Separate LAN from OPT on SG-1100
-
Can someone point me to a basic cookbook to isolate the network attached to "LAN" from the network attached to "OPT" on a Netgate SG-1100?
I've set up NAT with 192.168.1.x on LAN and 192.168.30.x on OPT. and I have added an "allow OPT to any" firewall rule for OPT and otherwise have only default firewall rules.
With this setup I can ping devices on LAN from devices on OPT, but cannot ping devices on OPT from LAN. My goal is to have the two interfaces completely separate. I'm not understanding why connection is allowed one way, but not the other.
Pointers to resources for this type of setup will be most appreciated.
Update: discovered why the default rules were giving this result. There was a device level firewall turned on on one of the devices in my test network. I turned that off and traffic flowed both ways between the LAN and OPT network. That made sense, and then I added rules to block traffic between the two networks and got the result I was expecting.
-
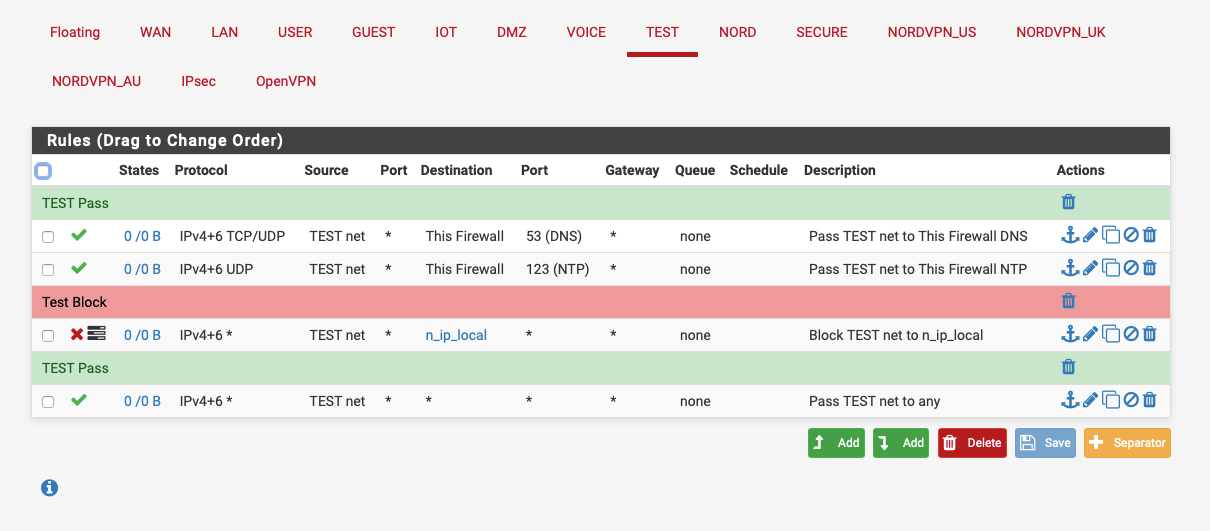
n_ip_local is an alias with all my subnets in.
-
Since you’ve got an “allow OPT to any” rule on OPT, that’s where the traffic is getting thru. Right above that rule you need to create a block rule for OPT to LAN.
Jeff
-
@akuma1x That makes sense, of course, but why is traffic already blocked in the other direction with only default rules on LAN?
-
It shouldn’t be blocked with default rules. But, to make sure, you’ll have to post screenshot of your rule sets. Also, do you have any floating rules, those run first, before other rules on interfaces.
Jeff
-
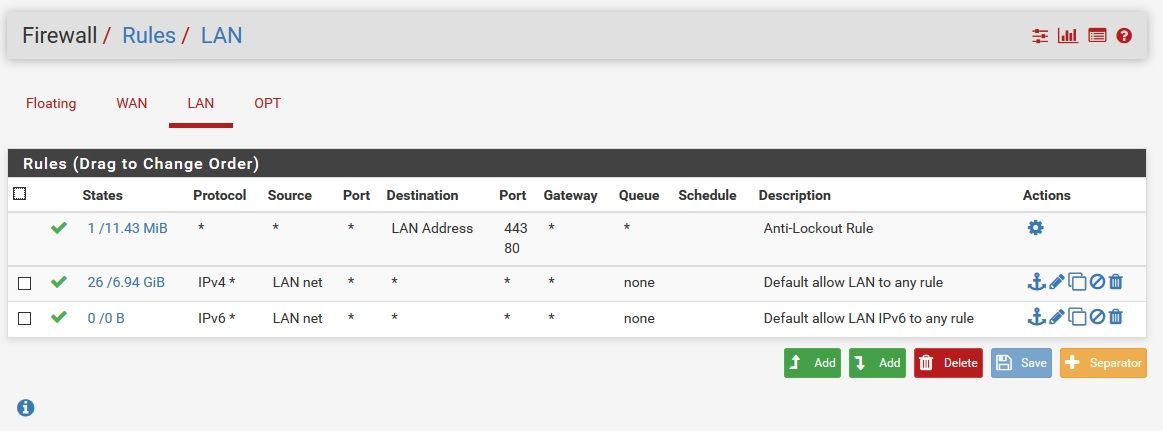
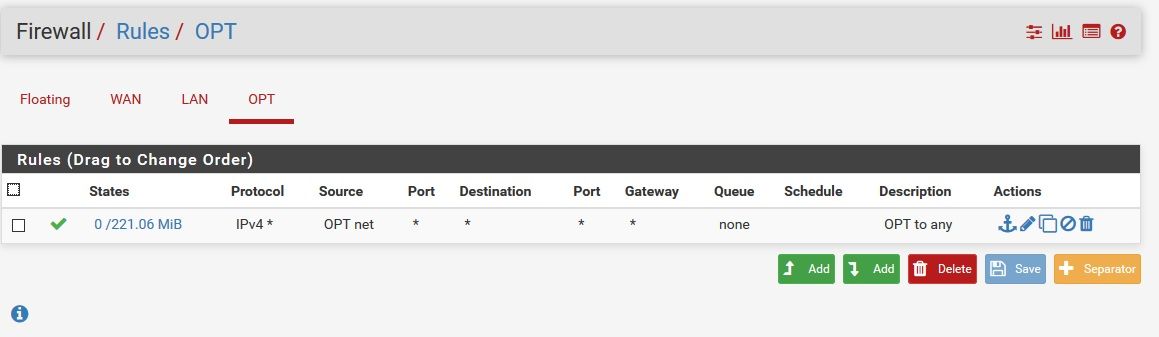
Default rules on LAN, only the one rule on OPT. A device on LAN is unable to ping a device on OPT. A device on OPT can ping a device on LAN.
Lan:
Opt:
Devices on both LAN and OPT are able to ping a host on the internet.