Communicating between subnets fails
-
Yeah that is simple... Your default lan rules of any any would allow lan to talk to any connected vlan.
You create a rule on your other vlans to block access to rfc1918.. Done!!
example
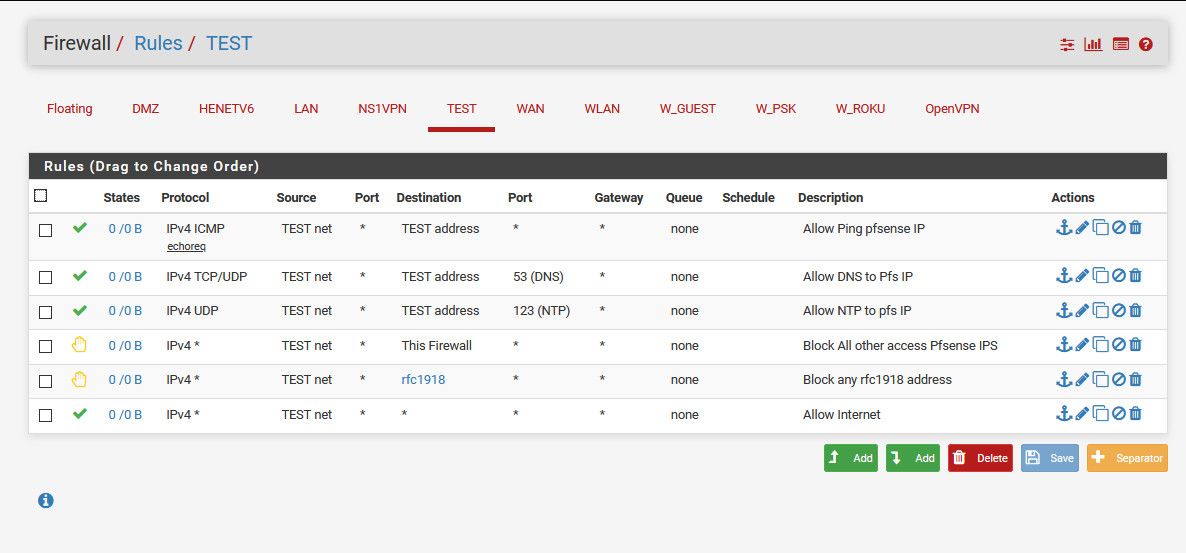
That vlan can not talk to lan or any other vlans you might have, but can talk to internet.. .And lan can talk to it.
-
@johnpoz Already did all of that a while ago but the thing is that I policy route that LAN's 'any any' rule to go through a VPN gateway. That being said, I added a Pass rule for those subnets without a policy route before that 'any any' which didn't solve the problem. Also, saw this online:
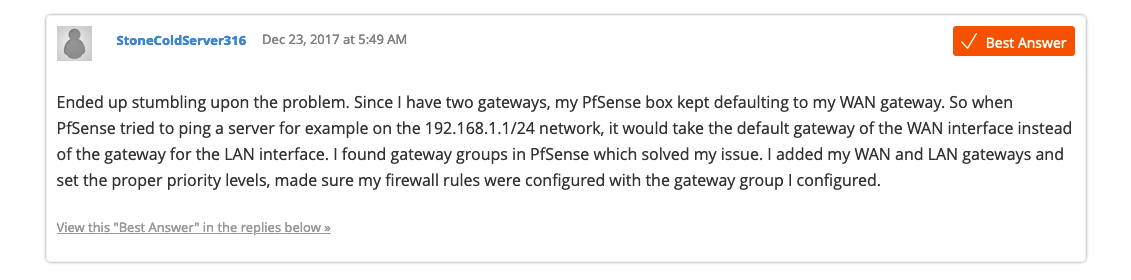
In his post he describes the same problem I have.
Edit: I have the exact same rules like in your screenshot haha, but with the VPN policy route
-
Then put a rule above the rule you policy route out allowing access to the vpn..
as to that post... Yeah its nonsense... A locally attached route is more defined and would be used vs default route... So that is not at all correct. Nor is there a "lan" gateway at all.. Once you put a gateway on an interface it becomes a "wan" to pfsense... If you have networks via downstream networks then sure you could create a gateway for routing - but that you would want to access via a transit network, not over you lan network where you have clients or you open up a whole new can of worms with asymmetrical routing issues if talking to hosts on that lan, etc...
But what causes problems is when you policy route and FORCE traffic out a gateway... Which doesn't allow pfsense to use its normal routing.
-
@johnpoz I did but still couldn't ping the other interface's net. Wait...I'll post a screenshot
-
And as already mentioned - you have to contend with any sort of firewall running on the actual hosts in the other network.
Out of the box windows does not answer ping from networks other than its own local one for example.
-
@johnpoz haha LOL...don't exaggerate, I'm not that newb of course I checked that it's on 'Private' mode. Also, I mentioned that NAT fixed it which of course proves that the firewall is the issue to fix
-
@techtester-m said in Communicating between subnets fails:
I checked that it's on 'Private' mode.
Yeah so - that still blocks freaking pings out of the box!! From non local network.
No source freaking nat is not a FIX its a HACK!! do what you want I am just getting fed up trying to fix stupid... Source natting your traffic into your own network to circumvent the hosts firewall is not a fix!!!
-
@johnpoz LOL you're right....my bad. I keep forgetting it's different subnets! So, if I set that rule you mentioned, above the 'any any (VPN)' the issue would remain only with Windows firewall?
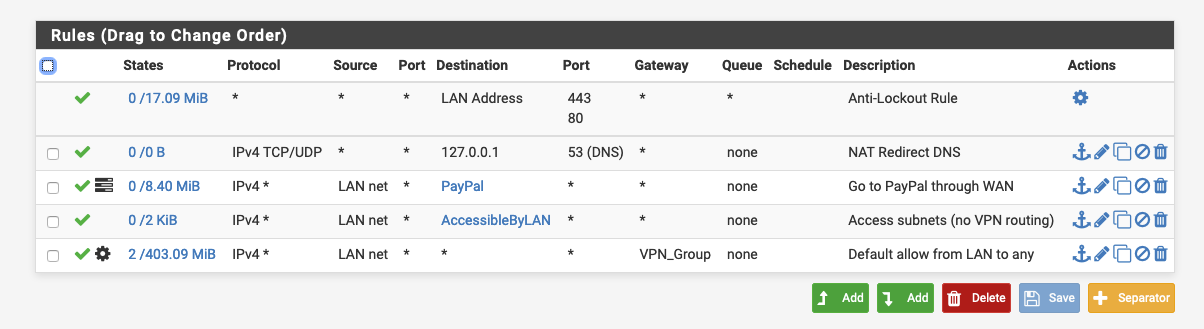
-
Not sure what you have in that alias, but yes that rule would use local routing to get to that alias vs shoving it out your vpn_group gateway.
BTW this is all gone over in the docs for policy routing
https://docs.netgate.com/pfsense/en/latest/book/multiwan/policy-routing-configuration.htmlBypassing Policy Routing
If there are other local interfaces, VPNs, MPLS interfaces, or traffic that must otherwise follow the system routing table, then that traffic must be configured to bypass policy routing. This is simple to do by making a rule to match the traffic in question and then placing that rule above any rules that have a gateway configured, because the first rule to match is the one that is used.
-
@johnpoz That alias contains all the other subnets. So basically if I can ping an interface's address I should also ping or have access to its net, right? Meaning that the only remaining issue would be in the Windows firewall, right?
Silly me haha, the NAT changed the source address to resemble the other subnet net which is kinda hacking the issue rather then solving it.
-
Yes if you can ping the other vlans IP address you should be fine. The traffic would need to be allowed by the dest devices firewall. And pfsense would need have to connectivity to this device.. simple way to troubleshoot is validate via sniff that pfsense is actually sending the traffic out that vlan interface... If it is, and its to the correct mac - then that screams device firewall blocking the traffic.
Only time you might "need" to source nat would be if say the device on this other vlan too stupid to allow for a gateway to even be set... Some IP cameras are like that for example - in that case the only way to talk to that other device from a different network is to source nat and make the traffic look like its local traffic to that device.
-
@johnpoz Thanks! You're the best! Wait...can you save me the Googling and help me with configuring Windows firewall to allow incoming connections from other subnets but never from outside the home network?
-
No problem - other scenario where you might "need" to source nat... But again its a "hack"!! is when the dest device uses a different gateway than pfsense.. Your setup in such a scenario is already borked to be honest ;)
If your source natting - your working around some sort of problem to be sure... Would/Should always be the last possible method used to work around the issue.. But it can be used if there is no other way to correctly route the traffic.
Example you nat to the internet.. This not actually the correct solution to the problem of not enough IPs.. The correct solution is have an IP for each device - nat is not a solution its a hack to get around a problem.
edit: Yet another example of where nat is used where its a "hack" ;) Company A with IP range X, buys company B that also uses IP range X... Now as a hack to get them talking to each other you could nat.. The correct solution is to change either A or B ip scheme to not overlap the other company..
-
@johnpoz I understand about NAT and all the devices on the network use the default gateway which is their net's interface address of course.
-
Then yeah your good to go.. Either just turn off the host firewall... I find them to be more pain then they are worth on a local secure network that I control and firewall at the edge of the network.. The only time they make any sense is if the local network they are on is hostile.. Or your not actually in control of the network be it hostile or not and want to be able to control what can talk to your device.
My local devices do not run their host firewalls. Since I control the whole network, and all the applications that get installed and run on all the devices. And firewall at the edge - devices in vlan X can not talk to vlan Y except for the ports I allow and need. What would be the point of also having to manage that traffic at the device?
-
@johnpoz Some devices are not used by me or controlled by me and other family members don't understand computers/IT as I do and so they can download malware, click on ads, spam emails etc. I don't wanna mess with their hosts' firewall or antivirus. They also use Windows while I use Mac OS which is more secure.
Anyway, do you know where on the Windows firewall I allow other subnets to connect? Is it exactly like "remote desktop"? I'm searching the web for the solution anyway....
-
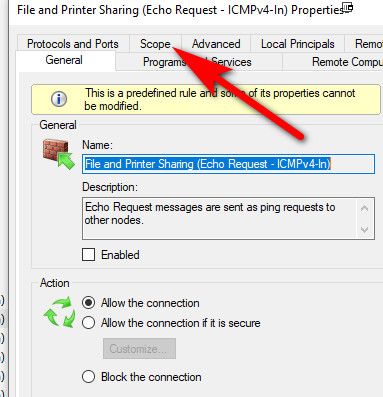
Do want to allow ping only?
Its listed under file and print sharing for some crazy reason - icmpv4 in, echo request.. Allow the ip ranges you want, ie your lan network under scope, or just say any..
As to messing with family computers.. That some "user" manages and runs shit on... Oh look I won an IPad if I click here because Im the millionth vistor ;)
Yeah put that at on their own isolated vlan that can not talk your stuff, simple solution there for sure ;) Treat that whole segment as just plain hostile..
-
@johnpoz said in Communicating between subnets fails:
Do want to allow ping only?
Not just ping but any access (TCP/UDP), accessing shared folders etc.
@johnpoz said in Communicating between subnets fails:
Yeah put that at on their own isolated vlan that can not talk your stuff, simple solution there for sure ;) Treat that whole segment as just plain hostile..
That's what I do anyway. I isolate the 'core' of the network and the important stuff including my network but still don't want their computers to be completely vulnerable even at the local level where an antivirus might stop some malware.
-
@techtester-m said in Communicating between subnets fails:
Not just ping but any access (TCP/UDP), accessing shared folders etc.
Well then either turn if off.. Or you have to allow every specific protocol you want to allow ;) Or create an any rule, which if you have a any rule - why is it even on ;)
If your going to allow access to every service that box is running, why would you need to run firewall on the host sucking up resources, slowing down the connections.
You need to run a firewall when you want to say allow IP X, but block IP Y from talking to Z service. If your going to allow everything to talk to whatever service is running - what is the point of the firewall?
-
@johnpoz Sorry but please bare with me I f*ing hate Windows. The PC is running Windows 10 and I can't find it lol
How do I get to these properties? Every thing I click keeps sending me to this window or a similar irrelevant one...