Solved: Cannot access beyond router via OpenVPN
-
I set up openvpn yesterday and although I can connect to it remotely, I can only access the router itself. Nothing beyond it.
I have firewall rules on the openvpn interface to allow all to all.
There are no blocking rules, every interface for testing has allow all to all.Looking at filter.log, I do not have any activity from the 10.8.0.2 (client assigned)
I've been at this for a day now and haven't gotten anywhere. Tried reinstalling and recreating multiple times.
LAN 172.20.0.0/24
IOTLAN: 172.20.100.0/24
IOTWIFI: 172.20.200.0/24router 172.20.0.1
Openvpn clients 10.8.0.0/24
I've attached my server and client configs:
[2.4.4-RELEASE][admin@protectli.pfdomain]/var/etc/openvpn: cat server2.conf
dev ovpns2 verb 1 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto tcp4-server cipher AES-256-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local 69.112.137.17 engine rdrand tls-server server 10.8.0.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server2 username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server2 443 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'pfSense+Openvpn+server' 1" lport 443 management /var/etc/openvpn/server2.sock unix push "route 172.20.0.0 255.255.255.0" push "route 172.20.100.0 255.255.255.0" push "route 172.20.200.0 255.255.255.0" push "dhcp-option DNS 172.20.0.1" ca /var/etc/openvpn/server2.ca cert /var/etc/openvpn/server2.cert key /var/etc/openvpn/server2.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server2.tls-auth 0 ncp-ciphers AES-128-GCM persist-remote-ip float topology subnetClient1 config:
dev tun persist-tun persist-key cipher AES-256-CBC ncp-ciphers AES-128-GCM auth SHA256 tls-client client resolv-retry infinite (privateaddress) 443 tcp-client verify-x509-name "pfSense Openvpn server" name auth-user-pass remote-cert-tls server <ca> -----BEGIN CERTIFICATE----- (removed) -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- (removed) -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- (removed) -----END PRIVATE KEY----- </key> key-direction 1 <tls-auth> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- -----END OpenVPN Static key V1----- </tls-auth>Thank you for any assistance.
-
This is the route table from the client machine when connected via openvpn from outside LAN.
IPv4 Route Table =========================================================================== Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 192.168.43.42 192.168.43.81 50 10.8.0.0 255.255.255.0 On-link 10.8.0.2 291 10.8.0.2 255.255.255.255 On-link 10.8.0.2 291 10.8.0.255 255.255.255.255 On-link 10.8.0.2 291 127.0.0.0 255.0.0.0 On-link 127.0.0.1 331 127.0.0.1 255.255.255.255 On-link 127.0.0.1 331 127.255.255.255 255.255.255.255 On-link 127.0.0.1 331 172.20.0.0 255.255.255.0 10.8.0.1 10.8.0.2 291 172.20.100.0 255.255.255.0 10.8.0.1 10.8.0.2 291 172.20.200.0 255.255.255.0 10.8.0.1 10.8.0.2 291 192.168.43.0 255.255.255.0 On-link 192.168.43.81 306 192.168.43.81 255.255.255.255 On-link 192.168.43.81 306 192.168.43.255 255.255.255.255 On-link 192.168.43.81 306 224.0.0.0 240.0.0.0 On-link 127.0.0.1 331 224.0.0.0 240.0.0.0 On-link 192.168.43.81 306 224.0.0.0 240.0.0.0 On-link 10.8.0.2 291 255.255.255.255 255.255.255.255 On-link 127.0.0.1 331 255.255.255.255 255.255.255.255 On-link 192.168.43.81 306 255.255.255.255 255.255.255.255 On-link 10.8.0.2 291 =========================================================================== Persistent Routes: None -
So your routes to your networks are there.. But do they point back to pfsense, do they have any firewalls running on them that would not allow traffic from your 10.0.8 vpn tunnel network Ips
Can you ping the IP address of pfsense IPs on your 172.20.0, 172.20.100 and 172.20.200? If so then the tunnel is working and your routing down the tunnel.
Simple test sniff on sa your 172.20.0 interface, now ping something on this network that you should be able to get to.. say 172.20.0.X -- do you see pfsense send on the traffic... If so, then its a client related problem, firewall, not using pfsense as its default gateway, etc.
-
Thank you for replying.
172.20.0.3: ping 172.20.0.17
worked (172.20.0.17 firewall allowing pings)The rules for 172.20.0.17:
To Action From -- ------ ---- OpenSSH ALLOW Anywhere 443/tcp ALLOW Anywhere 224.0.0.0/4 DENY Anywhere 5355/udp DENY Anywhere 8443/tcp ALLOW Anywhere 10001/udp ALLOW Anywhere 3478 ALLOW 172.20.0.0/24 8080 on bond0 ALLOW Anywhere OpenSSH (v6) ALLOW Anywhere (v6) 443/tcp (v6) ALLOW Anywhere (v6) 5355/udp (v6) DENY Anywhere (v6) 8443/tcp (v6) ALLOW Anywhere (v6) 10001/udp (v6) ALLOW Anywhere (v6) 8080 (v6) on bond0 ALLOW Anywhere (v6)There are no IP specific rules except for Unifi.
From remote client:
10.8.0.2: ping 172.20.0.1
(works)
10.8.0.2: ping 172.20.100.1
(works)
10.8.0.2: ping 172.20.0.17
(times out)I'm running klog -f /var/log/filter.log on 172.20.0.1 and no activity from 10.8.0.1.
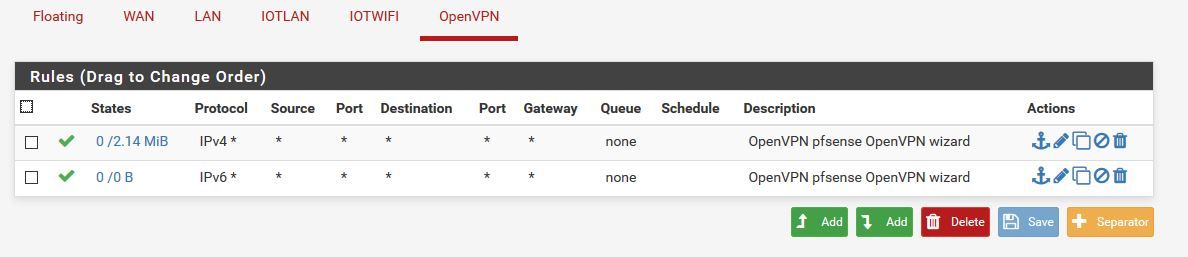
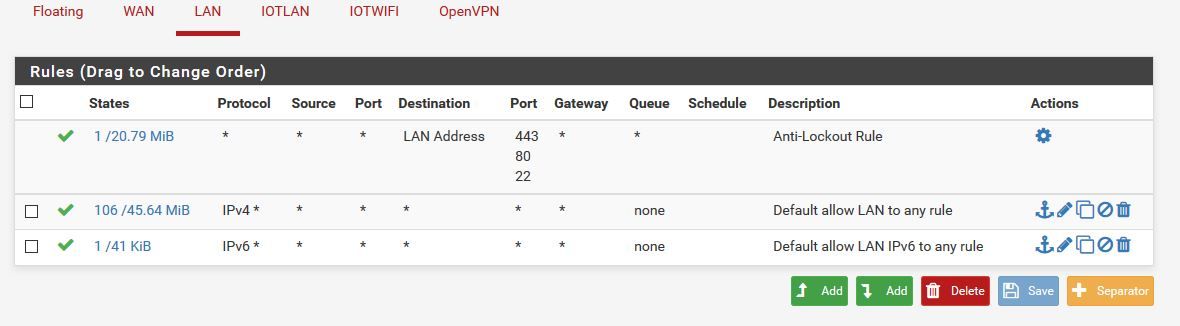
Thanks for helping me.
Devan
-
@ddbnj said in Cannot access beyond router via OpenVPN:
10.8.0.2: ping 172.20.0.17
(times out)And where do those rules allow icmp (ping)?
I see you allow ssh and etc... But no ICMP on that .17 firewall that I see.
So again to PROVE it to yourself... Sniff on pfsense when you ping .17 Do you see it sending the pings... Then its NOT pfsense!!
-
Sorry this is frustrating. Me too.
I turned off the firewall on 172.20.0.17.
pi:~ $ sudo iptables -S -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT pi:~ $I still can ping 172.20.0.17 from anywhere on 172.20.0.0/24.
Here are the packet capture from the VPN interface. It's for all ICMP data on this interface. All ping requests were remote while connected to openvpn.
14:46:00.102158 IP 10.8.0.2 > 10.8.0.1: ICMP echo request, id 1, seq 63, length 40 14:46:00.102168 IP 10.8.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 63, length 40 14:46:01.120550 IP 10.8.0.2 > 10.8.0.1: ICMP echo request, id 1, seq 64, length 40 14:46:01.120555 IP 10.8.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 64, length 40 14:46:02.135848 IP 10.8.0.2 > 10.8.0.1: ICMP echo request, id 1, seq 65, length 40 14:46:02.135853 IP 10.8.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 65, length 40 14:46:03.148124 IP 10.8.0.2 > 10.8.0.1: ICMP echo request, id 1, seq 66, length 40 14:46:03.148129 IP 10.8.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 66, length 40 14:46:06.790785 IP 10.8.0.2 > 172.20.0.1: ICMP echo request, id 1, seq 67, length 40 14:46:06.790795 IP 172.20.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 67, length 40 14:46:07.770961 IP 10.8.0.2 > 172.20.0.1: ICMP echo request, id 1, seq 68, length 40 14:46:07.770966 IP 172.20.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 68, length 40 14:46:08.800442 IP 10.8.0.2 > 172.20.0.1: ICMP echo request, id 1, seq 69, length 40 14:46:08.800446 IP 172.20.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 69, length 40 14:46:09.816666 IP 10.8.0.2 > 172.20.0.1: ICMP echo request, id 1, seq 70, length 40 14:46:09.816670 IP 172.20.0.1 > 10.8.0.2: ICMP echo reply, id 1, seq 70, length 40 14:46:15.991837 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 71, length 40 14:46:20.820495 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 72, length 40 14:46:25.919175 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 73, length 40As you can see I can reach and communicate up to the router and not beyond. I cannot ping or SSH to anything behind it.
-
I didn't say sniff on the vpn interface... Sniff on the 172.20.0.1 interface of pfsense... But you can see right here pfsense is seeing the traffic!!
14:46:15.991837 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 71, length 40 14:46:20.820495 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 72, length 40 14:46:25.919175 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 73, length 40Validate that traffic is actually living the 172.20.0.1 interface of pfsense towards your .17 box... To prove to youself its NOT pfsense...
If pfsense puts the traffic on the wire towards .17, and there is no answer its either firewall on the device. device is not using pfsense as its gateway.. Or something in between the device and pfsense.. This is not rocket science by any means.
I can pretty much promise you its your device!!!
-
Thank you.
As requested, from the LAN interface. I chose the VPN interface so one can see what a normal ICMP reply would resemble.
15:10:02.886130 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 90, length 40 15:10:07.853518 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 91, length 40 15:10:12.822370 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 92, length 40 15:10:17.803202 IP 10.8.0.2 > 172.20.0.17: ICMP echo request, id 1, seq 93, length 40I agree with you that it is my device. And also the other devices behind my router.
I don't know how to fix them to accept connections from outside the LAN with the firewall completely off.
All of my devices on the LAN obtain their IP addresses via DHCP.
ifconfig:
bond0: flags=5187<UP,BROADCAST,RUNNING,MASTER,MULTICAST> mtu 1500 inet 172.20.0.17 netmask 255.255.255.0 broadcast 172.20.0.255 inet6 fe80::f413:4fff:fefc:dfb6 prefixlen 64 scopeid 0x20<link> ether f6:13:4f:fc:df:b6 txqueuelen 1000 (Ethernet) RX packets 127203 bytes 47050038 (44.8 MiB) RX errors 0 dropped 4 overruns 0 frame 0 TX packets 48932 bytes 6892625 (6.5 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 eth0: flags=6147<UP,BROADCAST,SLAVE,MULTICAST> mtu 1500 ether f6:13:4f:fc:df:b6 txqueuelen 1000 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x10<host> loop txqueuelen 1000 (Local Loopback) RX packets 344781 bytes 118577339 (113.0 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 344781 bytes 118577339 (113.0 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500 inet 10.8.0.1 netmask 255.255.255.0 destination 10.8.0.1 inet6 fe80::b675:4544:9388:1cab prefixlen 64 scopeid 0x20<link> unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 125 bytes 7096 (6.9 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 wlan0: flags=6211<UP,BROADCAST,RUNNING,SLAVE,MULTICAST> mtu 1500 ether f6:13:4f:fc:df:b6 txqueuelen 1000 (Ethernet) RX packets 127203 bytes 47050038 (44.8 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 48932 bytes 6892625 (6.5 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0I do not see a gateway specified.
Examining the route:
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface default protectli.pfdom 0.0.0.0 UG 1024 0 0 bond0 10.8.0.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0 172.20.0.0 0.0.0.0 255.255.255.0 U 0 0 0 bond0 protectli.pfdom 0.0.0.0 255.255.255.255 UH 1024 0 0 bond0Bingo! I had an old VPN configuration using the same route. Once I turned off openvpn on that machine it worked.
Thank you for helping me work through this!
-Devan
-
@ddbnj said in Cannot access beyond router via OpenVPN:
10.8.0.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
Yeah that would dick it up ;)
Glad you got it sorted! Told you it wasn't pfsense ;) hehehehe
The trick is getting the person to clearly see that themselves... Which is why the sniff proves to the user, hey pfsense is doing what its suppose to be doing... Have to look elsewhere..