Rules for allowing limited ICMP on IPv4/v6 from WAN
-
Greetings. Could someone advise if Ihave these rules setup correctly? The v4 rule is just for troubleshooting from outside and the v6 is for making IPv6 work. Did some reading and i think they're right, but thought I'd check. Thanks for any assist.
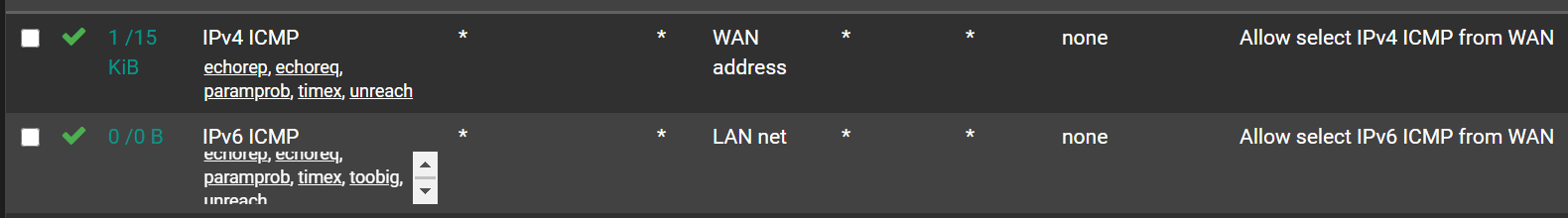
-
You wouldn't need to set
echoreporunreachas those would never arrive unsolicited -- only associated with an existing state, which would already pass them. I suspect the same is also true ofparamprobandtimex. You probably only need to explicitly allowechoreqif you intend to allow remote hosts to ping you.pf is pretty good about state tracking and associating ICMP messages with related connections already for things like unreachable messages.
-
@jimp Thanks very much. Appreciate all you do.
-
@jimp PS - Is the LAN Net OK for IPv6 dest? Thanks again.
-
@provels said in Rules for allowing limited ICMP on IPv4/v6 from WAN:
Is the LAN Net OK for IPv6 dest? Thanks again.
LAN Net is fine as long as that is the only subnet you have. I created an Alias for my whole /56 i received from my ISP and these are the rules I have:
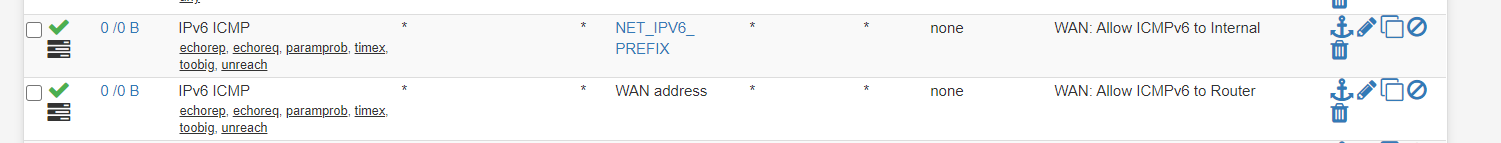
This was based on "RFC 4890 Recommendations for Filtering ICMPv6 Messages in Firewalls" paragraph 4.3.1. Traffic That Must Not Be Dropped.
I had not considered what @jimp said, that the pfsense takes care of some of these for you already.
I don't remember why I added the WAN address rule, but maybe it was trace-route? Or just so I could ping the router externally and see it was up?
The WAN address is an address external from my /56.
-
@IsaacFL Thanks. Now that you mention it, I believe the the RFC was where I had found the info I used as well but had forgotten (buffer overflow, I guess...). Thanks again, all.