How to Block Potentially Bad traffic
-
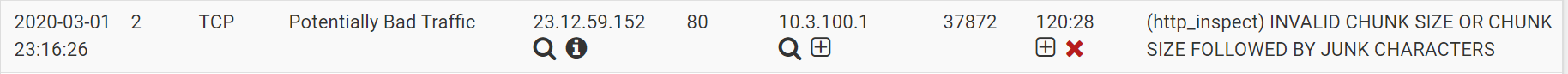
Hi, I have checked my snort alert and see the bad traffic (see below), and it makes me wonder if this is really bad traffic and if it is how to block it. I did further search in the whois database on this ip and it is the ip address of the United States Of America Ashburn Akamai Technologies Inc.
-
@wintok said in How to Block Potentially Bad traffic:
makes me wonder if this is really bad traffic
Yeah running an IPS/IDS is not a set it and forget sort of thing - its going to be loaded with noise (false positives)..
Running such a system requires lots of work, and understanding to weed out all the noise and tweak the rule sets to only work with your normal traffic flow without loads of false stuff.
Also in this day an age of pretty much all traffic encrypted - running such a system is not for everyone. If you don't actually expose services like httpd to the public, your prob going to see way more confusing information than anything of real interest..
Unless you have been doing this for years, and have lots of experience - its going to be a very steep learning curve.
-
I see akamai a lot and have set up an alias for them as well, that being said in snort, there is a specific rule for akamai. After disabling it, and applying, snort stops checking for that specifically. Works with other protocols as well.
That being said, I personally saw (no longer) akamai when watching YouTube (openappid rule for that as well) mostly. I believe they're a content delivery network, and those seem to get flagged a lot.
As per certain (http inspect) or any related rules to akamai or (for me steam, epic games, etc) others, I ended up suppressing common occurrences.
Week and a half later, all I really have to check snort for is the random windows update block or exe file block during driver updates. Using pfblockerng as well, once past snort traffic goes through pfblockerng where there are other lists that gets checked (ads, malicious,etc) and applied. pfblockerng (ip/dnsbl) is wonderful IMO very versatile, for me at least - especially with whitelisting and tld enabled. It might take a little bit for tld (less than 1 minute still) but instead of loading 500,000 plus entries, tld cuts it down (for me) to under 80,000.
Currently, my install blocks roughly 16%+ just in pfblockerng alone, not including snorts "emerging threats".
Grain of salt, hope it helps
-
@wintok said in How to Block Potentially Bad traffic:
Hi, I have checked my snort alert and see the bad traffic (see below), and it makes me wonder if this is really bad traffic and if it is how to block it. I did further search in the whois database on this ip and it is the ip address of the United States Of America Ashburn Akamai Technologies Inc.

The HTTP_INSPECT rules triggering is almost never the result of something malicious. These rules are sort of like the "grammar police" for HTTP traffic and will alert on anything they see that is not RFC compliant. Unfortunately, with Snort in the pfSense-2.4 branch, the only option is to block on all alerts or block on no alerts. So you would need to either suppress or disable this rule in your environment if you determine it is a false positive (which it likely is).
Snort in the 2.5 branch of pfSense offers a new Inline IPS Mode like Suricata has. That mode lets you set some rules to just ALERT on traffic while others can be set to DROP or REJECT traffic. So using that mode the rule you referenced would generate an alert but would not block (or drop) the traffic.