OErrG3BwVgLp5xUpQ"}' [Mon Jan 6 12:42:23 CET 2020] _postContentType='application/jose+json' [Mon Jan 6 12:42:23 CET 2020] Http already initialized. [Mon Jan 6 12:42:23 CET 2020] _CURL='curl -L --silent --dump-header /tmp/acme/web01.mydomain.de//http.header -g ' [Mon Jan 6 12:42:24 CET 2020] _ret='0' [Mon Jan 6 12:42:24 CET 2020] responseHeaders='HTTP/2 400 server: nginx date: Mon, 06 Jan 2020 11:42:24 GMT content-type: application/problem+json content-length: 144 boulder-requester: 11986107 cache-control: public, max-age=0, no-cache link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index" replay-nonce: 0001bFLwIvqvO9BXuRLBYHCa0EdhRlBKW8LkKmzabk9eMfs ' [Mon Jan 6 12:42:24 CET 2020] code='400' [Mon Jan 6 12:42:24 CET 2020] original='{ "type": "urn:ietf:params:acme:error:malformed", "detail": "Unable to update challenge :: authorization must be pending", "status": 400 }' [Mon Jan 6 12:42:24 CET 2020] response='{ "type": "urn:ietf:params:acme:error:malformed", "detail": "Unable to update challenge :: authorization must be pending", "status": 400 }'Hat noch jemand eine Idee für mich?
-
Jetzt bin ich weiter gekommen, jedoch nocht nicht zu 100% erfolgreich.
Der Pfad zum FTP-Verzeichnis mus absolut nicht relativ eingegeben werden. Ich habe diesen nun auf:
/home/webftp/.well-known/acme-challenge/gesetzt. Und nun legt der ACME-Dienst dort auch Files ab :-) Die Meldung beim Klick auf "Issiue/Renew":
web01.mydomain.de Renewing certificate account: Test server: letsencrypt-staging-2 /usr/local/pkg/acme/acme.sh --issue -d 'web01.mydomain.de' --webroot pfSenseacme --home '/tmp/acme/web01.mydomain.de/' --accountconf '/tmp/acme/web01.mydomain.de/accountconf.conf' --force --reloadCmd '/tmp/acme/web01.mydomain.de/reloadcmd.sh' --log-level 3 --log '/tmp/acme/web01.mydomain.de/acme_issuecert.log' Array ( [path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/ [ftpserver] => sftp://192.168.24.7 [username] => webftp [password] => ******* [folder] => /home/webftp/.well-known/acme-challenge/ ) [Mon Jan 6 14:18:03 CET 2020] Single domain='web01.mydomain.de' [Mon Jan 6 14:18:03 CET 2020] Getting domain auth token for each domain [Mon Jan 6 14:18:06 CET 2020] Getting webroot for domain='web01.mydomain.de' [Mon Jan 6 14:18:06 CET 2020] Verifying: web01.mydomain.de [Mon Jan 6 14:18:06 CET 2020] Found domain http api file: /tmp/acme/web01.mydomain.de//httpapi/pfSenseacme.sh challenge_response_put web01.mydomain.de, web01.mydomain.de FOUND domainitemFTP [Mon Jan 6 14:18:10 CET 2020] Found domain http api file: /tmp/acme/web01.mydomain.de//httpapi/pfSenseacme.sh [Mon Jan 6 14:18:10 CET 2020] web01.mydomain.de:Verify error:Invalid response from http://web01.mydomain.de/.well-known/acme-challenge/dU2GkTzKFQEL5_s3ZlFIQu3o31hjLnMLe9hzCaGWqbA [10.20.30.40]: [Mon Jan 6 14:18:10 CET 2020] Please check log file for more details: /tmp/acme/web01.mydomain.de/acme_issuecert.logDen hier ausgegeben Pfad:
http://web01.mydomain.de/.well-known/acme-challengekann ich sowohl von intern wie auch von extern aufrufen und lande im richtigen Verzeichnis und sehe die Files für den acme-challenge.
Was bedeutet dieser Fehler genau?
-
Konnte das Problem lösen. Siehe:
https://forum.netgate.com/topic/149458/acme-with-webroot-ftp-not-work/7