losing OpenVPN connection every 20 - 120 seconds
-
@akkiz said in losing OpenVPN connection every 20 - 120 seconds:
@akkiz couldnt see any traffic coming out of OPT1 port (which is assigned ovp3) problem still persist
You do not generally need to assign a VPN connection to an interface.. (not sure if this is the case when transferring all traffic to a "VPN service".
Is it possible to remove this "assignment" to test?
-
It shouldn't make any difference here but it's easy to test so...
I notice it's setting the send and receive buffers everytime. You might try removing that setting so it just uses the default values.
Connecting but not passing traffic really looks like a compression mismatch though. If you can connect using those settings from a host client instead of pfSense then we will at least have a known set of connection settings.
-
@stephenw10 let me set up and see but through their app it works fine for some countries but for some countries it connects but no traffic flows since ISP is blocking or throttling vpn connection here
-
@chpalmer it didnt make any difference
-
Ok so no connection logs from a phone app, you're going to need to connect from a PC to get that I think.
However the fact it connects and doesn't pass traffic to some servers seems exactly like what you're seeing in pfSense. It could just be your ISP blocking the traffic.
Steve
-
@stephenw10 yes i just came to know here they are blocking open vpn protocol but ipsec is open but i cant find any write up for it do u know how to configure ipsec in pf sense
-
@akkiz because i tried open vpn on my work pc it connects fine but no internet flows so i think my isp blocks open vpn from ipsec works fine here
-
@stephenw10 through phone app it works fine since it had all 3 protocols see attached pic
-
to be clear.
its not working using their equipment + pfsense and openvpn
but its working over wireless using the same equipment using the app + openvpn?
-
That looks like a Windows application. Are there logs there showing how it is connecting?
You might try using their TCP setting instead, if you know what those are.
IPSec is far more likely to be blocked, on the standard ports at least.
Steve
-
@bcruze express vpn app works fine in android and in windows laptop but open vpn does not work in pf sense or in windows ,but ipsec is working in windows
-
@stephenw10 my goal is to create 2 wireless access point one regular internet one vpn internet,so i can switch between the 2 networks
-
the internet speed is nearly same as before vpn
-
So OpenVPN does not work from Windows using either UDP or TCP?
-
@stephenw10 wait a sec let me try
-
@stephenw10 log.txt
it connects to server but no traffic flows my vpn provider has onlu udp i guess didnt see tcp
log.txt -
It shows TCP on the phone app.
If you see no traffic when connecting from Windows then there's no point trying to get pfSense to connect IMO. Something is blocking that traffic.
Steve
-
hello guys why am i able to use open vpn client on ddwrt does ddwrt software connects in a different manner than pf sense ??? i attached logs of ddwrt connection if you guys see something in the logs..
Client: CONNECTED SUCCESSLocal Address: 10.71.0.54
Remote Address: 10.71.0.53Status
VPN Client StatsTUN/TAP read bytes
28128246
TUN/TAP write bytes
84819766
TCP/UDP read bytes
91726426
TCP/UDP write bytes
30626151
Auth read bytes
84819766
pre-compress bytes
0
post-compress bytes
0
pre-decompress bytes
0
post-decompress bytes
0Log
Clientlog:
20200129 07:36:09 W WARNING: Using --management on a TCP port WITHOUT passwords is STRONGLY discouraged and considered insecure
20200129 07:36:09 W WARNING: --keysize is DEPRECATED and will be removed in OpenVPN 2.6
20200129 07:36:09 W WARNING: file '/tmp/openvpncl/client.key' is group or others accessible
20200129 07:36:09 W WARNING: file '/tmp/openvpncl/ta.key' is group or others accessible
20200129 07:36:09 W WARNING: file '/tmp/openvpncl/credentials' is group or others accessible
20200129 07:36:09 I OpenVPN 2.4.8 arm-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Jan 23 2020
20200129 07:36:09 I library versions: OpenSSL 1.1.1d 10 Sep 2019 LZO 2.09
20200129 07:36:09 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:16
20200129 07:36:09 W NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
20200129 07:36:09 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
20200129 07:36:09 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
20200129 07:36:09 I TCP/UDP: Preserving recently used remote address: [AF_INET]31.204.154.117:1195
20200129 07:36:09 Socket Buffers: R=[180224->180224] S=[180224->180224]
20200129 07:36:09 I UDPv4 link local: (not bound)
20200129 07:36:09 I UDPv4 link remote: [AF_INET]31.204.154.117:1195
20200129 07:36:09 TLS: Initial packet from [AF_INET]31.204.154.117:1195 sid=3e415a68 21d92ff3
20200129 07:36:09 W WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
20200129 07:36:09 VERIFY OK: depth=1 C=VG ST=BVI O=ExpressVPN OU=ExpressVPN CN=ExpressVPN CA emailAddress=support@expressvpn.com
20200129 07:36:09 VERIFY KU OK
20200129 07:36:09 Validating certificate extended key usage
20200129 07:36:09 NOTE: --mute triggered...
20200129 07:36:09 4 variation(s) on previous 3 message(s) suppressed by --mute
20200129 07:36:09 I [Server-457-1a] Peer Connection Initiated with [AF_INET]31.204.154.117:1195
20200129 07:36:10 SENT CONTROL [Server-457-1a]: 'PUSH_REQUEST' (status=1)
20200129 07:36:10 PUSH: Received control message: 'PUSH_REPLY redirect-gateway def1 dhcp-option DNS 10.71.0.1 comp-lzo no route 10.71.0.1 topology net30 ping 10 ping-restart 60 ifconfig 10.71.0.54 10.71.0.53 peer-id 12 cipher AES-256-GCM'
20200129 07:36:10 OPTIONS IMPORT: timers and/or timeouts modified
20200129 07:36:10 NOTE: --mute triggered...
20200129 07:36:10 7 variation(s) on previous 3 message(s) suppressed by --mute
20200129 07:36:10 Data Channel: using negotiated cipher 'AES-256-GCM'
20200129 07:36:10 NCP: overriding user-set keysize with default
20200129 07:36:10 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
20200129 07:36:10 NOTE: --mute triggered...
20200129 07:36:10 1 variation(s) on previous 3 message(s) suppressed by --mute
20200129 07:36:10 I TUN/TAP device tun1 opened
20200129 07:36:10 TUN/TAP TX queue length set to 100
20200129 07:36:10 I /sbin/ifconfig tun1 10.71.0.54 pointopoint 10.71.0.53 mtu 1500
20200129 07:36:10 /sbin/route add -net 31.204.154.117 netmask 255.255.255.255 gw 10.10.100.10
20200129 07:36:10 /sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.71.0.53
20200129 07:36:10 /sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.71.0.53
20200129 07:36:10 /sbin/route add -net 10.71.0.1 netmask 255.255.255.255 gw 10.71.0.53
20200129 07:36:11 I Initialization Sequence Completed
20200129 07:36:24 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:36:24 D MANAGEMENT: CMD 'state'
20200129 07:36:24 MANAGEMENT: Client disconnected
20200129 07:36:24 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:36:24 D MANAGEMENT: CMD 'state'
20200129 07:36:24 MANAGEMENT: Client disconnected
20200129 07:36:24 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:36:24 D MANAGEMENT: CMD 'state'
20200129 07:36:24 MANAGEMENT: Client disconnected
20200129 07:36:24 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:36:24 D MANAGEMENT: CMD 'status 2'
20200129 07:36:24 MANAGEMENT: Client disconnected
20200129 07:36:24 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:36:24 D MANAGEMENT: CMD 'log 500'
20200129 07:36:24 MANAGEMENT: Client disconnected
20200129 07:38:33 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:38:33 D MANAGEMENT: CMD 'state'
20200129 07:38:33 MANAGEMENT: Client disconnected
20200129 07:38:33 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:38:33 D MANAGEMENT: CMD 'state'
20200129 07:38:33 MANAGEMENT: Client disconnected
20200129 07:38:33 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:38:33 D MANAGEMENT: CMD 'state'
20200129 07:38:33 MANAGEMENT: Client disconnected
20200129 07:38:33 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:38:33 D MANAGEMENT: CMD 'status 2'
20200129 07:38:33 MANAGEMENT: Client disconnected
20200129 07:38:33 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:16
20200129 07:38:33 D MANAGEMENT: CMD 'log 500'
19700101 04:00:00 -
i feel there is a small issue with the way pf sense open vpn client connects vs ddwrt please guys crack this mystery !!! i have a restricted ISP i know....
-
@akkiz said in losing OpenVPN connection every 20 - 120 seconds:
i feel there is a small issue with the way pf sense open vpn client connects vs ddwrt please guys crack this mystery !!! i have a restricted ISP i know....
Should I undetsrand that a OpenVPN client, build into a ddwrt, connects fine to your VPN, and pfSense doesn't ?
From the same place ?
You are alternating the routers ? (first you put pfSense in place, test = doesn't work - and then the ddwrt and that one works.)
The fact that OpenVPN works fine over your connection using the ddwrt mean : it isn't your ISP that blocking you. I presume same ports, protocol etc.There is hope : it's a pure "settings" issue.
I can connect just fine to ExpressVPN using the OPenVPN client :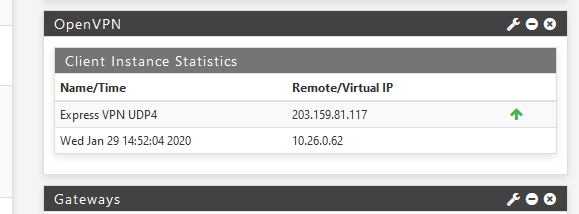
I used to setup and debug the client - keep n mind, thius explantion isn't 100 % correct - I made some changes (don't remember which ) - it's all a "read the logs, look up the messages that look like an error, Google them up, and do what other prospose)
A connection log :
2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[8857]: OpenVPN 2.4.8 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Dec 6 2019 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[8857]: library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10 2020-01-29 14:56:24 Local4.Info pfsense Jan 29 14:56:28 php-fpm[244]: OpenVPN PID written: 9078 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client2.sock 2020-01-29 14:56:24 Daemon.Warning pfsense Jan 29 14:56:28 openvpn[9078]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: TCP/UDP: Preserving recently used remote address: [AF_INET]203.159.81.117:1195 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: Socket Buffers: R=[42080->524288] S=[57344->524288] 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: UDPv4 link local (bound): [AF_INET]192.168.10.4:0 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: UDPv4 link remote: [AF_INET]203.159.81.117:1195 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: TLS: Initial packet from [AF_INET]203.159.81.117:1195, sid=70f8e02c 9745dcdc 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: VERIFY KU OK 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: Validating certificate extended key usage 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: VERIFY EKU OK 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-3583-0a, emailAddress=support@expressvpn.com 2020-01-29 14:56:24 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-3583-0a, emailAddress=support@expressvpn.com 2020-01-29 14:56:25 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA 2020-01-29 14:56:25 Daemon.Notice pfsense Jan 29 14:56:28 openvpn[9078]: [Server-3583-0a] Peer Connection Initiated with [AF_INET]203.159.81.117:1195 2020-01-29 14:56:25 Daemon.Notice pfsense Jan 29 14:56:29 xinetd[68926]: Starting reconfiguration 2020-01-29 14:56:25 Daemon.Error pfsense Jan 29 14:56:29 xinetd[68926]: service: 19000-tcp id: 19000-tcp not unique or is a duplicate - DISABLING 2020-01-29 14:56:25 Daemon.Notice pfsense Jan 29 14:56:29 xinetd[68926]: Swapping defaults 2020-01-29 14:56:25 Daemon.Notice pfsense Jan 29 14:56:29 xinetd[68926]: readjusting service 19000-tcp 2020-01-29 14:56:25 Daemon.Notice pfsense Jan 29 14:56:29 xinetd[68926]: Reconfigured: new=0 old=1 dropped=0 (services) 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: SENT CONTROL [Server-3583-0a]: 'PUSH_REQUEST' (status=1) 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.26.0.1,comp-lzo no,route 10.26.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.26.0.62 10.26.0.61,peer-id 14' 2020-01-29 14:56:26 Daemon.Error pfsense Jan 29 14:56:29 openvpn[9078]: Options error: option 'redirect-gateway' cannot be used in this context ([PUSH-OPTIONS]) 2020-01-29 14:56:26 Daemon.Error pfsense Jan 29 14:56:29 openvpn[9078]: Options error: option 'dhcp-option' cannot be used in this context ([PUSH-OPTIONS]) 2020-01-29 14:56:26 Daemon.Error pfsense Jan 29 14:56:29 openvpn[9078]: Options error: option 'route' cannot be used in this context ([PUSH-OPTIONS]) 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: OPTIONS IMPORT: timers and/or timeouts modified 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: OPTIONS IMPORT: compression parms modified 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: OPTIONS IMPORT: --ifconfig/up options modified 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: OPTIONS IMPORT: peer-id set 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: OPTIONS IMPORT: adjusting link_mtu to 1629 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: Outgoing Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: Incoming Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: TUN/TAP device ovpnc2 exists previously, keep at program end 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: TUN/TAP device /dev/tun2 opened 2020-01-29 14:56:26 Kernel.Notice pfsense Jan 29 14:56:29 kernel: ovpnc2: link state changed to UP 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:29 openvpn[9078]: /sbin/ifconfig ovpnc2 10.26.0.62 10.26.0.61 mtu 1500 netmask 255.255.255.255 up 2020-01-29 14:56:26 Daemon.Notice pfsense Jan 29 14:56:30 openvpn[9078]: /usr/local/sbin/ovpn-linkup ovpnc2 1500 1609 10.26.0.62 10.26.0.61 init 2020-01-29 14:56:28 Daemon.Notice pfsense Jan 29 14:56:32 openvpn[9078]: Initialization Sequence CompletedNote :
These :
The 3 "Options error" are meaningless for pfSense.Also : Your issue isn't probably VPN related. Other changes in the general pfSense setup can influence the connection, for example : bad MMS or MTU, etc.
Btw : It connects. I didn't pass any traffic throughit, because then I have to change my firewall rules, setup other gateways, etc.
So,
@akkiz said in losing OpenVPN connection every 20 - 120 seconds:
i feel there is a small issue ...
No issue I guess.
Just make it work.edit : these are my custom options :
persist-key persist-tun tls-client verify-x509-name Server name-prefix remote-cert-tls server key-direction 1 route-delay 2 tun-mtu 1500 fragment 1300 mssfix 1450 auth-nocacheSome of these are probably not needed.