Hiding management from everyone
-
I have my pfsense box working as a NAT, but I often login to see both ssh and GUI login attempts from random scanners on the internet or from our LAN
Is there a way to make pfsense management (ssh and GUI access) only available for a specific address or perhaps specific mac addresses? Thanks.
-
Unless you enable it, management is not available from the WAN side.
-
@JKnott
Alright, thank you. How about accessing from the LAN side though? Can I restrict that to just a specific vlan for example without messing with any of the NAT functionalities? -
The anti lockout rules on the lan, allow for ssh/gui access if enabled from any IP on the lan. That can be disabled if you want, and then only allow the source IPs you want talk to pfsense on ssh.
From other vlans, just don't allow ssh/gui port to pfsense IPs
Keep in mind that if you allow any or ssh/gui port out of that vlan, that it would be possible to hit your pfsense wan IP from that vlan.. When you want to block access to pfsense ports for admin, the this firewall is built in alias that is good to use.
example:
This vlan, all access other than what allowed to pfsense IP is blocked by the "this firewall" alias rule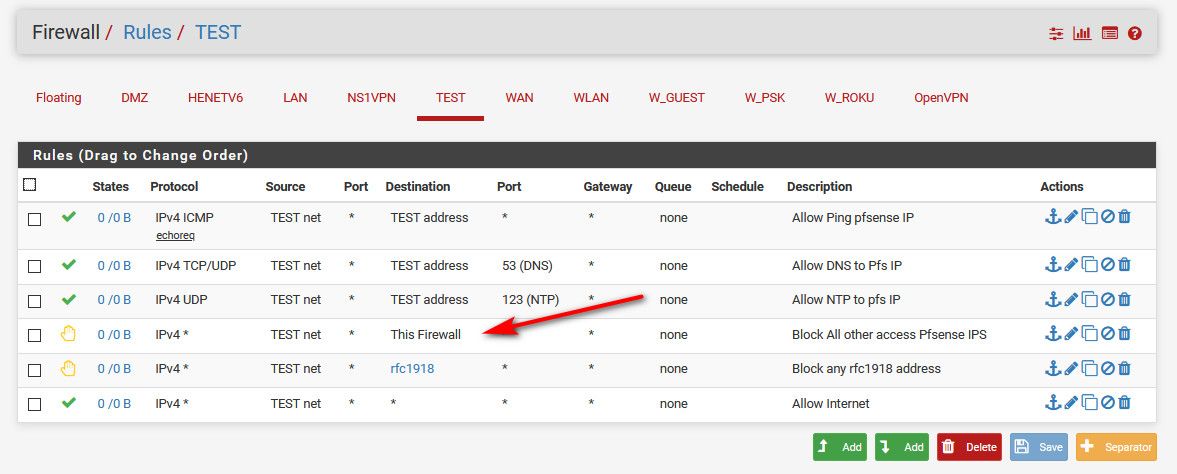
So while they can ping pfsense IP on this vlan, and ntp and dns - they can not access any other port on any pfsense IP. ie ssh or gui.
-
@johnpoz Thank you for the help! I will try that out.
-
As johnpoz mentioned, you can create rules to alllow only specific addresses. Another thing you can do, with ssh, is use a public/private key pair, so that no one without the appropriate key can connect.
-
@JKnott said in Hiding management from everyone:
with ssh, is use a public/private key pair,
This is kind of given to be honest... I would never have ssh open to only password, other than for the few minutes it takes to enable public key auth only ;)
Shoot even my unifi AP uses public key ;) Only issues is really can't actually disable the password auth that I have found.
-
When you setup your internal block rules make sure to use rules like this:
- Pass from <management addresses> to This Firewall (self) on <management ports>
- Reject from any to This Firewall (self) on <management ports>
There are other (and better) ways to do it depending on which services must be accessible to local clients, but the key is you should be using This Firewall (self) as the target to make sure that any addressable interface on the firewall is covered.
Otherwise if you have a rule like:
- Block from LAN subnet to LAN address
- Pass from LAN subnet to any (for the Internet)
You'll find that local clients can reach the firewall GUI and SSH using the external address or addresses on other connected interfaces.