OpenVPN client connected, no internet or LAN access
-
This the content of my server2.conf (there's no server1, it was deleted earlier, I have only one VPN server instance):
dev ovpns2 verb 1 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-256-CBC auth SHA512 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local *<MY WAN IP ADDRESS>* engine rdrand tls-server server 10.1.1.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server2 username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWxkNFP2WXIgc1D= true server2 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'vpn-server' 1" lport 1194 management /var/etc/openvpn/server2.sock unix max-clients 5 push "dhcp-option DOMAIN lan" push "dhcp-option DNS 192.168.1.14" push "block-outside-dns" push "register-dns" push "redirect-gateway def1" client-to-client duplicate-cn ca /var/etc/openvpn/server2.ca cert /var/etc/openvpn/server2.cert key /var/etc/openvpn/server2.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server2.tls-auth 0 ncp-ciphers AES-128-GCM:AES-256-GCM:AES-192-GCM comp-lzo adaptive persist-remote-ip float topology subnet keepalive 5 300 reneg-sec 36000 push "redirect-gateway def1" -
Have you added a firewall rule to the OpenVPN tab to allow traffic?
For Internet access, you need an outbound NAT rule for the VPN tunnel network in addition.
-
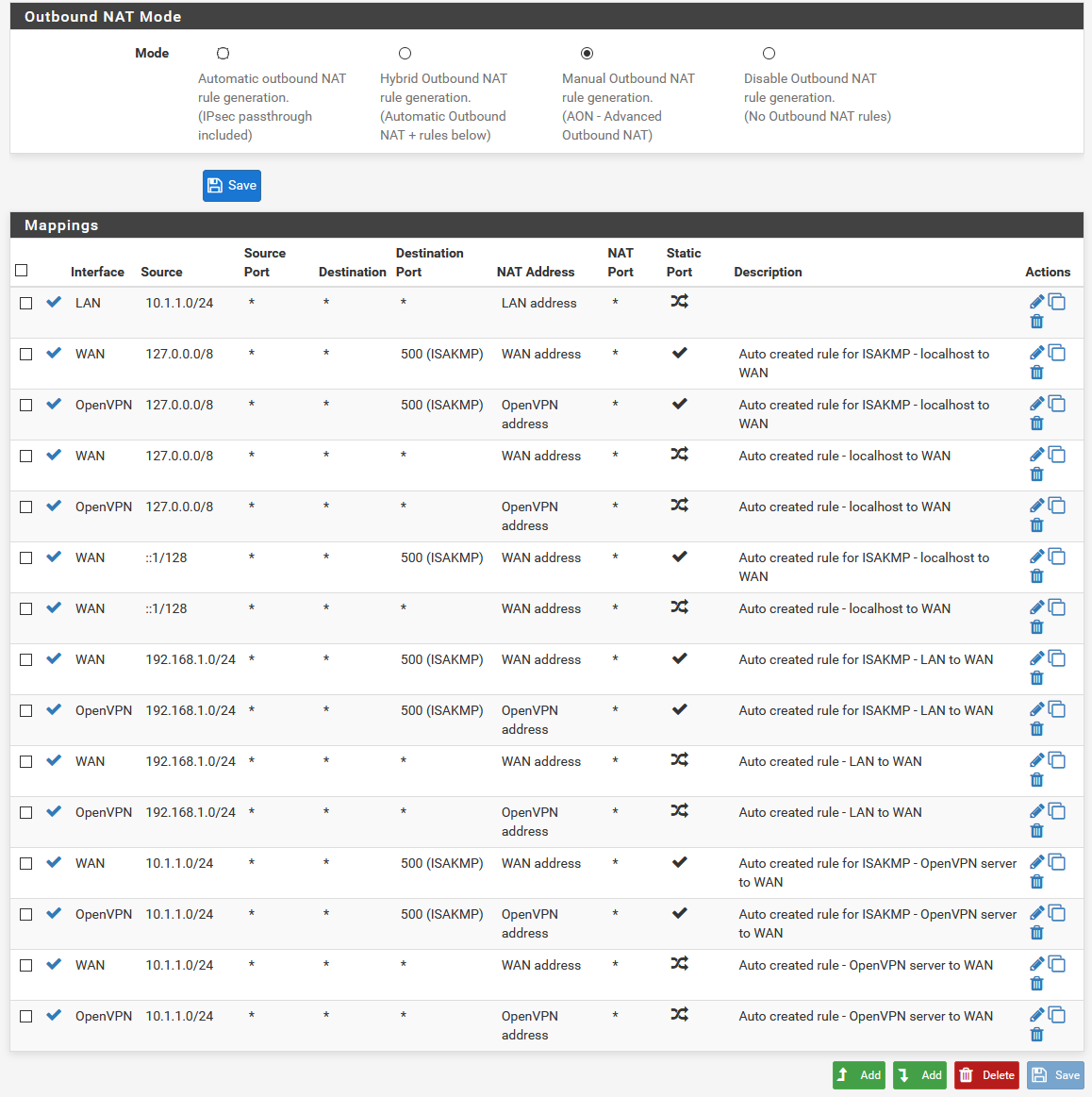
@viragomann Yes, FW rule is in place and I've tried also with duplicating the Outbound NAT rules and changing the interface from WAN to OpenVPN.
Outbound NAT rules:
-
@dean2028 said in OpenVPN client connected, no internet or LAN access:
... and I've tried also with duplicating the Outbound NAT rules and changing the interface from WAN to OpenVPN.
but to be honest, I don't really know what I'm doing here with these, therefore I'm not sure if this makes sense at all as it is now. If I leave it on Automatic, it doesn't work either.
-
All you need in the outbound NAT is this rule:

It seems to be added by pfSense automatically already.Try to access the pfSense WebGUI. Try the OpenVPN server IP which is 10.1.1, also try the LAN IP.
-
@viragomann Thanks for confirming the NAT rules.
Try to access the pfSense WebGUI. Try the OpenVPN server IP which is 10.1.1, also try the LAN IP.
I can reach the pfSense UI login page with both, the LAN IP 192.168.1.14 and the OpenVPN server IP 10.1.1.1.
-
So at least the route to the LAN network works.
Ensure that your LAN device does not block the access. If it's running a firewall it probably blocks access from other networks, since you haven't explicitly allowed it.
You may use the ping tool from the pfSense Diagnostic menu for investigating. You may try a ping with source address LAN and e.g. OpenVPN to see if it responses.
-
Ensure that your LAN device does not block the access. If it's running a firewall it probably blocks access from other networks, since you haven't explicitly allowed it.
@viragomann Shame on me... That was it. Thanks for the heads up. I believe the LAN access part solved then. However internet access still doesn't seem to work or at least I'm not able to open anything from the internet in Safari from the phone. Checked the pfSense ping tool to ping a host like google with OpenVPN selected and it seems the IP resolved and ping works.
-
@dean2028 said in OpenVPN client connected, no internet or LAN access:
and it seems the IP resolved
That may be the cue here.
Have you stated a DNS server in the OpenVPN settings? -
@viragomann Yes and just checked with a tool on the phone that the port is open to the pfSense LAN IP on port 53. However when I try a DNS lookup for an internet host on the phone, I get no response while connected to VPN.
-
That's quite weird. I went to the DNS resolver settings, changed Network interfaces to All from LAN and Localhost. Reconnected with the phone to the vpn and still did not work. Changed the Network interfaces back to LAN and Localhost, applied the settings, then the service chrashed. Started from the DNS resolver from the UI and it works now. Maybe it has something to do with Unbound and pfBlockerNG?
-
It’s not the possibility to access DNS port. You have to enter a DNS server in the proper box to push it to the client, otherwise the client won’t have no DNS config.
If you’re running the DNS Resolver or Forwarder on pfSense, this may be the IP of the pfSense itself. -
@viragomann I understand, but this was set since the beginning as I wrote in my first post about the config:
DNS Server 1: 192.168.1.14 (pfSense, I use pfSense as DNS server with pfBlockerNg)
but I tried to add it also manually before to the config by this line, but actually did not change anything:
push "dhcp-option DNS 192.168.1.14"What was interesting, I also saw connections earlier from the phone to the pfSense IP on port 53 based on states
(Firewall > Rules > OpenVPN, then clicked traffic data in the States column)but something was not good as the DNS server actually not responded to the queries from the phone. At the moment I have that only idea the DNS server service was not in a good condition.
Anyway, thanks a lot for your help, I really appreciate your prompt feedbacks!