how to setup Leakproof VPN (Private Internet Access)
-
Hello,
I have been used IPcop 10years ago, then used Cisco ASAs and have now learned how much you can do with pfSense and are becoming a big fan.
I have configured pfSense to establish an OpenVPN connection and would like to force all LAN traffic through the tunnel, including DNS requests.
OpenVPN is working and the traffic goes through the VPN.
But if the VPN Tunnel breaks, the traffic goes through the normal WAN port.
I would like that I have some rules, that traffic from LAN is not passing the WAN interface in case the VPN breaks.Unfortunately I am not sure how to set this up.
I am blocking all traffic from LAN to WAN and have created rules for LAN to WAN only for the traffic I would like to use.
This has been working, before I have added the OpenVPN connection.I have added the requested Outbound NAT rules, as requested by the Privat Internet Access documentation.
But I think that I need more/changed rules so that LAN traffic can only go through VPN.Any ideas what I need to do?
-
Some more information regarding my setup.
Interfaces:
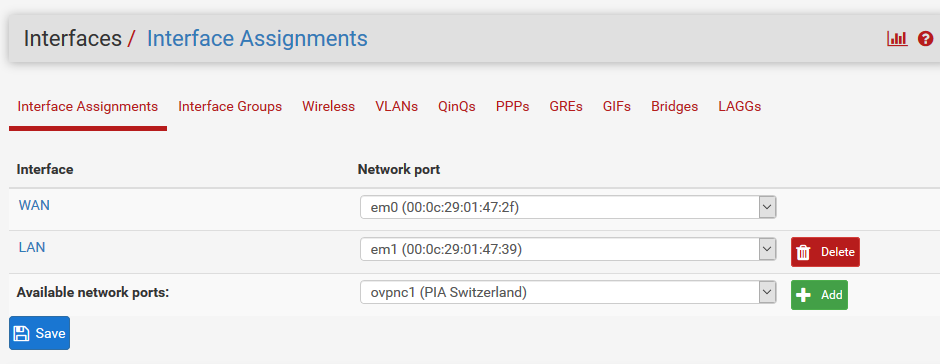
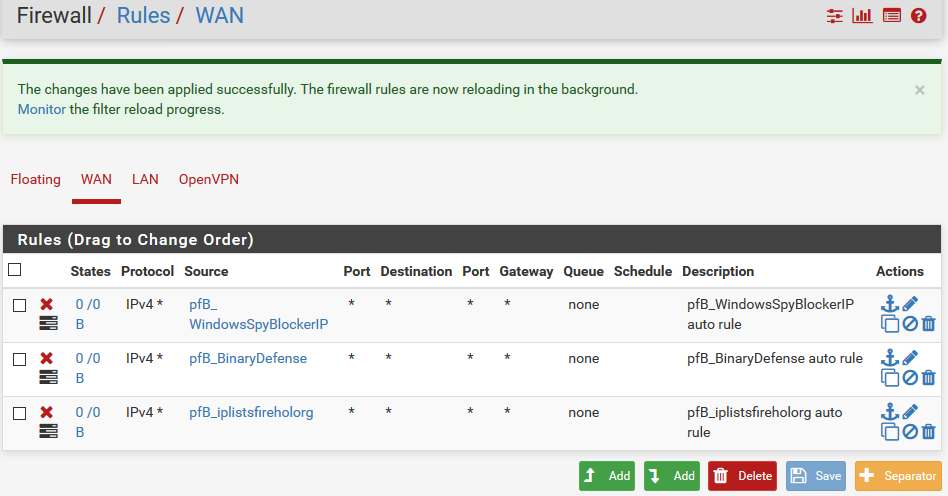
Rules for WAN-Interface
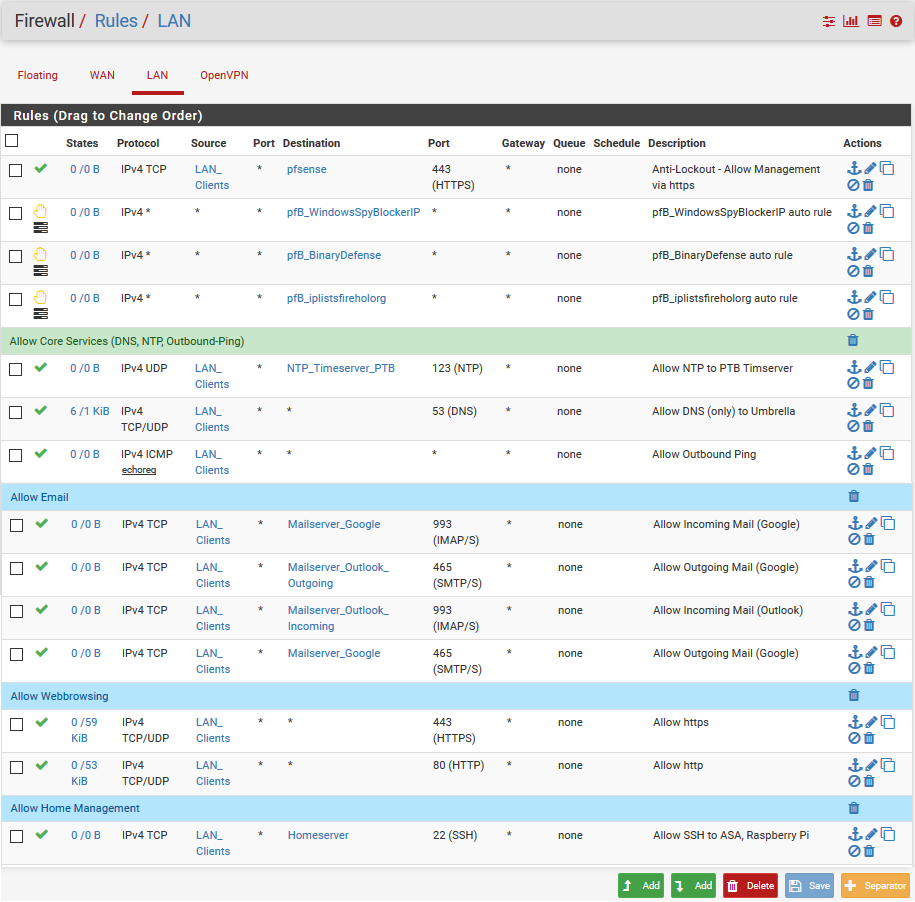
Rules for LAN-Interface
I know that I need to switch my current DNS Servers from OpenDNS to those of the VPN-Provider.
I will do so after the firewall blocks all traffic to the internet, if OpenVPN is not running.
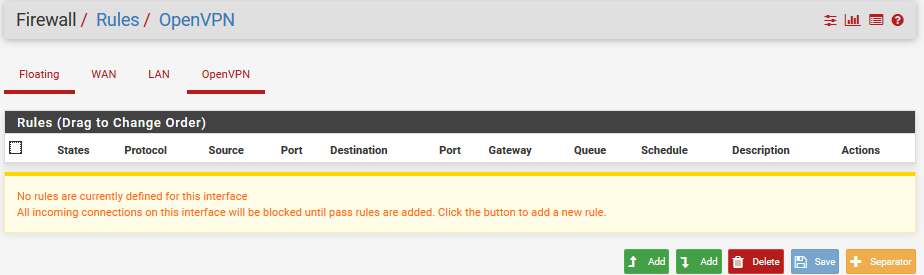
Rules for OpenVPN-Interface
Outbound NAT-Rules
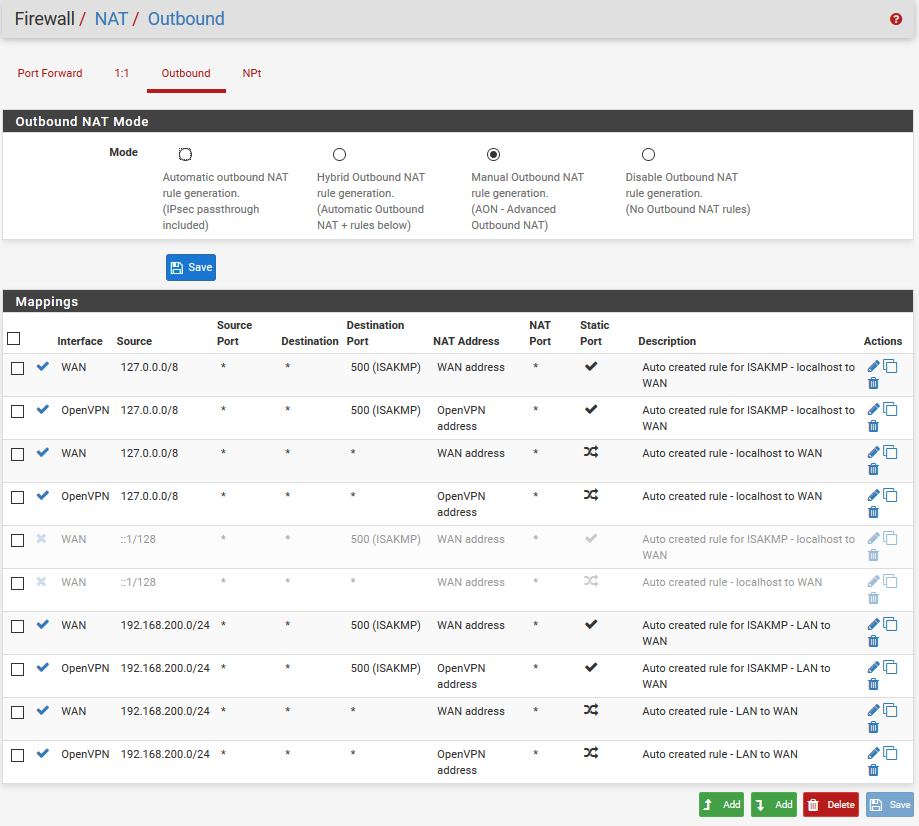
the pfsense is connecting as OpenVPN client to Port 1198
OpenVPN Client settings, according to Private Internet Access Docs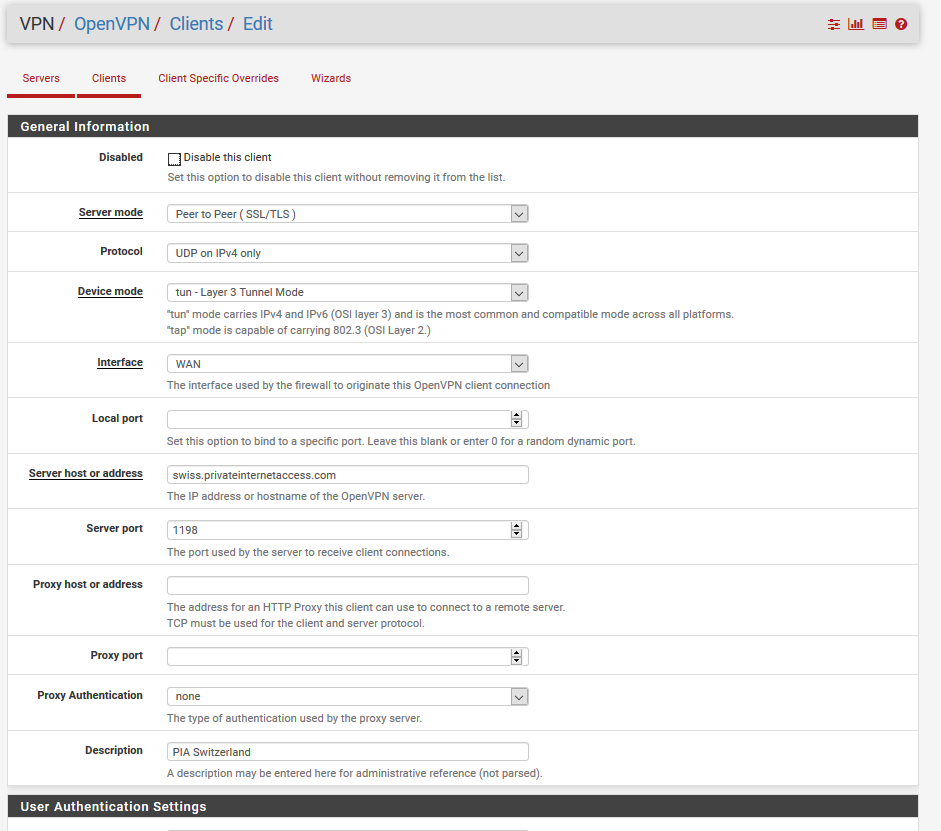
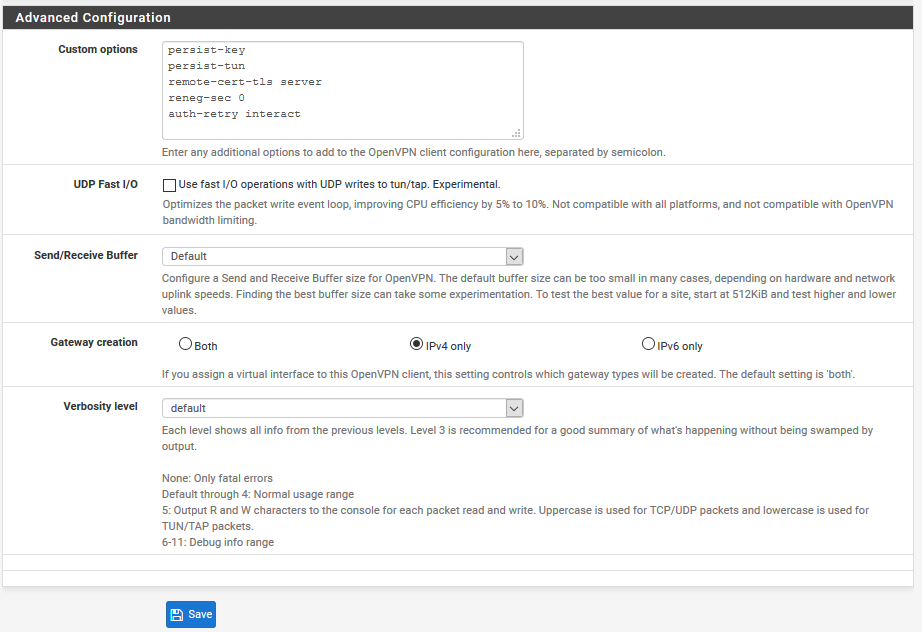
If you need further information to help me setting up leakproof DNS please ask.
Tom
-
@tom-2020 I will take a wild swing at this.
-
The OpenVPN and the NAT config look ok to me. Remember that NAT rules do not change the traffic behaviour. They merely dictate what happens to the traffic when it is "made" to leave an interface.
-
The "made" part happens in the firewall rules. For the firewall rules you need to have a LAN rule that matches the interesting traffic (that you want to go over the tunnel) and will set the gateway to the OpenVPN interface (Rule 1) . Below this you need a LAN catch all rule to catch the remaining traffic and allow or deny it (say Rule 2) and this traffic is the one you want to go over the normal WAN GW.
-
Now under normal circumstances your interesting traffic matches Rule 1 and goes out through the gateway. When you bring the gateway down, the traffic still goes through but now through the WAN gateway. This is decided by System>Advanced>Misc>Skip rules when gateway is down (Read the description there).
By default when the VPN GW is down, the Rule 1 is still processed but the part where you set the gateway (to the VPN) is omitted. If you want the traffic to be blocked then you need to check this box so that Rule 1 is ignored. -
You also need to have a rule 1.5 that is the same as Rule 1 but denies the traffic. So when the VPN GW is down, Rule 1 is ignored and rule 1.5 will kill the traffic. Rule 2 is still in place for the normal LAN traffic to go out though the WAN.
-
-
@AB5G
Thank you for detailed answer, you're very kind taking the time to explain the rules.I have only one question before I can test to implement the suggested changes:
"(...) The "made" part happens in the firewall rules. (...)"
You are talking about the Outbound NAT rules, am I right?
Rule 1 = allow / send all LAN traffic to the VPN Gateway
Rule 1.5 = block all traffic from LAN (this will stop "leakage" of LAN traffic over WAN, when the VPN is down.
Rule 2 = Allow specific traffic to WAN GatewayThe only traffic I want to allow to the WAN gateway is:
- DNS to VPN's Nameserver for the initial connection
- OpenVPN traffic to establish the Tunnel
All other traffic (LAN) should go through the tunnel or be blocked if the OpenVPN is not running.
Tom
-
@tom-2020 said in how to setup Leakproof VPN (Private Internet Access):
Rule 1 = allow / send all LAN traffic to the VPN Gateway
Rule 1.5 = block all traffic from LAN (this will stop "leakage" of LAN traffic over WAN, when the VPN is down.
Rule 2 = Allow specific traffic to WAN Gateway"You are talking about the Outbound NAT rules, am I right?" > I mean the firewall rules. Your firewall rules (as I look at them in the pic above) are not sending any traffic to the VPN gateway. Your traffic will goto the WAN gateway. The firewall rules are the one who decide which gateway to use.
Having a NAT rule that shows your subnet ntatted to the VPN GW does not equal to traffic being sent to the VPN GW. They merely dictate what happens to the traffic when it is "made" to leave the VPN interface. You "make" the traffic leave the VPN GW instead of the WAN GW in the firewall rules.
I would use the following
Rule 1 = allow / send 'DNS/OpenVPN' LAN traffic to the WAN Gateway (this will always be true)
Rule 2 = send everything else to VPN GW (this will be true when the VPN GW is up)
Rule 3 = Rule 2 with block (this will kill the traffic when the GW is down)In your example the traffic will never hit Rule 2 cause a match would always be found in Rule 1 or Rule 1.5(when Rule 1 is skipped)
-
Hello,
I mean the firewall rules. Your firewall rules (as I look at them in the pic above) are not sending any traffic to the VPN gateway. Your traffic will goto the WAN gateway. The firewall rules are the one who decide which gateway to use.
Thanks, now I understand, you are speaking about the gateway settings in my Firewall > Rules > LAN.
If I edit a rule I have found the "Display Advanced" button under the "Extra Options".
There I have a setting, where I can set a gateway: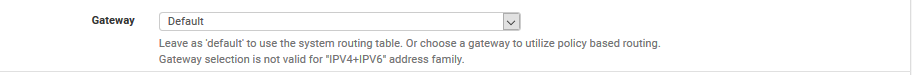
But I am unable to choose the OpenVPN as gateway:
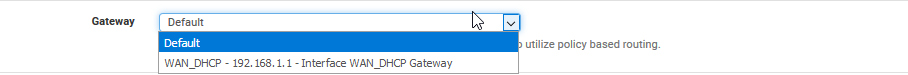
I think I need to assign the OpenVPN to a new interface, under Interface > Interface Assignments:
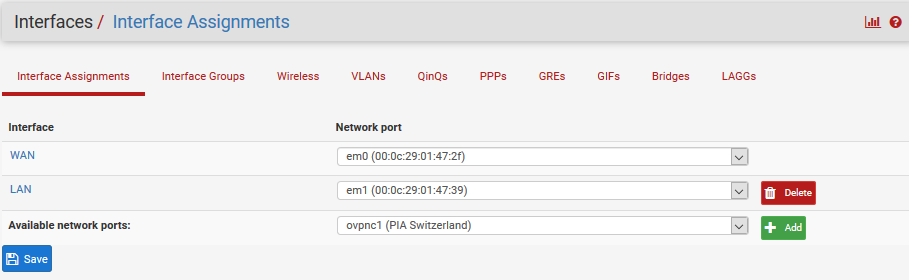
I added the network port ovpnc1 so it available as OPT1-Interface:
I then edited my Firewall LAN Rules that all traffic from LAN has to go via the OpenVPN-Gateway and put one last rule (yellow mark) to block all traffic (if the openvpngateway is unavailable), which I think is not needed because the firewall should block everything which is not allowed.
The new LAN rules:
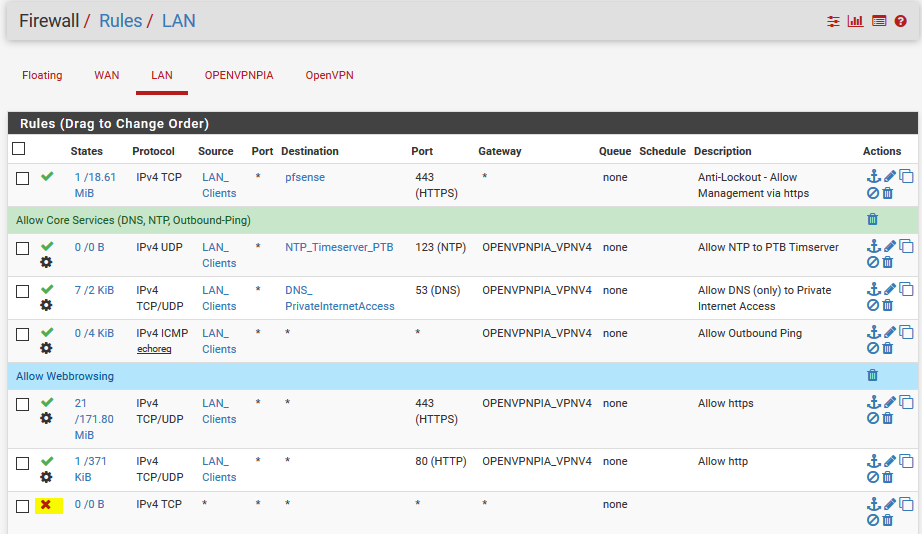
I made some tests and if the OpenVPN is active I don't see any traffic hitting the main firewall.
I am using the main firewall to checj which packages are leaving the pfsense firewall, which makes it easier to troubleshoot if everything is really working..Setup:
Main Firewall (Cisco ASA) --> pfSense with OpenVPN --> LaptopIf I disable the OpenVPN connection, and I try to connect to a website, the traffic is allowed to pass the pfsense, even if my last LAN-firewall rule says Block all traffic from any-to-any.
This is a connection to 8.8.8.8 via http without the VPN beeing active, passing the pfsense and hitting my ASA:
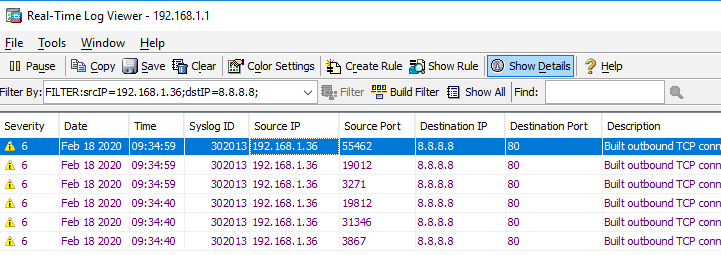
Normally this should not happen, according to my understanding.
I had also to tweak outbound NAT rules to make it work.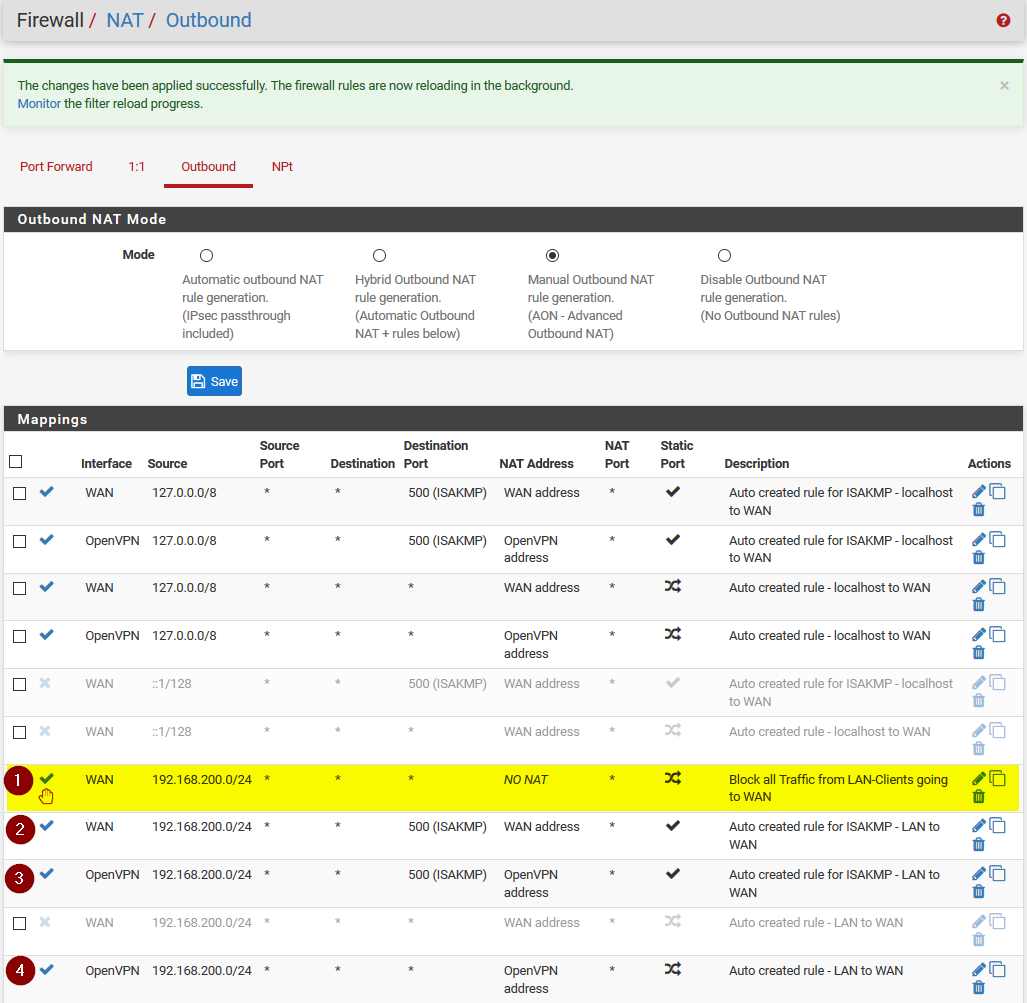
As far as I understand my rule (1) (yellow highlight) will block all traffic from LAN which goes to the WAN-address.
This should never be allowed.
I am not sure if I need to disable rule (2) also and what it is for.
Same for rule (3) as this should be covered in rule (4) (Destionation Port = any includes 500)I think the Outbound NAT rules can be cleaned up to make it easier.
Additionally I would like to know where I can put firewall rules in place, so that outbound connections from the pfsense for example to establish the VPN are only possible to the VPN provider.
This would be 3 rules:- Allow DNS-requests from pfSense to VPN providers DNS Servers (UDP/53)
- Allow OpenVPN-connection from pfSense to VPN-Server (UDP/1198)
- Block all other outgoing traffic
Where should I add those rules? On the OpenVPN Rules page?
- Tom
-
Did you enable the below as I indicated before?
System>Advanced>Misc>Skip rules when gateway is down.
With this you will activate the VPN kill switch. Your firewall rules now look ok.
Also on the NAT read my statement again (closely). You can have overlapping NAT rules for a subnet 192.168.200.0/24 pointing to VPN gw and another one pointing to the Wan gw. They don’t work like firewall rules. So they are not evaluated TOP to bottom. When interesting traffic matches a Lan firewall rule, the GW defined in the firewall rule will invoke the Corresponding NAT rule. If this is confusing then leave your NAT rules as you had them in the initial post.
-
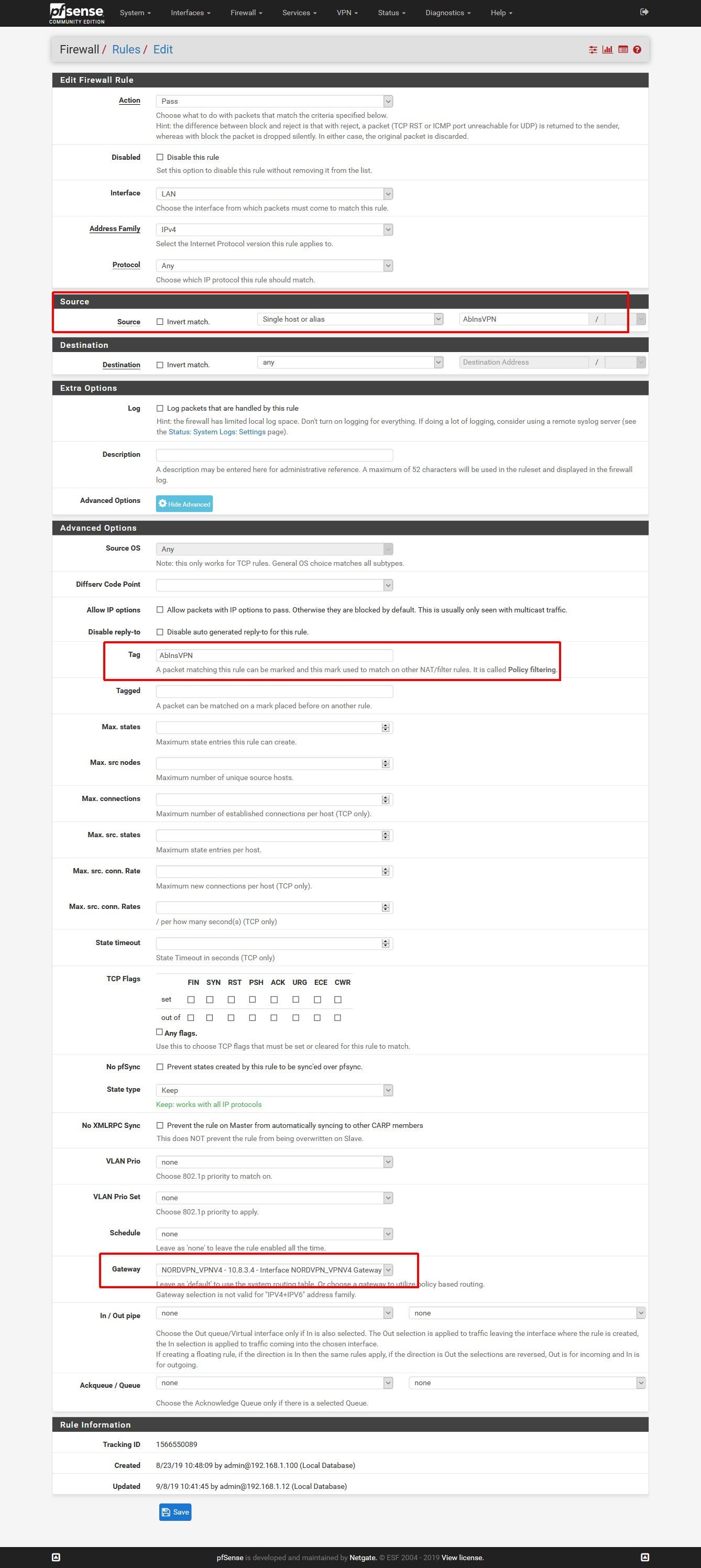
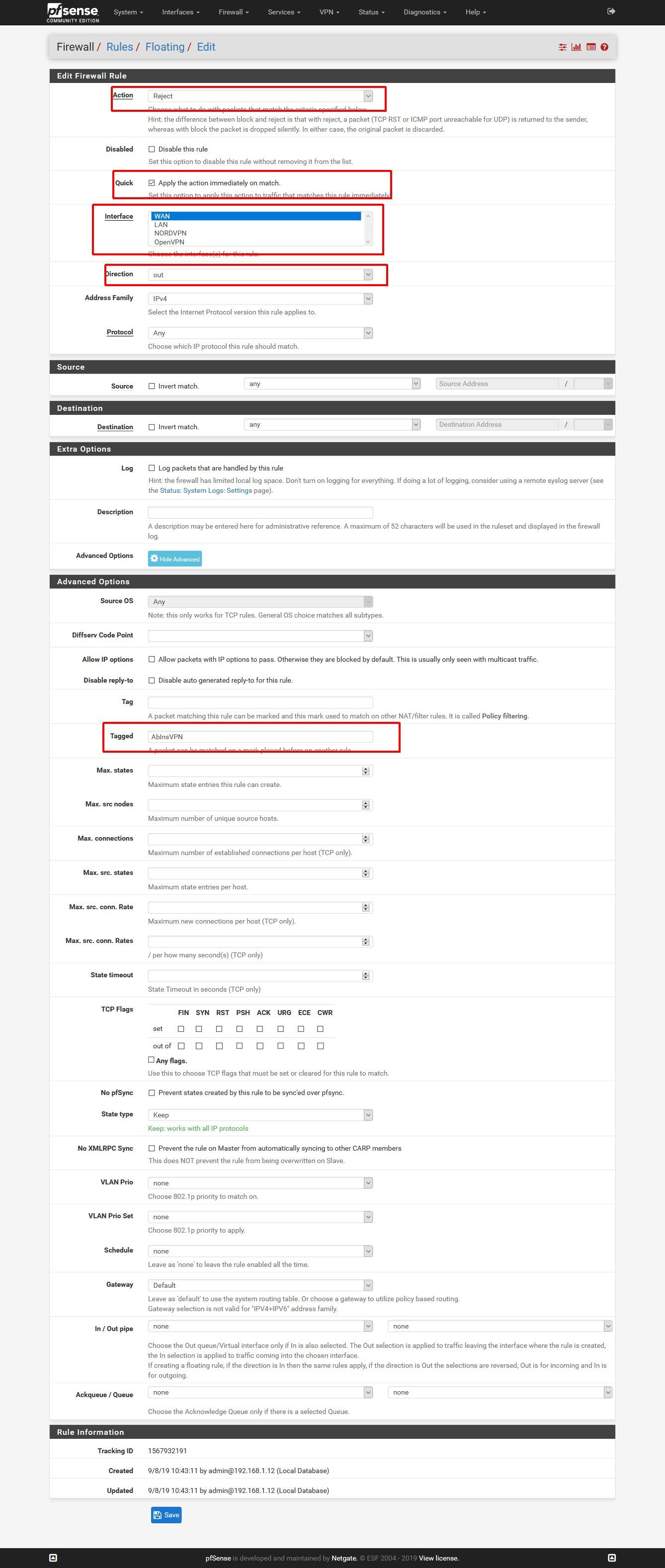
There is one easy solution to this, tagging. One Rule @ LAN and @ WAN and it is working fine. In the screenshots the hosts that get routed through the VPN are defined in an alias, which has the same name as the tag, but that is totally optional.
-
@Bob-Dig
thanks for the interesting hint, tagging looks like a great feature!
So basically I am tagging all (!) my current rules in the LAN section where I define which traffic is allowed and that it goes through the OpenVPN gateway.
And the I setup a rule which rejects all traffic which is tagged and goes to WAN, correct?How do I make sure that the only connection the pfsense can do itself will be to VPN Providers DNS and OpenVPN Servers?
As far as I understand this can also be done via "floating rules":
Floating Rules can:
Filter traffic from the firewall itself
Filter traffic in the outbound direction (all other tabs are Inbound processing only)
https://docs.netgate.com/pfsense/en/latest/firewall/floating-rules.html
[...]-Tom